Category:Telephone exchange equipment
Pages in category "Telephone exchange equipment"
The following 43 pages are in this category, out of 43 total. This list may not reflect recent changes.
C
I
N
https://en.wikipedia.org/wiki/Category:Telephone_exchange_equipment
The 3CX Phone System is the software-based private branch exchange (PBX) Phone system developed and marketed by the company, 3CX. The 3CX Phone System is based on the SIP (Session Initiation Protocol) standard and enables extensions to make calls via the public switched telephone network (PSTN) or via Voice over Internet Protocol (VoIP) services on premises, in the cloud, or via a cloud service owned and operated by the 3CX company. The 3CX Phone System is available for Windows, Linux, Raspberry Pi[1] and supports standard SIP soft/hard phones, VoIP services, faxing, voice and web meetings, as well as traditional PSTN phone lines.
https://en.wikipedia.org/wiki/3CX_Phone_System
In data communications, an automatic switching system is a switching system in which all the operations required to execute the three phases of Information transfer transactions are automatically executed in response to signals from a user end-instrument.[1]
In an automatic switching system, the information-transfer transaction is performed without human intervention, except for initiation of the access phase and the disengagement phase by a user.[2]
In telephony, it refers to a telephone exchange in which all the operations required to set up, supervise, and release connections required for telephone calls are automatically performed in response to signals from a calling device. This distinction lost importance as manual switching declined during the 20th century.
References
- Glover, S. (November 1966). "Automatic Switching at the Edmonton Television Studios". Journal of the SMPTE. 75 (11): 1089–1092. doi:10.5594/J05892. ISSN 0361-4573.
https://en.wikipedia.org/wiki/Automatic_switching_system
In electronics and telecommunications, a crossbar switch (cross-point switch, matrix switch) is a collection of switches arranged in a matrix configuration. A crossbar switch has multiple input and output lines that form a crossed pattern of interconnecting lines between which a connection may be established by closing a switch located at each intersection, the elements of the matrix. Originally, a crossbar switch consisted literally of crossing metal bars that provided the input and output paths. Later implementations achieved the same switching topology in solid-state electronics. The crossbar switch is one of the principal telephone exchange architectures, together with a rotary switch, memory switch,[2] and a crossover switch.
General properties
A crossbar switch is an assembly of individual switches between a set of inputs and a set of outputs. The switches are arranged in a matrix. If the crossbar switch has M inputs and N outputs, then a crossbar has a matrix with M × N cross-points or places where connections can be made. At each crosspoint is a switch; when closed, it connects one of the inputs to one of the outputs. A given crossbar is a single layer, non-blocking switch. A crossbar switching system is also called a coordinate switching system.
Collections of crossbars can be used to implement multiple layer and blocking switches. A blocking switch prevents connecting more than one input. A non-blocking switch allows other concurrent connections from inputs to other outputs.
Applications
Crossbar switches are commonly used in information processing applications such as telephony and circuit switching, but they are also used in applications such as mechanical sorting machines.
The matrix layout of a crossbar switch is also used in some semiconductor memory devices which enables the data transmission. Here the bars are extremely thin metal wires, and the switches are fusible links. The fuses are blown or opened using high voltage and read using low voltage. Such devices are called programmable read-only memory.[3] At the 2008 NSTI Nanotechnology Conference a paper was presented that discussed a nanoscale crossbar implementation of an adding circuit used as an alternative to logic gates for computation.[4]
Matrix arrays are fundamental to modern flat-panel displays. Thin-film-transistor LCDs have a transistor at each crosspoint, so they could be considered to include a crossbar switch as part of their structure.
For video switching in home and professional theater applications, a crossbar switch (or a matrix switch, as it is more commonly called in this application) is used to distribute the output of multiple video appliances simultaneously to every monitor or every room throughout a building. In a typical installation, all the video sources are located on an equipment rack, and are connected as inputs to the matrix switch.
Where central control of the matrix is practical, a typical rack-mount matrix switch offers front-panel buttons to allow manual connection of inputs to outputs. An example of such a usage might be a sports bar, where numerous programs are displayed simultaneously. Ordinarily, a sports bar would install a separate desk top box for each display for which independent control is desired. The matrix switch enables the operator to route signals at will, so that only enough set top boxes are needed to cover the total number of unique programs to be viewed, while making it easier to control sound from any program in the overall sound system.
Such switches are used in high-end home theater applications. Video sources typically shared include set-top receivers or DVD changers; the same concept applies to audio. The outputs are wired to televisions in individual rooms. The matrix switch is controlled via an Ethernet or RS-232 connection by a whole-house automation controller, such as those made by AMX, Crestron, or Control4, which provides the user interface that enables the user in each room to select which appliance to watch. The actual user interface varies by system brand, and might include a combination of on-screen menus, touch-screens, and handheld remote controls. The system is necessary to enable the user to select the program they wish to watch from the same room they will watch it from, otherwise it would be necessary for them to walk to the equipment rack.
The special crossbar switches used in distributing satellite TV signals are called multiswitches.
Implementations
Historically, a crossbar switch consisted of metal bars associated with each input and output, together with some means of controlling movable contacts at each cross-point. The first switches used metal pins or plugs to bridge a vertical and horizontal bar. In the later part of the 20th century, the use of mechanical crossbar switches declined and the term described any rectangular array of switches in general. Modern crossbar switches are usually implemented with semiconductor technology. An important emerging class of optical crossbars is implemented with microelectromechanical systems (MEMS) technology.
Mechanical
A type of mid-19th-century telegraph exchange consisted of a grid of vertical and horizontal brass bars with a hole at each intersection (c.f. top picture). The operator inserted a metal pin to connect one telegraph line to another.
Electromechanical switching in telephony
A telephony crossbar switch is an electromechanical device for switching telephone calls. The first design of what is now called a crossbar switch was the Bell company Western Electric's coordinate selector of 1915. To save money on control systems, this system was organized on the stepping switch or selector principle rather than the link principle. It was little used in America, but the Televerket Swedish governmental agency manufactured its own design (the Gotthilf Betulander design from 1919, inspired by the Western Electric system), and used it in Sweden from 1926 until the digitization in the 1980s in small and medium-sized A204 model switches. The system design used in AT&T Corporation's 1XB crossbar exchanges, which entered revenue service from 1938, developed by Bell Telephone Labs, was inspired by the Swedish design but was based on the rediscovered link principle. In 1945, a similar design by Swedish Televerket was installed in Sweden, making it possible to increase the capacity of the A204 model switch. Delayed by the Second World War, several millions of urban 1XB lines were installed from the 1950s in the United States.
In 1950, the Swedish Ericsson company developed their own versions of the 1XB and A204 systems for the international market. In the early 1960s, the company's sales of crossbar switches exceeded those of their rotating 500-switching system, as measured in the number of lines. Crossbar switching quickly spread to the rest of the world, replacing most earlier designs like the Strowger (step-by-step) and Panel systems in larger installations in the U.S. Graduating from entirely electromechanical control on introduction, they were gradually elaborated to have full electronic control and a variety of calling features including short-code and speed-dialing. In the UK the Plessey Company produced a range of TXK crossbar exchanges, but their widespread rollout by the British Post Office began later than in other countries, and then was inhibited by the parallel development of TXE reed relay and electronic exchange systems, so they never achieved a large number of customer connections although they did find some success as tandem switch exchanges.
Crossbar switches use switching matrices made from a two-dimensional array of contacts arranged in an x-y format. These switching matrices are operated by a series of horizontal bars arranged over the contacts. Each such select bar can be rocked up or down by electromagnets to provide access to two levels of the matrix. A second set of vertical hold bars is set at right angles to the first (hence the name, "crossbar") and also operated by electromagnets. The select bars carry spring-loaded wire fingers that enable the hold bars to operate the contacts beneath the bars. When the select and then the hold electromagnets operate in sequence to move the bars, they trap one of the spring fingers to close the contacts beneath the point where two bars cross. This then makes the connection through the switch as part of setting up a calling path through the exchange. Once connected, the select magnet is then released so it can use its other fingers for other connections, while the hold magnet remains energized for the duration of the call to maintain the connection. The crossbar switching interface was referred to as the TXK or TXC (telephone exchange crossbar) switch in the UK.
However, the Bell System Type B crossbar switch of the 1960s was made in the largest quantity. The majority were 200-point switches, with twenty verticals and ten levels of three wires, Each select bar carries ten fingers so that any of the ten circuits assigned to the ten verticals can connect to either of two levels. Five select bars, each able to rotate up or down, mean a choice of ten links to the next stage of switching. Each crosspoint in this particular model connected six wires. The vertical off-normal contacts next to the hold magnets are lined up along the bottom of the switch. They perform logic and memory functions, and the hold bar keeps them in the active position as long as the connection is up. The horizontal off-normals on the sides of the switch are activated by the horizontal bars when the butterfly magnets rotate them. This only happens while the connection is being set up, since the butterflies are only energized then.
The majority of Bell System switches were made to connect three wires including the tip and ring of a balanced pair circuit and a sleeve lead for control. Many connected six wires, either for two distinct circuits or for a four wire circuit or other complex connection. The Bell System Type C miniature crossbar of the 1970s was similar, but the fingers projected forward from the back and the select bars held paddles to move them. The majority of type C had twelve levels; these were the less common ten level ones. The Northern Electric Minibar used in SP1 switch was similar but even smaller. The ITT Pentaconta Multiswitch of the same era had usually 22 verticals, 26 levels, and six to twelve wires. Ericsson crossbar switches sometimes had only five verticals.
Instrumentation
For instrumentation use, James Cunningham, Son and Company[5] made high-speed, very-long-life crossbar switches[6] with physically small mechanical parts which permitted faster operation than telephone-type crossbar switches. Many of their switches had the mechanical Boolean AND function of telephony crossbar switches, but other models had individual relays (one coil per crosspoint) in matrix arrays, connecting the relay contacts to [x] and [y] buses. These latter types were equivalent to separate relays; there was no logical AND function built in. Cunningham crossbar switches had precious-metal contacts capable of handling millivolt signals.
Telephone exchange
Early crossbar exchanges were divided into an originating side and a terminating side, while the later and prominent Canadian and US SP1 switch and 5XB switch were not. When a user picked up the telephone handset, the resulting line loop operating the user's line relay caused the exchange to connect the user's telephone to an originating sender, which returned the user a dial tone. The sender then recorded the dialed digits and passed them to the originating marker, which selected an outgoing trunk and operated the various crossbar switch stages to connect the calling user to it. The originating marker then passed the trunk call completion requirements (type of pulsing, resistance of the trunk, etc.) and the called party's details to the sender and released. The sender then relayed this information to a terminating sender (which could be on either the same or a different exchange). This sender then used a terminating marker to connect the calling user, via the selected incoming trunk, to the called user, and caused the controlling relay set to send the ring signal to the called user's phone, and return ringing tone to the caller.
The crossbar switch itself was simple: exchange design moved all the logical decision-making to the common control elements, which were very reliable as relay sets. The design criteria specified only two hours of downtime for service every forty years, which was a large improvement over earlier electromechanical systems. The exchange design concept lent itself to incremental upgrades, as the control elements could be replaced separately from the call switching elements. The minimum size of a crossbar exchange was comparatively large, but in city areas with a large installed line capacity the whole exchange occupied less space than other exchange technologies of equivalent capacity. For this reason they were also typically the first switches to be replaced with digital systems, which were even smaller and more reliable.
Two principles of crossbar switching existed. An early method was based on the selector principle, which used crossbar switches to implement the same switching fabric used with Strowger switches. In this principle, each crossbar switch would receive one dialed digit, corresponding to one of several groups of switches or trunks. The switch would then find an idle switch or trunk among those selected and connect to it. Each crossbar switch could only handle one call at a time; thus, an exchange with a hundred 10×10 switches in five stages could only have twenty conversations in progress. Distributed control meant there was no common point of failure, but also meant that the setup stage lasted for the ten seconds or so the caller took to dial the required number. In control occupancy terms this comparatively long interval degrades the traffic capacity of a switch.[citation needed]
Starting with the 1XB switch, the later and more common method was based on the link principle, and used the switches as crosspoints. Each moving contact was multipled to the other contacts on the same level by bare-strip wiring, often nicknamed banjo wiring.[7] to a link on one of the inputs of a switch in the next stage. The switch could handle its portion of as many calls as it had levels or verticals. Thus an exchange with forty 10×10 switches in four stages could have one hundred conversations in progress. The link principle was more efficient, but required a complex control system to find idle links through the switching fabric.
This meant common control, as described above: all the digits were recorded, then passed to the common control equipment, the marker, to establish the call at all the separate switch stages simultaneously. A marker-controlled crossbar system had in the marker a highly vulnerable central control; this was invariably protected by having duplicate markers. The great advantage was that the control occupancy on the switches was of the order of one second or less, representing the operate and release lags of the X-then-Y armatures of the switches. The only downside of common control was the need to provide digit recorders enough to deal with the greatest forecast originating traffic level on the exchange.
The Plessey TXK1 or 5005 design used an intermediate form, in which a clear path was marked through the switching fabric by distributed logic, and then closed through all at once.
Crossbar exchanges remain in revenue service only in a few telephone networks. Preserved installations are maintained in museums, such as the Museum of Communications in Seattle, Washington, and the Science Museum in London.
Semiconductor
Semiconductor implementations of crossbar switches typically consist of a set of input amplifiers or retimers connected to a series of interconnects within a semiconductor device. A similar set of interconnects are connected to output amplifiers or retimers. At each cross-point where the bars cross, a pass transistor is implemented which connects the bars. When the pass transistor is enabled, the input is connected to the output.
As computer technologies have improved, crossbar switches have found uses in systems such as the multistage interconnection networks that connect the various processing units in a uniform memory access parallel processor to the array of memory elements.
Arbitration
A standard problem in using crossbar switches is that of setting the crosspoints.[citation needed] In the classic telephony application of crossbars, the crosspoints are closed, and open as the telephone calls come and go. In Asynchronous Transfer Mode or packet switching applications, the crosspoints must be made and broken at each decision interval. In high-speed switches, the settings of all of the crosspoints must be determined and then set millions or billions of times per second. One approach for making these decisions quickly is through the use of a wavefront arbiter.
See also
- Matrix mixer
- Nonblocking minimal spanning switch - describes how to combine crossbar switches into larger switches.
- RF switch matrix
References
- The Western Electric Engineer: Volumes 5-7. Western Electric. 1961. p. 23.
Further reading
- Pacific Telephone and Telegraph Company. General Administration Engineering Section (1956). Survey of telephone switching. San Francisco, California. OCLC 11376478.
- Scudder, F.J.; Reynolds, J.N. (January 1939). "Crossbar Dial Telephone Switching System". Bell System Technical Journal. 8 (1): 76–118. doi:10.1109/EE.1939.6431910. S2CID 51659407. Retrieved 23 April 2015.
External links
https://en.wikipedia.org/wiki/Crossbar_switch
The GTD-5 EAX (General Telephone Digital Number 5 Electronic Automatic Exchange) is the Class 5 telephone switch developed by GTE Automatic Electric Laboratories. This digital central office telephone circuit switching system is used in the former GTE service areas and by many smaller telecommunications service providers.
History
The GTD-5 EAX first appeared in Banning, California on June 26, 1982,[1] slowly replacing the electromechanical systems still in use in the independent switch market at that time. The GTD-5 EAX was also used as a Class 4 telephone switch or as a mixed Class 4/5 in markets too small for a GTD-3 EAX or 4ESS switch. The GTD-5 EAX was also exported internationally, and manufactured outside of the U.S. under license, primarily in Canada, Belgium and Italy. By 1988, it had 4% of the worldwide switching market, with an installed base of 11,000,000 subscriber lines.[2] GTE Automatic Electric Laboratories became GTE Network Systems and later GTE Communication Systems. In 1989, GTE sold partial ownership of its switching division to AT&T, forming AG Communication Systems. AG Communication Systems eventually fell under the ownership of Lucent Technologies, and was dissolved as a separate corporate entity in 2003.
Architecture
Processor complexes
The processing building block of the GTD-5 EAX was the "processor complex". These were each assigned a specific function within the overall switch design. In the original generation, Intel 8086 processors were used. These were replaced by NEC V30s (an 80186 instruction set compatible processor with 8086 pinout implemented in CMOS and somewhat faster than the 8086 due to internal improvements) in the second generation, and ultimately by 80386 processors.
- Administrative Processor Complex (APC)
The APC was responsible for the craft interface to the system, administration of status control for all hardware devices, Recent Change, billing, and overall administration.
- Telephony Processor Complex (TPC)
The TPC was responsible for call sequence and state control. It received signalling inputs collected from peripheral processors (see MXU, RLU, RSU, and TCU below) and sent control information back to the peripheral processors.
- Base Processor Complex (BPC)
This term referred collectively to the APC and TPCs. Physically, this distinction made little sense, but was important from a software compilation standpoint. Since the APC and TPC processors shared a large memory-mapped space, some stages of compilation were performed in common.
- Timeswitch and Peripheral Control Unit (TCU)
The TCU was responsible for a group of Facility Interface Units (FIUs). Each FIU was responsible for connecting the system to a particular class of physical connection: analog lines in the Analog Line FIU (and its successor, the Extended Line FIU); analog trunks in the Analog Trunk FIU; and digital carrier in the Digital Trunk FIU and its successor, the EDT FIU. Unlike the SM in the competitive 5ESS Switch, the TCUs did not perform all call processing functions, but limited themselves to digit collection and signalling interpretation.
- Remote Switching Unit (RSU)
The RSU was similar to the TCU, but had a network capable of local switching, and could process calls locally when links to the base unit were severed.
- Remote Line Unit (RLU)
The RLU was a condensed version of the RSU, with no local switching capability and limited line capacity.
- MultipleXor Unit (MXU)
The MXU was actually a Lenkurt 914E Subscriber Loop Carrier. When integrated with the GTD-5 EAX, it used a custom software load that permitted message communication with the remainder of the system.
Internal communication
Most communication within the GTD-5 was performed via direct memory-mapped I/O. The APC and each TPC were each connected to three common memory units. These common memory units each contained 16 megabytes of memory which were allocated to shared data structures, both dynamic structures related to dynamic call data and static (protected) data related to the office database. The APC, TPC, and TCUs all connected to a smaller shared memory, the Message Distribution Circuit (MDC). This was an 8k word 96 port memory that was used to place small packetized messages into software defined queues. The MXU, RLU, and RSU were all sufficiently far from the base unit that they could not participate in the shared memory based communication directly. A special circuit pack, the Remote Data Link Controller (RDLC) was installed in the DT-FIU of the remote unit and its host TCU. This allowed a serial communication link over a dedicated timeslot of a DS1 carrier. The host TCU was responsible for forwarding messages from the remote unit through the MDC.
Network
Two generations of network were available on the GTD-5. The latter network was made available sometime around 2000, but its characteristics are not described in public documentation. The network described in the article is the original network, available from 1982 until approximately 2000.
The GTD-5 EAX ran on a Time-Space-Time (TST) topology. Each TCU contained two timeswitches (TSWs) with a total capacity of 1544 timeslots: 772 in the originating time switch and 772 in the terminating time switch. Four FIUs of 193 timeslots each were connected to the TSW. Trunking FIUs connected 192 timeslots of facility (eight DS1 carriers or 192 individual analog trunks). The original Analog Line FIU had a 768 line capacity with one codec per line. The digital output of the 768 codecs was concentrated to 192 timeslots before presentation to the timeswitch, a 4:1 concentration. In the later 1980s, higher capacity line frames of 1172 and 1536 lines became available, allowing for higher concentration ratios of 6:1 and 8:1.
The Space Switch (SSW) was under the control of the TPCs and APC, which accessed it via the Space Interface Controller (SIC). The SSW was divided into eight Space Switch Units (SSUs). Each SSU could switch all 772 channels between 32 TCUs. The first 32 TCUs connected in sequential order to the first two SSUs. Connecting the two SSUs in parallel this way provided the doubling of network capacity required in a CLOS network. When the system grew beyond 32 TCUs, an additional 6 SSUs were added. Two of these SSUs connected to TCU32-TCU63 in a manner directly analogous to the first two SSUs. Two connected the inputs from TCU0-TCU31 to the output of TCU32-TCU63, while the final two connected the outputs of TCU32-TCU63 to the input of TCU0-TCU31.
The GTD-5, unlike its contemporaries, did not make extensive use of serial line technology. Network communication was based on a 12-bit parallel PCM word[3] carried over cables incorporating parallel twisted pairs. Communication between processors and peripherals was memory mapped, with similar cables extending 18 bit address and data buses between frames.
Analog line FIU (AL-FIU)
The AL-FIU contained 8 simplex groups of 96 lines each, referred to as Analog Line Units (ALUs), controlled by a redundant controller, the Analog Control Unit (ACU). The 96 lines within each ALU were housed on 12 circuit packs of eight line circuits. These 12 circuit packs were electrically grouped into four groups of three cards, where each group of three cards shared a serial 24 timeslot PCM group. The timeslot assignment capabilities of the codec were used to manage timeslots within the PCM group. The ACU contained a timeslot selection circuit that could select the same timeslot from up to eight PCM groups, (i.e. network timeslot 0-7 would select PCM timeslot 0, network timeslot 8-15 would select PCM timeslot 1, etc., giving eight opportunities for PCM timeslot 0 to connect to network). Since the same timeslot could be selected only eight times out of thirty-two possible candidates, the overall concentration was four to one. A later generation expanded the number of ALUs to twelve or sixteen, as appropriate, giving larger effective concentration.
Analog trunk FIU (AT-FIU)
The AT-FIU was a repackaged AL-FIU. Only two simplex groups were supported, and the trunk cards carried four circuits instead of eight. PCM groups were six cards wide instead of three. Since two simplex groups provided a total of 192 trunks, the AT-FIU was unconcentrated, as trunk interfaces demand.
Digital trunk FIU (DT-FIU)
T-carrier spans were terminated, four per card, on the Quad Span Interface Circuit (QSIC) in Digital Trunk Facility Interface Units (DTUs). Two QSICS were equipped per copy. providing for an eight DS1 capacity. The span interface circuits were completely redundant, and all control circuitry operated in lockstep between the two copies. This arrangement provided for excellent failure detection but was plagued by design flaws in the earliest versions. Corrected versions of the design were not widely available until the early 1990s. The later generation Extended Digital Trunk Unit (EDT) included 8 T-carriers per card, and incorporated ESF and PRI interfaces. This FIU operated also operated in lockstep between the two copies, but incorporated a small backplane mounted "fingerboard" to house the transformer circuit.
Processor architecture
Throughout its lifecycle, the GTD-5 EAX incorporated a quad-redundant processor architecture. The main processor complex of the APC, TPC, TCU, RLU, and RSU all consisted of a pair of processor cards, and each of those processor cards contained a pair of processors. The on-card pair of processors executed precisely the same sequence of instructions, and the output of the pair were compared each clock cycle. If the results were not identical, the processors were immediately reset, and the pair of processors on the other card were brought online as the active processor complex. The active processor always kept memory up-to-date so that when these forced switches occurred, little data loss was suffered. When the switch was requested as a part of routine maintenance, the switch could be accomplished with no data loss at all.
Software architecture
The GTD-5 EAX was programmed in a custom version of Pascal.[4][5] This Pascal was extended to include a separate data and type compilation phase, known as the COMPOOL (Communications Pool). By enforcing this separate compilation phase, strict typing could be enforced across separate code compilation. This allowed type checking across procedure boundaries and across processor boundaries.
A small subset of code was programmed in 8086 assembly language. The assembler used had a preprocessor that imported identifiers from the COMPOOL, allowing type compatibility checking between Pascal and assembly.
The earliest peripherals were programmed in the assembly language appropriate to each processor. Eventually, most peripherals were programmed in variations of C and C++.
Administration
The system is administered through an assortment of teletypewriter "Channels" (also called the system console). Various outboard systems have been connected to these channels to provide specialized functions.
Patents
The following is a non-exhaustive list of U.S. patents applicable to the GTD-5 EAX design
- 4569017 Duplex central processing unit synchronization circuit
- 4757494 Method of Generating Additive Combinations for PCM voice samples
- 4835767 Additive PCM speaker circuit for a time shared conference arrangement
- 4466093 Time Shared Conference Arrangement
- 4406005 Dual Rail Time Control Unit for a T-S-T Digital Switching System
- 4509169 Dual rail network for a remote switching unit
- 4466094 Data capture arrangement for a conference circuit
- 4740960 Synchronization arrangement for time multiplexed data scanning circuitry
- 4580243 Circuit for duplex synchronization of asynchronous signals
- 4466092 Test data insertion arrangement for a conference circuit
- 4740961 Synchronization circuitry for duplex digital span equipment
- 5226121 Method of bit rate de-adaption using the ECMA 102 protocol
- 4532624 Parity checking arrangement for a remote switching unit network
- 4509168 Digital remote switching unit
- 4514842 T-S-T-S-T Digital switching network
- 4520478 Space Stage Arrangement for a T-S-T Digital Switching System
- 4524441 Modular Space Stage Arrangement for a T-S-T Digital Switching System
- 4524422 Modularly Expandable Space Stage for a T-S-T Digital Switching System
- 4525831 Interface Arrangement for Buffering Communication information between stages of T-S-T switch
- 5140616 Network independent clocking circuit which allows a synchronous master to be connected to a circuit switched data adapter
- 4402077 Dual rail time and control unit for a duplex T-S-T-digital switching system
- 4468737 Circuit for extending a multiplexed address and data bus to distant peripheral devices
- 4374361 Clock failure monitor circuit employing counter pair to indicate clock failure within two pulses
- 4399534 Dual rail time and control unit for a duplex T-S-T-digital switching system
- 4498174 Parallel cyclic redundancy checking circuit
See also
References
- "100 Years of Telephone Switching",Robert J. Chapuis, A. E. Joel, Jr., Amos E. Joel,p. 51
External links
- Description of GTD-5 in 100 Years of Telephone Switching
- Description of GTD-5 in Electronic Materials Handbook: Packaging
https://en.wikipedia.org/wiki/GTD-5_EAX
Emergency Stand Alone (ESA) is a term used by the vendors of telephone equipment such as Nortel DMS-100, Lucent 5ESS or GTD-5.
Typically, small towns or communities have telephone services provided from a "remote switching unit" which is controlled by the more powerful host switching complex. ESA occurs when the host/remote links are severed, thus leaving the region in “community isolation”. While in the ESA mode, the town/community is limited to only receiving or placing calls within that community/town.
Larger towns/regions may have several remote switching units which required “backdoor trunking” to connect all remote units during ESA within the same town/community. Special translations can be implemented to allow 911 to be redirected to a local number such as the local police station or fire hall that resides within that same community/town.
https://en.wikipedia.org/wiki/Emergency_Stand_Alone
IPC Systems, Inc. is an American company headquartered in Jersey City, New Jersey that provides and services voice communication systems for financial companies.[1] In 2014, IPC Systems employs approximately 1,000 employees throughout the Americas, EMEA and Asia-Pacific regions[2]
IPC's products, called trading turrets, are specialized, multi-line, multi-speaker communications devices used by traders. Turrets can have access to hundreds of lines and allow traders to monitor multiple connections simultaneously to maintain communication with counterparties, liquidity providers, intermediaries and exchanges[3][4] IPC's desktop system for traders provides multiple market data screens. and gives traders the option to use instant messaging for colleague communications while checking on incoming calls.[2]
In 2010, IPC was described by Waters Technology as the "Best Trading Turret Provider"[5] Companies that provide similar services to IPC Systems include BT and Orange Business Services[5]
History
IPC was founded as Interconnect Planning Corporation, a consulting company, in 1973. Its voice communication system was created after Republic National Bank approached IPC founder Stephan Nichols with a request to improve the bank's trading hardware[6]
In 2001, IPC Systems was purchased by Goldman Sachs.[7]
IPC was the first to use Voice over Internet Protocol (VoIP) on the trading floor; this reduced communication costs.[7] The company introduced the first VoIP-based turret in 2001 and its second generation VoIP based turret, the IQ/MAX, in 2006.[8]
Goldman Sachs sold the company to Silver Lake Partners in 2006 for $800 million.[9] In 2014, Centerbridge Partners announced that it had agreed to acquire IPC Systems from Silver Lake Partners.[10]
IPC Systems also developed a division called Positron Public Safety, which developed similar systems for use by 911 operators and other dispatchers.[11] This was sold in 2008 to rival Intrado.[12]
References
- "Intrado-IPC Positron deal expected to close this quarter". Nov 18, 2008 Donny Jackson | Urgent Communications
https://en.wikipedia.org/wiki/IPC_Systems
A trading turret or dealer board is a specialized telephony key system that is generally used by financial traders on their trading desks. Trading has progressed from floor trading through phone trading to electronic trading during the later half of the twentieth century with phone trading having dominated during the 1980s and 1990s. Although most trading volume is now done via electronic trading platforms, some phone trading persists and trading turrets are common on trading desks of investment banks.
Voice trading turrets
Trading turrets, unlike typical phone systems, have a number of features, functions and capabilities specifically designed for the needs of financial traders. Trading turrets enable users to visualize and prioritize incoming call activity from customers or counter-parties and make calls to these same people instantaneously by pushing a single button to access dedicated point-to-point telephone lines (commonly called Ringdown circuits). In addition, many traders have dozens or hundreds of dedicated speed dial buttons and large distribution hoot-n-holler or Squawk box circuits which allow immediate mass dissemination or exchange of information to other traders within their organization or to customers and counter-parties. Due to these requirements many Turrets have multiple handsets and multi-channel speaker units, generally these are shared by teams (for example: equities, fixed income, foreign exchange) or in some cases globally across whole trading organizations.
Unlike standard Private Branch Exchange telephone systems (PBX) designed for general office users, Trading turret system architecture has historically relied on highly distributed switching architectures that enable parallel processing of calls and ensure a "non-blocking, non-contended" state where there is always a greater number of trunks (paths in/out of the system) than users as well as fault tolerance which ensures that any one component failure can not affect all users or lines. As processing power has increased and switching technologies have matured, voice trading systems are evolving from digital time-division multiplexing (TDM) system architectures to Internet Protocol (IP) server-based architectures. IP technologies have transformed communications for traders by enabling converged, multimedia communications that include, in addition to traditional voice calls, presence-based communications such as: unified communications and messaging, instant messaging (IM), chat and audio/video conferencing. Some of modern trading turret models are optimised to integrate with PBX platform. By natively registering on CUCM, for example, office users and turret users can have tighter collaboration and reduce total cost of ownership[citation needed].
While some of trading turret systems also include intercom functions, it is common that financial services firms use an independent intercom system along with trading turret systems.
See also
- Electronic trading platform
- Dedicated line
- Stock market data systems
- Straight-through processing (STP)
- Trading system
- Trading room
References
External links
- A Bankers Guide to Trading Turrets, Peter Redshaw, 12 September 2013. Gartner.
https://en.wikipedia.org/wiki/Trading_turret
A time-slot interchange (TSI) switch is a network switch that stores data in RAM in one sequence, and reads it out in a different sequence. It uses RAM, a small routing memory and a counter. Like any switch, it has input and output ports. The RAM stores the packets or other data that arrive via its input terminal.
Mechanism
In a pure time-slot interchange switch, there is only one physical input, and one physical output. Each physical connection is an opportunity for a switching fabric to fail. The limited number of connections of this switch is therefore valuable in a large switching fabric, because it makes this type of switching very reliable. The disadvantage of this type of switch is that it introduces delay into the signals.
When a packet (or byte, on telephone switches) comes to the input, the switch stores the data in RAM in one sequence, and reads it out in a different sequence. Switch designs vary, but typically, a repeating counter is incremented with an internal clock. It typically wraps-around to zero. The RAM location chosen for the incoming data is taken from a small memory indexed by the counter. It is usually a location for the desired output time-slot. The current value of the counter also selects the RAM data to forward in the current output time slot. Then the counter is incremented to the next value. The switch repeats the algorithm, eventually sending data from any input time-slot to any output time-slot.
To minimize connections, and therefore improve reliability, the data to reprogram the switch is usually programmed via a single wire that threads through the entire group of integrated circuits in a printed circuit board. The software typically compares the data shifted-in with the data shifted-out, to verify that the ICs remain correctly connected. The switching data entered into the ICs is double-buffered. That is, a new switch set-up is shifted-in, and then a single pulse applies the new configuration instantly to all the connected ICs.
Limitation
In
a time-slot interchange (TSI) switch, two memory accesses are required
for each connection (one to read and one to store). Let T be the time to
access the memory. Therefore, for a connection, 2T time will be taken
to access the memory. If there are n connections and t is the operation
time for n lines, then
t=2nT
which gives
n=t/2T
t and n normally come from a higher-level system design of the switching fabric. Hence the technology yielding T determines n for a given t. T also limits t for a given n. Real switching fabrics have real requirements for n and t, and therefore since T must be an actual number set by a possible technology, real switches cannot be arbitrarily large n or small t.
In higher-speed switches, the limit from T can be halved by using a more expensive, less reliable two-port RAM. In these designs, the read and write usually occur at the same time. The switch must still arbitrate when there is an attempt to read and write a RAM slot at the same time. This is normally done by avoiding the case in the control software, by rearranging the connections in the switching fabric. (E.g. see Nonblocking minimal spanning switch)
Customary applications
In packet-switching networks, a time-slot interchange switch is often combined with two space-division switches to implement small network switches.
In telephone switches, time-slot interchange switches usually form the outer layer of the switching fabric at a central office's switch. They take data from time-multiplexed T-1 or E-1 lines that serve neighborhoods. The T-1 or E-1 lines serve the subscriber line interface cards (SLICs) in local neighborhoods. The SLICs serve as the outer space-division switches of a modern wired telephone system.
See also
References
https://en.wikipedia.org/wiki/Time-slot_interchange
A nonblocking minimal spanning switch is a device that can connect N inputs to N outputs in any combination. The most familiar use of switches of this type is in a telephone exchange. The term "non-blocking" means that if it is not defective, it can always make the connection. The term "minimal" means that it has the fewest possible components, and therefore the minimal expense.
Historically, in telephone switches, connections between callers were arranged with large, expensive banks of electromechanical relays, Strowger switches. The basic mathematical property of Strowger switches is that for each input to the switch, there is exactly one output. Much of the mathematical switching circuit theory attempts to use this property to reduce the total number of switches needed to connect a combination of inputs to a combination of outputs.
In the 1940s and 1950s, engineers in Bell Lab began an extended series of mathematical investigations into methods for reducing the size and expense of the "switched fabric" needed to implement a telephone exchange. One early, successful mathematical analysis was performed by Charles Clos (French pronunciation: [ʃaʁl klo]), and a switched fabric constructed of smaller switches is called a Clos network.[1]
Background: switching topologies
The crossbar switch
The crossbar switch has the property of being able to connect N inputs to N outputs in any one-to-one combination, so it can connect any caller to any non-busy receiver, a property given the technical term "nonblocking". Being nonblocking it could always complete a call (to a non-busy receiver), which would maximize service availability.
However, the crossbar switch does so at the expense of using N2 (N squared) simple SPST switches. For large N (and the practical requirements of a phone switch are considered large) this growth was too expensive. Further, large crossbar switches had physical problems. Not only did the switch require too much space, but the metal bars containing the switch contacts would become so long that they would sag and become unreliable. Engineers also noticed that at any time, each bar of a crossbar switch was only making a single connection. The other contacts on the two bars were unused. This seemed to imply that most of the switching fabric of a crossbar switch was wasted.
The obvious way to emulate a crossbar switch was to find some way to build it from smaller crossbar switches. If a crossbar switch could be emulated by some arrangement of smaller crossbar switches, then these smaller crossbar switches could also, in turn be emulated by even smaller crossbar switches. The switching fabric could become very efficient, and possibly even be created from standardized parts. This is called a Clos network.
Completely connected 3-layer switches
The next approach was to break apart the crossbar switch into three layers of smaller crossbar switches. There would be an "input layer", a "middle layer" and an "output layer." The smaller switches are less massive, more reliable, and generally easier to build, and therefore less expensive.
A telephone system only has to make a one-to-one connection. Intuitively this seems to mean that the number of inputs and the number of outputs can always be equal in each subswitch, but intuition does not prove this can be done nor does it tell us how to do so. Suppose we want to synthesize a 16 by 16 crossbar switch. The design could have 4 subswitches on the input side, each with 4 inputs, for 16 total inputs. Further, on the output side, we could also have 4 output subswitches, each with 4 outputs, for a total of 16 outputs. It is desirable that the design use as few wires as possible, because wires cost real money. The least possible number of wires that can connect two subswitches is a single wire. So, each input subswitch will have a single wire to each middle subswitch. Also, each middle subswitch will have a single wire to each output subswitch.
The question is how many middle subswitches are needed, and therefore how many total wires should connect the input layer to the middle layer. Since telephone switches are symmetric (callers and callees are interchangeable), the same logic will apply to the output layer, and the middle subswitches will be "square", having the same number of inputs as outputs.
The number of middle subswitches depends on the algorithm used to allocate connection to them. The basic algorithm for managing a three-layer switch is to search the middle subswitches for a middle subswitch that has unused wires to the needed input and output switches. Once a connectible middle subswitch is found, connecting to the correct inputs and outputs in the input and output switches is trivial.
Theoretically, in the example, only four central switches are needed, each with exactly one connection to each input switch and one connection to each output switch. This is called a "minimal spanning switch," and managing it was the holy grail of the Bell Labs' investigations.
However, a bit of work with a pencil and paper will show that it is easy to get such a minimal switch into conditions in which no single middle switch has a connection to both the needed input switch and the needed output switch. It only takes four calls to partially block the switch. If an input switch is half-full, it has connections via two middle switches. If an output switch is also half full with connections from the other two middle switches, then there is no remaining middle switch which can provide a path between that input and output.
For this reason, a "simply connected nonblocking switch" 16x16 switch with four input subswitches and four output switches was thought to require 7 middle switches; in the worst case an almost-full input subswitch would use three middle switches, an almost-full output subswitch would use three different ones, and the seventh would be guaranteed to be free to make the last connection. For this reason, sometimes this switch arrangement is called a "2n−1 switch", where n is the number of input ports of the input subswitches.
The example is intentionally small, and in such a small example, the reorganization does not save many switches. A 16×16 crossbar has 256 contacts, while a 16×16 minimal spanning switch has 4×4×4×3 = 192 contacts.
As the numbers get larger, the savings increase. For example, a 10,000 line exchange would need 100 million contacts to implement a full crossbar. But three layers of 100 100×100 subswitches would use only 300 10,000 contact subswitches, or 3 million contacts.
Those subswitches could in turn each be made of 3×10 10×10 crossbars, a total of 3000 contacts, making 900,000 for the whole exchange; that is a far smaller number than 100 million.
Managing a minimal spanning switch
The crucial discovery was a way to reorganize connections in the middle switches to "trade wires" so that a new connection could be completed.
The first step is to find an unused link from the input subswitch to a middle-layer subswitch (which we shall call A), and an unused link from a middle-layer subswitch (which we shall call B) to the desired output subswitch. Since, prior to the arrival of the new connection, the input and output subswitches each had at least one unused connection, both of these unused links must exist.
If A and B happen to be the same middle-layer switch, then the connection can be made immediately just as in the "2n−1" switch case. However, if A and B are different middle-layer subswitches, more work is required. The algorithm finds a new arrangement of the connections through the middle subswitches A and B which includes all of the existing connections, plus the desired new connection.
Make a list of all of the desired connections that pass through A or B. That is, all of the existing connections to be maintained and the new connection. The algorithm proper only cares about the internal connections from input to output switch, although a practical implementation also has to keep track of the correct input and output switch connections.
In this list, each input subswitch can appear in at most two connections: one to subswitch A, and one to subswitch B. The options are zero, one, or two. Likewise, each output subswitch appears in at most two connections.
Each connection is linked to at most two others by a shared input or output subswitch, forming one link in a "chain" of connections.
Next, begin with the new connection. Assign it the path from its input subswitch, through middle subswitch A, to its output subswitch. If this first connection's output subswitch has a second connection, assign that second connection a path from its input subswitch through subswitch B. If that input subswitch has another connection, assign that third connection a path through subswitch A. Continue back and forth in this manner, alternating between middle subswitches A and B. Eventually one of two things must happen:
- the chain terminates in a subswitch with only one connection, or
- the chain loops back to the originally chosen connection.
In the first case, go back to the new connection's input subswitch and follow its chain backward, assigning connections to paths through middle subswitches B and A in the same alternating pattern.
When this is done, each input or output subswitch in the chain has at most two connections passing through it, and they are assigned to different middle switches. Thus, all the required links are available.
There may be additional connections through subswitches A and B which are not part of the chain including the new connection; those connections may be left as-is.
After the new connection pattern is designed in the software, then the electronics of the switch can actually be reprogrammed, physically moving the connections. The electronic switches are designed internally so that the new configuration can be written into the electronics without disturbing the existing connection, and then take effect with a single logic pulse. The result is that the connection moves instantaneously, with an imperceptible interruption to the conversation. In older electromechanical switches, one occasionally heard a clank of "switching noise."
This algorithm is a form of topological sort, and is the heart of the algorithm that controls a minimal spanning switch.
Practical implementations of switches
As soon as the algorithm was discovered, Bell system engineers and managers began discussing it. After several years, Bell engineers began designing electromechanical switches that could be controlled by it. At the time, computers used tubes and were not reliable enough to control a phone system (phone system switches are safety-critical, and they are designed to have an unplanned failure about once per thirty years). Relay-based computers were too slow to implement the algorithm. However, the entire system could be designed so that when computers were reliable enough, they could be retrofitted to existing switching systems.
It's not difficult to make composite switches fault-tolerant. When a subswitch fails, the callers simply redial. So, on each new connection, the software tries the next free connection in each subswitch rather than reusing the most recently released one. The new connection is more likely to work because it uses different circuitry.
Therefore, in a busy switch, when a particular PCB lacks any connections, it is an excellent candidate for testing.
To test or remove a particular printed circuit card from service, there is a well-known algorithm. As fewer connections pass through the card's subswitch, the software routes more test signals through the subswitch to a measurement device, and then reads the measurement. This does not interrupt old calls, which remain working.
If a test fails, the software isolates the exact circuit board by reading the failure from several external switches. It then marks the free circuits in the failing circuitry as busy. As calls using the faulty circuitry are ended, those circuits are also marked busy. Some time later, when no calls pass through the faulty circuitry, the computer lights a light on the circuit board that needs replacement, and a technician can replace the circuit board. Shortly after replacement, the next test succeeds, the connections to the repaired subswitch are marked "not busy," and the switch returns to full operation.
The diagnostics on Bell's early electronic switches would actually light a green light on each good printed circuit board, and light a red light on each failed printed circuit board. The printed circuits were designed so that they could be removed and replaced without turning off the whole switch.
The eventual result was the Bell 1ESS. This was controlled by a CPU called the Central Control (CC), a lock-step, Harvard architecture dual computer using reliable diode–transistor logic. In the 1ESS CPU, two computers performed each step, checking each other. When they disagreed, they would diagnose themselves, and the correctly running computer would take up switch operation while the other would disqualify itself and request repair. The 1ESS switch was still in limited use as of 2012, and had a verified reliability of less than one unscheduled hour of failure in each thirty years of operation, validating its design.
Initially it was installed on long-distance trunks in major cities, the most heavily used parts of each telephone exchange. On the first Mother's Day that major cities operated with it, the Bell system set a record for total network capacity, both in calls completed, and total calls per second per switch. This resulted in a record for total revenue per trunk.
Digital switches
A practical implementation of a switch can be created from an odd number of layers of smaller subswitches. Conceptually, the crossbar switches of the three-stage switch can each be further decomposed into smaller crossbar switches. Although each subswitch has limited multiplexing capability, working together they synthesize the effect of a larger N×N crossbar switch.
In a modern digital telephone switch, application of two different multiplexer approaches in alternate layers further reduces the cost of the switching fabric:
- space-division multiplexers are something like the crossbar switches already described, or some arrangement of crossover switches or banyan switches. Any single output can select from any input. In digital switches, this is usually an arrangement of AND gates. 8000 times per second, the connection is reprogrammed to connect particular wires for the duration of a time slot. Design advantage: In space-division systems the number of space-division connections is divided by the number of time slots in the time-division multiplexing system. This dramatically reduces the size and expense of the switching fabric. It also increases the reliability, because there are far fewer physical connections to fail.
- time-division multiplexers each have a memory which is read in a fixed order and written in a programmable order (or vice versa). This type of switch permutes time-slots in a time-division multiplexed signal that goes to the space-division multiplexers in its adjacent layers. Design advantage: Time-division switches have only one input and output wire. Since they have far fewer electrical connections to fail, they are far more reliable than space-division switches, and are therefore the preferred switches for the outer (input and output) layers of modern telephone switches.
Practical digital telephonic switches minimize the size and expense of the electronics. First, it is typical to "fold" the switch, so that both the input and output connections to a subscriber-line are handled by the same control logic. Then, a time-division switch is used in the outer layer. The outer layer is implemented in subscriber-line interface cards (SLICs) in the local presence street-side boxes. Under remote control from the central switch, the cards connect to timing-slots in a time-multiplexed line to a central switch. In the U.S. the multiplexed line is a multiple of a T-1 line. In Europe and many other countries it is a multiple of an E-1 line.
The scarce resources in a telephone switch are the connections between layers of subswitches. These connections can be either time slots or wires, depending on the type of multiplexing. The control logic has to allocate these connections, and the basic method is the algorithm already discussed. The subswitches are logically arranged so that they synthesize larger subswitches. Each subswitch, and synthesized subswitch is controlled (recursively) by logic derived from Clos's mathematics. The computer code decomposes larger multiplexers into smaller multiplexers.
If the recursion is taken to the limit, breaking down the crossbar to the minimum possible number of switching elements, the resulting device is sometimes called a crossover switch or a banyan switch depending on its topology.
Switches typically interface to other switches and fiber optic networks via fast multiplexed data lines such as SONET.
Each line of a switch may be periodically tested by the computer, by sending test data through it. If a switch's line fails, all lines of a switch are marked as in use. Multiplexer lines are allocated in a first-in-first out way, so that new connections find new switch elements. When all connections are gone from a defective switch, the defective switch can be avoided, and later replaced.
As of 2018, such switches are no longer made. They are being replaced by high-speed Internet Protocol routers.
Example of rerouting a switch
See also
References
- Clos, Charles (Mar 1953). "A study of non-blocking switching networks" (PDF). Bell System Technical Journal. 32 (2): 406–424. doi:10.1002/j.1538-7305.1953.tb01433.x. ISSN 0005-8580. Retrieved 22 March 2011.
https://en.wikipedia.org/wiki/Nonblocking_minimal_spanning_switch
The Panel Machine Switching System is a type of automatic telephone exchange for urban service that was used in the Bell System in the United States for seven decades. The first semi-mechanical types of this design were installed in 1915 in Newark, New Jersey, and the last were retired in the same city in 1983.
The Panel switch was named for its tall panels which consisted of layered strips of terminals. Between each strip was placed an insulating layer, which kept each metal strip electrically isolated from the ones above and below. These terminals were arranged in banks, five of which occupied an average selector frame. Each bank contained 100 sets of terminals, for a total of 500 sets of terminals per frame.[1] At the bottom, the frame had two electric motors to drive sixty selectors up and down by electromagnetically controlled clutches. As calls were completed through the system, selectors moved vertically over the sets of terminals until they reached the desired location, at which point the selector stopped its upward travel, and selections progressed to the next frame, until finally, the called subscriber's line was reached.
History
In c. 1906, AT&T organized two research groups for solving the unique challenges in switching telephone traffic in the large urban centers in the Bell System. Large cities had a complex infrastructure of manual switching that prevented complete ad hoc conversion to mechanical switching, but more favorable economics was anticipated from conversion to mechanical operation. No satisfactory methods existed for interconnecting manual systems with machines for switching. The two groups at the Western Electric Laboratories focussed on different technologies, using a competitive development approach to stimulate invention and increase product quality, a concept that had been successful at AT&T previously in transmitter design.[2] One group continued existing work that yielded the Rotary system, while the second group developed a system that was based on linear movement of switch components, which became known as the panel bank. As work continued, many subassemblies were shared, and the two switches only distinguished themselves in the switching mechanisms.
By 1910, the design of the Rotary system had progressed farther and internal trials employed it at Western Electric as a private branch exchange (PBX). However, by 1912, the company had decided that the panel system showed better promise to solve the large-city problem, and delegated the use of the Rotary system for use in Europe to satisfy the growing demand and competition from other vendors there, under the management and manufacture by the International Western Electric Company in Belgium.[3]
After a trial installation as a PBX within Western Electric in 1913, Panel system planning commenced with design and construction of field trial central offices using a semi-mechanical method of switching, in which subscribers still used telephones without a dial, and operators answered calls and keyed the destination telephone number into the panel switch, which then completed the call automatically.[4]
These first panel-type exchanges were placed in service in Newark, New Jersey,[5] on January 16, 1915 at the Mulberry central office serving 3640 subscribers, and on June 12 in the Waverly central office, which had 6480 lines. Panel development continued throughout the rest of the 1910s and in the 1920s in the United States. A third system in Newark (Branch Brook) followed in April 1917 for testing automatic call distribution.
The first fully machine-switching Panel systems using common control principles were the Douglas and Tyler exchanges in Omaha, Nebraska, completed in December 1921. Subscribers were issued new telephones with dials, that permitted the subscriber to place local calls without operator assistance. This installation was followed by the first installations in the eastern region in the Sherwood and Syracuse-2 central offices in Paterson, New Jersey, in May and July 1921, respectively.[6] The storied Pennsylvania exchange in New York City was cut-over to service in October 1922.[4][7]
Most Panel installations were replaced by modern systems during the 1970s. The last Panel switch, located in the Bigelow central office in Newark, was decommissioned by 1983.[8]
Operational overview
When a subscriber removes the receiver (earpiece) from the hookswitch of a telephone, the local loop circuit to the central office is closed. This causes the flow of current through the loop and a line relay, which causes the relay to operate, starting a selector in the line finder frame to hunt for the terminal of the subscriber's line. Simultaneously, a sender is selected, which provides dial tone to the caller once the line is found. The line finder then operates a cutoff relay, which prevents that telephone from being called, should another subscriber happen to dial the number.
Dial tone confirms to the subscriber that the system is ready for dialing. Depending on the local numbering system, the sender required either six or seven digits in order to complete the call. As the subscriber dialed, relays in the sender counted and stored the digits for later usage. As soon as the two, or three digits of the office code were dialed and stored, the sender performed a lookup against a translator (early-type) or decoder (later-type). The translator or decoder took the two or three digits as input, and returned data to the sender that contained the parameters for connecting to the called central office. After the sender received the data provided by the translator or decoder, the sender used this information to guide the district selector and office selector to the location of the terminals that would connect the caller to the central office where the terminating line was located. The sender also stored and utilized other information pertaining to the electrical requirements for signaling over the newly established connection, and the rate at which the subscriber should be billed, should the call successfully complete.
On the district or office selectors themselves, idle outgoing trunks were picked by the "sleeve test" method. After being directed by the sender to the correct group of terminals corresponding to the outgoing trunks to the called office, the selector continued moving upward through a number of terminals, checking for one with an un-grounded sleeve lead, then selecting and grounding it. If all the trunks were busy, the selector hunted to the end of the group, and finally sent back an "all circuits busy" tone. There was no provision for alternate routing as in earlier manual systems and later more sophisticated mechanical ones.
Once the connection to the terminating office was established, the sender used the last four (or five) digits of the telephone number to reach the called party. It did so by converting the digits into specific locations on the remaining incoming and final frames. After the connection was established all the way to the final frame, the called party's line was tested for busy. If the line was not busy, the incoming selector circuit sent ringing voltage forward to the called party's line and waited for the called party to answer their telephone. If the called party answered, supervision signals were sent backwards through the sender, and to the district frame, which established a talking path between both subscribers, and charged the calling party for the call. At this time, the sender was released, and could be used again in service of an entirely new call. If the called subscriber's line was busy, the final selector sent a busy signal back to the called party to alert them that the caller was on the phone and could not accept their call.
Telephone numbering
As in the Strowger system, each central office could address up to 10,000 numbered lines (0000 to 9999), requiring four digits for each subscriber station.
The panel system was designed to connect calls in a local metropolitan calling area. Each office was assigned a two- or three-digit office code, called an office code, which indicated to the system the central office in which the desired party was located. Callers dialed the office code followed by the station number. In larger cities, such as New York City, dialing required a three-digit office code,[9] and in less-populated cities, such as Seattle, WA[10] and Omaha, NE, a two-digit code. The remaining digits of the telephone number corresponded to the station number, which pointed to the physical location of the subscriber's telephone on the final frame of the called office. For instance, a telephone number may be listed as PA2-5678, where PA2 (722) is the office code and 5678 is the station number.
In areas that served party lines, the system accepted an additional digit for party identification. This allowed the sender to direct the final selector not only to the correct terminal, but to ring the correct subscriber's line on that terminal. The panel system supported individual, 2-party, and 4-party lines.
Circuit features
Similar to the divided-multiple telephone switchboard, the panel system was divided into an originating section and a terminating section. The subscriber's line had two appearances in a local office: one on the originating side, and one on the terminating side. The line circuit consisted of a line relay on the originating side to indicate that a customer had gone off-hook, and a cutoff relay to keep the line relay from interfering with an established connection. The cutoff relay was controlled by a sleeve lead that, as with the multiple switchboard, could be activated by either the originating section or the terminating. On the terminating end, the line circuit was connected to a final selector, which was used in call completion. Thus, when a call was completed to a subscriber, the final selector circuit connected to the desired line, and then performed a sleeve (busy) test. If the line was not busy, the final selector operated the cut-off relay via the sleeve lead, and proceeded to ring the called subscriber.
Supervision (line signaling) was supplied by a District circuit, similar to the cord circuit that plugged into a line jack on a switchboard. The District circuit supervised the calling party, and when the calling party went on-hook, it released the ground on the sleeve lead, thus releasing all selectors except the final, which returned down to their start position to make ready for further traffic. The final selector circuit was not supervised by the district circuit, and only returned to normal once the called party hung up.[11] Some District frames were equipped with the more complex supervisory and timing circuits required to generate coin collect and return signals for handling calls from payphones.
Many of the urban and commercial areas where Panel was first used had message rate service rather than flat rate calling. For this reason the line finder had a fourth wire known as the "M" lead. This enabled the District circuit to send metering pulses to control the subscriber's message register. The introduction of direct distance dialing (DDD) in the 1950s required the addition of automatic number identification equipment for centralized automatic message accounting.
The terminating section of the office was fixed to the structure of the last four digits of the telephone number, had a limit of 10,000 phone numbers. In some of the urban areas where Panel was used, even a single square mile might have three or five times that many telephone subscribers. Thus the incoming selectors of several separate switching entities shared floor space and staff, but required separate incoming trunk groups from distant offices. Sometimes an Office Selector Tandem was used to distribute incoming traffic among the offices. This was a Panel office with no senders or other common control equipment; just one stage of selectors and accepting only the Office Brush and Office Group parameters. Panel Sender Tandems were also used when their greater capabilities were worth their additional cost.
Sender
While the Strowger (step-by-step) switch moved under direct control of dial pulses that came from the telephone dial, the more sophisticated Panel switch had senders, which registered and stored the digits that the customer dialed, and then translated the received digits into numbers appropriate to drive the selectors to their desired position: District Brush, District Group, Office Brush, Office Group, Incoming Brush, Incoming Group, Final Brush, Final Tens, Final Units.
The use of senders provided advantages over the previous direct control systems, because they allowed the office code of the telephone number to be decoupled from the actual location on the switching fabric. Thus, an office code (for example, "722") had no direct relationship to the physical layout of the trunks on the district and office frames. By the usage of translation, the trunks could be located arbitrarily on the physical frames themselves, and the decoder or translator could direct the sender to their location as needed. Additionally, because the sender stored the telephone number dialed by the subscriber, and then controlled the selectors itself, there was no need for the subscriber's dial to have a direct-control relationship to the selectors themselves. This allowed the selectors to hunt at their own speed, over large groups of terminals, and allowed for smooth, motor controlled motion, rather than the staccato, momentary motion of the step-by-step system.
The sender also provided fault detection. As it was responsible for driving the selectors to their destinations, it was able to detect errors (known as trouble) and alert central office staff of the problem by lighting a lamp at the appropriate panel. In addition to lighting a lamp, the sender held itself and the selectors that were under its control out of service, which prevented their use by other callers. Upon noting the alarm condition, staff could inspect the sender and its associated selectors, and resolve whatever trouble occurred before returning the sender and selectors back to service.
When the sender's job was complete, it connected the talk path from the originating to the terminating side, and dropped out of the call. At this time, the sender was available to handle another subscriber's call. In this way, a comparatively small number of senders could handle a large amount of traffic, as each was only used for a short duration during call setup. This principle became known as common control, and was used in all subsequent switching systems.
Signaling and control
Revertive Pulsing (RP) was the primary signaling method used within and between panel switches. The selectors, once seized by the sender or another selector, would begin moving upwards under motor power. Each terminal the selector passed would send a pulse of ground potential along the circuit, back to the sender. The sender counted each pulse, and when the correct terminal was reached, the sender then signalled the selector to disengage the upward drive clutch and stop on the appropriate terminal as determined by the sender and decoder. The selector then either began its next selection operation, or extended the circuit to the next selector frame. In the case of the final frame, the last selection would result in connection to an individual's phone line and would begin ringing.
As the selectors were driven upwards by the motors, brushes attached to the vertical selector rods wiped over commutators at the top of the frame. These commutators contained alternating segments serving as insulators or conductors. When the brush passed over a conductive segment, it was grounded, thereby generating a pulse which was sent back to the sender for counting. When the sender counted the appropriate number of pulses, it cut the power to the solenoid in the terminating office, and caused the brush to stop at its current position.
Calls from one panel office to another worked very similarly to calls within an office by use of revertive pulse signalling. The originating office used the same protocol, but inserted a compensating resistance during pulsing so its sender encountered the same resistance for all trunks.[12] This is in contrast to more modern forms of forward pulsing, where the originating equipment will directly outpulse to the terminating side the information it needs to connect the call.
Compatibility
Later systems maintained compatibility with revertive pulsing, even as more advanced signaling methods were developed. The Number One Crossbar, which was the first successor to the Panel system also used this method of signaling exclusively, until later upgrades introduced newer signaling such as Multi-frequency signaling.
Panel was initially installed in cities where many stations still used manual (non-dial) service. For compatibility with manual offices, two types of signaling were supported. In areas with mostly machine switches and only a few manual switchboards, Panel Call Indicator (PCI) signaling transmitted the called number to the "B" Board Machine Incoming operator, which lit lamps on the operator's desk at the terminating manual office. The lamps illuminated digits on a display panel corresponding to the number dialed. The manual operator connected the call to the appropriate jack, and then repeated the process for the next incoming call. In areas with mostly manual switches, the Call Annunciator signaling system was used to avoid installing lamp panels at every operator station. The Call Annunciator used speech recorded on strips of photographic film to verbally announce the called number to the answering operator.
PCI signaling continued to be used for tandem purposes, decades after its original need had disappeared. In the 1950s, auxiliary senders were added for storing more than eight digits, and sending by multi-frequency (MF) signaling for direct distance dialing (DDD).
Calls from manual offices to panel offices required the "A" board, or outgoing operator, to request the number from the caller, connect to an idle trunk to the distant exchange, and relay the desired number to the B Board Manual Incoming Call operator, who keyed it to the Panel machine for setting up the incoming and final frames to the called telephone number.
Motor power
The panel switch is an example of a power drive system, in that it used 1/16 horsepower motors to drive the selectors vertically to hunt for the desired connection, and back down again when the call was completed. In contrast, Strowger or crossbar systems used individual electromagnets for operation, and in their case the power available from an electromagnet limits the maximum size of the switch element it can move. With Panel having no such restriction, its dimensions were determined solely by the needs of the switch, and the design of the exchange. The driving electric motor can be made as large as is necessary to move the switch elements. Thus, most calls required only about half as many stages as in earlier systems. Motors used on panel frames were capable of operating on alternating (AC) or direct current (DC), however they could only be started with DC. In the event of an AC power failure the motor would switch to its DC windings, and continue running until AC power was restored.
Maintenance and testing
Because of its relative complexity compared to direct control systems, the Panel system incorporated many new types of testing apparatus. At the time of its design, it was decided that maintenance should be done on a preventative basis, and regular testing of the equipment would be used to identify faults before they became severe enough to affect subscribers. To this end, multiple types of test equipment were provided.[13] Test equipment generally took the form of either a wooden, switchboard-like desk, a wheeled cart, known as a "Tea Wagon", or a small box-type test set that could be carried to the apparatus that required testing. The central test location in the office was known as the "OGT Desk", or "Trouble Desk", and took the form of a large wooden desk with lamps, jacks, keys, cords, and a voltmeter. This desk served as the central point for analysis and trouble resolution.
Other test apparatus included frame-mounted equipment that was used to routine commonly used circuits within the office. These included an automatic routine sender test frame, and an automatic routine selector test frame. When testing was to be done manually by a switchman, he or she used a Tea Wagon, which was wheeled to the apparatus to be tested, and plugged into jacks that were provided for this purpose.
Upgrades
Throughout its service time, the Panel system was upgraded as new features became available or necessary. Starting in the mid-1920s, such upgrades improved the initial design. Major attention was initially focused on improving the sender. Early two- and three-digit type senders stored dialed digits on rotary selector switches. The senders employed translators to convert the dialed digits into the appropriate brush and group selections needed to complete the call. As better technology became available, Panel senders were upgraded to the all-relay type. These were more reliable, and in addition, replaced the translator equipment with decoders, which also operated entirely with relays, rather than with motor-driven apparatus, which yielded faster call completion, and required less maintenance.
Another important improvement involved a fundamental change in the electrical logic of the switching system. The Panel originally shipped in a ground cut-off (GCO) configuration, wherein the cut-off relay had ground potential on one side of its winding at all times. A busy line condition was indicated by -48 volt battery applied to the other side of the cut-off relay winding, and thus at the sleeve lead. This would be detected by the final selector as it hunted over the terminals. Starting in 1929, all newer panel systems were deployed as battery cut-off (BCO) systems.[14] In this revision, the presence of ground and -48V was reversed. Battery was constantly applied to one side of the cut-off relay, and the presence of ground on the other side of the winding indicated the line was busy. This change necessitated a fundamental change in the design of the system, and was undertaken for many reasons. One of the most notable was that GCO offices were more prone to fire.[15]
The line finder was also improved during the system's lifetime. Originally, the line finder frame had a capacity of 300 lines each, and used 15 brushes (vertical hunting segments) on each rod. This was intended to reduce hunting time as there were more brushes hunting over a shorter distance. As these line finders went into service, however, it became evident that 15 brushes on each vertical selector rod were quite heavy, and needed springs and pulleys at the top of the frame to compensate for their mass. Later line finders used 10 brushes and rearranged the layout to accommodate 400 lines per line finder frame. This increased capacity while eliminating the need for compensating equipment.
Western Electric estimated that the design changes of 1925 to 1927 accounted for a 60% reduction in overall costs for the Panel system.[15]
The following table presents early major panel system upgrades:[16]
| Year | Line finder type | Sender connection type | Maximum number of senders per group |
Sender type | Cut-off relay type |
|---|---|---|---|---|---|
| 1920 | Line Switch (200-type) | Sender Selector | 22 | Translator | GCO |
| 1920 | 300 pt line finder | Sender Selector | 22 | Translator | GCO |
| 1924 | 400 pt line finder | Sender Selector | 22 | Translator | GCO |
| 1926 | 400 pt line finder | Rotary Link | 44 | Translator | GCO |
| 1927 | 400 pt line finder | Panel Link | 100 | Translator | GCO |
| 1928 | 400 pt line finder | Panel Link | 100 | Decoder | GCO |
| 1929 | 400 pt line finder | Panel Link | 100 | Decoder | BCO |
References
- The Panel Dial System Traffic Layouts. Western Electric Company, Inc. 1937. p. 2.
External links
- Call switching by panel switch at the Seattle Museum of Communications.
- Archive Footage of early panel system.
- Survey of telephone switching
- Phone Trips: 1970s-era recordings of telephone calls involving panel switches by Evan Doorbell.
- MP3 recording of revertive pulsing, followed by machine ringing and the clicks of the Panel test line.
- Panel Dial Office Photos and Videos. Over 150. IDF, MDF, Power, Panel Equipment, Test Frames
https://en.wikipedia.org/wiki/Panel_switch
Reference Computer is a computerized supplement to PBX (Private Branch Exchange or PBX) that supports the internal telephone directory, absence data and messages. Reference Computer is an effective aid for the switchboard operator as information on the lines are obtained directly from a display.
Reference computer is connected to the telephone exchange and a call comes in to an extension the computer shows all the data about that extension automatically. Reference computer enabled a sophisticated information management in large companies. People in the workplace could from their phones enter information about absences cause and time of return simply by entering certain digits on his telephone apparatus.
The first complete reference computer attached to PBX in the Swedish Telecom company's network had the name SESAM and came in operation in the early 1980s. It was associated initially with company's electromechanical telephone A344 (and thus gave it a host of new modern services).
The big break for reference computer, which is a Swedish invention, came when the telephone service's large "electronic PBX" A345 and A335 were provided with a reference computer (HVD). Several such existed in the Swedish market. SESAM system was first developed and marketed, then from the mid-1980s, known as PRESENT. These two systems were developed by four engineers from the telephone company who has obtained a Swedish patent for the invention. The patent was declared invalid in 1991 after the telephone company itself had sought annulment in the Stockholm District Court and the Svea Court of Appeal. State Board of Workers' inventions (SNAU) stated that it was a recommendation that the four engineers of the telephone company would hold SEK 3 million by the employer. Televerket and TeliaSonera AB has however refused to pay compensation. Subsequently, SNAU twice considered the question if the inventors are entitled to compensation. The issue is not yet finally settled by SNAU. The dispute has lasted for over 30 years. Reference computers and direct function in the newer PBX contributed to the rationalization of the telecom network. There is now a reference feature in the software in most modern PBX.
References
- "Televerkets årsberättelse år 1984"
- "Televerkets historia, 1997"
- "Thorpoulf Arwidson, Arbetstagares rätt till uppfinningar, RECITO, 2012
https://en.wikipedia.org/wiki/Reference_computer
SP-1 (Stored Program 1) was the name of a computerized telephone exchange (a so-called switching office) manufactured by Northern Electric (later Northern Telecom and now Nortel Networks beginning in 1972) in Canada. It was introduced in 1971 (as stated in a Northern Telecom print ad that is included (page 55) in a history of Nortel, written by Peter C. Newman who was commissioned by Nortel to write it. Copyright is 1995. No ISBN.)
As indicated by the name "Stored Program", the SP-1 introduced computer control to the telephone switching market. (AT&T's #1ESS preceded the SP-1 by several years.)
A central computer controlled the operation of the switch. Switch behavior was determined by the operation of a computer program.
With its use of computer hardware and software control, the SP-1 marked an evolutionary step in telephony design. It was an intermediate form between the previous generation of electromechanical systems and the next generation of fully digital systems. Like the previous generation of systems, the SP-1 was an analog switch that used a special form of mechanical relay (Minibar crossbar switch) to provide the voice connections. The voice signal remained in the analog domain throughout the exchange, with the crossbar switches providing a metallic path to connect the end points of a call together. However the SP1 replaced the previous generation's complex relay-based controllers (markers) with a modern Harvard architecture electronic computer, with separate data and program memories. SSI DTL logic was used throughout. Two types of memory was used - ferrite sheet memory for the CPU and Piggyback Twistor memory for the storage of program and routing information. A number of variations on the base switch were available. A "two wire" version for local service, a four wire version for toll service. Two/four wire versions were also available as was a TOPS variant that was used to provide Operator services. The first four wire switch (four wire-tops, i.e., it provided toll switching and operator services) was placed in service in Thunder Bay circa 1972. The operator service consoles (CRTs) used an Intel 4004 processor.
The next generation of systems evolved from the SP1 design to replace the analog switch with a digital technology. SP-1 proved the feasibility of software-controlled systems for telephony. It set the stage for the introduction of fully digital systems with the development of the DMS (Digital Multiplex Systems) by Nortel in the 1970s. (Nortel's SL-1 (PBX) was Nortel's first fully digital switching system, and it was introduced in service in 1975.)
See also
- DMS-100
- Electronic Switching System
- 1ESS switch
- TXE
- Stored Program Control exchange
- SP-1 Technical Bulletin
https://en.wikipedia.org/wiki/SP-1_switch
System X is the digital switching system installed in telephone exchanges throughout the United Kingdom, from 1980 onwards.
History
Development
System X was developed by the Post Office (later to become British Telecom), GEC, Plessey, and Standard Telephones and Cables (STC), and was first shown in public in 1979 at the Telecom 79 exhibition in Geneva, Switzerland.[1] STC withdrew from the project in 1982. In 1988, the telecommunications divisions of GEC and Plessey merged to form GPT, with Plessey subsequently being bought out by GEC and Siemens. In the late 1990s, GEC acquired Siemens' 40% stake in GPT. GEC renamed itself Marconi in 1999.
When Marconi was sold to Ericsson in January 2006, Telent plc retained System X and continues to support and develop it as part of its UK services business.
Implementation
The first System X unit to enter public service was in September 1980 and was installed in Baynard House, London and was a 'tandem junction unit' which switched telephone calls amongst some 40 local exchanges. The first local digital exchange started operation in 1981 in Woodbridge, Suffolk (near BT's Research HQ at Martlesham Heath). The last electromechanical trunk exchange (in Thurso, Scotland) was closed in July 1990, completing the UK's trunk network transition to purely digital operation and becoming the first national telephone system to achieve this. The last electromechanical local exchanges, Crawford, Crawfordjohn and Elvanfoot, all in Scotland, were changed over to digital on 23 June 1995 and the last electronic analogue exchanges, Selby, Yorkshire and Leigh on Sea, Essex were changed to digital on 11 March 1998.
In addition to the UK, System X was installed in the Channel Islands and several systems were installed in other countries, although it never achieved significant export sales.
Small exchanges: UXD5
Separately from System X, BT developed the UXD5 ("unit exchange digital"), a small digital exchange which was cost-effective for small and remote communities. Developed by BT at Martlesham Heath and based on the Monarch PABX, the first example was put into service at Glenkindie, Scotland, in 1979, the year before the first System X.[2] Several hundred of these exchanges were manufactured by Plessey[3] and installed in rural areas, largely in Scotland and Wales. The UXD5 was included as part of the portfolio when System X was marketed to other countries.
System X units
System X covers three main types of telephone switching equipment. Many of these switches reside all over the United Kingdom. Concentrators are usually kept in local telephone exchanges but can be housed remotely in less populated areas. DLEs and DMSUs operate in major towns and cities and provide call routing functions. The BT network architecture designated exchanges as DLEs / DMSUs / DJSUs etc. but other operators configured their exchanges differently depending on their network architecture.
With the focus of the design being on reliability, the general architectural principle of System X hardware is that all core functionality is duplicated across two 'sides' (side 0 and side 1). Either side of a functional resource can be the 'worker' with the other being an in-service 'standby'. Resources continually monitor themselves and should a fault be detected the associated resource will mark itself as 'faulty' and the other side will take the load instantaneously. This resilient configuration allows for hardware changes to fix faults or perform upgrades without interruption to service. Some critical hardware such as switchplanes and waveform generators are triplicated and work on an 'any 2 out of 3' basis. The CPUs in an R2PU processing cluster are quadruplicated to retain 75% performance capability with one out of service instead of 50% if they were simply duplicated. The SystemX processing system was the first multi-processor cluster in the world [requires confirmation]. Line cards providing customer line ports or the 2Mbps E1 terminations on the switch have no 'second side' redundancy, but of course a customer can have multiple lines or an interconnect have multiple E1s to provide resilience.
Concentrator unit
The concentrator unit consists of four main sub-systems: line modules, digital concentrator switch, digital line termination (DLT) units and control unit. Its purpose is to convert speech from analogue signals to digital format, and concentrate the traffic for onward transmission to the digital local exchange (DLE). It also receives dialled information from the subscriber and passes this to the exchange processors so that the call can be routed to its destination. In normal circumstances, it does not switch signals between subscriber lines but has limited capacity to do this if the connection to the exchange switch is lost.
Each analogue line module unit converts analogue signals from a maximum of 64 subscriber lines in the access network to the 64 kilobit/s digital binary signals used in the core network. This is done by sampling the incoming signal at a rate of 8 kS/s and coding each sample into an 8-bit word using pulse-code modulation (PCM) techniques. The line module also strips out any signalling information from the subscriber line, e.g., dialled digits, and passes this to the control unit. Up to 32 line modules are connected to a digital concentrator switch unit using 2 Mbit/s paths, giving each concentrator a capacity of up to 2048 subscriber lines. The digital concentrator switch multiplexes the signals from the line modules using time-division multiplexing and concentrates the signals onto up to 480 time slots on E1s up to the exchange switch via the digital line termination units. The other two time slots on each channel are used for synchronisation and signalling. These are timeslots 0 and 16 respectively.
Depending on hardware used, concentrators support the following line types: analogue lines (either single or multiple line groups), ISDN2 (basic rate ISDN) and ISDN30 (primary rate ISDN). ISDN can run either UK-specific DASS2 or ETSI(euro) protocols. Subject to certain restrictions a concentrator can run any mix of line types, this allows operators to balance business ISDN users with residential users to give a better service to both and efficiency for the operator.
Concentrator units can either stand alone as remote concentrators or be co-located with the exchange core (switch and processors).
Digital local exchange
The Digital Local Exchange (DLE) hosts a number of concentrators and routes calls to different DLEs or DMSUs depending on the destination of the call. The heart of the DLE is the Digital Switching Subsystem (DSS) which consists of Time Switches and a Space Switch. Incoming traffic on the 30 channel PCM highways from the Concentrator Units is connected to Time Switches. The purpose of these is to take any incoming individual Time Slot and connect it to an outgoing Time Slot and so perform a switching and routing function. To allow access to a large range of outgoing routes, individual Time Switches are connected to each other by a Space Switch. The Time Slot inter-connections are held in Switch Maps which are updated by Software running on the Processor Utility Subsystem (PUS). The nature of the Time Switch-Space Switch architecture is such that the system is very unlikely to be affected by a faulty time or space switch, unless many faults are present. The switch is a 'non-blocking' switch.
Digital main switching unit
The Digital Main Switching Unit (DMSU) deals with calls that have been routed by DLEs or another DMSU and is a 'trunk / transit switch', i.e. it does not host any concentrators. As with DLEs, DMSUs are made up of a Digital Switching Subsystem and a Processor Utility Subsystem, amongst other things. In the British PSTN network, each DMSU is connected to every other DMSU in the country, enabling almost congestion-proof connectivity for calls through the network. In inner London, specialised versions of the DMSU exist and are known as DJSU's - they are practically identical in terms of hardware - both being fully equipped switches, the DJSU has the distinction of carrying inter-London traffic only. The DMSU network in London has been gradually phased out and moved onto more modern "NGS" switches over the years as the demand for PSTN phone lines has decreased as BT has sought to reclaim some of its floor-space. The NGS switch referred to is a version of Ericsson's AXE10 product line, phased in between the late '90s and early '00s.
It is common to find multiple exchanges (switches) within the same exchange building in large UK cities: DLEs for the directly-connected customers and a DMSU to provide the links to the rest of the UK.
Processor utility subsystem
The Processor Utility Subsystem (PUS) controls the switching operations and is the brain of the DLE or DMSU. It hosts the Call Processing, Billing, Switching and Maintenance applications Software (amongst other software subsystems). The PUS is divided into up to eight 'clusters' depending on the amount of telephony traffic dealt with by the exchange. Each of the first four clusters of processors contains four central processing units (CPUs), the main memory stores (STRs) and the two types of backing store (primary (RAM) and secondary (hard disk)) memory. The PUS was coded with a version of the CORAL66 programming language known as PO CORAL (Post Office CORAL) later known as BTCORAL.
The original processor that went into service at Baynard house, London, was known as the MK2 BL processor. It was replaced in 1980 by the POPUS1 (Post Office Processor Utility Subsystem). POPUS1 processors were later installed in Lancaster House in Liverpool and also, in Cambridge. Later, these too were replaced with a much smaller system known as R2PU or Release 2 Processor Utility. This was the four CPU per cluster and up to 8-cluster system, as described above. Over time, as the system was developed, additional "CCP / Performance 3" clusters were added (clusters 5, 6, 7 and 8) using more modern hardware, akin to late-1990s computer technology, while the original processing clusters 0 to 3 were upgraded with, for example, larger stores (more RAM). The advanced features of this fault-tolerant system help explain why these are still in use today – like self fault detection and recovery, battery-backed RAM, mirrored disk storage, auto replacement of a failed memory unit, and the ability to trial new software (and roll back, if necessary) to the previous version. Later, the hard disks on the CCP clusters were replaced by with solid-state drives to improve reliability.
In modern times, all System X switches show a maximum of 12 processing clusters; 0–3 are the four-CPU System X-based clusters and the remaining eight positions can be filled with CCP clusters which deal with all traffic handling. Whilst the status quo for a large System X switch is to have four main and four CCP clusters, there are one or two switches that have four main and six CCP clusters. The CCP clusters are limited to call handling only, there was the potential for the exchange software to be re-written to accept the CCP clusters, but this was scrapped as being too costly of a solution to replace a system that was already working well. Should a CCP cluster fail, System X will automatically re-allocate its share of the call handling to another CCP cluster, if no CCP clusters are available then the exchange's main clusters will begin to take over the work of call handling as well as running the exchange.
In terms of structure, the System X processor is a "one master, many slaves" configuration – cluster 0 is referred to as the base cluster and all other clusters are effectively dependent to it. If a slave cluster is lost, then call handling for any routes or concentrators dependent to it is also lost; however, if the base cluster is lost then the entire exchange ceases to function. This is a very rare occurrence, as due to the design of System X it will isolate problematic hardware and raise a fault report. During normal operation, the highest level of disruption is likely to be a base cluster restart, all exchange functions are lost for 2–5 minutes while the base cluster and its slaves come back online, but afterwards the exchange will continue to function with the defective hardware isolated. The exchange can and will restart ('rollback') individual processes if it detects problems with them. If that doesn't work then a cluster restart can be performed. Should the base cluster or switch be irrecoverable via restarts, the latest archive configuration can be manually reloaded using the restoration procedure. This can take hours to bring everything fully back into service as the switch has to reload all its semi-permanent paths and the concentrators have to download their configurations. Post-2020, exchange software is being modified to reduce the restoration time significantly.
During normal operation, the exchange's processing clusters will sit between 5-15% usage, with the exception of the base cluster which will usually sit between 15-25% usage, spiking as high as 45% - this is due to the base cluster handling far more operations and processes than any other cluster on the switch.
Editions of System X
System X has gone through two major editions, Mark 1 and Mark 2, referring to the switch matrix used.
The Mark 1 Digital Subscriber Switch (DSS) was the first to be introduced. It is a time-space-time switch setup with a theoretical maximum matrix of 96x96 Time Switches. In practice, the maximum size of switch is a 64x64 Time Switch matrix. Each time switch is duplicated into two security planes, 0 and 1. This allows for error checking between the planes and multiple routing options if faults are found. Every timeswitch on a single plane can be out of service and full function of the switch can be maintained, however, if one timeswitch on plane 0 is out, and another on plane 1 is out, then links between the two are lost. Similarly, if a timeswitch has both plane 0 and 1 out, then the timeswitch is isolated. Each plane of the timeswitch occupies one shelf in a three-shelf group – the lower shelf is plane 0, the upper shelf is plane 1 and the middle shelf is occupied by up to 32 DLTs (Digital Line Terminations). The DLT is a 2048 kb/s 32-channel PCM link in and out of the exchange. The space switch is a more complicated entity, but is given a name ranging from AA to CC (or BB within general use), a plane of 0 or 1 and, due to the way it is laid out, an even or odd segment, designated by another 0 and 1. The name of a space switch in software, then, can look like this. SSW H'BA-0-1. The space switch is the entity that provides the logical cross connection of traffic across the switch, and the time switches are dependent to it. When working on a space switch it is imperative to make sure the rest of the switch is healthy as, due to its layout, powering off either the odd or even segment of a space switch will "kill" all of its dependent time switches for that plane. Mark 1 DSS is controlled by a triplicated set of Connection Control Units (CCU's) which run in a 2/3 majority for error checking, and is monitored constantly by a duplicated Alarm Monitoring Unit (AMU) which reports faults back to the DSS Handler process for appropriate action to be taken. The CCU and AMU also play part in diagnostic testing of Mark 1 DSS.
A Mark 1 System X unit is built in suites, each 8 racks in length, and there can be 15 or more suites. Considerations of space, power demand and cooling demand led to development of the Mark 2.
Mark 2 DSS ("DSS2") is the later revision, which continues to use the same processor system as Mark 1, but made serious and much needed revisions to both the physical size of the switch and the way that the switch functions. It is an optical fibre-based time-space-time-space-time switching matrix, connecting a maximum of 2048 2Mbps PCM systems, much like Mark 1; however the hardware is much more compact.
The four-rack group of the Mk1 CCU and AMU is gone, and replaced neatly by a single connection control rack, comprising the Outer Switch Modules (OSMs), Central Switch Modules (CSMs) and the relevant switch/processor interface hardware. The Timeswitch shelves are replaced with Digital Line Terminator Group (DLTG) shelves, which each contain two DLTGs, comprising 16 Double Digital Line Termination boards (DDLTs) and two Line Communication Multiplexors (LCMs), one for each security plane. The LCMs are connected by optical fibre over a forty megabit link to the OSMs. In total, there are 64 DLTG's in a fully sized Mk2 DSS unit, which is analogous to the 64 Time Switches of the Mk1 DSS unit. The Mk2 DSS unit is a lot smaller than the Mk1, and as such consumes less power and also generates less heat to be dealt with as a result. It is also possible to interface directly with SDH transmission over fibre at 40Mbps, thus reducing the amount of 2Mbps DDF and SDH tributary usage. Theoretically, a transit switch (DMSU) could purely interface with the SDH over fibre with no DDF at all. Further to this, due to the completely revised switch design and layout, the Mk2 switch manages to be somewhat faster than the Mk1 (although the actual difference is negligible in practice). It is also far more reliable, having many less discrete components in each of its sections means there is much less to go wrong, and when something does go wrong it is usually a matter of replacing the card tied to the software entity that has failed, rather than needing to run diagnostics to determine possible locations for the point of failure as is the case with Mk1 DSS.
Message Transmission Subsystem
A System X exchange's processors communicate with its concentrators and other exchanges using its Message Transmission subsystem (MTS). MTS links are 'nailed up' between nodes by re-purposing individual 64kbps digital speech channels across the switch into permanent paths for the signalling messages to route over. Messaging to and from concentrators is done using proprietary messaging, messaging between exchanges is done using C7 / SS7 messaging. UK-specific and ETSI variant protocols are supported. It was also possible to use channel associated signalling, but as the UK and Europe's exchanges went digital in the same era this was hardly used.
Replacement system
Many of the System X exchanges installed during the 1980s continue in service into the 2020s.
System X was scheduled for replacement with Next Generation softswitch equipment as part of the BT 21st Century Network (21CN) programme. Some other users of System X – in particular Jersey Telecom and Kingston Communications – replaced their circuit-switched System X equipment with Marconi XCD5000 softswitches (which were intended as the NGN replacement for System X) and Access Hub multiservice access nodes. However, the omission of Marconi from BT's 21CN supplier list and the shift in focus away from telephony to broadband all led to much of the System X estate being maintained.
See also
References
- "History of Plessey". www.britishtelephones.com. Retrieved 27 May 2021.
https://en.wikipedia.org/wiki/System_X_(telephony)
BT Fusion was a telecommunications product available from BT Group in the United Kingdom[1] until 1 April 2009 when it was withdrawn. It "fused" together mobile telephony and, from the user's point of view, conventional landline telephony. In fact, the fixed portion of the link was provided by a Voice over IP implementation using the domestic ADSL service. The BT Fusion service was compatible with the BT Smart Hub.[citation needed]
The premise of the service was that it could reduce mobile phone costs by not using the mobile network when the user is at home. The same phone was used (a modified version of the Motorola RAZR or Motorola V560), but if the phone was within range of a special base station installed in the user's home or office then incoming and outgoing calls will be routed through that base station instead of the mobile network. This link between the phone and base station was carried over Bluetooth (BT Fusion was latterly available using Wifi technology, thus allowing discounts not only at home but over BT Openzone WiFi hotspots). BT Fusion was an example of one type of telecommunication convergence.[citation needed]
From the base station, at-home calls were connected to the phone network using an ADSL broadband connection; only those with BT Broadband connections were eligible for the service. Voice over IP protocols were used to transmit the call, but this was intended to remain largely unnoticed from the user's point of view. In particular, the charges for calls made over the "home" part of a BT Fusion system were essentially the same as landline call charges.[citation needed]
Some commentators criticised the service as expensive and a "solution in search of a problem". In particular, they pointed to free or cheaper-than-landline IP phone systems like Skype.[citation needed]
References
- "BT 'BluePhone' Fusion is better than Skype because...?", The Register, 15 June 2005
External links
- BT site
- "BT 'BluePhone' Fusion is better than Skype because...?", The Register, 15 June 2005
https://en.wikipedia.org/wiki/BT_Fusion
BT Mobile is a mobile virtual network operator (MVNO) provided by BT Consumer; a division of BT Group in the United Kingdom that was launched in March 2015.[1] It uses the EE network[2] via an MVNO agreement signed in March 2014[3] as well as using the spectrum BT won in the 2013 4G auction.[4][5] EE is now owned by BT following a successful acquisition that was officially completed on 29 January 2016.[6][7] BT Mobile operates alongside BT Business Mobile which is provided by the BT Business and Public Sector division. BT Mobile launched as a SIM-only service and had more than 400,000 customers as of 5 May 2016.[8]
Products
SIM-only plans
BT Mobile is a full fledged mobile service with handsets and sim only offers four 12-month contract plans as of 7 November 2020:
- BT Mobile 500MB Plan - 500MB of data, 500 minutes and unlimited texts
- BT Mobile 10GB Plan - 10GB of data, 1000 minutes and unlimited texts
- BT Mobile 16GB Plan - 16GB of data, unlimited minutes and texts
- BT Mobile 20GB Plan - 20GB of data, unlimited minutes and texts
- BT Mobile 30GB Plan - 30GB of data, unlimited minutes and texts
- BT Mobile 100GB - 100GB of data, unlimited minutes and texts
Anyone living in a BT Broadband home are eligible for a £5 monthly discount on all BT Mobile plans - each account holder can have up to five discounted plans but there's no limit to the number of people in a house that can take up the offer.[9][10]
Features
BT Sport
Subscribers to BT Mobile can watch BT Sport through the dedicated mobile streaming app. However, watching BT Sport via television still requires a paid subscription.
BT Wi-Fi
Subscribers to BT Mobile have unlimited access to BT Wi-Fi, regardless of the data allowance in their contract. Connection to BT Wi-Fi can be made through an internet browser or the dedicated BT Wi-Fi application.
BT Mobile App
The BT Mobile app allows a subscriber to keep on top of their contract allowance, allowing them to see their minutes, texts and remaining data allowance. The app also shows outwith contract spending, details of the consumers contract and information on data roaming.
Services
Network
BT Mobile offers 4G as standard to all customers at no extra cost and in order to benefit from 4G speeds, a 4G-ready phone is required. However, customers in areas with no 4G coverage or without a 4G-ready phone will still be able to connect via the 3G and 2G networks.[11]
Coverage
As BT Mobile uses the EE network, its 4G network reaches more than 95% of the UK population while its 3G network reaches 98% and 2G network reaches 99%.[12][13]
Extra Speed 4G
On 3 February 2016, BT announced a new add-on service called Extra Speed 4G for BT Mobile customers, allowing them to access even faster upload and download speeds than standard 4G, provided they are in an Extra Speed 4G area. The speeds can reach a maximum of up to 60Mbit/s and the service costs £4 a month and is a 30-day rolling contract, which means customers won't be tied in for 12 months. The speed will vary on a day-to-day basis and depends on various things such as coverage, distance from the mast, the number of people using the network and the type of 4G phone you have, as well as whether you're indoors or in a densely populated area.[14][15]
Wi-Fi Calling
BT introduced Wi-Fi Calling on 29 March 2018, which allows customers to use Wi-Fi to call and text in areas with poor or no signal, and will come out of their monthly minutes and texts allowance or at the normal network rate, with no extra charge. It works on any Apple handset from iPhone 5S onwards and certain Android handsets bought from BT Mobile. For existing customers, BT's 'My BT' and BT Mobile app offer the ability to check phone compatibility. The phone's software must be updated to take benefit of the service, minimum iOS 11.3 or later for Apple handsets.[16][17][18][19][20]
4G Calling
BT introduced 4G Calling (VoLTE) on 29 March 2018, which allows customers to make calls over 4G and can continue to use 4G data as they talk. It works on any Apple handset from iPhone 6 onwards and certain Android handsets bought from BT Mobile. For existing customers, BT's 'My BT' and BT Mobile app offer the ability to check phone compatibility. The phone's software must be updated to take benefit of the service, minimum iOS 11.3 or later for Apple handsets.[21][22][18][19][20]
Voicemail
BT Mobile automatically diverts all unanswered calls to voicemail. Customers will receive a text from BT when a voicemail is left. It uses the same voicemail code - 1571 as BT's fixed lines.[23]
Parental Controls
BT Mobile offers free parental controls to limit what a user can access via the internet such as blocking inappropriate content.[24]
See also
References
- "Can I set up BT Mobile Parental Controls?". BT. Retrieved 30 March 2018.
External links
https://en.wikipedia.org/wiki/BT_Mobile
Telefónica Ireland was a broadband and telecommunications provider in Ireland that traded under the O2 brand (typeset as O2). O2 Ireland was previously called Esat Digifone when it was owned by Esat Telecommunications (and Telenor) from 1997 to 2006.
O2 Ireland became a subsidiary of Telefónica in 2006, after its parent company O2 in the United Kingdom was purchased. In June 2013, Hutchison Whampoa announced it would acquire the Irish arm of O2 for €780m.[3] O2 was merged into Hutchison Whampoa's subsidiary Three Ireland in March 2015.[4]
https://en.wikipedia.org/wiki/O2_(Ireland)
https://en.wikipedia.org/wiki/Digital_Access_Signalling_System_1
https://en.wikipedia.org/wiki/Health_and_Social_Care_Network#N3
https://en.wikipedia.org/wiki/TXE
https://en.wikipedia.org/wiki/TXK
https://en.wikipedia.org/wiki/Electric_Telegraph_Company
https://en.wikipedia.org/wiki/General_Post_Office
https://en.wikipedia.org/wiki/Category:Telephone_exchanges
The PRX205 (PRX/A) is a processor controlled reed relay telephone exchange developed by Philips Telecommunicatie Industrie BV (PTI) in Hilversum during the late 1960s and early 1970s. The first public switch was installed in Overvecht in Utrecht in 1972. About half of all sales were in the Netherlands; other countries with significant sales included Brazil, Indonesia, Peru and Jersey. The last PRX switch was taken out of service on 7 December 2010 at Volendam in the Netherlands.
The PRX digital version (PRX/D) was developed during the early 1980s in PTI's laboratories in Hilversum, Brussels and Malmesbury, Wiltshire but only went into limited production. PTI first went into partnership with AT&T in 1984 and then sold its remaining stake in the company to AT&T (later demerged into Lucent and subsequently merged to form Alcatel-Lucent) in 1987. After the takeover, the PRX/D development was stopped in favour of the AT&T 5ESS switch product, but development of PRX/A continued for some time afterwards. PRX/A systems were installed worldwide including many containerized versions and served reliably for 38 years.
External links
https://en.wikipedia.org/wiki/PRX_(telephony)
The rotary machine switching system, or most commonly known as the rotary system, was a type of automatic telephone exchange manufactured and used primarily in Europe from the 1910s. The system was developed and tested by AT&T's American engineering division, Western Electric, in the United States, at the same time when Western Electric was also developing the Panel switch. When AT&T selected the Panel System for large American exchanges, development and sales of the No. 7-A Machine Switching System, its formal commercial name, were transferred to Western Electric's international division in Belgium. In Europe and other continents the system was met with considerable commercial success.
The Rotary and Panel systems were very different systems, but both used the same newly developed component technology, such as Western Electric's latest relays, and the principles of the Lorimer system[1] of revertive pulsing and preselection.[2] The Rotary switches were smaller than the Panel system, and served only 200 rather than 500 stations. The initial version was the model 7A. It was succeeded by 7A1 and 7A2 and a rural system had the designation 7D.
Technology
The Rotary system used 1st and 2nd linefinders; when a customer picked up the phone all free linefinders in the group drove until one picked that customer line. Calls were switched over two, three or four group selection stages followed by a final selector. An office could start with two group selection stages for local calls (a first group level would serve 2000 lines), and be expanded to three group selection stages if it outgrew say 2000 or 4000 lines, depending on the number of first group levels required for other offices in a multi-exchange area.
Deployment
While the Panel system was chosen for American large cities, the Rotary system was selected for use in Europe and manufactured at the Bell Telephone Manufacturing factory of Western Electric (the International Bell Telephone Company) in Antwerp, Belgium. The first exchanges were installed in England at Darlington (10 October 1914) and Dudley (9 September 1916). However the British General Post Office standardised on the Step-by-Step (SXS) system in 1922, and subsequently the SXS Director system for London and other large cities. Six Rotary exchanges were installed in the city of Hull, between 1922 and 1929, where telephones service was supplied by Hull Corporation rather than by the GPO.
The Rotary system was chosen for The Hague, (the Netherlands) and New Zealand in 1913–14, but manufacture was disrupted by the German invasion of Belgium. Dies were moved to England, then to the Hawthorne Works of Western Electric in America (manufacture resumed at Antwerp in 1920). The first exchanges cutover (placed into service) were Masterton, New Zealand on 31 May 1919, followed by Courtenay Place and Wellington South in Wellington on 18 October 1919,[3] and Scheveningen, The Hague on 7 January 1920.[4] The Hague was the first multi-office area served entirely by the No. 7-A machine system with the cutover of the new Centrum office on 15 February 1924. There were four offices equipped with 23,000 lines; Bezuidenhout, Centrum (or Hofstraat), Hague West (or Marnix), and Scheveningen. The system was owned by The Hague Municipality; initially only 5,000 lines were fully automatic, the rest were semi-automatic.
The Rotary semi-automatic system 7A was chosen for public experiment in October 1912 by the French Administration Postes Télégraphes Téléphones. The first semi-automatic Rotary 7A (McBerty design) was turned on in Angers in November 1915, and the second in Marseille on 19 April 1919 (Marseille-Colbert I). Only two Rotary 7A semi-automatic were installed in France. All the other Rotary exchanges in France were 7A1 fully automatic (Gerald Deakin mechanics). The 1 January 1928, The semi-automatic Rotary 7A of Marseille-Colbert 1 was fully automated, maximum capacity lines 10,000. Angers stayed semi-automatic only, capacity approx 3,000 lines. Rotary fully automatic 7A1 was deployed in Nantes on 29 October 1927, Marseille-town (first Marseille-Dragon on 5 May 1928) and Paris (first Carnot on 22 September 1928) and Region of Paris in large and exclusive proportion. All the French Rotary 7A and 7A1 were exclusively manufactured in France, with French workers, essentially by ITT-LMT company, and, in subsidiary by French Ericsson Society and Society Grammont.
In 1925 IT&T purchased International Western Electric, formerly Bell Telephone Manufacturing Company, in Belgium, from AT&T; as the Bell System complied with regulators to sell its overseas manufacturing interests to settle anti-trust action. In the 1930s, ITT grew through purchasing German electronic companies Standard Elektrizitaetsgesellschaft and Mix & Genest, both of which were internationally active companies.
Apart from the Netherlands (38,100 lines) and New Zealand (48,400 lines), other countries that had installed or ordered Rotary equipment by 1925[5] were Australia, Belgium (29,000 lines), Denmark, England, France, Hungary, Italy, Norway (41,160 lines), Romania, South Africa, Sweden and Switzerland. There was a total of 104,615 lines in service, and 137,330 lines “proceeding”. Subsequently, at Zurich, Switzerland; the mechanical registers were replaced by PDP-11 computers.[6]
In Kingston-upon-Hull which had the only municipal telephone system in the United Kingdom (see KCOM Group), operated by the Hull City Council, rotary exchanges were operated from 1922 to 1975.[7] In the rest of the United Kingdom, the telephone system was operated by the British Post Office (later British Telecom), which had installed a Rotary exchange at Darlington (10 October 1914) and Dudley (9 September 1916), but subsequently decided to use the Strowger system in small and medium cities and the Director system in London (from 1927) and five other large British cities.
A Rotary system was installed in Auckland, New Zealand in the central city telephone exchange (WLT) in Wellesley Street in 1924.[8][9] Other Auckland exchanges with Rotary systems included Devonport 1 and 2 (DA1 and DA2) and Mount Eden 1 (MOD1).[citation needed] These four exchanges were still operating until at least 1970.[citation needed]
Working exhibit
In Christchurch, New Zealand at the Ferrymead Heritage Park, the Ferrymead Post & Telegraph Historical Society has a working exhibit of the 7A Rotary Switching system. The display includes a bay of 7A1 Line Finders and a bay of 7A1 Registers.
In Auckland, New Zealand, a rotary exchange was set up as an exhibit at the Museum of Transport and Technology at Western Springs.[8]
In Budapest, Hungary, at the Museum of Telephones (Telefónia Múzeum) there is a still workable 7A1 Rotary Switching system. (The exhibition has been closed until the first part of 2019 due to some reconstruction works.)
At the Norwegian Telecom Museum in Oslo, Norway there is a 7A2 exchange.
In Vámosgyörk, Hungary, at the Hungarian State Railways telecommunications main body Miskolc (Magyar Államvasutak Zrt. Távközlési Főnökség Miskolc) there is a still workable 7D PBX Rotary Switching system. Fully functional but not in operation, which has been replaced by an MD 110 system. It is kept as a museum style exhibit. It can serve up to 100 subscribers in number group 41 (4100 to 4199).
In Szentes, Hungary, at the Hungarian State Railways telecommunications main body Szeged (Magyar Államvasutak Zrt. Távközlési Főnökség Szeged) there is a still workable 7D PBX Rotary Switching system. Fully functional in operation. It is kept as a museum style exhibit. It can serve up to 200 subscribers in number group 75 and 76 (7500 to 7699).
US deployment
This section needs expansion. You can help by adding to it. (May 2013) |
Notes
- Note: Electrical Communication was published quarterly by the International Standard Electric Corporation. Subsidiaries of the company included the Bell Telephone Manufacturing Company, Antwerp and Standard Electric or Standard Telephones and Cables in various countries. Deakin and Turkhud were with the Bell Telephone Manufacturing Company, Antwerp; Shrimpton was with Standard Telephones and Cables (Australasia).
References
- "Nerve centre of Auckland's telephone system". The Auckland Star – archived at Paperspast – paperspast.natlib.govt.nz/. 31 May 1941. Retrieved 12 July 2019.
External links
- UK Telephone History
- Lorimer System by Bob Estreich
- Museum of Telephones in Budapest
- "Photos of rotary telephone equipment". New Zealand Free Lance in Papers Past. 22 October 1919.
- "How to use the automatic telephone; 1919 instructions". Evening Post (NZ) in Papers Past. 17 October 1919.
https://en.wikipedia.org/wiki/Rotary_system
https://en.wikipedia.org/wiki/Telephone_exchange#Early_automatic_exchanges
https://en.wikipedia.org/wiki/Dual-tone_multi-frequency_signaling
https://en.wikipedia.org/wiki/Local_loop
https://en.wikipedia.org/wiki/Single-wire_earth_return
https://en.wikipedia.org/wiki/Wire_spring_relay
https://en.wikipedia.org/wiki/Elastix
https://en.wikipedia.org/wiki/Destination_routing
https://en.wikipedia.org/wiki/Stored_program_control
https://en.wikipedia.org/wiki/Public_switched_telephone_network
https://en.wikipedia.org/wiki/Backbone_network
https://en.wikipedia.org/wiki/Internet_backbone
https://en.wikipedia.org/wiki/Redundancy_(engineering)
https://en.wikipedia.org/wiki/Safety-critical_system
https://en.wikipedia.org/wiki/Human_error
https://en.wikipedia.org/wiki/Triple_modular_redundancy
https://en.wikipedia.org/wiki/Fault_tolerance
https://en.wikipedia.org/wiki/Mission_critical
https://en.wikipedia.org/wiki/Online_transaction_processing
https://en.wikipedia.org/wiki/Automated_teller_machine
https://en.wikipedia.org/wiki/White-label_ABMs
https://en.wikipedia.org/wiki/Repetition_code
https://en.wikipedia.org/wiki/Error_correction_code
The American mathematician Richard Hamming pioneered this field in the 1940s and invented the first error-correcting code in 1950: the Hamming (7,4) code.[5]
https://en.wikipedia.org/wiki/Error_correction_code
https://en.wikipedia.org/wiki/Analog-to-digital_converter
https://en.wikipedia.org/wiki/Digital-to-analog_converter
https://en.wikipedia.org/wiki/Sampling_(signal_processing)
https://en.wikipedia.org/wiki/Discrete_time_and_continuous_time
https://en.wikipedia.org/wiki/Stored_program_control
https://en.wikipedia.org/wiki/Combinational_logic
https://en.wikipedia.org/wiki/Time-division_multiplexing
https://en.wikipedia.org/wiki/Stored-program_computer
https://en.wikipedia.org/wiki/Computer_memory
https://en.wikipedia.org/wiki/Flying-spot_store
https://en.wikipedia.org/wiki/Number_One_Electronic_Switching_System
https://en.wikipedia.org/wiki/Programmable_logic_array
https://en.wikipedia.org/wiki/Canonical_normal_form
https://en.wikipedia.org/wiki/AND_gate
https://en.wikipedia.org/wiki/Programmable_Array_Logic
https://en.wikipedia.org/wiki/Programmable_ROM#OTPM
https://en.wikipedia.org/wiki/EPROM
An EPROM (rarely EROM), or erasable programmable read-only memory, is a type of programmable read-only memory (PROM) chip that retains its data when its power supply is switched off. Computer memory that can retrieve stored data after a power supply has been turned off and back on is called non-volatile. It is an array of floating-gate transistors individually programmed by an electronic device that supplies higher voltages than those normally used in digital circuits. Once programmed, an EPROM can be erased by exposing it to strong ultraviolet light source (such as from a mercury-vapor lamp). EPROMs are easily recognizable by the transparent fused quartz (or on later models resin) window on the top of the package, through which the silicon chip is visible, and which permits exposure to ultraviolet light during erasing.[2]
https://en.wikipedia.org/wiki/EPROM
One time programmable memory
OTP (one time programmable) memory is a special type of non-volatile memory (NVM) that permits data to be written to memory only once. Once the memory has been programmed, it retains its value upon loss of power (i.e., is non-volatile). OTP memory is used in applications where reliable and repeatable reading of data is required. Examples include boot code, encryption keys and configuration parameters for analog, sensor or display circuitry. OTP NVM is characterized, over other types of NVM like eFuse or EEPROM, by offering a low power, small area footprint memory structure. As such OTP memory finds application in products from microprocessors & display drivers to Power Management ICs (PMICs).
Commercially available semiconductor antifuse-based OTP memory arrays have been around at least since 1969, with initial antifuse bit cells dependent on blowing a capacitor between crossing conductive lines. Texas Instruments developed a MOS gate oxide breakdown antifuse in 1979.[3] A dual-gate-oxide two-transistor (2T) MOS antifuse was introduced in 1982.[4] Early oxide breakdown technologies exhibited a variety of scaling, programming, size and manufacturing problems that prevented volume production of memory devices based on these technologies.
Another form of one-time programmable memory device uses the same semiconductor chip as an ultraviolet-erasable programmable read-only memory (UV-EPROM), but the finished device is put into an opaque package, instead of the expensive ceramic package with transparent quartz window required for erasing. These devices are programmed with the same methods as the UV EPROM parts but are less costly. Embedded controllers may be available in both field-erasable and one-time styles, allowing a cost saving in volume production without the expense and lead time of factory-programmed mask ROM chips. [5]
Although antifuse-based PROM has been available for decades, it wasn’t available in standard CMOS until 2001 when Kilopass Technology Inc. patented 1T, 2T, and 3.5T antifuse bit cell technologies using a standard CMOS process, enabling integration of PROM into logic CMOS chips. The first process node antifuse can be implemented in standard CMOS is 0.18 um. Since the gate oxide breakdown is less than the junction breakdown, special diffusion steps were not required to create the antifuse programming element. In 2005, a split channel antifuse device[6] was introduced by Sidense. This split channel bit cell combines the thick (IO) and thin (gate) oxide devices into one transistor (1T) with a common polysilicon gate.
https://en.wikipedia.org/wiki/Programmable_ROM#OTPM
Programming
A typical PROM comes with all bits reading as "1". Burning a fuse bit during programming causes the bit to be read as "0" by "blowing" the fuses, which is an irreversible process. Some devices can be "reprogrammed" if the new data replaces "1"s with "0"s. Some CPU instruction sets (e.g. 6502) took advantage of this by defining a break (BRK) instruction with the operation code of '00'. In cases where there was an incorrect instruction, it could be "reprogrammed" to a BRK causing the CPU to transfer control to a patch. This would execute the correct instruction and return to the instruction after the BRK.
The bit cell is programmed by applying a high-voltage pulse not encountered during a normal operation across the gate and substrate of the thin oxide transistor (around 6 V for a 2 nm thick oxide, or 30 MV/cm) to break down the oxide between gate and substrate. The positive voltage on the transistor's gate forms an inversion channel in the substrate below the gate, causing a tunneling current to flow through the oxide. The current produces additional traps in the oxide, increasing the current through the oxide and ultimately melting the oxide and forming a conductive channel from gate to substrate. The current required to form the conductive channel is around 100 µA/100 nm2 and the breakdown occurs in approximately 100 µs or less.[7]
https://en.wikipedia.org/wiki/Programmable_ROM#OTPM
https://en.wikipedia.org/wiki/Category:Computer-related_introductions_in_1956
https://en.wikipedia.org/wiki/IBM_305_RAMAC
https://en.wikipedia.org/wiki/IBM_370_printer
https://en.wikipedia.org/wiki/Floating-gate_MOSFET
The floating-gate MOSFET (FGMOS), also known as a floating-gate MOS transistor or floating-gate transistor, is a type of metal–oxide–semiconductor field-effect transistor (MOSFET) where the gate is electrically isolated, creating a floating node in direct current, and a number of secondary gates or inputs are deposited above the floating gate (FG) and are electrically isolated from it. These inputs are only capacitively connected to the FG. Since the FG is surrounded by highly resistive material, the charge contained in it remains unchanged for long periods[1] of time, nowadays typically longer than 10 years. Usually Fowler-Nordheim tunneling and hot-carrier injection mechanisms are used to modify the amount of charge stored in the FG.
The FGMOS is commonly used as a floating-gate memory cell, the digital storage element in EPROM, EEPROM and flash memory technologies. Other uses of the FGMOS include a neuronal computational element in neural networks,[2][3] analog storage element,[2] digital potentiometers and single-transistor DACs.
https://en.wikipedia.org/wiki/Floating-gate_MOSFET
In 1989, Intel employed the FGMOS as an analog nonvolatile memory element in its electrically trainable artificial neural network (ETANN) chip,[3] demonstrating the potential of using FGMOS devices for applications other than digital memory.
Three research accomplishments laid the groundwork for much of the current FGMOS circuit development:
- Thomsen and Brooke's demonstration and use of electron tunneling in a standard CMOS double-poly process[7] allowed many researchers to investigate FGMOS circuits concepts without requiring access to specialized fabrication processes.
- The νMOS, or neuron-MOS, circuit approach by Shibata and Ohmi[8] provided the initial inspiration and framework to use capacitors for linear computations. These researchers concentrated on the FG circuit properties instead of the device properties, and used either UV light to equalize charge, or simulated FG elements by opening and closing MOSFET switches.
- Carver Mead's adaptive retina[2] gave the first example of using continuously-operating FG programming/erasing techniques, in this case UV light, as the backbone of an adaptive circuit technology.
https://en.wikipedia.org/wiki/Floating-gate_MOSFET
Structure
An FGMOS can be fabricated by electrically isolating the gate of a standard MOS transistor[clarification needed], so that there are no resistive connections to its gate. A number of secondary gates or inputs are then deposited above the floating gate (FG) and are electrically isolated from it. These inputs are only capacitively connected to the FG, since the FG is completely surrounded by highly resistive material. So, in terms of its DC operating point, the FG is a floating node.
For applications where the charge of the FG needs to be modified, a pair of small extra transistors are added to each FGMOS transistor to conduct the injection and tunneling operations. The gates of every transistor are connected together; the tunneling transistor has its source, drain and bulk terminals interconnected to create a capacitive tunneling structure. The injection transistor is connected normally and specific voltages are applied to create hot carriers that are then injected via an electric field into the floating gate.
FGMOS transistor for purely capacitive use can be fabricated on N or P versions. [9] For charge modification applications, the tunneling transistor (and therefore the operating FGMOS) needs to be embedded into a well, hence the technology dictates the type of FGMOS that can be fabricated.
https://en.wikipedia.org/wiki/Floating-gate_MOSFET
Charge trap flash (CTF) is a semiconductor memory technology used in creating non-volatile NOR and NAND flash memory. It is a type of floating-gate MOSFET memory technology, but differs from the conventional floating-gate technology in that it uses a silicon nitride film to store electrons rather than the doped polycrystalline silicon typical of a floating-gate structure. This approach allows memory manufacturers to reduce manufacturing costs five ways:
- Fewer process steps are required to form a charge storage node
- Smaller process geometries can be used (therefore reducing chip size and cost)
- Multiple bits can be stored on a single flash memory cell
- Improved reliability
- Higher yield since the charge trap is less susceptible to point defects in the tunnel oxide layer
While the charge-trapping concept was around earlier, it wasn't until 2002 that AMD and Fujitsu produced high-volume charge-trapping flash memory. They began the commercial production of charge-trapping flash memory with the introduction of the GL NOR flash memory family. The same business, now operating under the Spansion name, has produced charge trapping devices in high volume since that time. Charge trapping flash accounted for 30% of 2008's $2.5 billion NOR flash market. Saifun Semiconductors, who licensed a large charge trapping technology portfolio to several companies, was acquired by Spansion in March 2008. From the late 2000s, CTF became a core component of 3D V-NAND flash memory developed by Toshiba and Samsung Electronics.
Origins
The original MOSFET (metal–oxide–semiconductor field-effect transistor, or MOS transistor) was invented by Egyptian engineer Mohamed M. Atalla and Korean engineer Dawon Kahng at Bell Labs in 1959, and demonstrated in 1960.[1] Kahng went on to invent the floating-gate MOSFET with Simon Min Sze at Bell Labs, and they proposed its use as a floating-gate (FG) memory cell, in 1967.[2] This was the first form of non-volatile memory based on the injection and storage of charges in a floating-gate MOSFET,[3] which later became the basis for EPROM (erasable PROM), EEPROM (electrically erasable PROM) and flash memory technologies.[4]
The charge-trapping concept was first presented by John Szedon and Ting L. Chu in 1967.[citation needed]
In late 1967, a Sperry research team led by H.A. Richard Wegener invented the metal–nitride–oxide–semiconductor transistor (MNOS transistor),[5] a type of MOSFET in which the oxide layer is replaced by a double layer of nitride and oxide.[6] Nitride was used as a trapping layer instead of a floating gate, but its use was limited as it was considered inferior to a floating gate.[7] The MNOS transistor device could be programmed through the application of a 50-volt forward or reverse bias between the gate and the channel to trap charges that would impact the threshold voltage of the transistor.
Charge trap (CT) memory was introduced with MNOS devices in the late 1960s. It had a device structure and operating principles similar to floating-gate (FG) memory, but the main difference is that the charges are stored in a conducting material (typically a doped polysilicon layer) in FG memory, whereas CT memory stored charges in localized traps within a dielectric layer (typically made of silicon nitride).[3]
Charge trap EEPROM
By 1974, charge trap technology was used as a storage mechanism in electrically erasable programmable read-only memory (EEPROM), and was an alternative to the standard floating-gate MOSFET technology.[8] In 1977, P.C.Y. Chen of Fairchild Camera and Instrument published a paper[9] detailing the invention of SONOS, a MOSFET technology with far less demanding program and erase conditions and longer charge storage. This improvement led to manufacturable EEPROM devices based on charge-trapping SONOS in the 1980s.
Charge trap flash experiments
In 1991, Japanese NEC researchers including N. Kodama, K. Oyama and Hiroki Shirai developed a type of flash memory that incorporated a charge trap method.[10] In 1998, Israeli engineer Boaz Eitan of Saifun Semiconductors (later acquired by Spansion) patented[11] a flash memory technology named NROM that took advantage of a charge trapping layer to replace the floating gate used in conventional flash memory designs. Two important innovations appear in this patent: the localization of the injected negative and positive charges close to the cell's drain/source terminals, and utilizing a reverse read concept to detect the cell's stored data on either end of the charge trap. These two new ideas enabled high cycling thus allowing reliable charge trap flash products to be produced for the first time since the charge trapping concept was invented 30 years earlier. Furthermore, using these concepts it is possible to create two separate physical bits per cell, doubling the capacity of stored data per cell.
In 2000, an Advanced Micro Devices (AMD) research team led by Richard M. Fastow, Egyptian engineer Khaled Z. Ahmed and Jordanian engineer Sameer Haddad (who later joined Spansion) demonstrated a charge trap mechanism for NOR flash memory cells.[12] These innovations were further improved at AMD and Fujitsu in 2002 (and later by Spansion), and first put into volume production by these companies in what was called “MirrorBit Flash memory.”
Spansion MirrorBit Flash memory
Charge trapping flash (CTF) was commercialized by AMD and Fujitsu in 2002.[13] That year, AMD (in a division later spun off as Spansion) announced a new flash memory technology it called "MirrorBit".[14] Spansion used this product to reduce manufacturing costs and extend the density range of NOR Flash memory past that of conventional NOR flash and to match the cost of the multi-level cell NOR flash being manufactured by Intel.
The MirrorBit cell uses a charge trapping layer not only as a substitute for a conventional floating gate, but it also takes advantage of the non-conducting nature of the charge storage nitride to allow two bits to share the same memory cell. Shown in Figure 1 the bits reside at opposite ends of the cell and can be read by running a current through the channel in different directions.
Products have been successfully made to combine this approach with multilevel cell technology to contain four bits on a cell.[15]
Charge trapping operation
Like the floating gate memory cell, a charge trapping cell uses a variable charge between the control gate and the channel to change the threshold voltage of the transistor. The mechanisms to modify this charge are relatively similar between the floating gate and the charge trap, and the read mechanisms are also very similar.
Charge trapping vs floating gate mechanisms
In a charge trapping flash, electrons are stored in a trapping layer just as they are stored in the floating gate in a standard flash memory, EEPROM, or EPROM. The key difference is that the charge trapping layer is an insulator, while the floating gate is a conductor.
High write loads in a flash memory cause stress on the tunnel oxide layer creating small disruptions in the crystal lattice called "oxide defects". If a large number of such disruptions are created a short circuit develops between the floating gate and the transistor's channel and the floating gate can no longer hold a charge. This is the root cause of flash wear-out (see Flash memory#Memory wear), which is specified as the chip's “endurance.” In order to reduce the occurrence of such short circuits, floating gate flash is manufactured using a thick tunnel oxide (~100Å), but this slows erase when Fowler-Nordheim tunneling is used and forces the design to use a higher tunneling voltage, which puts new burdens on other parts of the chip.
A charge trapping cell is relatively immune to such difficulties, since the charge trapping layer is an insulator.[16] A short circuit created by an oxide defect between the charge trapping layer and the channel will drain off only the electrons in immediate contact with the short, leaving the other electrons in place to continue to control the threshold voltage of the transistor. Since short circuits are less of a concern, a thinner tunnel oxide layer can be used (50-70Å) increasing the trapping layer's coupling to the channel and leading to a faster program speed (with localized trapped charges) and erasing with lower tunneling voltages. The lower tunneling voltages, in turn, place less stress on the tunnel oxide layer, leading to fewer lattice disruptions.
Another important benefit of using a charge trapping cell is that the thin charge trapping layer reduces capacitive coupling between neighboring cells to improve performance and scalability.[16]
Getting the charge onto the charge trapping layer
Electrons are moved onto the charge trapping layer similarly to the way that floating gate NOR flash is programmed, through channel hot electron (CHE) injection mechanism also known as Hot-carrier injection. In brief, a high voltage is placed between the control gate while a medium-high voltage is applied on the source and the drain while a current is induced from the source to the drain. Those electrons that have gained sufficient energy in traversing through the high-field region near the drain will boil off from the channel to be injected into the charge trapping layer where they come to rest.
Removing a charge from the charge trapping layer
Charge Trapping flash is erased via hot hole injection (see Hot-carrier injection) as opposed to the Fowler–Nordheim tunneling approach used in both NAND and NOR flash for erasure. This process uses a field, rather than the current used in FN, to move holes toward the charge trapping layer to remove the charge.
Manufacturing charge trapping flash
Charge trapping flash is similar in manufacture to floating gate flash with certain exceptions that serve to simplify manufacturing.
Materials differences from floating gate
Both floating gate flash and charge trapping flash use a stacked gate structure in which a floating gate or charge trapping layer lies immediately above the channel, and below a control gate. The floating gate or charge trapping layer is insulated from the channel by a tunnel oxide layer and from the control gate by a gate oxide layer. Materials for all of these layers are the same with the exception of the storage layer, which is conductive polysilicon for the floating gate structure and is typically silicon nitride for the charge trap.
Relationship of charge trapping to silicon nanocrystals
Freescale Semiconductor manufactures a somewhat similar technology the company calls "Thin Film Storage" in its microcontroller or MCU line. The Freescale approach uses silicon nanocrystals as conductive islands in a nonconductive layer of silicon oxide.
Like the more conventional silicon nitride charge trap, electrons do not flow from one side of the floating gate to the other, extending the cell's wear.
This nanocrystal approach is being manufactured in volume by Freescale and charge trapping storage in general is in development at ST Microelectronics, Philips, Renesas, Samsung, Toshiba, Atmel, and Spansion.[17]
Process differences from Floating Gate
Since the nitride charge trapping layer is nonconductive, it does not need to be patterned – all the charge traps are already insulated from each other. This can be used to simplify manufacturing.
Floating gate structures have required more elaborate gate dielectrics for the past few process generations and today commonly use an ONO (oxide-nitride-oxide) structure which is more complex to manufacture and is unnecessary in a charge-trapping flash.
One advantage of the nitride layer is that it is less sensitive to high temperature fabrication processing than is the polysilicon used in a floating gate. This simplifies processing of the layers above the charge trap.
In a marketing brochure Spansion has claimed that the processing cost of a MirrorBit NOR flash wafer is lower than that of a conventional floating gate wafer since there are 10% fewer photolithography mask steps, and 40% fewer "critical" steps (those requiring the finest resolution, and therefore the most expensive photolithographic equipment).[18] Infineon's marketing materials showed that 15% fewer mask steps were required to make charge trapping NAND flash than to manufacture the equivalent floating gate product.
MirrorBit Flash memory
Spansion's MirrorBit Flash and Saifun's NROM are two flash memories that use a charge trapping mechanism in nitride to store two bits onto the same cell effectively doubling the memory capacity of a chip. This is done by placing charges on either side of the charge trap layer. The cell is read by using forward and reverse currents through the channel to read either side of the charge trap.
MirrorBit operation – getting 2 bits onto the cell
During CHE programming (figure 2) the hot electrons are injected from the channel into the charge trapping layer toward the biased drain end of the channel, but not from the floating source end of the channel. By allowing the transistor's source and drain to switch from one end of the channel to the other, charges can be injected and stored into the charge trapping layer over either end of the channel.
In a similar way, one end of the charge trapping cell can be erased by placing the erasing field at one end or the other of the channel, allowing the other end to float as shown in figure 3. Band-to-band Hot Hole Erase creates holes that are trapped locally some of which recombine with electrons to remove the charge from that end of the charge trap.
Reading 2 bits from the cell
The MirrorBit read is performed very simply by reversing the source and drain contacts. The junction depletion region extending from the drain side shields the channel from the charge on the side of the charge trapping cell that overlies the drain. The net result of this is that the drain-side charge has little effect on the current running through the channel, while the source-side charge determines the threshold of the transistor.
When source and drain are reversed, the opposite side's charge determines the transistor's threshold.
This way two different charge levels at either end of the charge trapping cell will cause two different currents to flow through the cell, depending on the direction of the current flow.
Later developments
Charge trapping NAND – Samsung and others
Samsung Electronics in 2006 disclosed[19] its research into the use of Charge Trapping Flash to allow continued scaling of NAND technology using cell structures similar to the planar structures in use at that time. The technology depends on a SONOS (silicon–oxide–nitride–oxide–silicon) or MONOS (metal-ONOS) capacitor structure, storing the information in charge traps in the nitride layer.
Samsung disclosed two cell structures: TANOS (Titanium, Alumina, Nitride, Oxide, Silicon) for 40 nm, where researchers believed that the existing 3D cap structure (described in detail later in this article) could not be manufactured, and THNOS, in which the aluminum oxide would be replaced with an undisclosed high-k dielectric material. The high-k material was expected to yield longer retention times than the aluminum oxide structure.
In a cap structure the control gate is extended to form a barrier between adjacent floating gates in a conventional floating gate cell.
Over the following five years many device designers found ways to push the cap structure to increasingly tighter process geometries, successfully producing NAND at the 30 nm node with this approach.
Charge trapping is still viewed as a future technology for NAND flash, but it is being considered more for vertical structures than for planar cells.
Why NAND needs charge trapping technology
NAND flash has been scaling very aggressively (figure 4). As processes migrate, the width of the interface of the control gate and the floating gate shrinks in proportion to the square of the shrink, and the spacing between floating gates shrinks in proportion to the process shrink, but the floating gate's thickness remains the same (the thinner the floating gate is made the less tolerant the cell becomes to electron loss). This means that the coupling between adjacent floating gates becomes larger than the coupling between the control gate and the floating gate, leading to data corruption between adjacent bits.
As processes continue to shrink, this becomes increasingly problematic. For this reason the control gate in modern NAND flash has been reconfigured to cap the floating gate. In a cap structure the control gate is extended to form a barrier between adjacent floating gates in a conventional floating gate cell (see figure 5). This serves to reduce coupling to the adjacent floating gate while increasing the coupling between the floating gate and the control gate. One drawback is that the control gate couples to the channel, so measures must be taken to minimize this coupling.
It was believed in 2006 that the existing floating gate cap structure could not be manufactured at processes smaller than the 50 nm node due to difficulties in producing the complex three-layer ONO gate oxide that these devices require.
Samsung even announced[20] in late 2006 that by 2008 it would put such a device into production at the 40 nm process node, but over the five years following this announcement many device designers found ways to push the cap structure to increasingly tighter process geometries, successfully producing NAND down to 20 nm node with this approach.
The charge trapping approach is still viewed as a future for NAND flash for processes smaller than 20 nm and is being considered for both planar as well as vertical 3D structures.
When this change might occur
Today[when?] SanDisk asserts that the company expects to continue to use conventional NAND structures into a second node in the 10–19 nm range.[21] This implies that standard device structures could stay in place until the industry reaches 10 nm, however the challenges of producing a reliable floating gate become more severe with each process shrink.
On the other hand, the International Technology Roadmap for Semiconductors (ITRS) process technology roadmap's 2010 Process Integration, Devices, and Structures (PIDS) tables[22] show adoption of charge trapping starting at 22 nm in 2012, and becoming mainstream in 2014 with the 20 nm process.
It is possible that a planar charge trapping cell will be used for future processes. No manufacturers have yet disclosed their processes for geometries smaller than 19 nm.
Charge trapping layers for vertical structures
Vertical structures are seen as a logical next step for NAND flash, once further horizontal scaling becomes inviable. Since vertical features cannot be etched sideways, a charge trapping layer becomes a very interesting way to build a vertical NAND flash string.
Toshiba and Samsung Electronics have disclosed prototypes for vertical charge trapping NAND structures.
Toshiba's BiCS and Samsung's 3D NAND
Toshiba in 2007[23] and Samsung in 2009[24] announced the development of 3D V-NAND, a means of building a standard NAND flash bit string vertically rather than horizontally to increase the number of bits in a given area of silicon.
A rough idea of the cross section of this is shown in figure 6. In this drawing the red portions represent conductive polysilicon, the blue is silicon dioxide insulating layers, and the yellow is the nitride charge trapping layer.
The vertical structures (only one shown) are cylinders that implement a channel that is wrapped in alternating dielectric and charge trapping layers (blue and yellow). To manufacture such a device layers of conducting polysilicon and silicon dioxide dielectric are deposited first on top of a silicon substrate that contains standard CMOS logic elements. A trench is then etched and its walls are deposited first with silicon dioxide (blue), then silicon nitride (yellow), then another silicon dioxide (blue) layer, forming the gate dielectric, the charge trap, and the tunnel dielectric in that order. Finally the hole is filled with conducting polysilicon (red) which forms the channel. The alternating layers of conductive polysilicon function as the control gates in this structure.
This structure takes advantage of the fact that the charge trap layer does not need to be insulated between each control gate, so it need not be etched in the vertical direction.
Charge trapping in embedded memories
One advantage that charge trapping flash has over other technologies is that it can be relatively easily embedded with a standard logic process. A standard logic process can be converted to a logic-plus-flash process through the addition of three more high voltage masks and three more core CTF masks, and none of these six masks is a critical layer (i.e. needs to use the most advanced part of the process). All other logic processes can be shared directly.[25]
Bandgap-Engineered Charge-Trapping Memory Devices
In ITRS PIDS 2013, it was clearly mentioned that bandgap engineered charge-trapping devices are needed to resolve the retention and erase dilemma. SONOS using a simple tunnel oxide, however, is not suitable for NAND application-once electrons are trapped in deep SiN trap levels they are difficult to detrap even under high electric field. In order to erase the device quickly holes in the substrate are injected into the SiN to neutralize the electron charge. Since the hole barrier for SiO2 is high (~4.1 eV), hole injection efficiency is poor and sufficient hole current is only achievable by using very thin tunnel oxide (~ 2 nm). Such thin tunnel oxide, however, results in poor data retention because direct hole tunneling from the substrate under the weak built-in field caused by storage electrons cannot be stopped (the rate of direct tunneling is a strong function of the barrier thickness but only weakly depends on the electric field, thus the weak built-in field by charge storage is sufficient to cause direct hole tunneling from the substrate which ruins the data retention). Several variations of SONOS have been proposed. Tunnel dielectric engineering concepts are used to modify the tunneling barrier properties to create "variable thickness" tunnel dielectric. For example, triple ultra-thin (1–2 nm) layers of ONO are introduced to replace the single oxide (BE-SONOS) [H. T. Lue, et al, IEDM 2005]. Under high electric field, the upper two layers of oxide and nitride are offset above the Si valence band, and substrate holes readily tunnel through the bottom thin oxide and inject into the thick SiN trapping layer above. In data storage mode, the weak electric field does not offset the triple layer and both electrons in the SiN and holes in the substrate are blocked by the total thickness of the triple layer. Later BE-SONOS is added high-K (Al2O3) and metal gate to enhance the erase performances, the so-called BE-MANOS [S. C. Lai, et al, NVSMW 2007]. It is suggested to add a buffer oxide in between high-K Al2O3 and SiN to improve the retention. Right now the mass production 3D NAND adopts a similar structure of BE-MANOS, with some variations of detail recipe tuning by each individual companies. The concept of bandgap engineered for tunneling barrier is recognized as a necessary path for charge-trapping devices.
Although charge trapping NAND can help the GCR and FG cross talk issues and thus promises scaling below 20nm it does not help the fundamental limitations such as word line breakdown and too few electrons. Therefore, in the roadmap trend it occupies a transition role between planar FG and 3D NAND. When charge trapping devices are used to build 3D NAND, the larger device size naturally solves the electron number and the word line breakdown issues.
Further reading
- "Samsung unwraps 40nm charge trap flash device" (Press release). Solid State Technology. 11 September 2006. Archived from the original on 3 July 2013.
- Kinam Kim (2005). "Technology for sub-50nm DRAM and NAND flash manufacturing". Electron Devices Meeting, 2005. IEDM Technical Digest: 323–326. doi:10.1109/IEDM.2005.1609340. ISBN 0-7803-9268-X. S2CID 16423250.
- Sanghun Jeon; et al. (December 2005). "High work-function metal gate and high-κ dielectrics for charge trap flash memory device applications". IEEE Transactions on Electron Devices. 52 (12): 2654–2659. Bibcode:2005ITED...52.2654J. doi:10.1109/TED.2005.859691.
- Saied Tehrani; et al. (June 17, 2013). "The future of charge-trapping flash memory". EE Times.
References
- Chung, Sung-Yong (2010). "Technology and design of charge trapping device for NOR flash application". International Memory Workshop Short Course.
https://en.wikipedia.org/wiki/Charge_trap_flash
https://en.wikipedia.org/wiki/Metrovick_950
Hot carrier injection (HCI) is a phenomenon in solid-state electronic devices where an electron or a “hole” gains sufficient kinetic energy to overcome a potential barrier necessary to break an interface state. The term "hot" refers to the effective temperature used to model carrier density, not to the overall temperature of the device. Since the charge carriers can become trapped in the gate dielectric of a MOS transistor, the switching characteristics of the transistor can be permanently changed. Hot-carrier injection is one of the mechanisms that adversely affects the reliability of semiconductors of solid-state devices.[1]
Physics
The term “hot carrier injection” usually refers to the effect in MOSFETs, where a carrier is injected from the conducting channel in the silicon substrate to the gate dielectric, which usually is made of silicon dioxide (SiO2).
To become “hot” and enter the conduction band of SiO2, an electron must gain a kinetic energy of ~3.2 eV. For holes, the valence band offset in this case dictates they must have a kinetic energy of 4.6 eV. The term "hot electron" comes from the effective temperature term used when modelling carrier density (i.e., with a Fermi-Dirac function) and does not refer to the bulk temperature of the semiconductor (which can be physically cold, although the warmer it is, the higher the population of hot electrons it will contain all else being equal).
The term “hot electron” was originally introduced to describe non-equilibrium electrons (or holes) in semiconductors.[2] More broadly, the term describes electron distributions describable by the Fermi function, but with an elevated effective temperature. This greater energy affects the mobility of charge carriers and as a consequence affects how they travel through a semiconductor device.[3]
Hot electrons can tunnel out of the semiconductor material, instead of recombining with a hole or being conducted through the material to a collector. Consequent effects include increased leakage current and possible damage to the encasing dielectric material if the hot carrier disrupts the atomic structure of the dielectric.
Hot electrons can be created when a high-energy photon of electromagnetic radiation (such as light) strikes a semiconductor. The energy from the photon can be transferred to an electron, exciting the electron out of the valence band, and forming an electron-hole pair. If the electron receives enough energy to leave the valence band, and to surpass the conduction band, it becomes a hot electron. Such electrons are characterized by high effective temperatures. Because of the high effective temperatures, hot electrons are very mobile, and likely to leave the semiconductor and travel into other surrounding materials.
In some semiconductor devices, the energy dissipated by hot electron phonons represents an inefficiency as energy is lost as heat. For instance, some solar cells rely on the photovoltaic properties of semiconductors to convert light to electricity. In such cells, the hot electron effect is the reason that a portion of the light energy is lost to heat rather than converted to electricity.[4]
Hot electrons arise generically at low temperatures even in degenerate semiconductors or metals.[5] There are a number of models to describe the hot-electron effect.[6] The simplest predicts an electron-phonon (e-p) interaction based on a clean three-dimensional free-electron model.[7][8] Hot electron effect models illustrate a correlation between power dissipated, the electron gas temperature and overheating.
Effects on transistors
In MOSFETs, hot electrons have sufficient energy to tunnel through the thin gate oxide to show up as gate current, or as substrate leakage current. In a MOSFET, when a gate is positive, and the switch is on, the device is designed with the intent that electrons will flow laterally through the conductive channel, from the source to the drain. Hot electrons may jump from the channel region or from the drain, for instance, and enter the gate or the substrate. These hot electrons do not contribute to the amount of current flowing through the channel as intended and instead are a leakage current.
Attempts to correct or compensate for the hot electron effect in a MOSFET may involve locating a diode in reverse bias at gate terminal or other manipulations of the device (such as lightly doped drains or double-doped drains).
When electrons are accelerated in the channel, they gain energy along the mean free path. This energy is lost in two different ways:
- The carrier hits an atom in the substrate. Then the collision creates a cold carrier and an additional electron-hole pair. In the case of nMOS transistors, additional electrons are collected by the channel and additional holes are evacuated by the substrate.
- The carrier hits a Si-H bond and break the bond. An interface state is created and the hydrogen atom is released in the substrate.
The probability to hit either an atom or a Si-H bond is random, and the average energy involved in each process is the same in both case.
This is the reason why the substrate current is monitored during HCI stress. A high substrate current means a large number of created electron-hole pairs and thus an efficient Si-H bond breakage mechanism.
When interface states are created, the threshold voltage is modified and the subthreshold slope is degraded. This leads to lower current, and degrades the operating frequency of integrated circuit.
Scaling
Advances in semiconductor manufacturing techniques and ever increasing demand for faster and more complex integrated circuits (ICs) have driven the associated Metal–Oxide–Semiconductor field-effect transistor (MOSFET) to scale to smaller dimensions.
However, it has not been possible to scale the supply voltage used to operate these ICs proportionately due to factors such as compatibility with previous generation circuits, noise margin, power and delay requirements, and non-scaling of threshold voltage, subthreshold slope, and parasitic capacitance.
As a result, internal electric fields increase in aggressively scaled MOSFETs, which comes with the additional benefit of increased carrier velocities (up to velocity saturation), and hence increased switching speed,[9] but also presents a major reliability problem for the long term operation of these devices, as high fields induce hot carrier injection which affects device reliability.
Large electric fields in MOSFETs imply the presence of high-energy carriers, referred to as “hot carriers”. These hot carriers that have sufficiently high energies and momenta to allow them to be injected from the semiconductor into the surrounding dielectric films such as the gate and sidewall oxides as well as the buried oxide in the case of silicon on insulator (SOI) MOSFETs.
Reliability impact
The presence of such mobile carriers in the oxides triggers numerous physical damage processes that can drastically change the device characteristics over prolonged periods. The accumulation of damage can eventually cause the circuit to fail as key parameters such as threshold voltage shift due to such damage. The accumulation of damage resulting degradation in device behavior due to hot carrier injection is called “hot carrier degradation”.
The useful life-time of circuits and integrated circuits based on such a MOS device are thus affected by the life-time of the MOS device itself. To assure that integrated circuits manufactured with minimal geometry devices will not have their useful life impaired, the life-time of the component MOS devices must have their HCI degradation well understood. Failure to accurately characterize HCI life-time effects can ultimately affect business costs such as warranty and support costs and impact marketing and sales promises for a foundry or IC manufacturer.
Relationship to radiation effects
Hot carrier degradation is fundamentally the same as the ionization radiation effect known as the total dose damage to semiconductors, as experienced in space systems due to solar proton, electron, X-ray and gamma ray exposure.
HCI and NOR flash memory cells
HCI is the basis of operation for a number of non-volatile memory technologies such as EPROM cells. As soon as the potential detrimental influence of HC injection on the circuit reliability was recognized, several fabrication strategies were devised to reduce it without compromising the circuit performance.
NOR flash memory exploits the principle of hot carriers injection by deliberately injecting carriers across the gate oxide to charge the floating gate. This charge alters the MOS transistor threshold voltage to represent a logic '0' state. An uncharged floating gate represents a '1' state. Erasing the NOR Flash memory cell removes stored charge through the process of Fowler–Nordheim tunneling.
Because of the damage to the oxide caused by normal NOR Flash operation, HCI damage is one of the factors that cause the number of write-erase cycles to be limited. Because the ability to hold charge and the formation of damage traps in the oxide affects the ability to have distinct '1' and '0' charge states, HCI damage results in the closing of the non-volatile memory logic margin window over time. The number of write-erase cycles at which '1' and '0' can no longer be distinguished defines the endurance of a non-volatile memory.
See also
- Time-dependent gate oxide breakdown (also time-dependent dielectric breakdown, TDDB)
- Electromigration (EM)
- Negative bias temperature instability (NBTI)
- Stress migration
- Lattice scattering
References
- Richard C. Dorf (ed) The Electrical Engineering Handbook, CRC Press, 1993 ISBN 0-8493-0185-8 page 578
External links
- An article about hot carriers at www.siliconfareast.com
- IEEE International Reliability Physics Symposium, the primary academic and technical conference for semiconductor reliability involving HCI and other reliability phenomena
https://en.wikipedia.org/wiki/Hot-carrier_injection
The metal–oxide–semiconductor field-effect transistor (MOSFET, MOS-FET, or MOS FET) is a type of field-effect transistor (FET), most commonly fabricated by the controlled oxidation of silicon. It has an insulated gate, the voltage of which determines the conductivity of the device. This ability to change conductivity with the amount of applied voltage can be used for amplifying or switching electronic signals. A metal-insulator-semiconductor field-effect transistor (MISFET) is a term almost synonymous with MOSFET. Another synonym is IGFET for insulated-gate field-effect transistor.
The basic principle of the field-effect transistor was first patented by Julius Edgar Lilienfeld in 1925.[1]
The main advantage of a MOSFET is that it requires almost no input current to control the load current, when compared with bipolar transistors (bipolar junction transistors/BJTs). In an enhancement mode MOSFET, voltage applied to the gate terminal increases the conductivity of the device. In depletion mode transistors, voltage applied at the gate reduces the conductivity.[2]
The "metal" in the name MOSFET is sometimes a misnomer, because the gate material can be a layer of polysilicon (polycrystalline silicon). Similarly, "oxide" in the name can also be a misnomer, as different dielectric materials are used with the aim of obtaining strong channels with smaller applied voltages.
The MOSFET is by far the most common transistor in digital circuits, as billions may be included in a memory chip or microprocessor. Since MOSFETs can be made with either p-type or n-type semiconductors, complementary pairs of MOS transistors can be used to make switching circuits with very low power consumption, in the form of CMOS logic.
History
The basic principle of this kind of transistor was first patented by Julius Edgar Lilienfeld in 1925.[1]
The structure resembling the MOS transistor was proposed by Bell scientists William Shockley, John Bardeen and Walter Houser Brattain, during their investigation that led to discovery of the transistor effect. The structure failed to show the anticipated effects, due to the problem of surface state: traps on the semiconductor surface that hold electrons immobile. In 1955 Carl Frosch and L. Derick accidentally grew a layer of silicon dioxide over the silicon wafer. Further research showed that silicon dioxide could prevent dopants from diffusing into the silicon wafer. Building on this work Mohamed M. Atalla showed that silicon dioxide is very effective in solving the problem of one important class of surface states.[3]
In 1960s, following this research Mohamed Atalla and Dawon Kahng demonstrated[4] a device that had the structure of a modern MOS transistor. The principles behind the device were the same as the ones that were tried by Bardeen, Shockley and Brattain in their unsuccessful attempt to build a surface field-effect device.
The device was about 100 times slower than contemporary bipolar transistors and was initially seen as inferior. Nevertheless Kahng pointed out several advantages of the device, notably ease of fabrication and its application in integrated circuits.[5]
Composition
Usually the semiconductor of choice is silicon. Recently, some chip manufacturers, most notably IBM and Intel, have started using an alloy of silicon and germanium (SiGe) in MOSFET channels. Unfortunately, many semiconductors with better electrical properties than silicon, such as gallium arsenide, do not form good semiconductor-to-insulator interfaces, and thus are not suitable for MOSFETs. Research continues on creating insulators with acceptable electrical characteristics on other semiconductor materials.
To overcome the increase in power consumption due to gate current leakage, a high-κ dielectric is used instead of silicon dioxide for the gate insulator, while polysilicon is replaced by metal gates (e.g. Intel, 2009[6]).
The gate is separated from the channel by a thin insulating layer, traditionally of silicon dioxide and later of silicon oxynitride. Some companies have started to introduce a high-κ dielectric and metal gate combination in the 45 nanometer node.
When a voltage is applied between the gate and body terminals, the electric field generated penetrates through the oxide and creates an inversion layer or channel at the semiconductor-insulator interface. The inversion layer provides a channel through which current can pass between source and drain terminals. Varying the voltage between the gate and body modulates the conductivity of this layer and thereby controls the current flow between drain and source. This is known as enhancement mode.
Operation
Metal–oxide–semiconductor structure
The traditional metal–oxide–semiconductor (MOS) structure is obtained by growing a layer of silicon dioxide (SiO
2) on top of a silicon substrate, commonly by thermal oxidation and depositing a layer of metal or polycrystalline silicon (the latter is commonly used). As the silicon dioxide is a dielectric material, its structure is equivalent to a planar capacitor, with one of the electrodes replaced by a semiconductor.
When a voltage is applied across a MOS structure, it modifies the distribution of charges in the semiconductor. If we consider a p-type semiconductor (with the density of acceptors, p the density of holes; p = NA in neutral bulk), a positive voltage, , from gate to body (see figure) creates a depletion layer by forcing the positively charged holes away from the gate-insulator/semiconductor interface, leaving exposed a carrier-free region of immobile, negatively charged acceptor ions (see doping (semiconductor)). If is high enough, a high concentration of negative charge carriers forms in an inversion layer located in a thin layer next to the interface between the semiconductor and the insulator.
Conventionally, the gate voltage at which the volume density of electrons in the inversion layer is the same as the volume density of holes in the body is called the threshold voltage. When the voltage between transistor gate and source (VGS) exceeds the threshold voltage (Vth), the difference is known as overdrive voltage.
This structure with p-type body is the basis of the n-type MOSFET, which requires the addition of n-type source and drain regions.
MOS capacitors and band diagrams
The MOS capacitor structure is the heart of the MOSFET. Consider a MOS capacitor where the silicon base is of p-type. If a positive voltage is applied at the gate, holes which are at the surface of the p-type substrate will be repelled by the electric field generated by the voltage applied. At first, the holes will simply be repelled and what will remain on the surface will be immobile (negative) atoms of the acceptor type, which creates a depletion region on the surface. Remember that a hole is created by an acceptor atom, e.g. Boron, which has one less electron than Silicon. One might ask how can holes be repelled if they are actually non-entities? The answer is that what really happens is not that a hole is repelled, but electrons are attracted by the positive field, and fill these holes, creating a depletion region where no charge carriers exist because the electron is now fixed onto the atom and immobile.
As the voltage at the gate increases, there will be a point at which the surface above the depletion region will be converted from p-type into n-type, as electrons from the bulk area will start to get attracted by the larger electric field. This is known as inversion. The threshold voltage at which this conversion happens is one of the most important parameters in a MOSFET.
In the case of a p-type bulk, inversion happens when the intrinsic energy level at the surface becomes smaller than the Fermi level at the surface. One can see this from a band diagram. Remember that the Fermi level defines the type of semiconductor in discussion. If the Fermi level is equal to the Intrinsic level, the semiconductor is of intrinsic, or pure type. If the Fermi level lies closer to the conduction band (valence band) then the semiconductor type will be of n-type (p-type). Therefore, when the gate voltage is increased in a positive sense (for the given example), this will "bend" the intrinsic energy level band so that it will curve downwards towards the valence band. If the Fermi level lies closer to the valence band (for p-type), there will be a point when the Intrinsic level will start to cross the Fermi level and when the voltage reaches the threshold voltage, the intrinsic level does cross the Fermi level, and that is what is known as inversion. At that point, the surface of the semiconductor is inverted from p-type into n-type. Remember that as said above, if the Fermi level lies above the Intrinsic level, the semiconductor is of n-type, therefore at Inversion, when the Intrinsic level reaches and crosses the Fermi level (which lies closer to the valence band), the semiconductor type changes at the surface as dictated by the relative positions of the Fermi and Intrinsic energy levels.
Structure and channel formation
A MOSFET is based on the modulation of charge concentration by a MOS capacitance between a body electrode and a gate electrode located above the body and insulated from all other device regions by a gate dielectric layer. If dielectrics other than an oxide are employed, the device may be referred to as a metal-insulator-semiconductor FET (MISFET). Compared to the MOS capacitor, the MOSFET includes two additional terminals (source and drain), each connected to individual highly doped regions that are separated by the body region. These regions can be either p or n type, but they must both be of the same type, and of opposite type to the body region. The source and drain (unlike the body) are highly doped as signified by a "+" sign after the type of doping.
If the MOSFET is an n-channel or nMOS FET, then the source and drain are n+ regions and the body is a p region. If the MOSFET is a p-channel or pMOS FET, then the source and drain are p+ regions and the body is a n region. The source is so named because it is the source of the charge carriers (electrons for n-channel, holes for p-channel) that flow through the channel; similarly, the drain is where the charge carriers leave the channel.
The occupancy of the energy bands in a semiconductor is set by the position of the Fermi level relative to the semiconductor energy-band edges.
With sufficient gate voltage, the valence band edge is driven far from the Fermi level, and holes from the body are driven away from the gate.
At larger gate bias still, near the semiconductor surface the conduction band edge is brought close to the Fermi level, populating the surface with electrons in an inversion layer or n-channel at the interface between the p region and the oxide. This conducting channel extends between the source and the drain, and current is conducted through it when a voltage is applied between the two electrodes. Increasing the voltage on the gate leads to a higher electron density in the inversion layer and therefore increases the current flow between the source and drain. For gate voltages below the threshold value, the channel is lightly populated, and only a very small subthreshold leakage current can flow between the source and the drain.
When a negative gate-source voltage (positive source-gate) is applied, it creates a p-channel at the surface of the n region, analogous to the n-channel case, but with opposite polarities of charges and voltages. When a voltage less negative than the threshold value (a negative voltage for the p-channel) is applied between gate and source, the channel disappears and only a very small subthreshold current can flow between the source and the drain. The device may comprise a silicon on insulator device in which a buried oxide is formed below a thin semiconductor layer. If the channel region between the gate dielectric and the buried oxide region is very thin, the channel is referred to as an ultrathin channel region with the source and drain regions formed on either side in or above the thin semiconductor layer. Other semiconductor materials may be employed. When the source and drain regions are formed above the channel in whole or in part, they are referred to as raised source/drain regions.
| Parameter | nMOSFET | pMOSFET | |
|---|---|---|---|
| Source/drain type | n-type | p-type | |
|
n-type | p-type | |
|
Polysilicon | n+ | p+ |
| Metal | φm ~ Si conduction band | φm ~ Si valence band | |
| Well type | p-type | n-type | |
| Threshold voltage, Vth |
|
| |
| Band-bending | Downwards | Upwards | |
| Inversion layer carriers | Electrons | Holes | |
| Substrate type | p-type | n-type | |
Modes of operation
The operation of a MOSFET can be separated into three different modes, depending on the voltages at the terminals. In the following discussion, a simplified algebraic model is used.[9] Modern MOSFET characteristics are more complex than the algebraic model presented here.[10]
For an enhancement-mode, n-channel MOSFET, the three operational modes are:
Cutoff, subthreshold, and weak-inversion mode
When VGS < Vth:
where is gate-to-source bias and is the threshold voltage of the device.
According to the basic threshold model, the transistor is turned off, and there is no conduction between drain and source. A more accurate model considers the effect of thermal energy on the Fermi–Dirac distribution of electron energies which allow some of the more energetic electrons at the source to enter the channel and flow to the drain. This results in a subthreshold current that is an exponential function of gate-source voltage. While the current between drain and source should ideally be zero when the transistor is being used as a turned-off switch, there is a weak-inversion current, sometimes called subthreshold leakage.
In weak inversion where the source is tied to bulk, the current varies exponentially with as given approximately by:[11][12]
where = current at , the thermal voltage and the slope factor n is given by:
with = capacitance of the depletion layer and = capacitance of the oxide layer. This equation is generally used, but is only an adequate approximation for the source tied to the bulk. For the source not tied to the bulk, the subthreshold equation for drain current in saturation is[13][14]
In a long-channel device, there is no drain voltage dependence of the current once , but as channel length is reduced drain-induced barrier lowering introduces drain voltage dependence that depends in a complex way upon the device geometry (for example, the channel doping, the junction doping and so on). Frequently, threshold voltage Vth for this mode is defined as the gate voltage at which a selected value of current ID0 occurs, for example, ID0 = 1 μA, which may not be the same Vth-value used in the equations for the following modes.
Some micropower analog circuits are designed to take advantage of subthreshold conduction.[15][16][17] By working in the weak-inversion region, the MOSFETs in these circuits deliver the highest possible transconductance-to-current ratio, namely: , almost that of a bipolar transistor.[18]
The subthreshold I–V curve depends exponentially upon threshold voltage, introducing a strong dependence on any manufacturing variation that affects threshold voltage; for example: variations in oxide thickness, junction depth, or body doping that change the degree of drain-induced barrier lowering. The resulting sensitivity to fabricational variations complicates optimization for leakage and performance.[19][20]
Triode mode or linear region (also known as the ohmic mode)
When VGS > Vth and VDS < VGS − Vth:
The transistor is turned on, and a channel has been created which allows current between the drain and the source. The MOSFET operates like a resistor, controlled by the gate voltage relative to both the source and drain voltages. The current from drain to source is modeled as:
where is the charge-carrier effective mobility, is the gate width, is the gate length and is the gate oxide capacitance per unit area. The transition from the exponential subthreshold region to the triode region is not as sharp as the equations suggest.[21][22][verification needed]
Saturation or active mode
When VGS > Vth and VDS ≥ (VGS – Vth):
The switch is turned on, and a channel has been created, which allows current between the drain and source. Since the drain voltage is higher than the source voltage, the electrons spread out, and conduction is not through a narrow channel but through a broader, two- or three-dimensional current distribution extending away from the interface and deeper in the substrate. The onset of this region is also known as pinch-off to indicate the lack of channel region near the drain. Although the channel does not extend the full length of the device, the electric field between the drain and the channel is very high, and conduction continues. The drain current is now weakly dependent upon drain voltage and controlled primarily by the gate-source voltage, and modeled approximately as:
The additional factor involving λ, the channel-length modulation parameter, models current dependence on drain voltage due to the Early effect, or channel length modulation. According to this equation, a key design parameter, the MOSFET transconductance is:
where the combination Vov = VGS − Vth is called the overdrive voltage,[23] and where VDSsat = VGS − Vth accounts for a small discontinuity in which would otherwise appear at the transition between the triode and saturation regions.
Another key design parameter is the MOSFET output resistance rout given by:
rout is the inverse of gDS where . ID is the expression in saturation region.
If λ is taken as zero, an infinite output resistance of the device results that leads to unrealistic circuit predictions, particularly in analog circuits.
As the channel length becomes very short, these equations become quite inaccurate. New physical effects arise. For example, carrier transport in the active mode may become limited by velocity saturation. When velocity saturation dominates, the saturation drain current is more nearly linear than quadratic in VGS. At even shorter lengths, carriers transport with near zero scattering, known as quasi-ballistic transport. In the ballistic regime, the carriers travel at an injection velocity that may exceed the saturation velocity and approaches the Fermi velocity at high inversion charge density. In addition, drain-induced barrier lowering increases off-state (cutoff) current and requires an increase in threshold voltage to compensate, which in turn reduces the saturation current.[24][25][verification needed]
Body effect
The occupancy of the energy bands in a semiconductor is set by the position of the Fermi level relative to the semiconductor energy-band edges. Application of a source-to-substrate reverse bias of the source-body pn-junction introduces a split between the Fermi levels for electrons and holes, moving the Fermi level for the channel further from the band edge, lowering the occupancy of the channel. The effect is to increase the gate voltage necessary to establish the channel, as seen in the figure. This change in channel strength by application of reverse bias is called the 'body effect'.
Simply put, using an nMOS example, the gate-to-body bias VGB positions the conduction-band energy levels, while the source-to-body bias VSB positions the electron Fermi level near the interface, deciding occupancy of these levels near the interface, and hence the strength of the inversion layer or channel.
The body effect upon the channel can be described using a modification of the threshold voltage, approximated by the following equation:
where VTB is the threshold voltage with substrate bias present, and VT0 is the zero-VSB value of threshold voltage, is the body effect parameter, and 2φB is the approximate potential drop between surface and bulk across the depletion layer when VSB = 0 and gate bias is sufficient to ensure that a channel is present.[26] As this equation shows, a reverse bias VSB > 0 causes an increase in threshold voltage VTB and therefore demands a larger gate voltage before the channel populates.
The body can be operated as a second gate, and is sometimes referred to as the "back gate"; the body effect is sometimes called the "back-gate effect".[27]
Circuit symbols
A variety of symbols are used for the MOSFET. The basic design is generally a line for the channel with the source and drain leaving it at right angles and then bending back at right angles into the same direction as the channel. Sometimes three line segments are used for enhancement mode and a solid line for depletion mode (see depletion and enhancement modes). Another line is drawn parallel to the channel for the gate.
The bulk or body connection, if shown, is shown connected to the back of the channel with an arrow indicating pMOS or nMOS. Arrows always point from P to N, so an NMOS (N-channel in P-well or P-substrate) has the arrow pointing in (from the bulk to the channel). If the bulk is connected to the source (as is generally the case with discrete devices) it is sometimes angled to meet up with the source leaving the transistor. If the bulk is not shown (as is often the case in IC design as they are generally common bulk) an inversion symbol is sometimes used to indicate PMOS, alternatively an arrow on the source may be used in the same way as for bipolar transistors (out for nMOS, in for pMOS).
Comparison of enhancement-mode and depletion-mode MOSFET symbols, along with JFET symbols. The orientation of the symbols, (most significantly the position of source relative to drain) is such that more positive voltages appear higher on the page than less positive voltages, implying conventional current flowing "down" the page:[28][29][30]
| P-channel | 
|

|

|
|

|
|---|---|---|---|---|---|
| N-channel | 
|

|
|
|
|
|
|
JFET | MOSFET enh. | MOSFET enh. (no bulk) | MOSFET dep. | |
In schematics where G, S, D are not labeled, the detailed features of the symbol indicate which terminal is source and which is drain. For enhancement-mode and depletion-mode MOSFET symbols (in columns two and five), the source terminal is the one connected to the triangle. Additionally, in this diagram, the gate is shown as an "L" shape, whose input leg is closer to S than D, also indicating which is which. However, these symbols are often drawn with a "T" shaped gate (as elsewhere on this page), so it is the triangle which must be relied upon to indicate the source terminal.
For the symbols in which the bulk, or body, terminal is shown, it is here shown internally connected to the source (i.e., the black triangles in the diagrams in columns 2 and 5). This is a typical configuration, but by no means the only important configuration. In general, the MOSFET is a four-terminal device, and in integrated circuits many of the MOSFETs share a body connection, not necessarily connected to the source terminals of all the transistors.
Applications
Digital integrated circuits such as microprocessors and memory devices contain thousands to millions to billions of integrated MOSFET transistors on each device, providing the basic switching functions required to implement logic gates and data storage. Discrete devices are widely used in applications such as switch mode power supplies, variable-frequency drives and other power electronics applications where each device may be switching thousands of watts. Radio-frequency amplifiers up to the UHF spectrum use MOSFET transistors as analog signal and power amplifiers. Radio systems also use MOSFETs as oscillators, or mixers to convert frequencies. MOSFET devices are also applied in audio-frequency power amplifiers for public address systems, sound reinforcement and home and automobile sound systems[citation needed]
MOS integrated circuits
Following the development of clean rooms to reduce contamination to levels never before thought necessary, and of photolithography[31] and the planar process to allow circuits to be made in very few steps, the Si–SiO2 system possessed the technical attractions of low cost of production (on a per circuit basis) and ease of integration. Largely because of these two factors, the MOSFET has become the most widely used type of transistor in the Institution of Engineering and Technology (IET).[citation needed]
General Microelectronics introduced the first commercial MOS integrated circuit in 1964.[32] Additionally, the method of coupling two complementary MOSFETs (P-channel and N-channel) into one high/low switch, known as CMOS, means that digital circuits dissipate very little power except when actually switched.
The earliest microprocessors starting in 1970 were all MOS microprocessors; i.e., fabricated entirely from PMOS logic or fabricated entirely from NMOS logic. In the 1970s, MOS microprocessors were often contrasted with CMOS microprocessors and bipolar bit-slice processors.[33]
CMOS circuits
The MOSFET is used in digital complementary metal–oxide–semiconductor (CMOS) logic,[34] which uses p- and n-channel MOSFETs as building blocks. Overheating is a major concern in integrated circuits since ever more transistors are packed into ever smaller chips. CMOS logic reduces power consumption because no current flows (ideally), and thus no power is consumed, except when the inputs to logic gates are being switched. CMOS accomplishes this current reduction by complementing every nMOSFET with a pMOSFET and connecting both gates and both drains together. A high voltage on the gates will cause the nMOSFET to conduct and the pMOSFET not to conduct and a low voltage on the gates causes the reverse. During the switching time as the voltage goes from one state to another, both MOSFETs will conduct briefly. This arrangement greatly reduces power consumption and heat generation.
Digital
The growth of digital technologies like the microprocessor has provided the motivation to advance MOSFET technology faster than any other type of silicon-based transistor.[35] A big advantage of MOSFETs for digital switching is that the oxide layer between the gate and the channel prevents DC current from flowing through the gate, further reducing power consumption and giving a very large input impedance. The insulating oxide between the gate and channel effectively isolates a MOSFET in one logic stage from earlier and later stages, which allows a single MOSFET output to drive a considerable number of MOSFET inputs. Bipolar transistor-based logic (such as TTL) does not have such a high fanout capacity. This isolation also makes it easier for the designers to ignore to some extent loading effects between logic stages independently. That extent is defined by the operating frequency: as frequencies increase, the input impedance of the MOSFETs decreases.
Analog
The MOSFET's advantages in digital circuits do not translate into supremacy in all analog circuits. The two types of circuit draw upon different features of transistor behavior. Digital circuits switch, spending most of their time either fully on or fully off. The transition from one to the other is only of concern with regards to speed and charge required. Analog circuits depend on operation in the transition region where small changes to Vgs can modulate the output (drain) current. The JFET and bipolar junction transistor (BJT) are preferred for accurate matching (of adjacent devices in integrated circuits), higher transconductance and certain temperature characteristics which simplify keeping performance predictable as circuit temperature varies.
Nevertheless, MOSFETs are widely used in many types of analog circuits because of their own advantages (zero gate current, high and adjustable output impedance and improved robustness vs. BJTs which can be permanently degraded by even lightly breaking down the emitter-base).[vague] The characteristics and performance of many analog circuits can be scaled up or down by changing the sizes (length and width) of the MOSFETs used. By comparison, in bipolar transistors follow a different scaling law. MOSFETs' ideal characteristics regarding gate current (zero) and drain-source offset voltage (zero) also make them nearly ideal switch elements, and also make switched capacitor analog circuits practical. In their linear region, MOSFETs can be used as precision resistors, which can have a much higher controlled resistance than BJTs. In high power circuits, MOSFETs sometimes have the advantage of not suffering from thermal runaway as BJTs do.[dubious ] This means that complete analog circuits can be made on a silicon chip in a much smaller space and with simpler fabrication techniques. MOSFETS are ideally suited to switch inductive loads because of tolerance to inductive kickback.
Some ICs combine analog and digital MOSFET circuitry on a single mixed-signal integrated circuit, making the needed board space even smaller. This creates a need to isolate the analog circuits from the digital circuits on a chip level, leading to the use of isolation rings and silicon on insulator (SOI). Since MOSFETs require more space to handle a given amount of power than a BJT, fabrication processes can incorporate BJTs and MOSFETs into a single device. Mixed-transistor devices are called bi-FETs (bipolar FETs) if they contain just one BJT-FET and BiCMOS (bipolar-CMOS) if they contain complementary BJT-FETs. Such devices have the advantages of both insulated gates and higher current density.
Analog switches
MOSFET analog switches use the MOSFET to pass analog signals when on, and as a high impedance when off. Signals flow in both directions across a MOSFET switch. In this application, the drain and source of a MOSFET exchange places depending on the relative voltages of the source/drain electrodes. The source is the more negative side for an N-MOS or the more positive side for a P-MOS. All of these switches are limited on what signals they can pass or stop by their gate-source, gate-drain and source–drain voltages; exceeding the voltage, current, or power limits will potentially damage the switch.
Single-type
This analog switch uses a four-terminal simple MOSFET of either P or N type.
In the case of an n-type switch, the body is connected to the most negative supply (usually GND) and the gate is used as the switch control. Whenever the gate voltage exceeds the source voltage by at least a threshold voltage, the MOSFET conducts. The higher the voltage, the more the MOSFET can conduct. An N-MOS switch passes all voltages less than Vgate − Vtn. When the switch is conducting, it typically operates in the linear (or ohmic) mode of operation, since the source and drain voltages will typically be nearly equal.
In the case of a P-MOS, the body is connected to the most positive voltage, and the gate is brought to a lower potential to turn the switch on. The P-MOS switch passes all voltages higher than Vgate − Vtp (threshold voltage Vtp is negative in the case of enhancement-mode P-MOS).
Dual-type (CMOS)
This "complementary" or CMOS type of switch uses one P-MOS and one N-MOS FET to counteract the limitations of the single-type switch. The FETs have their drains and sources connected in parallel, the body of the P-MOS is connected to the high potential (VDD) and the body of the N-MOS is connected to the low potential (gnd). To turn the switch on, the gate of the P-MOS is driven to the low potential and the gate of the N-MOS is driven to the high potential. For voltages between VDD − Vtn and gnd − Vtp, both FETs conduct the signal; for voltages less than gnd − Vtp, the N-MOS conducts alone; and for voltages greater than VDD − Vtn, the P-MOS conducts alone.
The voltage limits for this switch are the gate-source, gate-drain and source-drain voltage limits for both FETs. Also, the P-MOS is typically two to three times wider than the N-MOS, so the switch will be balanced for speed in the two directions.
Tri-state circuitry sometimes incorporates a CMOS MOSFET switch on its output to provide for a low-ohmic, full-range output when on, and a high-ohmic, mid-level signal when off.
Construction
Gate material
The primary criterion for the gate material is that it is a good conductor. Highly doped polycrystalline silicon is an acceptable but certainly not ideal conductor, and also suffers from some more technical deficiencies in its role as the standard gate material. Nevertheless, there are several reasons favoring use of polysilicon:
- The threshold voltage (and consequently the drain to source on-current) is modified by the work function difference between the gate material and channel material. Because polysilicon is a semiconductor, its work function can be modulated by adjusting the type and level of doping. Furthermore, because polysilicon has the same bandgap as the underlying silicon channel, it is quite straightforward to tune the work function to achieve low threshold voltages for both NMOS and PMOS devices. By contrast, the work functions of metals are not easily modulated, so tuning the work function to obtain low threshold voltages (LVT) becomes a significant challenge. Additionally, obtaining low-threshold devices on both PMOS and NMOS devices sometimes requires the use of different metals for each device type.
- The silicon-SiO2 interface has been well studied and is known to have relatively few defects. By contrast many metal-insulator interfaces contain significant levels of defects which can lead to Fermi level pinning, charging, or other phenomena that ultimately degrade device performance.
- In the MOSFET IC fabrication process, it is preferable to deposit the gate material prior to certain high-temperature steps in order to make better-performing transistors. Such high temperature steps would melt some metals, limiting the types of metal that can be used in a metal-gate-based process.
While polysilicon gates have been the de facto standard for the last twenty years, they do have some disadvantages which have led to their likely future replacement by metal gates. These disadvantages include:
- Polysilicon is not a great conductor (approximately 1000 times more resistive than metals) which reduces the signal propagation speed through the material. The resistivity can be lowered by increasing the level of doping, but even highly doped polysilicon is not as conductive as most metals. To improve conductivity further, sometimes a high-temperature metal such as tungsten, titanium, cobalt, and more recently nickel is alloyed with the top layers of the polysilicon. Such a blended material is called silicide. The silicide-polysilicon combination has better electrical properties than polysilicon alone and still does not melt in subsequent processing. Also the threshold voltage is not significantly higher than with polysilicon alone, because the silicide material is not near the channel. The process in which silicide is formed on both the gate electrode and the source and drain regions is sometimes called salicide, self-aligned silicide.
- When the transistors are extremely scaled down, it is necessary to make the gate dielectric layer very thin, around 1 nm in state-of-the-art technologies. A phenomenon observed here is the so-called poly depletion, where a depletion layer is formed in the gate polysilicon layer next to the gate dielectric when the transistor is in the inversion. To avoid this problem, a metal gate is desired. A variety of metal gates such as tantalum, tungsten, tantalum nitride, and titanium nitride are used, usually in conjunction with high-κ dielectrics. An alternative is to use fully silicided polysilicon gates, a process known as FUSI.
Present high performance CPUs use metal gate technology, together with high-κ dielectrics, a combination known as high-κ, metal gate (HKMG). The disadvantages of metal gates are overcome by a few techniques:[36]
- The threshold voltage is tuned by including a thin "work function metal" layer between the high-κ dielectric and the main metal. This layer is thin enough that the total work function of the gate is influenced by both the main metal and thin metal work functions (either due to alloying during annealing, or simply due to the incomplete screening by the thin metal). The threshold voltage thus can be tuned by the thickness of the thin metal layer.
- High-κ dielectrics are now well studied, and their defects are understood.
- HKMG processes exist that do not require the metals to experience high temperature anneals; other processes select metals that can survive the annealing step.
Insulator
As devices are made smaller, insulating layers are made thinner, often through steps of thermal oxidation or localised oxidation of silicon (LOCOS). For nano-scaled devices, at some point tunneling of carriers through the insulator from the channel to the gate electrode takes place. To reduce the resulting leakage current, the insulator can be made thinner by choosing a material with a higher dielectric constant. To see how thickness and dielectric constant are related, note that Gauss's law connects field to charge as:
with Q = charge density, κ = dielectric constant, ε0 = permittivity of empty space and E = electric field. From this law it appears the same charge can be maintained in the channel at a lower field provided κ is increased. The voltage on the gate is given by:
with VG = gate voltage, Vch = voltage at channel side of insulator, and tins = insulator thickness. This equation shows the gate voltage will not increase when the insulator thickness increases, provided κ increases to keep tins / κ = constant (see the article on high-κ dielectrics for more detail, and the section in this article on gate-oxide leakage).
The insulator in a MOSFET is a dielectric which can in any event be silicon oxide, formed by LOCOS but many other dielectric materials are employed. The generic term for the dielectric is gate dielectric since the dielectric lies directly below the gate electrode and above the channel of the MOSFET.
Junction design
The source-to-body and drain-to-body junctions are the object of much attention because of three major factors: their design affects the current-voltage (I-V) characteristics of the device, lowering output resistance, and also the speed of the device through the loading effect of the junction capacitances, and finally, the component of stand-by power dissipation due to junction leakage.
The drain induced barrier lowering of the threshold voltage and channel length modulation effects upon I-V curves are reduced by using shallow junction extensions. In addition, halo doping can be used, that is, the addition of very thin heavily doped regions of the same doping type as the body tight against the junction walls to limit the extent of depletion regions.[37]
The capacitive effects are limited by using raised source and drain geometries that make most of the contact area border thick dielectric instead of silicon.[38]
These various features of junction design are shown (with artistic license) in the figure.
Scaling
This section is written like a personal reflection, personal essay, or argumentative essay that states a Wikipedia editor's personal feelings or presents an original argument about a topic. (September 2016) |
Over the past decades, the MOSFET (as used for digital logic) has continually been scaled down in size; typical MOSFET channel lengths were once several micrometres, but modern integrated circuits are incorporating MOSFETs with channel lengths of tens of nanometers. Robert Dennard's work on scaling theory was pivotal in recognising that this ongoing reduction was possible. Intel began production of a process featuring a 32 nm feature size (with the channel being even shorter) in late 2009. The semiconductor industry maintains a "roadmap", the ITRS,[39] which sets the pace for MOSFET development. Historically, the difficulties with decreasing the size of the MOSFET have been associated with the semiconductor device fabrication process, the need to use very low voltages, and with poorer electrical performance necessitating circuit redesign and innovation (small MOSFETs exhibit higher leakage currents and lower output resistance).
Smaller MOSFETs are desirable for several reasons. The main reason to make transistors smaller is to pack more and more devices in a given chip area. This results in a chip with the same functionality in a smaller area, or chips with more functionality in the same area. Since fabrication costs for a semiconductor wafer are relatively fixed, the cost per integrated circuits is mainly related to the number of chips that can be produced per wafer. Hence, smaller ICs allow more chips per wafer, reducing the price per chip. In fact, over the past 30 years the number of transistors per chip has been doubled every 2–3 years once a new technology node is introduced. For example, the number of MOSFETs in a microprocessor fabricated in a 45 nm technology can well be twice as many as in a 65 nm chip. This doubling of transistor density was first observed by Gordon Moore in 1965 and is commonly referred to as Moore's law.[40] It is also expected that smaller transistors switch faster. For example, one approach to size reduction is a scaling of the MOSFET that requires all device dimensions to reduce proportionally. The main device dimensions are the channel length, channel width, and oxide thickness. When they are scaled down by equal factors, the transistor channel resistance does not change, while gate capacitance is cut by that factor. Hence, the RC delay of the transistor scales with a similar factor. While this has been traditionally the case for the older technologies, for the state-of-the-art MOSFETs reduction of the transistor dimensions does not necessarily translate to higher chip speed because the delay due to interconnections is more significant.
Producing MOSFETs with channel lengths much smaller than a micrometre is a challenge, and the difficulties of semiconductor device fabrication are always a limiting factor in advancing integrated circuit technology. Though processes such as ALD have improved fabrication for small components, the small size of the MOSFET (less than a few tens of nanometers) has created operational problems:
Higher subthreshold conduction
As MOSFET geometries shrink, the voltage that can be applied to the gate must be reduced to maintain reliability. To maintain performance, the threshold voltage of the MOSFET has to be reduced as well. As threshold voltage is reduced, the transistor cannot be switched from complete turn-off to complete turn-on with the limited voltage swing available; the circuit design is a compromise between strong current in the on case and low current in the off case, and the application determines whether to favor one over the other. Subthreshold leakage (including subthreshold conduction, gate-oxide leakage and reverse-biased junction leakage), which was ignored in the past, now can consume upwards of half of the total power consumption of modern high-performance VLSI chips.[41][42]
Increased gate-oxide leakage
The gate oxide, which serves as insulator between the gate and channel, should be made as thin as possible to increase the channel conductivity and performance when the transistor is on and to reduce subthreshold leakage when the transistor is off. However, with current gate oxides with a thickness of around 1.2 nm (which in silicon is ~5 atoms thick) the quantum mechanical phenomenon of electron tunneling occurs between the gate and channel, leading to increased power consumption. Silicon dioxide has traditionally been used as the gate insulator. Silicon dioxide however has a modest dielectric constant. Increasing the dielectric constant of the gate dielectric allows a thicker layer while maintaining a high capacitance (capacitance is proportional to dielectric constant and inversely proportional to dielectric thickness). All else equal, a higher dielectric thickness reduces the quantum tunneling current through the dielectric between the gate and the channel.
Insulators that have a larger dielectric constant than silicon dioxide (referred to as high-κ dielectrics), such as group IVb metal silicates e.g. hafnium and zirconium silicates and oxides are being used to reduce the gate leakage from the 45 nanometer technology node onwards. On the other hand, the barrier height of the new gate insulator is an important consideration; the difference in conduction band energy between the semiconductor and the dielectric (and the corresponding difference in valence band energy) also affects leakage current level. For the traditional gate oxide, silicon dioxide, the former barrier is approximately 8 eV. For many alternative dielectrics the value is significantly lower, tending to increase the tunneling current, somewhat negating the advantage of higher dielectric constant. The maximum gate-source voltage is determined by the strength of the electric field able to be sustained by the gate dielectric before significant leakage occurs. As the insulating dielectric is made thinner, the electric field strength within it goes up for a fixed voltage. This necessitates using lower voltages with the thinner dielectric.
Increased junction leakage
To make devices smaller, junction design has become more complex, leading to higher doping levels, shallower junctions, "halo" doping and so forth,[43][44] all to decrease drain-induced barrier lowering (see the section on junction design). To keep these complex junctions in place, the annealing steps formerly used to remove damage and electrically active defects must be curtailed[45] increasing junction leakage. Heavier doping is also associated with thinner depletion layers and more recombination centers that result in increased leakage current, even without lattice damage.
Drain-induced barrier lowering and VT roll off
Drain-induced barrier lowering (DIBL) and VT roll off: Because of the short-channel effect, channel formation is not entirely done by the gate, but now the drain and source also affect the channel formation. As the channel length decreases, the depletion regions of the source and drain come closer together and make the threshold voltage (VT) a function of the length of the channel. This is called VT roll-off. VT also becomes function of drain to source voltage VDS. As we increase the VDS, the depletion regions increase in size, and a considerable amount of charge is depleted by the VDS. The gate voltage required to form the channel is then lowered, and thus, the VT decreases with an increase in VDS. This effect is called drain induced barrier lowering (DIBL).
Lower output resistance
For analog operation, good gain requires a high MOSFET output impedance, which is to say, the MOSFET current should vary only slightly with the applied drain-to-source voltage. As devices are made smaller, the influence of the drain competes more successfully with that of the gate due to the growing proximity of these two electrodes, increasing the sensitivity of the MOSFET current to the drain voltage. To counteract the resulting decrease in output resistance, circuits are made more complex, either by requiring more devices, for example the cascode and cascade amplifiers, or by feedback circuitry using operational amplifiers, for example a circuit like that in the adjacent figure.
Lower transconductance
The transconductance of the MOSFET decides its gain and is proportional to hole or electron mobility (depending on device type), at least for low drain voltages. As MOSFET size is reduced, the fields in the channel increase and the dopant impurity levels increase. Both changes reduce the carrier mobility, and hence the transconductance. As channel lengths are reduced without proportional reduction in drain voltage, raising the electric field in the channel, the result is velocity saturation of the carriers, limiting the current and the transconductance.
Interconnect capacitance
Traditionally, switching time was roughly proportional to the gate capacitance of gates. However, with transistors becoming smaller and more transistors being placed on the chip, interconnect capacitance (the capacitance of the metal-layer connections between different parts of the chip) is becoming a large percentage of capacitance.[46][47] Signals have to travel through the interconnect, which leads to increased delay and lower performance.
Heat production
The ever-increasing density of MOSFETs on an integrated circuit creates problems of substantial localized heat generation that can impair circuit operation. Circuits operate more slowly at high temperatures, and have reduced reliability and shorter lifetimes. Heat sinks and other cooling devices and methods are now required for many integrated circuits including microprocessors. Power MOSFETs are at risk of thermal runaway. As their on-state resistance rises with temperature, if the load is approximately a constant-current load then the power loss rises correspondingly, generating further heat. When the heatsink is not able to keep the temperature low enough, the junction temperature may rise quickly and uncontrollably, resulting in destruction of the device.
Process variations
With MOSFETs becoming smaller, the number of atoms in the silicon that produce many of the transistor's properties is becoming fewer, with the result that control of dopant numbers and placement is more erratic. During chip manufacturing, random process variations affect all transistor dimensions: length, width, junction depths, oxide thickness etc., and become a greater percentage of overall transistor size as the transistor shrinks. The transistor characteristics become less certain, more statistical. The random nature of manufacture means we do not know which particular example MOSFETs actually will end up in a particular instance of the circuit. This uncertainty forces a less optimal design because the design must work for a great variety of possible component MOSFETs. See process variation, design for manufacturability, reliability engineering, and statistical process control.[48]
Modeling challenges
Modern ICs are computer-simulated with the goal of obtaining working circuits from the very first manufactured lot. As devices are miniaturized, the complexity of the processing makes it difficult to predict exactly what the final devices look like, and modeling of physical processes becomes more challenging as well. In addition, microscopic variations in structure due simply to the probabilistic nature of atomic processes require statistical (not just deterministic) predictions. These factors combine to make adequate simulation and "right the first time" manufacture difficult.
Other types
Dual-gate
The dual-gate MOSFET has a tetrode configuration, where both gates control the current in the device. It is commonly used for small-signal devices in radio frequency applications where biasing the drain-side gate at constant potential reduces the gain loss caused by Miller effect, replacing two separate transistors in cascode configuration. Other common uses in RF circuits include gain control and mixing (frequency conversion). The tetrode description, though accurate, does not replicate the vacuum-tube tetrode. Vacuum-tube tetrodes, using a screen grid, exhibit much lower grid-plate capacitance and much higher output impedance and voltage gains than triode vacuum tubes. These improvements are commonly an order of magnitude (10 times) or considerably more. Tetrode transistors (whether bipolar junction or field-effect) do not exhibit improvements of such a great degree.
The FinFET is a double-gate silicon-on-insulator device, one of a number of geometries being introduced to mitigate the effects of short channels and reduce drain-induced barrier lowering. The fin refers to the narrow channel between source and drain. A thin insulating oxide layer on either side of the fin separates it from the gate. SOI FinFETs with a thick oxide on top of the fin are called double-gate and those with a thin oxide on top as well as on the sides are called triple-gate FinFETs.[49][50]
Depletion-mode
There are depletion-mode MOSFET devices, which are less commonly used than the standard enhancement-mode devices already described. These are MOSFET devices that are doped so that a channel exists even with zero voltage from gate to source. To control the channel, a negative voltage is applied to the gate (for an n-channel device), depleting the channel, which reduces the current flow through the device. In essence, the depletion-mode device is equivalent to a normally closed (on) switch, while the enhancement-mode device is equivalent to a normally open (off) switch.[51]
Due to their low noise figure in the RF region, and better gain, these devices are often preferred to bipolars in RF front-ends such as in TV sets.
Depletion-mode MOSFET families include BF960 by Siemens and Telefunken, and the BF980 in the 1980s by Philips (later to become NXP Semiconductors), whose derivatives are still used in AGC and RF mixer front-ends.
Metal-insulator-semiconductor field-effect transistor (MISFET)
Metal-insulator-semiconductor field-effect-transistor,[52][53][54] or MISFET, is a more general term than MOSFET and a synonym to insulated-gate field-effect transistor (IGFET). All MOSFETs are MISFETs, but not all MISFETs are MOSFETs.
The gate dielectric insulator in a MISFET is silicon dioxide in a MOSFET, but other materials can also be employed. The gate dielectric lies directly below the gate electrode and above the channel of the MISFET. The term metal is historically used for the gate material, even though now it is usually highly doped polysilicon or some other non-metal.
Insulator types may be:
- Silicon dioxide, in MOSFETs
- Organic insulators (e.g., undoped trans-polyacetylene; cyanoethyl pullulan, CEP[55]), for organic-based FETs.[54]
NMOS logic
For devices of equal current driving capability, n-channel MOSFETs can be made smaller than p-channel MOSFETs, due to p-channel charge carriers (holes) having lower mobility than do n-channel charge carriers (electrons), and producing only one type of MOSFET on a silicon substrate is cheaper and technically simpler. These were the driving principles in the design of NMOS logic which uses n-channel MOSFETs exclusively. However, neglecting leakage current, unlike CMOS logic, NMOS logic consumes power even when no switching is taking place. With advances in technology, CMOS logic displaced NMOS logic in the mid-1980s to become the preferred process for digital chips.
Power MOSFET
Power MOSFETs have a different structure.[56] As with most power devices, the structure is vertical and not planar. Using a vertical structure, it is possible for the transistor to sustain both high blocking voltage and high current. The voltage rating of the transistor is a function of the doping and thickness of the N-epitaxial layer (see cross section), while the current rating is a function of the channel width (the wider the channel, the higher the current). In a planar structure, the current and breakdown voltage ratings are both a function of the channel dimensions (respectively width and length of the channel), resulting in inefficient use of the "silicon estate". With the vertical structure, the component area is roughly proportional to the current it can sustain, and the component thickness (actually the N-epitaxial layer thickness) is proportional to the breakdown voltage.[57]
Power MOSFETs with lateral structure are mainly used in high-end audio amplifiers and high-power PA systems. Their advantage is a better behaviour in the saturated region (corresponding to the linear region of a bipolar transistor) than the vertical MOSFETs. Vertical MOSFETs are designed for switching applications.[58]
Double-diffused metal–oxide–semiconductor (DMOS)
There are LDMOS (lateral double-diffused metal oxide semiconductor) and VDMOS (vertical double-diffused metal oxide semiconductor). Most power MOSFETs are made using this technology.
Radiation-hardened-by-design (RHBD)
Semiconductor sub-micrometer and nanometer electronic circuits are the primary concern for operating within the normal tolerance in harsh radiation environments like outer space. One of the design approaches for making a radiation-hardened-by-design (RHBD) device is enclosed-layout-transistor (ELT). Normally, the gate of the MOSFET surrounds the drain, which is placed in the center of the ELT. The source of the MOSFET surrounds the gate. Another RHBD MOSFET is called H-Gate. Both of these transistors have very low leakage currents with respect to radiation. However, they are large in size and take up more space on silicon than a standard MOSFET. In older STI (shallow trench isolation) designs, radiation strikes near the silicon oxide region cause the channel inversion at the corners of the standard MOSFET due to accumulation of radiation induced trapped charges. If the charges are large enough, the accumulated charges affect STI surface edges along the channel near the channel interface (gate) of the standard MOSFET. This causes a device channel inversion to occur along the channel edges, creating an off-state leakage path. Subsequently, the device turns on; this process severely degrades the reliability of circuits. The ELT offers many advantages, including an improvement of reliability by reducing unwanted surface inversion at the gate edges which occurs in the standard MOSFET. Since the gate edges are enclosed in ELT, there is no gate oxide edge (STI at gate interface), and thus the transistor off-state leakage is reduced very much. Low-power microelectronic circuits including computers, communication devices, and monitoring systems in space shuttles and satellites are very different from what is used on earth. They are radiation (high-speed atomic particles like proton and neutron, solar flare magnetic energy dissipation in Earth's space, energetic cosmic rays like X-ray, gamma ray etc.) tolerant circuits. These special electronics are designed by applying different techniques using RHBD MOSFETs to ensure safe space journeys and safe space-walks of astronauts.
See also
- Floating-gate MOSFET – Type of MOSFET where the gate is electrically isolated
- BSIM – Family of MOSFET transistor models for integrated circuit design
- ggNMOS – Electrostatic discharge (ESD) protection device
- High-electron-mobility transistor – Type of field-effect transistor
- Polysilicon depletion effect – Variation of threshold voltage in polycrystalline silicon materials
- Transistor model – Simulation of physical processes taking place in an electronic device
- Intrinsic diode – MOSFET that can handle significant power levels
References
- "Power MOSFET Basics: Understanding Gate Charge and Using It To Assess Switching Performance". element14. Archived from the original on 30 June 2014. Retrieved 27 November 2010.
External links
This article's use of external links may not follow Wikipedia's policies or guidelines. (September 2016) |
- How Semiconductors and Transistors Work (MOSFETs) WeCanFigureThisOut.org
- "Understanding power MOSFET data sheet parameters – Nexperia PDF Application Note AN11158" (PDF). Archived (PDF) from the original on 2022-10-09.
- "An introduction to depletion-mode MOSFETs". Archived from the original on 28 September 2008.
- "Power MOSFETs". Archived from the original on 2012-07-06. Retrieved 2010-03-04.
- "Criteria for Successful Selection of IGBT and MOSFET Modules". Archived from the original on 2012-11-12. Retrieved 2018-12-16.
- "MOSFET Process Step by Step". Archived from the original on 2009-08-22. Retrieved 2016-02-06. A Flash slide showing the fabricating process of a MOSFET in detail
- "MOSFET Calculator". Archived from the original on 2008-05-27. Retrieved 2008-06-03.
- "Advanced MOSFET issues". ecee.colorado.edu. 27 November 2010.
- "MOSFET applet".
- Nicolai, Ulrich; Reimann, Tobias; Petzoldt, Jürgen; Lutz, Josef (1998). Application Manual IGBT and MOSFET Power Modules (1st ed.). ISLE Verlag. ISBN 978-3-932633-24-9. Archived from the original on 2 March 2012.
- Wintrich, Arendt; Nicolai, Ulrich; Tursky, Werner; Reimann, Tobias (2011). PDF-Version (PDF) (2nd ed.). Nuremberg: Semikron. ISBN 978-3-938843-66-6. Archived from the original (PDF) on 3 September 2013.
- "MIT Open Courseware 6.002 – Spring 2007".
- "MIT Open Courseware 6.012 – Fall 2009".
- "Georgia Tech BJT and FET Slides".
- "CircuitDesign: MOS Diffusion Parasitics".
- Lundstrom, Mark (2008). "Course on Physics of Nanoscale Transistors". nanoHUB Papers.
- Lundstrom, Mark (2005). "Notes on Ballistic MOSFETs". nanoHUB Papers.
https://en.wikipedia.org/wiki/MOSFET
Fowler–Nordheim tunneling
Introduction
The next part of this article deals with the basic theory of cold field electron emission from bulk metals. This is best treated in four main stages, involving theory associated with: (1) derivation of a formula for "escape probability", by considering electron tunneling through a rounded triangular barrier; (2) an integration over internal electron states to obtain the "total energy distribution"; (3) a second integration, to obtain the emission current density as a function of local barrier field and local work function; (4) conversion of this to a formula for current as a function of applied voltage. The modified equations needed for large-area emitters, and issues of experimental data analysis, are dealt with separately.
Fowler–Nordheim tunneling is the wave-mechanical tunneling of an electron through an exact or rounded triangular barrier. Two basic situations are recognized: (1) when the electron is initially in a localized state; (2) when the electron is initially not strongly localized, and is best represented by a travelling wave. Emission from a bulk metal conduction band is a situation of the second type, and discussion here relates to this case. It is also assumed that the barrier is one-dimensional (i.e., has no lateral structure), and has no fine-scale structure that causes "scattering" or "resonance" effects. To keep this explanation of Fowler–Nordheim tunneling relatively simple, these assumptions are needed; but the atomic structure of matter is in effect being disregarded.
https://en.wikipedia.org/wiki/Field_electron_emission#Fowler%E2%80%93Nordheim_tunneling
A neural network can refer to either a neural circuit of biological neurons (sometimes also called a biological neural network), or a network of artificial neurons or nodes in the case of an artificial neural network.[1] Artificial neural networks are used for solving artificial intelligence (AI) problems; they model connections of biological neurons as weights between nodes. A positive weight reflects an excitatory connection, while negative values mean inhibitory connections. All inputs are modified by a weight and summed. This activity is referred to as a linear combination. Finally, an activation function controls the amplitude of the output. For example, an acceptable range of output is usually between 0 and 1, or it could be −1 and 1.
These artificial networks may be used for predictive modeling, adaptive control and applications where they can be trained via a dataset. Self-learning resulting from experience can occur within networks, which can derive conclusions from a complex and seemingly unrelated set of information.[2]
https://en.wikipedia.org/wiki/Neural_network
A digital potentiometer (also called a resistive digital-to-analog converter,[1] or informally a digipot) is a digitally-controlled electronic component that mimics the analog functions of a potentiometer. It is often used for trimming and scaling analog signals by microcontrollers.
Design
A digital potentiometer is built either from a resistor ladder integrated circuit or a digital-to-analog converter although a resistor ladder construction is the more common.[citation needed] Every step on the resistor ladder has its own switch which can connect this step to the output terminal of the potentiometer. The selected step on the ladder determines the resistance ratio of the digital potentiometer. The number of steps is normally indicated with a bit value e.g. 8 bits equals 256 steps; 8 bits is the most common, but resolutions between 5 and 10 bits (32 to 1024 steps) are available.[2] A digital potentiometer uses digital protocols like I²C or Serial Peripheral Interface Bus for signalling; some use simpler up/down protocols. Some typical uses of digital potentiometers are in circuits requiring gain control of amplifiers (frequently instrumentation amplifiers), small-signal audio-balancing, and offset adjustment.
The resistor material can be for e.g. Poly-Silicon or Thin-Film Resistors.[3]
Most digital potentiometers use only volatile memory, which means they forget their position when they are powered down (on power up they will report a default value, often their midpoint value) - when these are used, their last position may be stored by the microcontroller or FPGA to which they are interfaced. Some digipots do include their own non-volatile storage,[4] so their default reading on power up will be the same as they showed before they were powered down.[5]
Limitations
While quite similar to normal potentiometers, digital potentiometers are constrained by current limit in the range of tens of milliamperes. Also, most digital potentiometers limit the voltage range on the two input terminals (of the resistor) to the digital supply range (e.g. 0–5 VDC), so additional circuitry maybe required to replace a conventional potentiometer. (Altough Digitalpotentiometers with separate Dual Supply Analog Voltages are also available.[6]) Further, instead of the seemingly continuous control that can be obtained from a multiturn resistive potentiometer, digital potentiometers have discrete steps in resistance.
Another constraint is that special logic is often required to check for zero crossing of an analog AC signal to allow the resistance value to be changed without causing an audible click in the output for audio amplifiers. (Schematic needed)
Volatile digital potentiometers also differ from electro-mechanical ones in that on power up, the resistance will default to (possibly) a different value after a power cycle. Similarly, their resistance is only valid when the correct DC supply voltage is present. When voltage is removed, the resistance between the two end points and the (nominal) wiper are undefined. In an operational amplifier circuit, the off-state impedance of a real potentiometer can help stabilize the DC operating point of the circuit during the power-up stage. This may not be the case when a digital potentiometer is used.
Both electro-mechanical and digital potentiometers generally have poor tolerances (typically ±20%[7]), poor temperature coefficients[8] (upto many hundreds of ppm per degree C[8]), and a stop resistance that is typically about 0.5-1% of the full scale resistance. Note that stop resistance is the residual resistance when the terminal to wiper resistance is set to the minimum value.[citation needed]
With a digital potentiometer, the resistance might be depended on supply voltage.[7]
Digital potentiometer have a limited band width due to parasitic capacitance in device. Parts with lower End-To-End resistance typically have a greater band width.
The transmission gate/switching element in the Digital potentiometer cause harmonic distortions.
A multiplying DAC used as a digital potentiometer[9] can eliminate most of these limitations. Typically a signal span of +15V to -15V is possible, with 16 bit control, i.e. 65535 discrete set points, and drift and non-linearity are negligible. However a DAC has to be initialised each time the system is powered on, which is typically done by software in an embedded microcontroller. A multiplying DAC can not be directly used as a rheostat (2 wire connection), but in that mode a digipot performs badly anyway, due to its temperature coefficient and resistance tolerance.[citation needed]
Applications
- LCD-Contrast/Brightness
- Sensor Calibration
- Digital Volume Control
- Programmable Comperators
- Programmable Low/High Pass Filters
Alternatives
See also
References
External links
https://en.wikipedia.org/wiki/Digital_potentiometer
The memory cell is the fundamental building block of computer memory. The memory cell is an electronic circuit that stores one bit of binary information and it must be set to store a logic 1 (high voltage level) and reset to store a logic 0 (low voltage level). Its value is maintained/stored until it is changed by the set/reset process. The value in the memory cell can be accessed by reading it.
Over the history of computing, different memory cell architectures have been used, including core memory and bubble memory. Today, the most common memory cell architecture is MOS memory, which consists of metal–oxide–semiconductor (MOS) memory cells. Modern random-access memory (RAM) uses MOS field-effect transistors (MOSFETs) as flip-flops, along with MOS capacitors for certain types of RAM.
The SRAM (static RAM) memory cell is a type of flip-flop circuit, typically implemented using MOSFETs. These require very low power to keep the stored value when not being accessed. A second type, DRAM (dynamic RAM), is based around MOS capacitors. Charging and discharging a capacitor can store a '1' or a '0' in the cell. However, the charge in this capacitor will slowly leak away, and must be refreshed periodically. Because of this refresh process, DRAM uses more power. However, DRAM can achieve greater storage densities.
On the other hand, most non-volatile memory (NVM) is based on floating-gate memory cell architectures. Non-volatile memory technologies including EPROM, EEPROM and flash memory use floating-gate memory cells, which are based around floating-gate MOSFET transistors.
Description
The memory cell is the fundamental building block of memory. It can be implemented using different technologies, such as bipolar, MOS, and other semiconductor devices. It can also be built from magnetic material such as ferrite cores or magnetic bubbles.[1] Regardless of the implementation technology used, the purpose of the binary memory cell is always the same. It stores one bit of binary information that can be accessed by reading the cell and it must be set to store a 1 and reset to store a 0.[2]
Significance
Logic circuits without memory cells are called combinational, meaning the output depends only on the present input. But memory is a key element of digital systems. In computers, it allows to store both programs and data and memory cells are also used for temporary storage of the output of combinational circuits to be used later by digital systems. Logic circuits that use memory cells are called sequential circuits, meaning the output depends not only on the present input, but also on the history of past inputs. This dependence on the history of past inputs makes these circuits stateful and it is the memory cells that store this state. These circuits require a timing generator or clock for their operation.[3]
Computer memory used in most contemporary computer systems is built mainly out of DRAM cells; since the layout is much smaller than SRAM, it can be more densely packed yielding cheaper memory with greater capacity. Since the DRAM memory cell stores its value as the charge of a capacitor, and there are current leakage issues, its value must be constantly rewritten. This is one of the reasons that make DRAM cells slower than the larger SRAM (static RAM) cells, which has its value always available. That is the reason why SRAM memory is used for on-chip cache included in modern microprocessor chips.[4]
History
On December 11, 1946 Freddie Williams applied for a patent on his cathode-ray tube (CRT) storing device (Williams tube) with 128 40-bit words. It was operational in 1947 and is considered the first practical implementation of random-access memory (RAM).[5] In that year, the first patent applications for magnetic-core memory were filed by Frederick Viehe.[6][7] Practical magnetic-core memory was developed by An Wang in 1948, and improved by Jay Forrester and Jan A. Rajchman in the early 1950s, before being commercialised with the Whirlwind computer in 1953.[8] Ken Olsen also contributed to its development.[9]
Semiconductor memory began in the early 1960s with bipolar memory cells, made of bipolar transistors. While it improved performance, it could not compete with the lower price of magnetic-core memory.[10]
MOS memory cells
The invention of the MOSFET (metal–oxide–semiconductor field-effect transistor), also known as the MOS transistor, by Mohamed M. Atalla and Dawon Kahng at Bell Labs in 1959,[11] enabled the practical use of metal–oxide–semiconductor (MOS) transistors as memory cell storage elements, a function previously served by magnetic cores.[12] The first modern memory cells were introduced in 1964, when John Schmidt designed the first 64-bit p-channel MOS (PMOS) static random-access memory (SRAM).[13][14]
SRAM typically has six-transistor cells, whereas DRAM (dynamic random-access memory) typically has single-transistor cells.[15][13] In 1965, Toshiba's Toscal BC-1411 electronic calculator used a form of capacitive bipolar DRAM, storing 180-bit data on discrete memory cells, consisting of germanium bipolar transistors and capacitors.[16][17] MOS technology is the basis for modern DRAM. In 1966, Dr. Robert H. Dennard at the IBM Thomas J. Watson Research Center was working on MOS memory. While examining the characteristics of MOS technology, he found it was capable of building capacitors, and that storing a charge or no charge on the MOS capacitor could represent the 1 and 0 of a bit, while the MOS transistor could control writing the charge to the capacitor. This led to his development of a single-transistor DRAM memory cell.[18] In 1967, Dennard filed a patent for a single-transistor DRAM memory cell, based on MOS technology.[19]
The first commercial bipolar 64-bit SRAM was released by Intel in 1969 with the 3101 Schottky TTL. One year later, it released the first DRAM integrated circuit chip, the Intel 1103, based on MOS technology. By 1972, it beat previous records in semiconductor memory sales.[20] DRAM chips during the early 1970s had three-transistor cells, before single-transistor cells became standard since the mid-1970s.[15][13]
CMOS memory was commercialized by RCA, which launched a 288-bit CMOS SRAM memory chip in 1968.[21] CMOS memory was initially slower than NMOS memory, which was more widely used by computers in the 1970s.[22] In 1978, Hitachi introduced the twin-well CMOS process, with its HM6147 (4 kb SRAM) memory chip, manufactured with a 3 µm process. The HM6147 chip was able to match the performance of the fastest NMOS memory chip at the time, while the HM6147 also consumed significantly less power. With comparable performance and much less power consumption, the twin-well CMOS process eventually overtook NMOS as the most common semiconductor manufacturing process for computer memory in the 1980s.[22]
The two most common types of DRAM memory cells since the 1980s have been trench-capacitor cells and stacked-capacitor cells.[23] Trench-capacitor cells are where holes (trenches) are made in a silicon substrate, whose side walls are used as a memory cell, whereas stacked-capacitor cells are the earliest form of three-dimensional memory (3D memory), where memory cells are stacked vertically in a three-dimensional cell structure.[24] Both debuted in 1984, when Hitachi introduced trench-capacitor memory and Fujitsu introduced stacked-capacitor memory.[23]
Floating-gate MOS memory cells
The floating-gate MOSFET (FGMOS) was invented by Dawon Kahng and Simon Sze at Bell Labs in 1967.[25] They proposed the concept of floating-gate memory cells, using FGMOS transistors, which could be used to produce reprogrammable ROM (read-only memory).[26] Floating-gate memory cells later became the basis for non-volatile memory (NVM) technologies including EPROM (erasable programmable ROM), EEPROM (electrically erasable programmable ROM) and flash memory.[27]
Flash memory was invented by Fujio Masuoka at Toshiba in 1980.[28][29] Masuoka and his colleagues presented the invention of NOR flash in 1984,[30] and then NAND flash in 1987.[31] Multi-level cell (MLC) flash memory was introduced by NEC, which demonstrated quad-level cells in a 64 Mb flash chip storing 2-bit per cell in 1996.[23] 3D V-NAND, where flash memory cells are stacked vertically using 3D charge trap flash (CTP) technology, was first announced by Toshiba in 2007,[32] and first commercially manufactured by Samsung Electronics in 2013.[33][34]
Implementation
The following schematics detail the three most used implementations for memory cells:
- The dynamic random access memory cell (DRAM);
- The static random access memory cell (SRAM);
- Flip-flops like the J/K shown below, using only logic gates.
DRAM cell (1 transistor and one capacitor). |
SRAM cell (6 transistors). |
Clocked J/K flip-flop. |
Operation
DRAM memory cell
Storage
- The storage element of the DRAM memory cell is the capacitor labeled (4) in the diagram above. The charge stored in the capacitor degrades over time, so its value must be refreshed (read and rewritten) periodically. The nMOS transistor (3) acts as a gate to allow reading or writing when open or storing when closed.[35]
Reading
- For reading the Word line (2) drives a logic 1 (voltage high) into the gate of the nMOS transistor (3) which makes it conductive and the charge stored at the capacitor (4) is then transferred to the bit line (1). The bit line will have a parasitic capacitance (5) that will drain part of the charge and slow the reading process. The capacitance of the bit line will determine the needed size of the storage capacitor (4). It is a trade-off. If the storage capacitor is too small, the voltage of the bit line would take too much time to raise or not even rise above the threshold needed by the amplifiers at the end of the bit line. Since the reading process degrades the charge in the storage capacitor (4) its value is rewritten after each read.[36]
Writing
- The writing process is the easiest, the desired value logic 1 (high voltage) or logic 0 (low voltage) is driven into the bit line. The word line activates the nMOS transistor (3) connecting it to the storage capacitor (4). The only issue is to keep it open enough time to ensure that the capacitor is fully charged or discharged before turning off the nMOS transistor (3).[36]
SRAM memory cell
(A) S = 1, R = 0: set
(B) S = 0, R = 0: hold
(C) S = 0, R = 1: reset
(D) S = 1, R = 1: not allowed
Transitioning from the restricted combination (D) to (A) leads to an unstable state.
Storage
- The working principle of SRAM memory cell can be easier to understand if the transistors M1 through M4 are drawn as logic gates. That way it is clear that at its heart, the cell storage is built by using two cross-coupled inverters. This simple loop creates a bi-stable circuit. A logic 1 at the input of the first inverter turns into a 0 at its output, and it is fed into the second inverter which transforms that logic 0 back to a logic 1 feeding back the same value to the input of the first inverter. That creates a stable state that does not change over time. Similarly the other stable state of the circuit is to have a logic 0 at the input of the first inverter. After been inverted twice it will also feedback the same value.[37]
- Therefore there are only two stable states that the circuit can be in:
- = 0 and = 1
- = 1 and = 0
Reading
- To read the contents of the memory cell stored in the loop, the transistors M5 and M6 must be turned on. when they receive voltage to their gates from the word line (), they become conductive and so the and values get transmitted to the bit line () and to its complement ().[37] Finally this values get amplified at the end of the bit lines.[37]
Writing
- The
writing process is similar, the difference is that now the new value
that will be stored in the memory cell is driven into the bit line () and the inverted one into its complement (). Next transistors M5 and M6 are open by driving a logic 1 (voltage high) into the word line (). This effectively connects the bit lines to the by-stable inverter loop. There are two possible cases:
- If the value of the loop is the same as the new value driven, there is no change;
- if the value of the loop is different from the new value driven there are two conflicting values, in order for the voltage in the bit lines to overwrite the output of the inverters, the size of the M5 and M6 transistors must be larger than that of the M1-M4 transistors. This allows more current to flow through first ones and therefore tips the voltage in the direction of the new value, at some point the loop will then amplify this intermediate value to full rail.[37]
Flip-flop
The flip-flop has many different implementations, its storage element is usually a latch consisting of a NAND gate loop or a NOR gate loop with additional gates used to implement clocking. Its value is always available for reading as an output. The value remains stored until it is changed through the set or reset process. Flip-flops are typically implemented using MOSFETs.
Floating gate
Floating-gate memory cells, based on floating-gate MOSFETs, are used for most non-volatile memory (NVM) technologies, including EPROM, EEPROM and flash memory.[27] According to R. Bez and A. Pirovano:
A floating-gate memory cell is basically an MOS transistor with a gate completely surrounded by dielectrics (Fig. 1.2), the floating-gate (FG), and electrically governed by a capacitive-coupled control-gate (CG). Being electrically isolated, the FG acts as the storing electrode for the cell device. Charge injected into the FG is maintained there, allowing modulation of the ‘apparent’ threshold voltage (i.e. VT seen from the CG) of the cell transistor.[27]
See also
References
- Li, Hai; Chen, Yiran (19 April 2016). Nonvolatile memory design: Magnetic, resistive, and phase change. CRC press. pp. 6, 7. ISBN 9781439807460.
https://en.wikipedia.org/wiki/Memory_cell_(computing)
| Computer memory and data storage types |
|---|
|
|
| Volatile |
|---|
|
|
|
|
| Non-volatile |
|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
In computing, memory is a device or system that is used to store information for immediate use in a computer or related computer hardware and digital electronic devices.[2] The term memory is often synonymous with the term primary storage or main memory. An archaic synonym for memory is store.[3]
Computer memory operates at a high speed compared to storage that is slower but less expensive and higher in capacity. Besides storing opened programs, computer memory serves as disk cache and write buffer to improve both reading and writing performance. Operating systems borrow RAM capacity for caching so long as not needed by running software.[4] If needed, contents of the computer memory can be transferred to storage; a common way of doing this is through a memory management technique called virtual memory.
Modern memory is implemented as semiconductor memory,[5][6] where data is stored within memory cells built from MOS transistors and other components on an integrated circuit.[7] There are two main kinds of semiconductor memory, volatile and non-volatile. Examples of non-volatile memory are flash memory and ROM, PROM, EPROM and EEPROM memory. Examples of volatile memory are dynamic random-access memory (DRAM) used for primary storage, and static random-access memory (SRAM) used for CPU cache.
Most semiconductor memory is organized into memory cells each storing one bit (0 or 1). Flash memory organization includes both one bit per memory cell and multi-level cell capable of storing multiple bits per cell. The memory cells are grouped into words of fixed word length, for example, 1, 2, 4, 8, 16, 32, 64 or 128 bits. Each word can be accessed by a binary address of N bits, making it possible to store 2N words in the memory.
History
In the early 1940s, memory technology often permitted a capacity of a few bytes. The first electronic programmable digital computer, the ENIAC, using thousands of vacuum tubes, could perform simple calculations involving 20 numbers of ten decimal digits stored in the vacuum tubes.
The next significant advance in computer memory came with acoustic delay-line memory, developed by J. Presper Eckert in the early 1940s. Through the construction of a glass tube filled with mercury and plugged at each end with a quartz crystal, delay lines could store bits of information in the form of sound waves propagating through the mercury, with the quartz crystals acting as transducers to read and write bits. Delay-line memory was limited to a capacity of up to a few thousand bits.
Two alternatives to the delay line, the Williams tube and Selectron tube, originated in 1946, both using electron beams in glass tubes as means of storage. Using cathode ray tubes, Fred Williams invented the Williams tube, which was the first random-access computer memory. The Williams tube was able to store more information than the Selectron tube (the Selectron was limited to 256 bits, while the Williams tube could store thousands) and less expensive. The Williams tube was nevertheless frustratingly sensitive to environmental disturbances.
Efforts began in the late 1940s to find non-volatile memory. Magnetic-core memory allowed for recall of memory after power loss. It was developed by Frederick W. Viehe and An Wang in the late 1940s, and improved by Jay Forrester and Jan A. Rajchman in the early 1950s, before being commercialised with the Whirlwind computer in 1953.[8] Magnetic-core memory was the dominant form of memory until the development of MOS semiconductor memory in the 1960s.[9]
The first semiconductor memory was implemented as a flip-flop circuit in the early 1960s using bipolar transistors.[9] Semiconductor memory made from discrete devices was first shipped by Texas Instruments to the United States Air Force in 1961. The same year, the concept of solid-state memory on an integrated circuit (IC) chip was proposed by applications engineer Bob Norman at Fairchild Semiconductor.[10] The first bipolar semiconductor memory IC chip was the SP95 introduced by IBM in 1965.[9] While semiconductor memory offered improved performance over magnetic-core memory, it remain larger and more expensive and did not displace magnetic-core memory until the late 1960s.[9][11]
MOS memory
The invention of the metal–oxide–semiconductor field-effect transistor (MOSFET) enabled the practical use of metal–oxide–semiconductor (MOS) transistors as memory cell storage elements. MOS memory was developed by John Schmidt at Fairchild Semiconductor in 1964.[12] In addition to higher performance, MOS semiconductor memory was cheaper and consumed less power than magnetic core memory.[13] In 1965, J. Wood and R. Ball of the Royal Radar Establishment proposed digital storage systems that use CMOS (complementary MOS) memory cells, in addition to MOSFET power devices for the power supply, switched cross-coupling, switches and delay-line storage.[14] The development of silicon-gate MOS integrated circuit (MOS IC) technology by Federico Faggin at Fairchild in 1968 enabled the production of MOS memory chips.[15] NMOS memory was commercialized by IBM in the early 1970s.[16] MOS memory overtook magnetic core memory as the dominant memory technology in the early 1970s.[13]
The two main types of volatile random-access memory (RAM) are static random-access memory (SRAM) and dynamic random-access memory (DRAM). Bipolar SRAM was invented by Robert Norman at Fairchild Semiconductor in 1963,[9] followed by the development of MOS SRAM by John Schmidt at Fairchild in 1964.[13] SRAM became an alternative to magnetic-core memory, but requires six transistors for each bit of data.[17] Commercial use of SRAM began in 1965, when IBM introduced their SP95 SRAM chip for the System/360 Model 95.[9]
Toshiba introduced bipolar DRAM memory cells for its Toscal BC-1411 electronic calculator in 1965.[18][19] While it offered improved performance, bipolar DRAM could not compete with the lower price of the then dominant magnetic-core memory.[20] MOS technology is the basis for modern DRAM. In 1966, Robert H. Dennard at the IBM Thomas J. Watson Research Center was working on MOS memory. While examining the characteristics of MOS technology, he found it was possible to build capacitors, and that storing a charge or no charge on the MOS capacitor could represent the 1 and 0 of a bit, while the MOS transistor could control writing the charge to the capacitor. This led to his development of a single-transistor DRAM memory cell.[17] In 1967, Dennard filed a patent for a single-transistor DRAM memory cell based on MOS technology.[21] This led to the first commercial DRAM IC chip, the Intel 1103 in October 1970.[22][23][24] Synchronous dynamic random-access memory (SDRAM) later debuted with the Samsung KM48SL2000 chip in 1992.[25][26]
The term memory is also often used to refer to non-volatile memory including read-only memory (ROM) through modern flash memory. Programmable read-only memory (PROM) was invented by Wen Tsing Chow in 1956, while working for the Arma Division of the American Bosch Arma Corporation.[27][28] In 1967, Dawon Kahng and Simon Sze of Bell Labs proposed that the floating gate of a MOS semiconductor device could be used for the cell of a reprogrammable ROM, which led to Dov Frohman of Intel inventing EPROM (erasable PROM) in 1971.[29] EEPROM (electrically erasable PROM) was developed by Yasuo Tarui, Yutaka Hayashi and Kiyoko Naga at the Electrotechnical Laboratory in 1972.[30] Flash memory was invented by Fujio Masuoka at Toshiba in the early 1980s.[31][32] Masuoka and colleagues presented the invention of NOR flash in 1984,[33] and then NAND flash in 1987.[34] Toshiba commercialized NAND flash memory in 1987.[35][36][37]
Developments in technology and economies of scale have made possible so-called very large memory (VLM) computers.[37]
Volatile memory
Volatile memory is computer memory that requires power to maintain the stored information. Most modern semiconductor volatile memory is either static RAM (SRAM) or dynamic RAM (DRAM).[a] DRAM dominates for desktop system memory. SRAM is used for CPU cache. SRAM is also found in small embedded systems requiring little memory.
SRAM retains its contents as long as the power is connected and may use a simpler interface, but requires six transistors per bit. Dynamic RAM is more complicated for interfacing and control, needing regular refresh cycles to prevent losing its contents, but uses only one transistor and one capacitor per bit, allowing it to reach much higher densities and much cheaper per-bit costs.[2][23][37]
Non-volatile memory
Non-volatile memory can retain the stored information even when not powered. Examples of non-volatile memory include read-only memory, flash memory, most types of magnetic computer storage devices (e.g. hard disk drives, floppy disks and magnetic tape), optical discs, and early computer storage methods such as paper tape and punched cards.[37]
Non-volatile memory technologies under development include ferroelectric RAM, programmable metallization cell, Spin-transfer torque magnetic RAM, SONOS, resistive random-access memory, racetrack memory, Nano-RAM, 3D XPoint, and millipede memory.
Semi-volatile memory
A third category of memory is semi-volatile. The term is used to describe a memory that has some limited non-volatile duration after power is removed, but then data is ultimately lost. A typical goal when using a semi-volatile memory is to provide the high performance and durability associated with volatile memories while providing some benefits of non-volatile memory.
For example, some non-volatile memory types experience wear when written. A worn cell has increased volatility but otherwise continues to work. Data locations which are written frequently can thus be directed to use worn circuits. As long as the location is updated within some known retention time, the data stays valid. After a period of time without update, the value is copied to a less-worn circuit with longer retention. Writing first to the worn area allows a high write rate while avoiding wear on the not-worn circuits.[38]
As a second example, an STT-RAM can be made non-volatile by building large cells, but doing so raises the cost per bit and power requirements and reduces the write speed. Using small cells improves cost, power, and speed, but leads to semi-volatile behavior. In some applications, the increased volatility can be managed to provide many benefits of a non-volatile memory, for example by removing power but forcing a wake-up before data is lost; or by caching read-only data and discarding the cached data if the power-off time exceeds the non-volatile threshold.[39]
The term semi-volatile is also used to describe semi-volatile behavior constructed from other memory types. For example, a volatile and a non-volatile memory may be combined, where an external signal copies data from the volatile memory to the non-volatile memory, but if power is removed before the copy occurs, the data is lost. Or, a battery-backed volatile memory, and if external power is lost there is some known period where the battery can continue to power the volatile memory, but if power is off for an extended time, the battery runs down and data is lost.[37]
Management
Proper management of memory is vital for a computer system to operate properly. Modern operating systems have complex systems to properly manage memory. Failure to do so can lead to bugs, slow performance, or takeover by viruses and malicious software.
Bugs
Improper management of memory is a common cause of bugs, including the following types:
- A memory leak occurs when a program requests memory from the operating system and never returns the memory when it's done with it. A program with this bug will gradually require more and more memory until the program fails as the operating system runs out.
- A segmentation fault results when a program tries to access memory that it does not have permission to access. Generally, a program doing so will be terminated by the operating system.
- A buffer overflow occurs when a program writes data to the end of its allocated space and then continues to write data beyond this to memory that has been allocated for other purposes. This may result in erratic program behavior, including memory access errors, incorrect results, a crash, or a breach of system security. They are thus the basis of many software vulnerabilities and can be maliciously exploited.
Early computer systems
In early computer systems, programs typically specified the location to write memory and what data to put there. This location was a physical location on the actual memory hardware. Early computers did not have the complex memory management systems used today.
This approach has its pitfalls. If the location specified is incorrect, this will cause the computer to write the data to some other part of the program. The results of an error like this are unpredictable. In some cases, the error might overwrite memory used by the operating system. Hackers can take advantage of this lack of protection to create viruses and malware.
Virtual memory
Virtual memory is a system where physical memory is managed by the operating system typically with assistance from a memory management unit. It allows multiple types of memory to be used. For example, some data can be stored in RAM while other data is stored on a hard drive (e.g. in a swapfile), functioning as an extension of the cache hierarchy. This offers several advantages. Computer programmers no longer need to worry about where their data is physically stored or whether the user's computer will have enough memory. The operating system will place actively used data in RAM, which is much faster than hard disks. When the amount of RAM is not sufficient to run all the current programs, it can result in a situation where the computer spends more time moving data from RAM to disk and back than it does accomplishing tasks; this is known as thrashing.
Protected memory
Protected memory is a system where each program is given an area of memory to use and is prevented from going outside that range. If the operating system detects that a program has tried to alter memory that does not belong to it, the program is terminated (or otherwise restricted or redirected). This way, only the offending program crashes, and other programs are not affected by the misbehavior (whether accidental or intentional). Use of protected memory greatly enhances both the reliability and security of a computer system.
Without protected memory, it is possible that a bug in one program will alter the memory used by another program. This will cause that other program to run off of corrupted memory with unpredictable results. If the operating system's memory is corrupted, the entire computer system may crash and need to be rebooted. At times programs intentionally alter the memory used by other programs. This is done by viruses and malware to take over computers. It may also be used benignly by desirable programs which are intended to modify other programs, debuggers, for example, to insert breakpoints or hooks.
See also
- Memory geometry
- Memory hierarchy
- Memory organization
- Processor registers store data but normally are not considered as memory, since they only store one word and do not include an addressing mechanism.
Notes
References
The i1103 was manufactured on a 6-mask silicon-gate P-MOS process with 8 μm minimum features. The resulting product had a 2,400 µm, 2 memory cell size, a die size just under 10 mm², and sold for around $21.
The first commercial synchronous DRAM, the Samsung 16-Mbit KM48SL2000, employs a single-bank architecture that lets system designers easily transition from asynchronous to synchronous systems.
[...] Windows Server Enterprise supports clustering with up to eight-node clusters and very large memory (VLM) configurations of up to 32 GB on 32-bit systems and 2 TB on 64-bit systems.
- Keppel, Naeimi, Nasrullah. "Method and apparatus for managing a spin-transfer torque memory". Google Patents. Retrieved 20 May 2018.
Further reading
- Miller, Stephen W. (1977), Memory and Storage Technology, Montvale.: AFIPS Press
- Memory and Storage Technology, Alexandria, Virginia.: Time Life Books, 1988
https://en.wikipedia.org/wiki/Computer_memory
Flash memory is an electronic non-volatile computer memory storage medium that can be electrically erased and reprogrammed. The two main types of flash memory, NOR flash and NAND flash, are named for the NOR and NAND logic gates. Both use the same cell design, consisting of floating gate MOSFETs. They differ at the circuit level depending on whether the state of the bit line or word lines is pulled high or low: in NAND flash, the relationship between the bit line and the word lines resembles a NAND gate; in NOR flash, it resembles a NOR gate.
Flash memory, a type of floating-gate memory, was invented at Toshiba in 1980 and is based on EEPROM technology. Toshiba began marketing flash memory in 1987.[1] EPROMs had to be erased completely before they could be rewritten. NAND flash memory, however, may be erased, written, and read in blocks (or pages), which generally are much smaller than the entire device. NOR flash memory allows a single machine word to be written – to an erased location – or read independently. A flash memory device typically consists of one or more flash memory chips (each holding many flash memory cells), along with a separate flash memory controller chip.
The NAND type is found mainly in memory cards, USB flash drives, solid-state drives (those produced since 2009), feature phones, smartphones, and similar products, for general storage and transfer of data. NAND or NOR flash memory is also often used to store configuration data in digital products, a task previously made possible by EEPROM or battery-powered static RAM. A key disadvantage of flash memory is that it can endure only a relatively small number of write cycles in a specific block.[2]
Flash memory[3] is used in computers, PDAs, digital audio players, digital cameras, mobile phones, synthesizers, video games, scientific instrumentation, industrial robotics, and medical electronics. Flash memory has fast read access time, but it is not as fast as static RAM or ROM. In portable devices, it is preferred to use flash memory because of its mechanical shock resistance since mechanical drives are more prone to mechanical damage.[4]
Because erase cycles are slow, the large block sizes used in flash memory erasing give it a significant speed advantage over non-flash EEPROM when writing large amounts of data. As of 2019, flash memory costs much less[by how much?] than byte-programmable EEPROM and had become the dominant memory type wherever a system required a significant amount of non-volatile solid-state storage. EEPROMs, however, are still used in applications that require only small amounts of storage, as in serial presence detect.[5][6]
Flash memory packages can use die stacking with through-silicon vias and several dozen layers of 3D TLC NAND cells (per die) simultaneously to achieve capacities of up to 1 tebibyte per package using 16 stacked dies and an integrated flash controller as a separate die inside the package.[7][8][9][10]
History
Background
The origins of flash memory can be traced back to the development of the floating-gate MOSFET (FGMOS), also known as the floating-gate transistor.[11][12] The original MOSFET (metal–oxide–semiconductor field-effect transistor), also known as the MOS transistor, was invented by Egyptian engineer Mohamed M. Atalla and Korean engineer Dawon Kahng at Bell Labs in 1959.[13] Kahng went on to develop a variation, the floating-gate MOSFET, with Taiwanese-America engineer Simon Min Sze at Bell Labs in 1967.[14] They proposed that it could be used as floating-gate memory cells for storing a form of programmable read-only memory (PROM) that is both non-volatile and re-programmable.[14]
Early types of floating-gate memory included EPROM (erasable PROM) and EEPROM (electrically erasable PROM) in the 1970s.[14] However, early floating-gate memory required engineers to build a memory cell for each bit of data, which proved to be cumbersome,[15] slow,[16] and expensive, restricting floating-gate memory to niche applications in the 1970s, such as military equipment and the earliest experimental mobile phones.[11]
Invention and commercialization
Fujio Masuoka, while working for Toshiba, proposed a new type of floating-gate memory that allowed entire sections of memory to be erased quickly and easily, by applying a voltage to a single wire connected to a group of cells.[11] This led to Masuoka's invention of flash memory at Toshiba in 1980.[15][17][18] According to Toshiba, the name "flash" was suggested by Masuoka's colleague, Shōji Ariizumi, because the erasure process of the memory contents reminded him of the flash of a camera.[19] Masuoka and colleagues presented the invention of NOR flash in 1984,[20][21] and then NAND flash at the IEEE 1987 International Electron Devices Meeting (IEDM) held in San Francisco.[22]
Toshiba commercially launched NAND flash memory in 1987.[1][14] Intel Corporation introduced the first commercial NOR type flash chip in 1988.[23] NOR-based flash has long erase and write times, but provides full address and data buses, allowing random access to any memory location. This makes it a suitable replacement for older read-only memory (ROM) chips, which are used to store program code that rarely needs to be updated, such as a computer's BIOS or the firmware of set-top boxes. Its endurance may be from as little as 100 erase cycles for an on-chip flash memory,[24] to a more typical 10,000 or 100,000 erase cycles, up to 1,000,000 erase cycles.[25] NOR-based flash was the basis of early flash-based removable media; CompactFlash was originally based on it, though later cards moved to less expensive NAND flash.
NAND flash has reduced erase and write times, and requires less chip area per cell, thus allowing greater storage density and lower cost per bit than NOR flash. However, the I/O interface of NAND flash does not provide a random-access external address bus. Rather, data must be read on a block-wise basis, with typical block sizes of hundreds to thousands of bits. This makes NAND flash unsuitable as a drop-in replacement for program ROM, since most microprocessors and microcontrollers require byte-level random access. In this regard, NAND flash is similar to other secondary data storage devices, such as hard disks and optical media, and is thus highly suitable for use in mass-storage devices, such as memory cards and solid-state drives (SSD). Flash memory cards and SSDs store data using multiple NAND flash memory chips.
The first NAND-based removable memory card format was SmartMedia, released in 1995. Many others followed, including MultiMediaCard, Secure Digital, Memory Stick, and xD-Picture Card.
Later developments
A new generation of memory card formats, including RS-MMC, miniSD and microSD, feature extremely small form factors. For example, the microSD card has an area of just over 1.5 cm2, with a thickness of less than 1 mm.
NAND flash has achieved significant levels of memory density as a result of several major technologies that were commercialized during the late 2000s to early 2010s.[26]
Multi-level cell (MLC) technology stores more than one bit in each memory cell. NEC demonstrated multi-level cell (MLC) technology in 1998, with an 80 Mb flash memory chip storing 2 bits per cell.[27] STMicroelectronics also demonstrated MLC in 2000, with a 64 MB NOR flash memory chip.[28] In 2009, Toshiba and SanDisk introduced NAND flash chips with QLC technology storing 4 bits per cell and holding a capacity of 64 Gbit.[29][30] Samsung Electronics introduced triple-level cell (TLC) technology storing 3-bits per cell, and began mass-producing NAND chips with TLC technology in 2010.[31]
Charge trap flash
Charge trap flash (CTF) technology replaces the polysilicon floating gate, which is sandwiched between a blocking gate oxide above and a tunneling oxide below it, with an electrically insulating silicon nitride layer; the silicon nitride layer traps electrons. In theory, CTF is less prone to electron leakage, providing improved data retention.[32][33][34][35][36][37]
Because CTF replaces the polysilicon with an electrically insulating nitride, it allows for smaller cells and higher endurance (lower degradation or wear). However, electrons can become trapped and accumulate in the nitride, leading to degradation. Leakage is exacerbated at high temperatures since electrons become more excitated with increasing temperatures. CTF technology however still uses a tunneling oxide and blocking layer which are the weak points of the technology, since they can still be damaged in the usual ways (the tunnel oxide can be degraded due to extremely high electric fields and the blocking layer due to Anode Hot Hole Injection (AHHI).[38][39]
Degradation or wear of the oxides is the reason why flash memory has limited endurance, and data retention goes down (the potential for data loss increases) with increasing degradation, since the oxides lose their electrically insulating characteristics as they degrade. The oxides must insulate against electrons to prevent them from leaking which would cause data loss.
In 1991, NEC researchers including N. Kodama, K. Oyama and Hiroki Shirai described a type of flash memory with a charge trap method.[40] In 1998, Boaz Eitan of Saifun Semiconductors (later acquired by Spansion) patented a flash memory technology named NROM that took advantage of a charge trapping layer to replace the conventional floating gate used in conventional flash memory designs.[41] In 2000, an Advanced Micro Devices (AMD) research team led by Richard M. Fastow, Egyptian engineer Khaled Z. Ahmed and Jordanian engineer Sameer Haddad (who later joined Spansion) demonstrated a charge-trapping mechanism for NOR flash memory cells.[42] CTF was later commercialized by AMD and Fujitsu in 2002.[43] 3D V-NAND (vertical NAND) technology stacks NAND flash memory cells vertically within a chip using 3D charge trap flash (CTP) technology. 3D V-NAND technology was first announced by Toshiba in 2007,[44] and the first device, with 24 layers, was first commercialized by Samsung Electronics in 2013.[45][46]
3D integrated circuit technology
3D integrated circuit (3D IC) technology stacks integrated circuit (IC) chips vertically into a single 3D IC chip package.[26] Toshiba introduced 3D IC technology to NAND flash memory in April 2007, when they debuted a 16 GB eMMC compliant (product number THGAM0G7D8DBAI6, often abbreviated THGAM on consumer websites) embedded NAND flash memory chip, which was manufactured with eight stacked 2 GB NAND flash chips.[47] In September 2007, Hynix Semiconductor (now SK Hynix) introduced 24-layer 3D IC technology, with a 16 GB flash memory chip that was manufactured with 24 stacked NAND flash chips using a wafer bonding process.[48] Toshiba also used an eight-layer 3D IC for their 32 GB THGBM flash chip in 2008.[49] In 2010, Toshiba used a 16-layer 3D IC for their 128 GB THGBM2 flash chip, which was manufactured with 16 stacked 8 GB chips.[50] In the 2010s, 3D ICs came into widespread commercial use for NAND flash memory in mobile devices.[26]
As of August 2017, microSD cards with a capacity up to 400 GB (400 billion bytes) are available.[51][52] The same year, Samsung combined 3D IC chip stacking with its 3D V-NAND and TLC technologies to manufacture its 512 GB KLUFG8R1EM flash memory chip with eight stacked 64-layer V-NAND chips.[53] In 2019, Samsung produced a 1024 GB flash chip, with eight stacked 96-layer V-NAND chips and with QLC technology.[54][55]
Principles of operation
Flash memory stores information in an array of memory cells made from floating-gate transistors. In single-level cell (SLC) devices, each cell stores only one bit of information. Multi-level cell (MLC) devices, including triple-level cell (TLC) devices, can store more than one bit per cell.
The floating gate may be conductive (typically polysilicon in most kinds of flash memory) or non-conductive (as in SONOS flash memory).[56]
Floating-gate MOSFET
In flash memory, each memory cell resembles a standard metal–oxide–semiconductor field-effect transistor (MOSFET) except that the transistor has two gates instead of one. The cells can be seen as an electrical switch in which current flows between two terminals (source and drain) and is controlled by a floating gate (FG) and a control gate (CG). The CG is similar to the gate in other MOS transistors, but below this, there is the FG insulated all around by an oxide layer. The FG is interposed between the CG and the MOSFET channel. Because the FG is electrically isolated by its insulating layer, electrons placed on it are trapped. When the FG is charged with electrons, this charge screens the electric field from the CG, thus, increasing the threshold voltage (VT) of the cell. This means that the VT of the cell can be changed between the uncharged FG threshold voltage (VT1) and the higher charged FG threshold voltage (VT2) by changing the FG charge. In order to read a value from the cell, an intermediate voltage (VI) between VT1 and VT2 is applied to the CG. If the channel conducts at VI, the FG must be uncharged (if it were charged, there would not be conduction because VI is less than VT2). If the channel does not conduct at the VI, it indicates that the FG is charged. The binary value of the cell is sensed by determining whether there is current flowing through the transistor when VI is asserted on the CG. In a multi-level cell device, which stores more than one bit per cell, the amount of current flow is sensed (rather than simply its presence or absence), in order to determine more precisely the level of charge on the FG.
Floating gate MOSFETs are so named because there is an electrically insulating tunnel oxide layer between the floating gate and the silicon, so the gate "floats" above the silicon. The oxide keeps the electrons confined to the floating gate. Degradation or wear (and the limited endurance of floating gate Flash memory) occurs due to the extremely high electric field (10 million volts per centimeter) experienced by the oxide. Such high voltage densities can break atomic bonds over time in the relatively thin oxide, gradually degrading its electrically insulating properties and allowing electrons to be trapped in and pass through freely (leak) from the floating gate into the oxide, increasing the likelihood of data loss since the electrons (the quantity of which is used to represent different charge levels, each assigned to a different combination of bits in MLC Flash) are normally in the floating gate. This is why data retention goes down and the risk of data loss increases with increasing degradation.[57][58][36][59][60]The silicon oxide in a cell degrades with every erase operation. The degradation increases the amount of negative charge in the cell over time due to trapped electrons in the oxide and negates some of the control gate voltage, this over time also makes erasing the cell slower, so to maintain the performance and reliability of the NAND chip, the cell must be retired from use. Endurance also decreases with the number of bits in a cell. With more bits in a cell, the number of possible states (each represented by a different voltage level) in a cell increases and is more sensitive to the voltages used for programming. Voltages may be adjusted to compensate for degradation of the silicon oxide, and as the number of bits increases, the number of possible states also increases and thus the cell is less tolerant of adjustments to programming voltages, because there is less space between the voltage levels that define each state in a cell.[61]
Fowler–Nordheim tunneling
The process of moving electrons from the control gate and into the floating gate is called Fowler–Nordheim tunneling, and it fundamentally changes the characteristics of the cell by increasing the MOSFET's threshold voltage. This, in turn, changes the drain-source current that flows through the transistor for a given gate voltage, which is ultimately used to encode a binary value. The Fowler-Nordheim tunneling effect is reversible, so electrons can be added to or removed from the floating gate, processes traditionally known as writing and erasing.[62]
Internal charge pumps
Despite the need for relatively high programming and erasing voltages, virtually all flash chips today require only a single supply voltage and produce the high voltages that are required using on-chip charge pumps.
Over half the energy used by a 1.8 V NAND flash chip is lost in the charge pump itself. Since boost converters are inherently more efficient than charge pumps, researchers developing low-power SSDs have proposed returning to the dual Vcc/Vpp supply voltages used on all early flash chips, driving the high Vpp voltage for all flash chips in an SSD with a single shared external boost converter.[63][64][65][66][67][68][69][70]
In spacecraft and other high-radiation environments, the on-chip charge pump is the first part of the flash chip to fail, although flash memories will continue to work – in read-only mode – at much higher radiation levels.[71]
NOR flash
In NOR flash, each cell has one end connected directly to ground, and the other end connected directly to a bit line. This arrangement is called "NOR flash" because it acts like a NOR gate: when one of the word lines (connected to the cell's CG) is brought high, the corresponding storage transistor acts to pull the output bit line low. NOR flash continues to be the technology of choice for embedded applications requiring a discrete non-volatile memory device.[citation needed] The low read latencies characteristic of NOR devices allow for both direct code execution and data storage in a single memory product.[72]
Programming
A single-level NOR flash cell in its default state is logically equivalent to a binary "1" value, because current will flow through the channel under application of an appropriate voltage to the control gate, so that the bitline voltage is pulled down. A NOR flash cell can be programmed, or set to a binary "0" value, by the following procedure:
- an elevated on-voltage (typically >5 V) is applied to the CG
- the channel is now turned on, so electrons can flow from the source to the drain (assuming an NMOS transistor)
- the source-drain current is sufficiently high to cause some high energy electrons to jump through the insulating layer onto the FG, via a process called hot-electron injection.
Erasing
To erase a NOR flash cell (resetting it to the "1" state), a large voltage of the opposite polarity is applied between the CG and source terminal, pulling the electrons off the FG through quantum tunneling. Modern NOR flash memory chips are divided into erase segments (often called blocks or sectors). The erase operation can be performed only on a block-wise basis; all the cells in an erase segment must be erased together. Programming of NOR cells, however, generally can be performed one byte or word at a time.
NAND flash
NAND flash also uses floating-gate transistors, but they are connected in a way that resembles a NAND gate: several transistors are connected in series, and the bit line is pulled low only if all the word lines are pulled high (above the transistors' VT). These groups are then connected via some additional transistors to a NOR-style bit line array in the same way that single transistors are linked in NOR flash.
Compared to NOR flash, replacing single transistors with serial-linked groups adds an extra level of addressing. Whereas NOR flash might address memory by page then word, NAND flash might address it by page, word and bit. Bit-level addressing suits bit-serial applications (such as hard disk emulation), which access only one bit at a time. Execute-in-place applications, on the other hand, require every bit in a word to be accessed simultaneously. This requires word-level addressing. In any case, both bit and word addressing modes are possible with either NOR or NAND flash.
To read data, first the desired group is selected (in the same way that a single transistor is selected from a NOR array). Next, most of the word lines are pulled up above VT2, while one of them is pulled up to VI. The series group will conduct (and pull the bit line low) if the selected bit has not been programmed.
Despite the additional transistors, the reduction in ground wires and bit lines allows a denser layout and greater storage capacity per chip. (The ground wires and bit lines are actually much wider than the lines in the diagrams.) In addition, NAND flash is typically permitted to contain a certain number of faults (NOR flash, as is used for a BIOS ROM, is expected to be fault-free). Manufacturers try to maximize the amount of usable storage by shrinking the size of the transistors or cells, however the industry can avoid this and achieve higher storage densities per die by using 3D NAND, which stacks cells on top of each other.
NAND Flash cells are read by analysing their response to various voltages.[59]
Writing and erasing
NAND flash uses tunnel injection for writing and tunnel release for erasing. NAND flash memory forms the core of the removable USB storage devices known as USB flash drives, as well as most memory card formats and solid-state drives available today.
The hierarchical structure of NAND flash starts at a cell level which establishes strings, then pages, blocks, planes and ultimately a die. A string is a series of connected NAND cells in which the source of one cell is connected to the drain of the next one. Depending on the NAND technology, a string typically consists of 32 to 128 NAND cells. Strings are organised into pages which are then organised into blocks in which each string is connected to a separate line called a bitline. All cells with the same position in the string are connected through the control gates by a wordline. A plane contains a certain number of blocks that are connected through the same bitline. A flash die consists of one or more planes, and the peripheral circuitry that is needed to perform all the read, write, and erase operations.
The architecture of NAND flash means that data can be read and programmed (written) in pages, typically between 4 KiB and 16 KiB in size, but can only be erased at the level of entire blocks consisting of multiple pages. When a block is erased, all the cells are logically set to 1. Data can only be programmed in one pass to a page in a block that was erased. Any cells that have been set to 0 by programming can only be reset to 1 by erasing the entire block. This means that before new data can be programmed into a page that already contains data, the current contents of the page plus the new data must be copied to a new, erased page. If a suitable erased page is available, the data can be written to it immediately. If no erased page is available, a block must be erased before copying the data to a page in that block. The old page is then marked as invalid and is available for erasing and reuse.[73]
Vertical NAND
Vertical NAND (V-NAND) or 3D NAND memory stacks memory cells vertically and uses a charge trap flash architecture. The vertical layers allow larger areal bit densities without requiring smaller individual cells.[74] It is also sold under the trademark BiCS Flash, which is a trademark of Kioxia Corporation (former Toshiba Memory Corporation). 3D NAND was first announced by Toshiba in 2007.[44] V-NAND was first commercially manufactured by Samsung Electronics in 2013.[45][46][75][76]
Structure
V-NAND uses a charge trap flash geometry (which was commercially introduced in 2002 by AMD and Fujitsu)[43] that stores charge on an embedded silicon nitride film. Such a film is more robust against point defects and can be made thicker to hold larger numbers of electrons. V-NAND wraps a planar charge trap cell into a cylindrical form.[74] As of 2020, 3D NAND Flash memories by Micron and Intel instead use floating gates, however, Micron 128 layer and above 3D NAND memories use a conventional charge trap structure, due to the dissolution of the partnership between Micron and Intel. Charge trap 3D NAND Flash is thinner than floating gate 3D NAND. In floating gate 3D NAND, the memory cells are completely separated from one another, whereas in charge trap 3D NAND, vertical groups of memory cells share the same silicon nitride material.[77]
An individual memory cell is made up of one planar polysilicon layer containing a hole filled by multiple concentric vertical cylinders. The hole's polysilicon surface acts as the gate electrode. The outermost silicon dioxide cylinder acts as the gate dielectric, enclosing a silicon nitride cylinder that stores charge, in turn enclosing a silicon dioxide cylinder as the tunnel dielectric that surrounds a central rod of conducting polysilicon which acts as the conducting channel.[74]
Memory cells in different vertical layers do not interfere with each other, as the charges cannot move vertically through the silicon nitride storage medium, and the electric fields associated with the gates are closely confined within each layer. The vertical collection is electrically identical to the serial-linked groups in which conventional NAND flash memory is configured.[74]
Construction
Growth of a group of V-NAND cells begins with an alternating stack of conducting (doped) polysilicon layers and insulating silicon dioxide layers.[74]
The next step is to form a cylindrical hole through these layers. In practice, a 128 Gbit V-NAND chip with 24 layers of memory cells requires about 2.9 billion such holes. Next, the hole's inner surface receives multiple coatings, first silicon dioxide, then silicon nitride, then a second layer of silicon dioxide. Finally, the hole is filled with conducting (doped) polysilicon.[74]
Performance
As of 2013, V-NAND flash architecture allows read and write operations twice as fast as conventional NAND and can last up to 10 times as long, while consuming 50 percent less power. They offer comparable physical bit density using 10-nm lithography but may be able to increase bit density by up to two orders of magnitude, given V-NAND's use of up to several hundred layers.[74] As of 2020, V-NAND chips with 160 layers are under development by Samsung.[78]
Cost
The wafer cost of a 3D NAND is comparable with scaled down (32 nm or less) planar NAND Flash.[79] However, with planar NAND scaling stopping at 16 nm, the cost per bit reduction can continue by 3D NAND starting with 16 layers. However, due to the non-vertical sidewall of the hole etched through the layers; even a slight deviation leads to a minimum bit cost, i.e., minimum equivalent design rule (or maximum density), for a given number of layers; this minimum bit cost layer number decreases for smaller hole diameter.[80]
Limitations
Block erasure
One limitation of flash memory is that it can be erased only a block at a time. This generally sets all bits in the block to 1. Starting with a freshly erased block, any location within that block can be programmed. However, once a bit has been set to 0, only by erasing the entire block can it be changed back to 1. In other words, flash memory (specifically NOR flash) offers random-access read and programming operations but does not offer arbitrary random-access rewrite or erase operations. A location can, however, be rewritten as long as the new value's 0 bits are a superset of the over-written values. For example, a nibble value may be erased to 1111, then written as 1110. Successive writes to that nibble can change it to 1010, then 0010, and finally 0000. Essentially, erasure sets all bits to 1, and programming can only clear bits to 0.[81] Some file systems designed for flash devices make use of this rewrite capability, for example Yaffs1, to represent sector metadata. Other flash file systems, such as YAFFS2, never make use of this "rewrite" capability—they do a lot of extra work to meet a "write once rule".
Although data structures in flash memory cannot be updated in completely general ways, this allows members to be "removed" by marking them as invalid. This technique may need to be modified for multi-level cell devices, where one memory cell holds more than one bit.
Common flash devices such as USB flash drives and memory cards provide only a block-level interface, or flash translation layer (FTL), which writes to a different cell each time to wear-level the device. This prevents incremental writing within a block; however, it does help the device from being prematurely worn out by intensive write patterns.
Data Retention
Data stored on flash cells is steadily lost due to electron detrapping[definition needed]. The rate of loss increases exponentially as the absolute temperature increases. For example: For a 45 nm NOR Flash, at 1000 hours, the threshold voltage (Vt) loss at 25 deg Celsius is about half that at 90 deg Celsius.[82]
Memory wear
Another limitation is that flash memory has a finite number of program – erase cycles (typically written as P/E cycles). [83][84] Micron Technology and Sun Microsystems announced an SLC NAND flash memory chip rated for 1,000,000 P/E cycles on 17 December 2008.[85] Longer P/E cycles of Industrial SSDs speak for their endurance level and make them more reliable for Industrial usage.
The guaranteed cycle count may apply only to block zero (as is the case with TSOP NAND devices), or to all blocks (as in NOR). This effect is mitigated in some chip firmware or file system drivers by counting the writes and dynamically remapping blocks in order to spread write operations between sectors; this technique is called wear leveling. Another approach is to perform write verification and remapping to spare sectors in case of write failure, a technique called bad block management (BBM). For portable consumer devices, these wear out management techniques typically extend the life of the flash memory beyond the life of the device itself, and some data loss may be acceptable in these applications. For high-reliability data storage, however, it is not advisable to use flash memory that would have to go through a large number of programming cycles. This limitation is meaningless for 'read-only' applications such as thin clients and routers, which are programmed only once or at most a few times during their lifetimes.
In December 2012, Taiwanese engineers from Macronix revealed their intention to announce at the 2012 IEEE International Electron Devices Meeting that they had figured out how to improve NAND flash storage read/write cycles from 10,000 to 100 million cycles using a "self-healing" process that used a flash chip with "onboard heaters that could anneal small groups of memory cells."[86] The built-in thermal annealing was to replace the usual erase cycle with a local high temperature process that not only erased the stored charge, but also repaired the electron-induced stress in the chip, giving write cycles of at least 100 million.[87] The result was to be a chip that could be erased and rewritten over and over, even when it should theoretically break down. As promising as Macronix's breakthrough might have been for the mobile industry, however, there were no plans for a commercial product featuring this capability to be released any time in the near future.[88]
Read disturb
The method used to read NAND flash memory can cause nearby cells in the same memory block to change over time (become programmed). This is known as read disturb. The threshold number of reads is generally in the hundreds of thousands of reads between intervening erase operations. If reading continually from one cell, that cell will not fail but rather one of the surrounding cells on a subsequent read. To avoid the read disturb problem the flash controller will typically count the total number of reads to a block since the last erase. When the count exceeds a target limit, the affected block is copied over to a new block, erased, then released to the block pool. The original block is as good as new after the erase. If the flash controller does not intervene in time, however, a read disturb error will occur with possible data loss if the errors are too numerous to correct with an error-correcting code.[89][90][91]
X-ray effects
Most flash ICs come in ball grid array (BGA) packages, and even the ones that do not are often mounted on a PCB next to other BGA packages. After PCB Assembly, boards with BGA packages are often X-rayed to see if the balls are making proper connections to the proper pad, or if the BGA needs rework. These X-rays can erase programmed bits in a flash chip (convert programmed "0" bits into erased "1" bits). Erased bits ("1" bits) are not affected by X-rays.[92][93]
Some manufacturers are now making X-ray proof SD[94] and USB[95] memory devices.
Low-level access
The low-level interface to flash memory chips differs from those of other memory types such as DRAM, ROM, and EEPROM, which support bit-alterability (both zero to one and one to zero) and random access via externally accessible address buses.
NOR memory has an external address bus for reading and programming. For NOR memory, reading and programming are random-access, and unlocking and erasing are block-wise. For NAND memory, reading and programming are page-wise, and unlocking and erasing are block-wise.
NOR memories
Reading from NOR flash is similar to reading from random-access memory, provided the address and data bus are mapped correctly. Because of this, most microprocessors can use NOR flash memory as execute in place (XIP) memory, meaning that programs stored in NOR flash can be executed directly from the NOR flash without needing to be copied into RAM first. NOR flash may be programmed in a random-access manner similar to reading. Programming changes bits from a logical one to a zero. Bits that are already zero are left unchanged. Erasure must happen a block at a time, and resets all the bits in the erased block back to one. Typical block sizes are 64, 128, or 256 KiB.
Bad block management is a relatively new feature in NOR chips. In older NOR devices not supporting bad block management, the software or device driver controlling the memory chip must correct for blocks that wear out, or the device will cease to work reliably.
The specific commands used to lock, unlock, program, or erase NOR memories differ for each manufacturer. To avoid needing unique driver software for every device made, special Common Flash Memory Interface (CFI) commands allow the device to identify itself and its critical operating parameters.
Besides its use as random-access ROM, NOR flash can also be used as a storage device, by taking advantage of random-access programming. Some devices offer read-while-write functionality so that code continues to execute even while a program or erase operation is occurring in the background. For sequential data writes, NOR flash chips typically have slow write speeds, compared with NAND flash.
Typical NOR flash does not need an error correcting code.[96]
NAND memories
NAND flash architecture was introduced by Toshiba in 1989.[97] These memories are accessed much like block devices, such as hard disks. Each block consists of a number of pages. The pages are typically 512,[98] 2,048 or 4,096 bytes in size. Associated with each page are a few bytes (typically 1/32 of the data size) that can be used for storage of an error correcting code (ECC) checksum.
Typical block sizes include:
- 32 pages of 512+16 bytes each for a block size (effective) of 16 KiB
- 64 pages of 2,048+64 bytes each for a block size of 128 KiB[99]
- 64 pages of 4,096+128 bytes each for a block size of 256 KiB[100]
- 128 pages of 4,096+128 bytes each for a block size of 512 KiB.
While reading and programming is performed on a page basis, erasure can only be performed on a block basis.[101]
NAND devices also require bad block management by the device driver software or by a separate controller chip. Some SD cards, for example, include controller circuitry to perform bad block management and wear leveling. When a logical block is accessed by high-level software, it is mapped to a physical block by the device driver or controller. A number of blocks on the flash chip may be set aside for storing mapping tables to deal with bad blocks, or the system may simply check each block at power-up to create a bad block map in RAM. The overall memory capacity gradually shrinks as more blocks are marked as bad.
NAND relies on ECC to compensate for bits that may spontaneously fail during normal device operation. A typical ECC will correct a one-bit error in each 2048 bits (256 bytes) using 22 bits of ECC, or a one-bit error in each 4096 bits (512 bytes) using 24 bits of ECC.[102] If the ECC cannot correct the error during read, it may still detect the error. When doing erase or program operations, the device can detect blocks that fail to program or erase and mark them bad. The data is then written to a different, good block, and the bad block map is updated.
Hamming codes are the most commonly used ECC for SLC NAND flash. Reed-Solomon codes and BCH codes (Bose-Chaudhuri-Hocquenghem codes) are commonly used ECC for MLC NAND flash. Some MLC NAND flash chips internally generate the appropriate BCH error correction codes.[96]
Most NAND devices are shipped from the factory with some bad blocks. These are typically marked according to a specified bad block marking strategy. By allowing some bad blocks, manufacturers achieve far higher yields than would be possible if all blocks had to be verified to be good. This significantly reduces NAND flash costs and only slightly decreases the storage capacity of the parts.
When executing software from NAND memories, virtual memory strategies are often used: memory contents must first be paged or copied into memory-mapped RAM and executed there (leading to the common combination of NAND + RAM). A memory management unit (MMU) in the system is helpful, but this can also be accomplished with overlays. For this reason, some systems will use a combination of NOR and NAND memories, where a smaller NOR memory is used as software ROM and a larger NAND memory is partitioned with a file system for use as a non-volatile data storage area.
NAND sacrifices the random-access and execute-in-place advantages of NOR. NAND is best suited to systems requiring high capacity data storage. It offers higher densities, larger capacities, and lower cost. It has faster erases, sequential writes, and sequential reads.
Standardization
A group called the Open NAND Flash Interface Working Group (ONFI) has developed a standardized low-level interface for NAND flash chips. This allows interoperability between conforming NAND devices from different vendors. The ONFI specification version 1.0[103] was released on 28 December 2006. It specifies:
- A standard physical interface (pinout) for NAND flash in TSOP-48, WSOP-48, LGA-52, and BGA-63 packages
- A standard command set for reading, writing, and erasing NAND flash chips
- A mechanism for self-identification (comparable to the serial presence detection feature of SDRAM memory modules)
The ONFI group is supported by major NAND flash manufacturers, including Hynix, Intel, Micron Technology, and Numonyx, as well as by major manufacturers of devices incorporating NAND flash chips.[104]
Two major flash device manufacturers, Toshiba and Samsung, have chosen to use an interface of their own design known as Toggle Mode (and now Toggle). This interface isn't pin-to-pin compatible with the ONFI specification. The result is that a product designed for one vendor's devices may not be able to use another vendor's devices.[105]
A group of vendors, including Intel, Dell, and Microsoft, formed a Non-Volatile Memory Host Controller Interface (NVMHCI) Working Group.[106] The goal of the group is to provide standard software and hardware programming interfaces for nonvolatile memory subsystems, including the "flash cache" device connected to the PCI Express bus.
Distinction between NOR and NAND flash
NOR and NAND flash differ in two important ways:
- The connections of the individual memory cells are different.[107]
- The interface provided for reading and writing the memory is different; NOR allows random access as it can be either byte-addressable or word-addressable, with words being for example 32 bits long,[108][109][110] while NAND allows only page access.[111]
NOR and NAND flash get their names from the structure of the interconnections between memory cells.[citation needed] In NOR flash, cells are connected in parallel to the bit lines, allowing cells to be read and programmed individually.[112] The parallel connection of cells resembles the parallel connection of transistors in a CMOS NOR gate.[113] In NAND flash, cells are connected in series,[112] resembling a CMOS NAND gate. The series connections consume less space than parallel ones, reducing the cost of NAND flash.[112] It does not, by itself, prevent NAND cells from being read and programmed individually.[citation needed]
Each NOR flash cell is larger than a NAND flash cell – 10 F2 vs 4 F2 – even when using exactly the same semiconductor device fabrication and so each transistor, contact, etc. is exactly the same size – because NOR flash cells require a separate metal contact for each cell.[114]
Because of the series connection and removal of wordline contacts, a large grid of NAND flash memory cells will occupy perhaps only 60% of the area of equivalent NOR cells[115] (assuming the same CMOS process resolution, for example, 130 nm, 90 nm, or 65 nm). NAND flash's designers realized that the area of a NAND chip, and thus the cost, could be further reduced by removing the external address and data bus circuitry. Instead, external devices could communicate with NAND flash via sequential-accessed command and data registers, which would internally retrieve and output the necessary data. This design choice made random-access of NAND flash memory impossible, but the goal of NAND flash was to replace mechanical hard disks, not to replace ROMs.
| Attribute | NAND | NOR |
|---|---|---|
| Main application | File storage | Code execution |
| Storage capacity | High | Low |
| Cost per bit | Low |
|
| Active power | Low |
|
| Standby power | Low | |
| Write speed | Fast |
|
| Read speed | Fast | |
| Execute in place (XIP) | No | Yes |
| Reliability | High |
Write endurance
The write endurance of SLC floating-gate NOR flash is typically equal to or greater than that of NAND flash, while MLC NOR and NAND flash have similar endurance capabilities. Examples of endurance cycle ratings listed in datasheets for NAND and NOR flash, as well as in storage devices using flash memory, are provided.[116]
| Type of flash memory |
Endurance rating (erases per block) |
Example(s) of flash memory or storage device |
|---|---|---|
| SLC NAND | 100,000 | Samsung OneNAND KFW4G16Q2M, Toshiba SLC NAND Flash chips,[117][118][119][120][121] Transcend SD500, Fujitsu S26361-F3298 |
| MLC NAND | 5,000–10,000 for medium-capacity; 1,000 to 3,000 for high-capacity[122] |
Samsung K9G8G08U0M (Example for medium-capacity applications), Memblaze PBlaze4,[123] ADATA SU900, Mushkin Reactor |
| TLC NAND | 1,000 | Samsung SSD 840 |
| QLC NAND | unknown | SanDisk X4 NAND flash SD cards[124][125][126][127] |
| 3D SLC NAND | 100,000 | Samsung Z-NAND[128] |
| 3D MLC NAND | 6,000–40,000 | Samsung SSD 850 PRO, Samsung SSD 845DC PRO,[129][130] Samsung 860 PRO |
| 3D TLC NAND | 1,000–3,000 | Samsung SSD 850 EVO, Samsung SSD 845DC EVO, Crucial MX300[131][132][133],Memblaze PBlaze5 900, Memblaze PBlaze5 700, Memblaze PBlaze5 910/916,Memblaze PBlaze5 510/516,[134][135][136][137] ADATA SX 8200 PRO (also being sold under "XPG Gammix" branding, model S11 PRO) |
| 3D QLC NAND | 100–1,000 | Samsung SSD 860 QVO SATA, Intel SSD 660p, Samsung SSD 980 QVO NVMe, Micron 5210 ION, Samsung SSD BM991 NVMe[138][139][140][141][142][143][144][145] |
| 3D PLC NAND | unknown | In development by SK Hynix (formerly Intel)[146] and Kioxia (formerly Toshiba Memory).[122] |
| SLC (floating- gate) NOR |
100,000–1,000,000 | Numonyx M58BW (Endurance rating of 100,000 erases per block); Spansion S29CD016J (Endurance rating of 1,000,000 erases per block) |
| MLC (floating- gate) NOR |
100,000 | Numonyx J3 flash |
However, by applying certain algorithms and design paradigms such as wear leveling and memory over-provisioning, the endurance of a storage system can be tuned to serve specific requirements.[147]
In order to compute the longevity of the NAND flash, one must account for the size of the memory chip, the type of memory (e.g. SLC/MLC/TLC), and use pattern. Industrial NAND are in demand due to their capacity, longer endurance and reliability in sensitive environments.
3D NAND performance may degrade as layers are added.[128]
As the number of bits per cell increases, the performance of NAND flash may degrade, increasing random read times to 100μs for TLC NAND which is 4 times the time required in SLC NAND, and twice the time required in MLC NAND, for random reads.[61]
Flash file systems
Because of the particular characteristics of flash memory, it is best used with either a controller to perform wear leveling and error correction or specifically designed flash file systems, which spread writes over the media and deal with the long erase times of NOR flash blocks. The basic concept behind flash file systems is the following: when the flash store is to be updated, the file system will write a new copy of the changed data to a fresh block, remap the file pointers, then erase the old block later when it has time.
In practice, flash file systems are used only for memory technology devices (MTDs), which are embedded flash memories that do not have a controller. Removable flash memory cards, SSDs, eMMC/eUFS chips and USB flash drives have built-in controllers to perform wear leveling and error correction so use of a specific flash file system may not add benefit.
Capacity
Multiple chips are often arrayed or die stacked to achieve higher capacities[148] for use in consumer electronic devices such as multimedia players or GPSs. The capacity scaling (increase) of flash chips used to follow Moore's law because they are manufactured with many of the same integrated circuits techniques and equipment. Since the introduction of 3D NAND, scaling is no longer necessarily associated with Moore's law since ever smaller transistors (cells) are no longer used.
Consumer flash storage devices typically are advertised with usable sizes expressed as a small integer power of two (2, 4, 8, etc.) and a conventional designation of megabytes (MB) or gigabytes (GB); e.g., 512 MB, 8 GB. This includes SSDs marketed as hard drive replacements, in accordance with traditional hard drives, which use decimal prefixes.[149] Thus, an SSD marked as "64 GB" is at least 64 × 10003 bytes (64 GB). Most users will have slightly less capacity than this available for their files, due to the space taken by file system metadata and because some operating systems report SSD capacity using binary prefixes which are somewhat larger than conventional prefixes .
The flash memory chips inside them are sized in strict binary multiples, but the actual total capacity of the chips is not usable at the drive interface. It is considerably larger than the advertised capacity in order to allow for distribution of writes (wear leveling), for sparing, for error correction codes, and for other metadata needed by the device's internal firmware.
In 2005, Toshiba and SanDisk developed a NAND flash chip capable of storing 1 GB of data using multi-level cell (MLC) technology, capable of storing two bits of data per cell. In September 2005, Samsung Electronics announced that it had developed the world's first 2 GB chip.[150]
In March 2006, Samsung announced flash hard drives with a capacity of 4 GB, essentially the same order of magnitude as smaller laptop hard drives, and in September 2006, Samsung announced an 8 GB chip produced using a 40 nm manufacturing process.[151] In January 2008, SanDisk announced availability of their 16 GB MicroSDHC and 32 GB SDHC Plus cards.[152][153]
More recent flash drives (as of 2012) have much greater capacities, holding 64, 128, and 256 GB.[154]
A joint development at Intel and Micron will allow the production of 32-layer 3.5 terabyte (TB[clarification needed]) NAND flash sticks and 10 TB standard-sized SSDs. The device includes 5 packages of 16 × 48 GB TLC dies, using a floating gate cell design.[155]
Flash chips continue to be manufactured with capacities under or around 1 MB (e.g. for BIOS-ROMs and embedded applications).
In July 2016, Samsung announced the 4 TB[clarification needed] Samsung 850 EVO which utilizes their 256 Gbit 48-layer TLC 3D V-NAND.[156] In August 2016, Samsung announced a 32 TB 2.5-inch SAS SSD based on their 512 Gbit 64-layer TLC 3D V-NAND. Further, Samsung expects to unveil SSDs with up to 100 TB of storage by 2020.[157]
Transfer rates
Flash memory devices are typically much faster at reading than writing.[158] Performance also depends on the quality of storage controllers, which become more critical when devices are partially full.[vague][158] Even when the only change to manufacturing is die-shrink, the absence of an appropriate controller can result in degraded speeds.[159]
Applications
Serial flash
Serial flash is a small, low-power flash memory that provides only serial access to the data - rather than addressing individual bytes, the user reads or writes large contiguous groups of bytes in the address space serially. Serial Peripheral Interface Bus (SPI) is a typical protocol for accessing the device. When incorporated into an embedded system, serial flash requires fewer wires on the PCB than parallel flash memories, since it transmits and receives data one bit at a time. This may permit a reduction in board space, power consumption, and total system cost.
There are several reasons why a serial device, with fewer external pins than a parallel device, can significantly reduce overall cost:
- Many ASICs are pad-limited, meaning that the size of the die is constrained by the number of wire bond pads, rather than the complexity and number of gates used for the device logic. Eliminating bond pads thus permits a more compact integrated circuit, on a smaller die; this increases the number of dies that may be fabricated on a wafer, and thus reduces the cost per die.
- Reducing the number of external pins also reduces assembly and packaging costs. A serial device may be packaged in a smaller and simpler package than a parallel device.
- Smaller and lower pin-count packages occupy less PCB area.
- Lower pin-count devices simplify PCB routing.
There are two major SPI flash types. The first type is characterized by small pages and one or more internal SRAM page buffers allowing a complete page to be read to the buffer, partially modified, and then written back (for example, the Atmel AT45 DataFlash or the Micron Technology Page Erase NOR Flash). The second type has larger sectors where the smallest sectors typically found in this type of SPI flash are 4 kB, but they can be as large as 64 kB. Since this type of SPI flash lacks an internal SRAM buffer, the complete page must be read out and modified before being written back, making it slow to manage. However, the second type is cheaper than the first and is therefore a good choice when the application is code shadowing.
The two types are not easily exchangeable, since they do not have the same pinout, and the command sets are incompatible.
Most FPGAs are based on SRAM configuration cells and require an external configuration device, often a serial flash chip, to reload the configuration bitstream every power cycle.[160]
Firmware storage
With the increasing speed of modern CPUs, parallel flash devices are often much slower than the memory bus of the computer they are connected to. Conversely, modern SRAM offers access times below 10 ns, while DDR2 SDRAM offers access times below 20 ns. Because of this, it is often desirable to shadow code stored in flash into RAM; that is, the code is copied from flash into RAM before execution, so that the CPU may access it at full speed. Device firmware may be stored in a serial flash chip, and then copied into SDRAM or SRAM when the device is powered-up.[161] Using an external serial flash device rather than on-chip flash removes the need for significant process compromise (a manufacturing process that is good for high-speed logic is generally not good for flash and vice versa). Once it is decided to read the firmware in as one big block it is common to add compression to allow a smaller flash chip to be used. Since 2005, many devices use serial NOR flash to deprecate parallel NOR flash for firmware storage. Typical applications for serial flash include storing firmware for hard drives, Ethernet network interface adapters, DSL modems, etc.
Flash memory as a replacement for hard drives
One more recent application for flash memory is as a replacement for hard disks. Flash memory does not have the mechanical limitations and latencies of hard drives, so a solid-state drive (SSD) is attractive when considering speed, noise, power consumption, and reliability. Flash drives are gaining traction as mobile device secondary storage devices; they are also used as substitutes for hard drives in high-performance desktop computers and some servers with RAID and SAN architectures.
There remain some aspects of flash-based SSDs that make them unattractive. The cost per gigabyte of flash memory remains significantly higher than that of hard disks.[162] Also flash memory has a finite number of P/E (program/erase) cycles, but this seems to be currently under control since warranties on flash-based SSDs are approaching those of current hard drives.[163] In addition, deleted files on SSDs can remain for an indefinite period of time before being overwritten by fresh data; erasure or shred techniques or software that work well on magnetic hard disk drives have no effect on SSDs, compromising security and forensic examination. However, due to the so-called TRIM command employed by most solid state drives, which marks the logical block addresses occupied by the deleted file as unused to enable garbage collection, data recovery software is not able to restore files deleted from such.
For relational databases or other systems that require ACID transactions, even a modest amount of flash storage can offer vast speedups over arrays of disk drives.[164][165]
In May 2006, Samsung Electronics announced two flash-memory based PCs, the Q1-SSD and Q30-SSD were expected to become available in June 2006, both of which used 32 GB SSDs, and were at least initially available only in South Korea.[166] The Q1-SSD and Q30-SSD launch was delayed and finally was shipped in late August 2006.[167]
The first flash-memory based PC to become available was the Sony Vaio UX90, announced for pre-order on 27 June 2006 and began to be shipped in Japan on 3 July 2006 with a 16Gb flash memory hard drive.[168] In late September 2006 Sony upgraded the flash-memory in the Vaio UX90 to 32Gb.[169]
A solid-state drive was offered as an option with the first MacBook Air introduced in 2008, and from 2010 onwards, all models were shipped with an SSD. Starting in late 2011, as part of Intel's Ultrabook initiative, an increasing number of ultra-thin laptops are being shipped with SSDs standard.
There are also hybrid techniques such as hybrid drive and ReadyBoost that attempt to combine the advantages of both technologies, using flash as a high-speed non-volatile cache for files on the disk that are often referenced, but rarely modified, such as application and operating system executable files.
Flash memory as RAM
As of 2012, there are attempts to use flash memory as the main computer memory, DRAM.[170]
Archival or long-term storage
Floating-gate transistors in the flash storage device hold charge which represents data. This charge gradually leaks over time, leading to an accumulation of logical errors, also known as "bit rot" or "bit fading".[171]
Data retention
It is unclear how long data on flash memory will persist under archival conditions (i.e., benign temperature and humidity with infrequent access with or without prophylactic rewrite). Datasheets of Atmel's flash-based "ATmega" microcontrollers typically promise retention times of 20 years at 85 °C (185 °F) and 100 years at 25 °C (77 °F).[172]
The retention span varies among types and models of flash storage. When supplied with power and idle, the charge of the transistors holding the data is routinely refreshed by the firmware of the flash storage.[171] The ability to retain data varies among flash storage devices due to differences in firmware, data redundancy, and error correction algorithms.[173]
An article from CMU in 2015 states "Today's flash devices, which do not require flash refresh, have a typical retention age of 1 year at room temperature." And that retention time decreases exponentially with increasing temperature. The phenomenon can be modeled by the Arrhenius equation.[174][175]
FPGA configuration
Some FPGAs are based on flash configuration cells that are used directly as (programmable) switches to connect internal elements together, using the same kind of floating-gate transistor as the flash data storage cells in data storage devices.[160]
Industry
One source states that, in 2008, the flash memory industry includes about US$9.1 billion in production and sales. Other sources put the flash memory market at a size of more than US$20 billion in 2006, accounting for more than eight percent of the overall semiconductor market and more than 34 percent of the total semiconductor memory market.[176] In 2012, the market was estimated at $26.8 billion.[177] It can take up to 10 weeks to produce a flash memory chip.[178]
Manufacturers
The following were the largest NAND flash memory manufacturers, as of the first quarter of 2019.[179]
- Samsung Electronics – 34.9%
- Kioxia – 18.1%
- Western Digital Corporation – 14%
- Micron Technology – 13.5%
- SK Hynix – 10.3%
- Intel – 8.7% Note: SK Hynix acquired Intel's NAND business at the end of 2021[180]
Samsung remains the largest NAND flash memory manufacturer as of first quarter 2022.[181]
Shipments
| Year(s) | Discrete flash memory chips | Flash memory data capacity (gigabytes) | Floating-gate MOSFET memory cells (billions) |
|---|---|---|---|
| 1992 | 26,000,000[182] | 3[182] | 24[a] |
| 1993 | 73,000,000[182] | 17[182] | 139[a] |
| 1994 | 112,000,000[182] | 25[182] | 203[a] |
| 1995 | 235,000,000[182] | 38[182] | 300[a] |
| 1996 | 359,000,000[182] | 140[182] | 1,121[a] |
| 1997 | 477,200,000+[183] | 317+[183] | 2,533+[a] |
| 1998 | 762,195,122[184] | 455+[183] | 3,642+[a] |
| 1999 | 12,800,000,000[185] | 635+[183] | 5,082+[a] |
| 2000–2004 | 134,217,728,000 (NAND)[186] | 1,073,741,824,000 (NAND)[186] | |
| 2005–2007 | ? | ||
| 2008 | 1,226,215,645 (mobile NAND)[187] | ||
| 2009 | 1,226,215,645+ (mobile NAND) | ||
| 2010 | 7,280,000,000+[b] | ||
| 2011 | 8,700,000,000[189] | ||
| 2012 | 5,151,515,152 (serial)[190] | ||
| 2013 | ? | ||
| 2014 | ? | 59,000,000,000[191] | 118,000,000,000+[a] |
| 2015 | 7,692,307,692 (NAND)[192] | 85,000,000,000[193] | 170,000,000,000+[a] |
| 2016 | ? | 100,000,000,000[194] | 200,000,000,000+[a] |
| 2017 | ? | 148,200,000,000[c] | 296,400,000,000+[a] |
| 2018 | ? | 231,640,000,000[d] | 463,280,000,000+[a] |
| 2019 | ? | ? | ? |
| 2020 | ? | ? | ? |
| 1992–2020 | 45,358,454,134+ memory chips | 758,057,729,630+ gigabytes | 2,321,421,837,044 billion+ cells |
In addition to individual flash memory chips, flash memory is also embedded in microcontroller (MCU) chips and system-on-chip (SoC) devices.[198] Flash memory is embedded in ARM chips,[198] which have sold 150 billion units worldwide as of 2019,[199] and in programmable system-on-chip (PSoC) devices, which have sold 1.1 billion units as of 2012.[200] This adds up to at least 151.1 billion MCU and SoC chips with embedded flash memory, in addition to the 45.4 billion known individual flash chip sales as of 2015, totalling at least 196.5 billion chips containing flash memory.
Flash scalability
Due to its relatively simple structure and high demand for higher capacity, NAND flash memory is the most aggressively scaled technology among electronic devices. The heavy competition among the top few manufacturers only adds to the aggressiveness in shrinking the floating-gate MOSFET design rule or process technology node.[90] While the expected shrink timeline is a factor of two every three years per original version of Moore's law, this has recently been accelerated in the case of NAND flash to a factor of two every two years.
| ITRS or company | 2010 | 2011 | 2012 | 2013 | 2014 | 2015 | 2016 | 2017 | 2018 |
|---|---|---|---|---|---|---|---|---|---|
| ITRS Flash Roadmap 2011[201] | 32 nm | 22 nm | 20 nm | 18 nm | 16 nm |
| |||
| Updated ITRS Flash Roadmap[202] | 17 nm | 15 nm | 14 nm |
| |||||
| Samsung[201][202][203] (Samsung 3D NAND)[202] |
35–20 nm[31] | 27 nm | 21 nm (MLC, TLC) |
19–16 nm 19–10 nm (MLC, TLC)[204] |
19–10 nm V-NAND (24L) |
16–10 nm V-NAND (32L) |
16–10 nm | 12–10 nm | 12–10 nm |
| Micron, Intel[201][202][203] | 34–25 nm | 25 nm | 20 nm (MLC + HKMG) |
20 nm (TLC) |
16 nm | 16 nm 3D NAND |
16 nm 3D NAND |
12 nm 3D NAND |
12 nm 3D NAND |
| Toshiba, WD (SanDisk)[201][202][203] | 43–32 nm 24 nm (Toshiba)[205] |
24 nm | 19 nm (MLC, TLC) |
15 nm | 15 nm 3D NAND |
15 nm 3D NAND |
12 nm 3D NAND |
12 nm 3D NAND | |
| SK Hynix[201][202][203] | 46–35 nm | 26 nm | 20 nm (MLC) | 16 nm | 16 nm | 16 nm | 12 nm | 12 nm |
As the MOSFET feature size of flash memory cells reaches the 15–16 nm minimum limit, further flash density increases will be driven by TLC (3 bits/cell) combined with vertical stacking of NAND memory planes. The decrease in endurance and increase in uncorrectable bit error rates that accompany feature size shrinking can be compensated by improved error correction mechanisms.[206] Even with these advances, it may be impossible to economically scale flash to smaller and smaller dimensions as the number of electron holding capacity reduces. Many promising new technologies (such as FeRAM, MRAM, PMC, PCM, ReRAM, and others) are under investigation and development as possible more scalable replacements for flash.[207]
Timeline
| Date of introduction | Chip name | Memory Package Capacity Megabits (Mb), Gigabits (Gb), Terabits (Tb) |
Flash type | Cell type | Layers or Stacks of Layers |
Manufacturer(s) | Process | Area | Ref |
|---|---|---|---|---|---|---|---|---|---|
| 1984 | ? | ? | NOR | SLC | 1 | Toshiba | ? | ? | [20] |
| 1985 | ? | 256 kb | NOR | SLC | 1 | Toshiba | 2,000 nm | ? | [28] |
| 1987 | ? | ? | NAND | SLC | 1 | Toshiba | ? | ? | [1] |
| 1989 | ? | 1 Mb | NOR | SLC | 1 | Seeq, Intel | ? | ? | [28] |
| 4 Mb | NAND | SLC | 1 | Toshiba | 1,000 nm |
| |||
| 1991 | ? | 16 Mb | NOR | SLC | 1 | Mitsubishi | 600 nm | ? | [28] |
| 1993 | DD28F032SA | 32 Mb | NOR | SLC | 1 | Intel | ? | 280 mm² | [208][209] |
| 1994 | ? | 64 Mb | NOR | SLC | 1 | NEC | 400 nm | ? | [28] |
| 1995 | ? | 16 Mb | DINOR | SLC | 1 | Mitsubishi, Hitachi | ? | ? | [28][210] |
| NAND | SLC | 1 | Toshiba | ? | ? | [211] | |||
| 32 Mb | NAND | SLC | 1 | Hitachi, Samsung, Toshiba | ? | ? | [28] | ||
| 34 Mb | Serial | SLC | 1 | SanDisk |
| ||||
| 1996 | ? | 64 Mb | NAND | SLC | 1 | Hitachi, Mitsubishi | 400 nm | ? | [28] |
| QLC | 1 | NEC |
| ||||||
| 128 Mb | NAND | SLC | 1 | Samsung, Hitachi | ? |
| |||
| 1997 | ? | 32 Mb | NOR | SLC | 1 | Intel, Sharp | 400 nm | ? | [212] |
| NAND | SLC | 1 | AMD, Fujitsu | 350 nm |
| ||||
| 1999 | ? | 256 Mb | NAND | SLC | 1 | Toshiba | 250 nm | ? | [28] |
| MLC | 1 | Hitachi | 1 |
| |||||
| 2000 | ? | 32 Mb | NOR | SLC | 1 | Toshiba | 250 nm | ? | [28] |
| 64 Mb | NOR | QLC | 1 | STMicroelectronics | 180 nm |
| |||
| 512 Mb | NAND | SLC | 1 | Toshiba | ? | ? | [213] | ||
| 2001 | ? | 512 Mb | NAND | MLC | 1 | Hitachi | ? | ? | [28] |
| 1 Gibit | NAND | MLC | 1 | Samsung |
| ||||
| 1 | Toshiba, SanDisk | 160 nm | ? | [214] | |||||
| 2002 | ? | 512 Mb | NROM | MLC | 1 | Saifun | 170 nm | ? | [28] |
| 2 Gb | NAND | SLC | 1 | Samsung, Toshiba | ? | ? | [215][216] | ||
| 2003 | ? | 128 Mb | NOR | MLC | 1 | Intel | 130 nm | ? | [28] |
| 1 Gb | NAND | MLC | 1 | Hitachi |
| ||||
| 2004 | ? | 8 Gb | NAND | SLC | 1 | Samsung | 60 nm | ? | [215] |
| 2005 | ? | 16 Gb | NAND | SLC | 1 | Samsung | 50 nm | ? | [31] |
| 2006 | ? | 32 Gb | NAND | SLC | 1 | Samsung | 40 nm |
| |
| Apr-07 | THGAM | 128 Gb | Stacked NAND | SLC | Toshiba | 56 nm | 252 mm² | [47] | |
| Sep-07 | ? | 128 Gb | Stacked NAND | SLC | Hynix | ? | ? | [48] | |
| 2008 | THGBM | 256 Gb | Stacked NAND | SLC | Toshiba | 43 nm | 353 mm² | [49] | |
| 2009 | ? | 32 Gb | NAND | TLC | Toshiba | 32 nm | 113 mm² | [29] | |
| 64 Gb | NAND | QLC | Toshiba, SanDisk | 43 nm | ? | [29][30] | |||
| 2010 | ? | 64 Gb | NAND | SLC | Hynix | 20 nm | ? | [217] | |
| TLC | Samsung | 20 nm | ? | [31] | |||||
| THGBM2 | 1 Tb | Stacked NAND | QLC | Toshiba | 32 nm | 374 mm² | [50] | ||
| 2011 | KLMCG8GE4A | 512 Gb | Stacked NAND | MLC | Samsung | ? | 192 mm² | [218] | |
| 2013 | ? | ? | NAND | SLC | SK Hynix | 16 nm | ? | [217] | |
| 128 Gb | V-NAND | TLC | Samsung | 10 nm | ? |
| |||
| 2015 | ? | 256 Gb | V-NAND | TLC | Samsung | ? | ? | [204] | |
| 2017 | eUFS 2.1 | 512 Gb | V-NAND | TLC | 8 of 64 | Samsung | ? | ? | [53] |
| 768 Gb | V-NAND | QLC | Toshiba | ? | ? | [219] | |||
| KLUFG8R1EM | 4 Tb | Stacked V-NAND | TLC | Samsung | ? | 150 mm² | [53] | ||
| 2018 | ? | 1 Tb | V-NAND | QLC | Samsung | ? | ? | [220] | |
| 1.33 Tb | V-NAND | QLC | Toshiba | ? | 158 mm² | [221][222] | |||
| 2019 | ? | 512 Gb | V-NAND | QLC | Samsung | ? | ? | [54][55] | |
| 1 Tb | V-NAND | TLC | SK Hynix | ? | ? | [223] | |||
| eUFS 2.1 | 1 Tb | Stacked V-NAND[224] | QLC | 16 of 64 | Samsung | ? | 150 mm² | [54][55][225] |
See also
- eMMC
- Flash memory controller
- List of flash file systems
- List of flash memory controller manufacturers
- microSDXC (up to 2 TB), and the successor format Secure Digital Ultra Capacity (SDUC) supporting cards up to 128 TiB
- Open NAND Flash Interface Working Group
- Read-mostly memory (RMM)
- Universal Flash Storage
- USB flash drive security
- Write amplification
Notes
- NOR – 3.64 billion[188]
- NAND – 3.64 billion+ (est.)
- NAND non-volatile memory (NVM) – 85 exabytes (est.)[195]
- Solid-state drive (SSD) – 63.2 exabytes[196]
References
The flash memory can be reprogrammed up to 100 times.[permanent dead link]
The devices offer single-power-supply operation (2.7 V to 3.6 V), sector architecture, Embedded Algorithms, high performance, and a 1,000,000 program/erase cycle endurance guarantee.
The PSoC ... utilizes a unique Flash process: SONOS
Reliability Qualification results show that the projected data retention failure rate is much less than 1 PPM over 20 years at 85 °C or 100 years at 25 °C
Unit shipments increased 64% in 1999 from the prior year, and are forecast to increase 44% to 1.8 billion units in 2000.
- "Samsung Breaks Terabyte Threshold for Smartphone Storage with Industry's First 1TB Embedded Universal Flash Storage". Samsung. 30 January 2019. Retrieved 13 July 2019.
External links
- Semiconductor Characterization System has diverse functions
- Understanding and selecting higher performance NAND architectures Archived 31 October 2012 at the Wayback Machine
- How flash storage works, presentation by David Woodhouse from Intel
- Flash endurance testing
- NAND Flash Data Recovery Cookbook
- Type of Flash Memory by OpenWrt
https://en.wikipedia.org/wiki/Flash_memory
An EPROM (rarely EROM), or erasable programmable read-only memory, is a type of programmable read-only memory (PROM) chip that retains its data when its power supply is switched off. Computer memory that can retrieve stored data after a power supply has been turned off and back on is called non-volatile. It is an array of floating-gate transistors individually programmed by an electronic device that supplies higher voltages than those normally used in digital circuits. Once programmed, an EPROM can be erased by exposing it to strong ultraviolet light source (such as from a mercury-vapor lamp). EPROMs are easily recognizable by the transparent fused quartz (or on later models resin) window on the top of the package, through which the silicon chip is visible, and which permits exposure to ultraviolet light during erasing.[2]
Operation
Development of the EPROM memory cell started with investigation of faulty integrated circuits where the gate connections of transistors had broken. Stored charge on these isolated gates changes their threshold voltage.
Following the invention of the MOSFET (metal–oxide–semiconductor field-effect transistor) by Mohamed Atalla and Dawon Kahng at Bell Labs, presented in 1960, Frank Wanlass studied MOSFET structures in the early 1960s. In 1963, he noted the movement of charge through oxide onto a gate. While he did not pursue it, this idea would later become the basis for EPROM technology.[3]
In 1967, Dawon Kahng and Simon Min Sze at Bell Labs proposed that the floating gate of a MOSFET could be used for the cell of a reprogrammable ROM (read-only memory).[4] Building on this concept, Dov Frohman of Intel invented EPROM in 1971,[4] and was awarded U.S. Patent 3,660,819 in 1972. Frohman designed the Intel 1702, a 2048-bit EPROM, which was announced by Intel in 1971.[4]
Each storage location of an EPROM consists of a single field-effect transistor. Each field-effect transistor consists of a channel in the semiconductor body of the device. Source and drain contacts are made to regions at the end of the channel. An insulating layer of oxide is grown over the channel, then a conductive (silicon or aluminum) gate electrode is deposited, and a further thick layer of oxide is deposited over the gate electrode. The floating-gate electrode has no connections to other parts of the integrated circuit and is completely insulated by the surrounding layers of oxide. A control gate electrode is deposited and further oxide covers it.[5]
To retrieve data from the EPROM, the address represented by the values at the address pins of the EPROM is decoded and used to connect one word (usually an 8-bit byte) of storage to the output buffer amplifiers. Each bit of the word is a 1 or 0, depending on the storage transistor being switched on or off, conducting or non-conducting.
The switching state of the field-effect transistor is controlled by the voltage on the control gate of the transistor. Presence of a voltage on this gate creates a conductive channel in the transistor, switching it on. In effect, the stored charge on the floating gate allows the threshold voltage of the transistor to be programmed.
Storing data in the memory requires selecting a given address and applying a higher voltage to the transistors. This creates an avalanche discharge of electrons, which have enough energy to pass through the insulating oxide layer and accumulate on the gate electrode. When the high voltage is removed, the electrons are trapped on the electrode.[6] Because of the high insulation value of the silicon oxide surrounding the gate, the stored charge cannot readily leak away and the data can be retained for decades.
The programming process is not electrically reversible. To erase the data stored in the array of transistors, ultraviolet light is directed onto the die. Photons of the UV light cause ionization within the silicon oxide, which allows the stored charge on the floating gate to dissipate. Since the whole memory array is exposed, all the memory is erased at the same time. The process takes several minutes for UV lamps of convenient sizes; sunlight would erase a chip in weeks, and indoor fluorescent lighting over several years.[7] Generally, the EPROMs must be removed from equipment to be erased, since it is not usually practical to build in a UV lamp to erase parts in-circuit. Electrically Erasable Programmable Read-Only Memory (EEPROM) was developed to provide an electrical erase function and has now mostly displaced ultraviolet-erased parts.
Details
As the quartz window is expensive to make, OTP (one-time programmable) chips were introduced; here, the die is mounted in an opaque package so it cannot be erased after programming – this also eliminates the need to test the erase function, further reducing cost. OTP versions of both EPROMs and EPROM-based microcontrollers are manufactured. However, OTP EPROM (whether separate or part of a larger chip) is being increasingly replaced by EEPROM for small sizes, where the cell cost isn't too important, and flash for larger sizes.
A programmed EPROM retains its data for a minimum of ten to twenty years,[8] with many still retaining data after 35 or more years, and can be read an unlimited number of times without affecting the lifetime. The erasing window must be kept covered with an opaque label to prevent accidental erasure by the UV found in sunlight or camera flashes. Old PC BIOS chips were often EPROMs, and the erasing window was often covered with an adhesive label containing the BIOS publisher's name, the BIOS revision, and a copyright notice. Often this label was foil-backed to ensure its opacity to UV.
Erasure of the EPROM begins to occur with wavelengths shorter than 400 nm. Exposure time for sunlight of one week or three years for room fluorescent lighting may cause erasure. The recommended erasure procedure is exposure to UV light at 253.7 nm of at least 15 Ws/cm2, usually achieved in 20 to 30 minutes with the lamp at a distance of about 2.5 cm.[9]
Erasure can also be accomplished with X-rays:
Erasure, however, has to be accomplished by non-electrical methods, since the gate electrode is not accessible electrically. Shining ultraviolet light on any part of an unpackaged device causes a photocurrent to flow from the floating gate back to the silicon substrate, thereby discharging the gate to its initial, uncharged condition (photoelectric effect). This method of erasure allows complete testing and correction of a complex memory array before the package is finally sealed. Once the package is sealed, information can still be erased by exposing it to X radiation in excess of 5*104 rads,[a] a dose which is easily attained with commercial X-ray generators.[10]
In other words, to erase your EPROM, you would first have to X-ray it and then put it in an oven at about 600 degrees Celsius (to anneal semiconductor alterations caused by the X-rays). The effects of this process on the reliability of the part would have required extensive testing so they decided on the window instead.[11]
EPROMs have a limited but large number of erase cycles; the silicon dioxide around the gates accumulates damage from each cycle, making the chip unreliable after several thousand cycles. EPROM programming is slow compared to other forms of memory. Because higher-density parts have little exposed oxide between the layers of interconnects and gate, ultraviolet erasing becomes less practical for very large memories. Even dust inside the package can prevent some cells from being erased.[12]
Application
For large volumes of parts (thousands of pieces or more), mask-programmed ROMs are the lowest cost devices to produce. However, these require many weeks lead time to make, since the artwork for an IC mask layer must be altered to store data on the ROMs. Initially, it was thought that the EPROM would be too expensive for mass production use and that it would be confined to development only. It was soon found that small-volume production was economical with EPROM parts, particularly when the advantage of rapid upgrades of firmware was considered.
Some microcontrollers, from before the era of EEPROMs and flash memory, use an on-chip EPROM to store their program. Such microcontrollers include some versions of the Intel 8048, the Freescale 68HC11, and the "C" versions of the PIC microcontroller. Like EPROM chips, such microcontrollers came in windowed (expensive) versions that were used for debugging and program development. The same chip came in (somewhat cheaper) opaque OTP packages for production. Leaving the die of such a chip exposed to light can also change behavior in unexpected ways when moving from a windowed part used for development to a non-windowed part for production.
EPROM generations, sizes and types
The first generation 1702 devices were fabricated with the p-MOS technology. They were powered with VCC = VBB = +5 V and VDD = VGG = -9 V in Read mode, and with VDD = VGG = -47 V in Programming mode.[13][14]
The second generation 2704/2708 devices switched to n-MOS technology and to three-rail VCC = +5 V, VBB = -5 V, VDD = +12 V power supply with VPP = 12 V and a +25 V pulse in Programming mode.
The n-MOS technology evolution introduced single-rail VCC = +5 V power supply and single VPP = +25 V[15] programming voltage without pulse in the third generation. The unneeded VBB and VDD pins were reused for additional address bits allowing larger capacities (2716/2732) in the same 24-pin package, and even larger capacities with larger packages. Later the decreased cost of the CMOS technology allowed the same devices to be fabricated using it, adding the letter "C" to the device numbers (27xx(x) are n-MOS and 27Cxx(x) are CMOS).
While parts of the same size from different manufacturers are compatible in read mode, different manufacturers added different and sometimes multiple programming modes leading to subtle differences in the programming process. This prompted larger capacity devices to introduce a "signature mode", allowing the manufacturer and device to be identified by the EPROM programmer. It was implemented by forcing +12 V on pin A9 and reading out two bytes of data. However, as this was not universal, programmer software also would allow manual setting of the manufacturer and device type of the chip to ensure proper programming.[16]
| EPROM Type | Year | Size — bits | Size — bytes | Length (hex) | Last address (hex) | Technology |
|---|---|---|---|---|---|---|
| 1702, 1702A | 1971 | 2 Kbit | 256 | 100 | FF | PMOS |
| 2704 | 1975 | 4 Kbit | 512 | 200 | 1FF | NMOS |
| 2708 | 1975 | 8 Kbit | 1 KB | 400 | 3FF | NMOS |
| 2716, 27C16, TMS2716, 2516 | 1977 | 16 Kbit | 2 KB | 800 | 7FF | NMOS/CMOS |
| 2732, 27C32, 2532 | 1979 | 32 Kbit | 4 KB | 1000 | FFF | NMOS/CMOS |
| 2764, 27C64, 2564 | 64 Kbit | 8 KB | 2000 | 1FFF | NMOS/CMOS | |
| 27128, 27C128 | 128 Kbit | 16 KB | 4000 | 3FFF | NMOS/CMOS | |
| 27256, 27C256 | 256 Kbit | 32 KB | 8000 | 7FFF | NMOS/CMOS | |
| 27512, 27C512 | 512 Kbit | 64 KB | 10000 | FFFF | NMOS/CMOS | |
| 27C010, 27C100 | 1 Mbit | 128 KB | 20000 | 1FFFF | CMOS | |
| 27C020 | 2 Mbit | 256 KB | 40000 | 3FFFF | CMOS | |
| 27C040, 27C400, 27C4001 | 4 Mbit | 512 KB | 80000 | 7FFFF | CMOS | |
| 27C080 | 8 Mbit | 1 MB | 100000 | FFFFF | CMOS | |
| 27C160 | 16 Mbit | 2 MB | 200000 | 1FFFFF | CMOS | |
| 27C320, 27C322 | 32 Mbit | 4 MB | 400000 | 3FFFFF | CMOS |
Gallery
This 8749 Microcontroller stores its program in internal EPROM.
See also
- Programmable ROM
- EEPROM
- Flash memory
- Intel HEX - File format
- SREC - File format
- Programmer (hardware)
Notes
- 500 J/kg
References
- U.S. International Trade Commission, ed. (October 1998). Certain EPROM, EEPROM, Flash Memory and Flash Microcontroller Semiconductor Devices and Products Containing Same, Inv. 337-TA-395. Diane Publishing. pp. 51–72. ISBN 1-4289-5721-9. The details of SEEQ's Silicon Signature method of a device programmer reading an EPROM's ID.
Bibliography
- Sah, Chih-Tang (1991), Fundamentals of solid-state electronics, World Scientific, ISBN 981-02-0637-2.
External links
https://en.wikipedia.org/wiki/EPROM
https://en.wikipedia.org/wiki/Computer_memory
https://en.wikipedia.org/wiki/EEPROM
Artificial neural networks (ANNs), usually simply called neural networks (NNs) or neural nets,[1] are computing systems inspired by the biological neural networks that constitute animal brains.[2]
An ANN is based on a collection of connected units or nodes called artificial neurons, which loosely model the neurons in a biological brain. Each connection, like the synapses in a biological brain, can transmit a signal to other neurons. An artificial neuron receives signals then processes them and can signal neurons connected to it. The "signal" at a connection is a real number, and the output of each neuron is computed by some non-linear function of the sum of its inputs. The connections are called edges. Neurons and edges typically have a weight that adjusts as learning proceeds. The weight increases or decreases the strength of the signal at a connection. Neurons may have a threshold such that a signal is sent only if the aggregate signal crosses that threshold.
Typically, neurons are aggregated into layers. Different layers may perform different transformations on their inputs. Signals travel from the first layer (the input layer), to the last layer (the output layer), possibly after traversing the layers multiple times.
Training
Neural networks learn (or are trained) by processing examples, each of which contains a known "input" and "result," forming probability-weighted associations between the two, which are stored within the data structure of the net itself. The training of a neural network from a given example is usually conducted by determining the difference between the processed output of the network (often a prediction) and a target output. This difference is the error. The network then adjusts its weighted associations according to a learning rule and using this error value. Successive adjustments will cause the neural network to produce output that is increasingly similar to the target output. After a sufficient number of these adjustments, the training can be terminated based on certain criteria. This is a form of supervised learning.
Such systems "learn" to perform tasks by considering examples, generally without being programmed with task-specific rules. For example, in image recognition, they might learn to identify images that contain cats by analyzing example images that have been manually labeled as "cat" or "no cat" and using the results to identify cats in other images. They do this without any prior knowledge of cats, for example, that they have fur, tails, whiskers, and cat-like faces. Instead, they automatically generate identifying characteristics from the examples that they process.
History
The simplest kind of feedforward neural network (FNN) is a linear network, which consists of a single layer of output nodes; the inputs are fed directly to the outputs via a series of weights. The sum of the products of the weights and the inputs is calculated in each node. The mean squared errors between these calculated outputs and a given target values are minimized by creating an adjustment to the weights. This technique has been known for over two centuries as the method of least squares or linear regression. It was used as a means of finding a good rough linear fit to a set of points by Legendre (1805) and Gauss (1795) for the prediction of planetary movement.[3][4][5][6][7]
Wilhelm Lenz and Ernst Ising created and analyzed the Ising model (1925)[8] which is essentially a non-learning artificial recurrent neural network (RNN) consisting of neuron-like threshold elements.[6] In 1972, Shun'ichi Amari made this architecture adaptive.[9][6] His learning RNN was popularised by John Hopfield in 1982.[10]
Warren McCulloch and Walter Pitts[11] (1943) also considered a non-learning computational model for neural networks.[12] In the late 1940s, D. O. Hebb[13] created a learning hypothesis based on the mechanism of neural plasticity that became known as Hebbian learning. Farley and Wesley A. Clark[14] (1954) first used computational machines, then called "calculators", to simulate a Hebbian network. In 1958, psychologist Frank Rosenblatt invented the perceptron, the first implemented artificial neural network,[15][16][17][18] funded by the United States Office of Naval Research.[19]
Some say that research stagnated following Minsky and Papert (1969),[20] who discovered that basic perceptrons were incapable of processing the exclusive-or circuit and that computers lacked sufficient power to process useful neural networks. However, by the time this book came out, methods for training multilayer perceptrons (MLPs) were already known.
The first deep learning MLP was published by Alexey Grigorevich Ivakhnenko and Valentin Lapa in 1965, as the Group Method of Data Handling.[21][22][23] The first deep learning MLP trained by stochastic gradient descent[24] was published in 1967 by Shun'ichi Amari.[25][6] In computer experiments conducted by Amari's student Saito, a five layer MLP with two modifiable layers learned useful internal representations to classify non-linearily separable pattern classes.[6]
Self-organizing maps (SOMs) were described by Teuvo Kohonen in 1982.[26][27] SOMs are neurophysiologically inspired[28] neural networks that learn low-dimensional representations of high-dimensional data while preserving the topological structure of the data. They are trained using competitive learning.[26]
The convolutional neural network (CNN) architecture with convolutional layers and downsampling layers was introduced by Kunihiko Fukushima in 1980.[29] He called it the neocognitron. In 1969, he also introduced the ReLU (rectified linear unit) activation function.[30][6] The rectifier has become the most popular activation function for CNNs and deep neural networks in general.[31] CNNs have become an essential tool for computer vision.
The backpropagation algorithm is an efficient application of the Leibniz chain rule (1673)[32] to networks of differentiable nodes.[6] It is also known as the reverse mode of automatic differentiation or reverse accumulation, due to Seppo Linnainmaa (1970).[33][34][35][36][6] The term "back-propagating errors" was introduced in 1962 by Frank Rosenblatt,[37][6] but he did not have an implementation of this procedure, although Henry J. Kelley[38] and Bryson[39] had dynamic programming based continuous precursors of backpropagation[21][40][41][42] already in 1960-61 in the context of control theory.[6] In 1973, Dreyfus used backpropagation to adapt parameters of controllers in proportion to error gradients.[43] In 1982, Paul Werbos applied backpropagation to MLPs in the way that has become standard.[44][40] In 1986 Rumelhart, Hinton and Williams showed that backpropagation learned interesting internal representations of words as feature vectors when trained to predict the next word in a sequence.[45]
The time delay neural network (TDNN) of Alex Waibel (1987) combined convolutions and weight sharing and backpropagation.[46][47] In 1988, Wei Zhang et al. applied backpropagation to a CNN (a simplified Neocognitron with convolutional interconnections between the image feature layers and the last fully connected layer) for alphabet recognition.[48][49] In 1989, Yann LeCun et al. trained a CNN to recognize handwritten ZIP codes on mail.[50] In 1992, max-pooling for CNNs was introduced by Juan Weng et al. to help with least-shift invariance and tolerance to deformation to aid 3D object recognition.[51][52][53] LeNet-5 (1998), a 7-level CNN by Yann LeCun et al.,[54] that classifies digits, was applied by several banks to recognize hand-written numbers on checks digitized in 32x32 pixel images.
From 1988 onward,[55][56] the use of neural networks transformed the field of protein structure prediction, in particular when the first cascading networks were trained on profiles (matrices) produced by multiple sequence alignments.[57]
In the 1980s, backpropagation did not work well for deep FNNs and RNNs. To overcome this problem, Juergen Schmidhuber (1992) proposed a hierarchy of RNNs pre-trained one level at a time by self-supervised learning.[58] It uses predictive coding to learn internal representations at multiple self-organizing time scales. This can substantially facilitate downstream deep learning. The RNN hierarchy can be collapsed into a single RNN, by distilling a higher level chunker network into a lower level automatizer network.[58][6] In 1993, a chunker solved a deep learning task whose depth exceeded 1000.[59]
In 1992, Juergen Schmidhuber also published an alternative to RNNs[60] which is now called a linear Transformer or a Transformer with linearized self-attention[61][62][6] (save for a normalization operator). It learns internal spotlights of attention:[63] a slow feedforward neural network learns by gradient descent to control the fast weights of another neural network through outer products of self-generated activation patterns FROM and TO (which are now called key and value for self-attention).[61] This fast weight attention mapping is applied to a query pattern.
The modern Transformer was introduced by Ashish Vaswani et. al. in their 2017 paper "Attention Is All You Need."[64] It combines this with a softmax operator and a projection matrix.[6] Transformers have increasingly become the model of choice for natural language processing.[65] Many modern large language models such as ChatGPT, GPT-4, and BERT use it. Transformers are also increasingly being used in computer vision.[66]
In 1991, Juergen Schmidhuber also published adversarial neural networks that contest with each other in the form of a zero-sum game, where one network's gain is the other network's loss.[67][68][69] The first network is a generative model that models a probability distribution over output patterns. The second network learns by gradient descent to predict the reactions of the environment to these patterns. This was called "artificial curiosity."
In 2014, this principle was used in a generative adversarial network (GAN) by Ian Goodfellow et al.[70] Here the environmental reaction is 1 or 0 depending on whether the first network's output is in a given set. This can be used to create realistic deepfakes.[71] Excellent image quality is achieved by Nvidia's StyleGAN (2018)[72] based on the Progressive GAN by Tero Karras, Timo Aila, Samuli Laine, and Jaakko Lehtinen.[73] Here the GAN generator is grown from small to large scale in a pyramidal fashion.
Sepp Hochreiter's diploma thesis (1991)[74] was called "one of the most important documents in the history of machine learning" by his supervisor Juergen Schmidhuber.[6] Hochreiter identified and analyzed the vanishing gradient problem[74][75] and proposed recurrent residual connections to solve it. This led to the deep learning method called long short-term memory (LSTM), published in Neural Computation (1997).[76] LSTM recurrent neural networks can learn "very deep learning" tasks[77] with long credit assignment paths that require memories of events that happened thousands of discrete time steps before. The "vanilla LSTM" with forget gate was introduced in 1999 by Felix Gers, Schmidhuber and Fred Cummins.[78] LSTM has become the most cited neural network of the 20th century.[6] In 2015, Rupesh Kumar Srivastava, Klaus Greff, and Schmidhuber used the LSTM principle to create the Highway network, a feedforward neural network with hundreds of layers, much deeper than previous networks.[79][80] 7 months later, Kaiming He, Xiangyu Zhang; Shaoqing Ren, and Jian Sun won the ImageNet 2015 competition with an open-gated or gateless Highway network variant called Residual neural network.[81] This has become the most cited neural network of the 21st century.[6]
The development of metal–oxide–semiconductor (MOS) very-large-scale integration (VLSI), in the form of complementary MOS (CMOS) technology, enabled increasing MOS transistor counts in digital electronics. This provided more processing power for the development of practical artificial neural networks in the 1980s.[82]
Neural networks' early successes included predicting the stock market and in 1995 a (mostly) self-driving car.[a][83]
Geoffrey Hinton et al. (2006) proposed learning a high-level representation using successive layers of binary or real-valued latent variables with a restricted Boltzmann machine[84] to model each layer. In 2012, Ng and Dean created a network that learned to recognize higher-level concepts, such as cats, only from watching unlabeled images.[85] Unsupervised pre-training and increased computing power from GPUs and distributed computing allowed the use of larger networks, particularly in image and visual recognition problems, which became known as "deep learning".[86]
Ciresan and colleagues (2010)[87] showed that despite the vanishing gradient problem, GPUs make backpropagation feasible for many-layered feedforward neural networks.[88] Between 2009 and 2012, ANNs began winning prizes in image recognition contests, approaching human level performance on various tasks, initially in pattern recognition and handwriting recognition.[89][90] For example, the bi-directional and multi-dimensional long short-term memory (LSTM)[91][92] of Graves et al. won three competitions in connected handwriting recognition in 2009 without any prior knowledge about the three languages to be learned.[91][92]
Ciresan and colleagues built the first pattern recognizers to achieve human-competitive/superhuman performance[93] on benchmarks such as traffic sign recognition (IJCNN 2012).
Models
This section may be confusing or unclear to readers. (April 2017) |
ANNs began as an attempt to exploit the architecture of the human brain to perform tasks that conventional algorithms had little success with. They soon reoriented towards improving empirical results, abandoning attempts to remain true to their biological precursors. ANNs have the ability to learn and model non-linearities and complex relationships. This is achieved by neurons being connected in various patterns, allowing the output of some neurons to become the input of others. The network forms a directed, weighted graph.[94]
An artificial neural network consists of simulated neurons. Each neuron is connected to other nodes via links like a biological axon-synapse-dendrite connection. All the nodes connected by links take in some data and use it to perform specific operations and tasks on the data. Each link has a weight, determining the strength of one node's influence on another,[95] allowing weights to choose the signal between neurons.
Artificial neurons
ANNs are composed of artificial neurons which are conceptually derived from biological neurons. Each artificial neuron has inputs and produces a single output which can be sent to multiple other neurons.[96] The inputs can be the feature values of a sample of external data, such as images or documents, or they can be the outputs of other neurons. The outputs of the final output neurons of the neural net accomplish the task, such as recognizing an object in an image.
To find the output of the neuron we take the weighted sum of all the inputs, weighted by the weights of the connections from the inputs to the neuron. We add a bias term to this sum.[97] This weighted sum is sometimes called the activation. This weighted sum is then passed through a (usually nonlinear) activation function to produce the output. The initial inputs are external data, such as images and documents. The ultimate outputs accomplish the task, such as recognizing an object in an image.[98]
Organization
The neurons are typically organized into multiple layers, especially in deep learning. Neurons of one layer connect only to neurons of the immediately preceding and immediately following layers. The layer that receives external data is the input layer. The layer that produces the ultimate result is the output layer. In between them are zero or more hidden layers. Single layer and unlayered networks are also used. Between two layers, multiple connection patterns are possible. They can be 'fully connected', with every neuron in one layer connecting to every neuron in the next layer. They can be pooling, where a group of neurons in one layer connects to a single neuron in the next layer, thereby reducing the number of neurons in that layer.[99] Neurons with only such connections form a directed acyclic graph and are known as feedforward networks.[100] Alternatively, networks that allow connections between neurons in the same or previous layers are known as recurrent networks.[101]
Hyperparameter
A hyperparameter is a constant parameter whose value is set before the learning process begins. The values of parameters are derived via learning. Examples of hyperparameters include learning rate, the number of hidden layers and batch size.[102] The values of some hyperparameters can be dependent on those of other hyperparameters. For example, the size of some layers can depend on the overall number of layers.
Learning
This section includes a list of references, related reading, or external links, but its sources remain unclear because it lacks inline citations. (August 2019) |
Learning is the adaptation of the network to better handle a task by considering sample observations. Learning involves adjusting the weights (and optional thresholds) of the network to improve the accuracy of the result. This is done by minimizing the observed errors. Learning is complete when examining additional observations does not usefully reduce the error rate. Even after learning, the error rate typically does not reach 0. If after learning, the error rate is too high, the network typically must be redesigned. Practically this is done by defining a cost function that is evaluated periodically during learning. As long as its output continues to decline, learning continues. The cost is frequently defined as a statistic whose value can only be approximated. The outputs are actually numbers, so when the error is low, the difference between the output (almost certainly a cat) and the correct answer (cat) is small. Learning attempts to reduce the total of the differences across the observations. Most learning models can be viewed as a straightforward application of optimization theory and statistical estimation.[94][103]
Learning rate
The learning rate defines the size of the corrective steps that the model takes to adjust for errors in each observation.[104] A high learning rate shortens the training time, but with lower ultimate accuracy, while a lower learning rate takes longer, but with the potential for greater accuracy. Optimizations such as Quickprop are primarily aimed at speeding up error minimization, while other improvements mainly try to increase reliability. In order to avoid oscillation inside the network such as alternating connection weights, and to improve the rate of convergence, refinements use an adaptive learning rate that increases or decreases as appropriate.[105] The concept of momentum allows the balance between the gradient and the previous change to be weighted such that the weight adjustment depends to some degree on the previous change. A momentum close to 0 emphasizes the gradient, while a value close to 1 emphasizes the last change.
Cost function
While it is possible to define a cost function ad hoc, frequently the choice is determined by the function's desirable properties (such as convexity) or because it arises from the model (e.g. in a probabilistic model the model's posterior probability can be used as an inverse cost).
Backpropagation
Backpropagation is a method used to adjust the connection weights to compensate for each error found during learning. The error amount is effectively divided among the connections. Technically, backprop calculates the gradient (the derivative) of the cost function associated with a given state with respect to the weights. The weight updates can be done via stochastic gradient descent or other methods, such as extreme learning machines,[106] "no-prop" networks,[107] training without backtracking,[108] "weightless" networks,[109][110] and non-connectionist neural networks.[citation needed]
Learning paradigms
This section includes a list of references, related reading, or external links, but its sources remain unclear because it lacks inline citations. (August 2019) |
Machine learning is commonly separated into three main learning paradigms, supervised learning,[111] unsupervised learning[112] and reinforcement learning.[113] Each corresponds to a particular learning task.
Supervised learning
Supervised learning uses a set of paired inputs and desired outputs. The learning task is to produce the desired output for each input. In this case, the cost function is related to eliminating incorrect deductions.[114] A commonly used cost is the mean-squared error, which tries to minimize the average squared error between the network's output and the desired output. Tasks suited for supervised learning are pattern recognition (also known as classification) and regression (also known as function approximation). Supervised learning is also applicable to sequential data (e.g., for hand writing, speech and gesture recognition). This can be thought of as learning with a "teacher", in the form of a function that provides continuous feedback on the quality of solutions obtained thus far.
Unsupervised learning
In unsupervised learning, input data is given along with the cost function, some function of the data and the network's output. The cost function is dependent on the task (the model domain) and any a priori assumptions (the implicit properties of the model, its parameters and the observed variables). As a trivial example, consider the model where is a constant and the cost . Minimizing this cost produces a value of that is equal to the mean of the data. The cost function can be much more complicated. Its form depends on the application: for example, in compression it could be related to the mutual information between and , whereas in statistical modeling, it could be related to the posterior probability of the model given the data (note that in both of those examples, those quantities would be maximized rather than minimized). Tasks that fall within the paradigm of unsupervised learning are in general estimation problems; the applications include clustering, the estimation of statistical distributions, compression and filtering.
Reinforcement learning
In applications such as playing video games, an actor takes a string of actions, receiving a generally unpredictable response from the environment after each one. The goal is to win the game, i.e., generate the most positive (lowest cost) responses. In reinforcement learning, the aim is to weight the network (devise a policy) to perform actions that minimize long-term (expected cumulative) cost. At each point in time the agent performs an action and the environment generates an observation and an instantaneous cost, according to some (usually unknown) rules. The rules and the long-term cost usually only can be estimated. At any juncture, the agent decides whether to explore new actions to uncover their costs or to exploit prior learning to proceed more quickly.
Formally the environment is modeled as a Markov decision process (MDP) with states and actions . Because the state transitions are not known, probability distributions are used instead: the instantaneous cost distribution , the observation distribution and the transition distribution , while a policy is defined as the conditional distribution over actions given the observations. Taken together, the two define a Markov chain (MC). The aim is to discover the lowest-cost MC.
ANNs serve as the learning component in such applications.[115][116] Dynamic programming coupled with ANNs (giving neurodynamic programming)[117] has been applied to problems such as those involved in vehicle routing,[118] video games, natural resource management[119][120] and medicine[121] because of ANNs ability to mitigate losses of accuracy even when reducing the discretization grid density for numerically approximating the solution of control problems. Tasks that fall within the paradigm of reinforcement learning are control problems, games and other sequential decision making tasks.
Self-learning
Self-learning in neural networks was introduced in 1982 along with a neural network capable of self-learning named crossbar adaptive array (CAA).[122] It is a system with only one input, situation s, and only one output, action (or behavior) a. It has neither external advice input nor external reinforcement input from the environment. The CAA computes, in a crossbar fashion, both decisions about actions and emotions (feelings) about encountered situations. The system is driven by the interaction between cognition and emotion.[123] Given the memory matrix, W =||w(a,s)||, the crossbar self-learning algorithm in each iteration performs the following computation:
In situation s perform action a; Receive consequence situation s'; Compute emotion of being in consequence situation v(s'); Update crossbar memory w'(a,s) = w(a,s) + v(s').
The backpropagated value (secondary reinforcement) is the emotion toward the consequence situation. The CAA exists in two environments, one is behavioral environment where it behaves, and the other is genetic environment, where from it initially and only once receives initial emotions about to be encountered situations in the behavioral environment. Having received the genome vector (species vector) from the genetic environment, the CAA will learn a goal-seeking behavior, in the behavioral environment that contains both desirable and undesirable situations.[124]
Neuroevolution
Neuroevolution can create neural network topologies and weights using evolutionary computation. With modern enhancements, neuroevolution is competitive with sophisticated gradient descent approaches.[125] One advantage of neuroevolution is that it may be less prone to get caught in "dead ends".[126]
Stochastic neural network
Stochastic neural networks originating from Sherrington–Kirkpatrick models are a type of artificial neural network built by introducing random variations into the network, either by giving the network's artificial neurons stochastic transfer functions, or by giving them stochastic weights. This makes them useful tools for optimization problems, since the random fluctuations help the network escape from local minima.[127] Stochastic neural networks trained using a Bayesian approach are known as Bayesian neural networks.[128]
Other
In a Bayesian framework, a distribution over the set of allowed models is chosen to minimize the cost. Evolutionary methods,[129] gene expression programming,[130] simulated annealing,[131] expectation-maximization, non-parametric methods and particle swarm optimization[132] are other learning algorithms. Convergent recursion is a learning algorithm for cerebellar model articulation controller (CMAC) neural networks.[133][134]
Modes
This section includes a list of references, related reading, or external links, but its sources remain unclear because it lacks inline citations. (August 2019) |
Two modes of learning are available: stochastic and batch. In stochastic learning, each input creates a weight adjustment. In batch learning weights are adjusted based on a batch of inputs, accumulating errors over the batch. Stochastic learning introduces "noise" into the process, using the local gradient calculated from one data point; this reduces the chance of the network getting stuck in local minima. However, batch learning typically yields a faster, more stable descent to a local minimum, since each update is performed in the direction of the batch's average error. A common compromise is to use "mini-batches", small batches with samples in each batch selected stochastically from the entire data set.
Types
ANNs have evolved into a broad family of techniques that have advanced the state of the art across multiple domains. The simplest types have one or more static components, including number of units, number of layers, unit weights and topology. Dynamic types allow one or more of these to evolve via learning. The latter are much more complicated, but can shorten learning periods and produce better results. Some types allow/require learning to be "supervised" by the operator, while others operate independently. Some types operate purely in hardware, while others are purely software and run on general purpose computers.
Some of the main breakthroughs include: convolutional neural networks that have proven particularly successful in processing visual and other two-dimensional data;[135][136] long short-term memory avoid the vanishing gradient problem[137] and can handle signals that have a mix of low and high frequency components aiding large-vocabulary speech recognition,[138][139] text-to-speech synthesis,[140][40][141] and photo-real talking heads;[142] competitive networks such as generative adversarial networks in which multiple networks (of varying structure) compete with each other, on tasks such as winning a game[143] or on deceiving the opponent about the authenticity of an input.[70]
Network design
Neural architecture search (NAS) uses machine learning to automate ANN design. Various approaches to NAS have designed networks that compare well with hand-designed systems. The basic search algorithm is to propose a candidate model, evaluate it against a dataset and use the results as feedback to teach the NAS network.[144] Available systems include AutoML and AutoKeras.[145]
Design issues include deciding the number, type and connectedness of network layers, as well as the size of each and the connection type (full, pooling, ...).
Hyperparameters must also be defined as part of the design (they are not learned), governing matters such as how many neurons are in each layer, learning rate, step, stride, depth, receptive field and padding (for CNNs), etc.[146]
Use
Using artificial neural networks requires an understanding of their characteristics.
- Choice of model: This depends on the data representation and the application. Overly complex models are slow learning.
- Learning algorithm: Numerous trade-offs exist between learning algorithms. Almost any algorithm will work well with the correct hyperparameters[147] for training on a particular data set. However, selecting and tuning an algorithm for training on unseen data requires significant experimentation.
- Robustness: If the model, cost function and learning algorithm are selected appropriately, the resulting ANN can become robust.
ANN capabilities fall within the following broad categories:[148]
- Function approximation,[149] or regression analysis,[150] including time series prediction, fitness approximation[151] and modeling.
- Classification, including pattern and sequence recognition, novelty detection and sequential decision making.[152]
- Data processing,[153] including filtering, clustering, blind source separation[154] and compression.
- Robotics, including directing manipulators and prostheses.
Applications
Because of their ability to reproduce and model nonlinear processes, artificial neural networks have found applications in many disciplines. Application areas include system identification and control (vehicle control, trajectory prediction,[155] process control, natural resource management), quantum chemistry,[156] general game playing,[157] pattern recognition (radar systems, face identification, signal classification,[158] 3D reconstruction,[159] object recognition and more), sensor data analysis,[160] sequence recognition (gesture, speech, handwritten and printed text recognition[161]), medical diagnosis, finance[162] (e.g. ex-ante models for specific financial long-run forecasts and artificial financial markets), data mining, visualization, machine translation, social network filtering[163] and e-mail spam filtering. ANNs have been used to diagnose several types of cancers[164][165] and to distinguish highly invasive cancer cell lines from less invasive lines using only cell shape information.[166][167]
ANNs have been used to accelerate reliability analysis of infrastructures subject to natural disasters[168][169] and to predict foundation settlements.[170] ANNs have also been used for building black-box models in geoscience: hydrology,[171][172] ocean modelling and coastal engineering,[173][174] and geomorphology.[175] ANNs have been employed in cybersecurity, with the objective to discriminate between legitimate activities and malicious ones. For example, machine learning has been used for classifying Android malware,[176] for identifying domains belonging to threat actors and for detecting URLs posing a security risk.[177] Research is underway on ANN systems designed for penetration testing, for detecting botnets,[178] credit cards frauds[179] and network intrusions.
ANNs have been proposed as a tool to solve partial differential equations in physics[180][181][182] and simulate the properties of many-body open quantum systems.[183][184][185][186] In brain research ANNs have studied short-term behavior of individual neurons,[187] the dynamics of neural circuitry arise from interactions between individual neurons and how behavior can arise from abstract neural modules that represent complete subsystems. Studies considered long-and short-term plasticity of neural systems and their relation to learning and memory from the individual neuron to the system level.
Theoretical properties
Computational power
The multilayer perceptron is a universal function approximator, as proven by the universal approximation theorem. However, the proof is not constructive regarding the number of neurons required, the network topology, the weights and the learning parameters.
A specific recurrent architecture with rational-valued weights (as opposed to full precision real number-valued weights) has the power of a universal Turing machine,[188] using a finite number of neurons and standard linear connections. Further, the use of irrational values for weights results in a machine with super-Turing power.[189][190][failed verification]
Capacity
A model's "capacity" property corresponds to its ability to model any given function. It is related to the amount of information that can be stored in the network and to the notion of complexity. Two notions of capacity are known by the community. The information capacity and the VC Dimension. The information capacity of a perceptron is intensively discussed in Sir David MacKay's book[191] which summarizes work by Thomas Cover.[192] The capacity of a network of standard neurons (not convolutional) can be derived by four rules[193] that derive from understanding a neuron as an electrical element. The information capacity captures the functions modelable by the network given any data as input. The second notion, is the VC dimension. VC Dimension uses the principles of measure theory and finds the maximum capacity under the best possible circumstances. This is, given input data in a specific form. As noted in,[191] the VC Dimension for arbitrary inputs is half the information capacity of a Perceptron. The VC Dimension for arbitrary points is sometimes referred to as Memory Capacity.[194]
Convergence
Models may not consistently converge on a single solution, firstly because local minima may exist, depending on the cost function and the model. Secondly, the optimization method used might not guarantee to converge when it begins far from any local minimum. Thirdly, for sufficiently large data or parameters, some methods become impractical.
Another issue worthy to mention is that training may cross some Saddle point which may lead the convergence to the wrong direction.
The convergence behavior of certain types of ANN architectures are more understood than others. When the width of network approaches to infinity, the ANN is well described by its first order Taylor expansion throughout training, and so inherits the convergence behavior of affine models.[195][196] Another example is when parameters are small, it is observed that ANNs often fits target functions from low to high frequencies. This behavior is referred to as the spectral bias, or frequency principle, of neural networks.[197][198][199][200] This phenomenon is the opposite to the behavior of some well studied iterative numerical schemes such as Jacobi method. Deeper neural networks have been observed to be more biased towards low frequency functions.[201]
Generalization and statistics
This section includes a list of references, related reading, or external links, but its sources remain unclear because it lacks inline citations. (August 2019) |
Applications whose goal is to create a system that generalizes well to unseen examples, face the possibility of over-training. This arises in convoluted or over-specified systems when the network capacity significantly exceeds the needed free parameters. Two approaches address over-training. The first is to use cross-validation and similar techniques to check for the presence of over-training and to select hyperparameters to minimize the generalization error.
The second is to use some form of regularization. This concept emerges in a probabilistic (Bayesian) framework, where regularization can be performed by selecting a larger prior probability over simpler models; but also in statistical learning theory, where the goal is to minimize over two quantities: the 'empirical risk' and the 'structural risk', which roughly corresponds to the error over the training set and the predicted error in unseen data due to overfitting.
Supervised neural networks that use a mean squared error (MSE) cost function can use formal statistical methods to determine the confidence of the trained model. The MSE on a validation set can be used as an estimate for variance. This value can then be used to calculate the confidence interval of network output, assuming a normal distribution. A confidence analysis made this way is statistically valid as long as the output probability distribution stays the same and the network is not modified.
By assigning a softmax activation function, a generalization of the logistic function, on the output layer of the neural network (or a softmax component in a component-based network) for categorical target variables, the outputs can be interpreted as posterior probabilities. This is useful in classification as it gives a certainty measure on classifications.
The softmax activation function is:
Criticism
Training
A common criticism of neural networks, particularly in robotics, is that they require too much training for real-world operation.[202] Potential solutions include randomly shuffling training examples, by using a numerical optimization algorithm that does not take too large steps when changing the network connections following an example, grouping examples in so-called mini-batches and/or introducing a recursive least squares algorithm for CMAC.[133]
Theory
A central claim[citation needed] of ANNs is that they embody new and powerful general principles for processing information. These principles are ill-defined. It is often claimed[by whom?] that they are emergent from the network itself. This allows simple statistical association (the basic function of artificial neural networks) to be described as learning or recognition. In 1997, Alexander Dewdney commented that, as a result, artificial neural networks have a "something-for-nothing quality, one that imparts a peculiar aura of laziness and a distinct lack of curiosity about just how good these computing systems are. No human hand (or mind) intervenes; solutions are found as if by magic; and no one, it seems, has learned anything".[203] One response to Dewdney is that neural networks handle many complex and diverse tasks, ranging from autonomously flying aircraft[204] to detecting credit card fraud to mastering the game of Go.
Technology writer Roger Bridgman commented:
Neural networks, for instance, are in the dock not only because they have been hyped to high heaven, (what hasn't?) but also because you could create a successful net without understanding how it worked: the bunch of numbers that captures its behaviour would in all probability be "an opaque, unreadable table...valueless as a scientific resource".
In spite of his emphatic declaration that science is not technology, Dewdney seems here to pillory neural nets as bad science when most of those devising them are just trying to be good engineers. An unreadable table that a useful machine could read would still be well worth having.[205]
Biological brains use both shallow and deep circuits as reported by brain anatomy,[206] displaying a wide variety of invariance. Weng[207] argued that the brain self-wires largely according to signal statistics and therefore, a serial cascade cannot catch all major statistical dependencies.
Hardware
Large and effective neural networks require considerable computing resources.[208] While the brain has hardware tailored to the task of processing signals through a graph of neurons, simulating even a simplified neuron on von Neumann architecture may consume vast amounts of memory and storage. Furthermore, the designer often needs to transmit signals through many of these connections and their associated neurons – which require enormous CPU power and time.
Schmidhuber noted that the resurgence of neural networks in the twenty-first century is largely attributable to advances in hardware: from 1991 to 2015, computing power, especially as delivered by GPGPUs (on GPUs), has increased around a million-fold, making the standard backpropagation algorithm feasible for training networks that are several layers deeper than before.[21] The use of accelerators such as FPGAs and GPUs can reduce training times from months to days.[208]
Neuromorphic engineering or a physical neural network addresses the hardware difficulty directly, by constructing non-von-Neumann chips to directly implement neural networks in circuitry. Another type of chip optimized for neural network processing is called a Tensor Processing Unit, or TPU.[209]
Practical counterexamples
Analyzing what has been learned by an ANN is much easier than analyzing what has been learned by a biological neural network. Furthermore, researchers involved in exploring learning algorithms for neural networks are gradually uncovering general principles that allow a learning machine to be successful. For example, local vs. non-local learning and shallow vs. deep architecture.[210]
Hybrid approaches
Advocates of hybrid models (combining neural networks and symbolic approaches) say that such a mixture can better capture the mechanisms of the human mind.[211]
Gallery
See also
- ADALINE
- Autoencoder
- Bio-inspired computing
- Blue Brain Project
- Catastrophic interference
- Cognitive architecture
- Connectionist expert system
- Connectomics
- Hyperdimensional computing
- Large width limits of neural networks
- List of machine learning concepts
- Neural gas
- Neural network software
- Optical neural network
- Parallel distributed processing
- Philosophy of artificial intelligence
- Recurrent neural networks
- Spiking neural network
- Stochastic parrot
- Tensor product network
Notes
- Steering for the 1995 "No Hands Across America" required "only a few human assists".
References
- Tahmasebi; Hezarkhani (2012). "A hybrid neural networks-fuzzy logic-genetic algorithm for grade estimation". Computers & Geosciences. 42: 18–27. Bibcode:2012CG.....42...18T. doi:10.1016/j.cageo.2012.02.004. PMC 4268588. PMID 25540468.
Bibliography
- Bhadeshia H. K. D. H. (1999). "Neural Networks in Materials Science" (PDF). ISIJ International. 39 (10): 966–979. doi:10.2355/isijinternational.39.966.
- Bishop, Christopher M. (1995). Neural networks for pattern recognition. Clarendon Press. ISBN 978-0-19-853849-3. OCLC 33101074.
- Borgelt, Christian (2003). Neuro-Fuzzy-Systeme : von den Grundlagen künstlicher Neuronaler Netze zur Kopplung mit Fuzzy-Systemen. Vieweg. ISBN 978-3-528-25265-6. OCLC 76538146.
- Cybenko, G.V. (2006). "Approximation by Superpositions of a Sigmoidal function". In van Schuppen, Jan H. (ed.). Mathematics of Control, Signals, and Systems. Springer International. pp. 303–314. PDF
- Dewdney, A. K. (1997). Yes, we have no neutrons : an eye-opening tour through the twists and turns of bad science. New York: Wiley. ISBN 978-0-471-10806-1. OCLC 35558945.
- Duda, Richard O.; Hart, Peter Elliot; Stork, David G. (2001). Pattern classification (2 ed.). Wiley. ISBN 978-0-471-05669-0. OCLC 41347061.
- Egmont-Petersen, M.; de Ridder, D.; Handels, H. (2002). "Image processing with neural networks – a review". Pattern Recognition. 35 (10): 2279–2301. CiteSeerX 10.1.1.21.5444. doi:10.1016/S0031-3203(01)00178-9.
- Fahlman, S.; Lebiere, C (1991). "The Cascade-Correlation Learning Architecture" (PDF). Archived from the original (PDF) on 3 May 2013. Retrieved 28 August 2006.
- created for National Science Foundation, Contract Number EET-8716324, and Defense Advanced Research Projects Agency (DOD), ARPA Order No. 4976 under Contract F33615-87-C-1499.
- Gurney, Kevin (1997). An introduction to neural networks. UCL Press. ISBN 978-1-85728-673-1. OCLC 37875698.
- Haykin, Simon S. (1999). Neural networks : a comprehensive foundation. Prentice Hall. ISBN 978-0-13-273350-2. OCLC 38908586.
- Hertz, J.; Palmer, Richard G.; Krogh, Anders S. (1991). Introduction to the theory of neural computation. Addison-Wesley. ISBN 978-0-201-51560-2. OCLC 21522159.
- Information theory, inference, and learning algorithms. Cambridge University Press. 25 September 2003. Bibcode:2003itil.book.....M. ISBN 978-0-521-64298-9. OCLC 52377690.
- Kruse, Rudolf; Borgelt, Christian; Klawonn, F.; Moewes, Christian; Steinbrecher, Matthias; Held, Pascal (2013). Computational intelligence : a methodological introduction. Springer. ISBN 978-1-4471-5012-1. OCLC 837524179.
- Lawrence, Jeanette (1994). Introduction to neural networks : design, theory and applications. California Scientific Software. ISBN 978-1-883157-00-5. OCLC 32179420.
- MacKay, David, J.C. (2003). Information Theory, Inference, and Learning Algorithms (PDF). Cambridge University Press. ISBN 978-0-521-64298-9.
- Masters, Timothy (1994). Signal and image processing with neural networks : a C++ sourcebook. J. Wiley. ISBN 978-0-471-04963-0. OCLC 29877717.
- Maurer, Harald (2021). Cognitive science : integrative synchronization mechanisms in cognitive neuroarchitectures of the modern connectionism. CRC Press. doi:10.1201/9781351043526. ISBN 978-1-351-04352-6. S2CID 242963768.
- Ripley, Brian D. (2007). Pattern Recognition and Neural Networks. Cambridge University Press. ISBN 978-0-521-71770-0.
- Siegelmann, H.T.; Sontag, Eduardo D. (1994). "Analog computation via neural networks". Theoretical Computer Science. 131 (2): 331–360. doi:10.1016/0304-3975(94)90178-3. S2CID 2456483.
- Smith, Murray (1993). Neural networks for statistical modeling. Van Nostrand Reinhold. ISBN 978-0-442-01310-3. OCLC 27145760.
- Wasserman, Philip D. (1993). Advanced methods in neural computing. Van Nostrand Reinhold. ISBN 978-0-442-00461-3. OCLC 27429729.
- Wilson, Halsey (2018). Artificial intelligence. Grey House Publishing. ISBN 978-1-68217-867-6.
- Computational statistics
- Artificial neural networks
- Classification algorithms
- Computational neuroscience
- Market research
- Mathematical psychology
- Mathematical and quantitative methods (economics)
https://en.wikipedia.org/wiki/Artificial_neural_network
In a telephone network, flood search routing is non-deterministic routing in which a dialed number received at a switch is transmitted to all switches, i.e., flooded, in the area code directly connected to that switch; if the dialed number is not an affiliated subscriber at that switch, the number is then retransmitted to all directly connected switches, and then routed through the switch that has the dialed number corresponding to the particular user end instrument affiliated with it.[1][2] All digits of the numbering plan are used to identify a particular subscriber. Flood search routing allows subscribers to have telephone numbers independent of switch codes. Flood search routing provides the highest probability that a telephone call will go through even though a number of switches and links fail.
Flood search routing is used in military telecommunication systems, such as the mobile subscriber equipment (MSE) system.[3][4]
See also
References
- Hura, Gurdeep S.; Singhal, Mukesh (2001). Data and Computer Communications: Networking and Internetworking (illustrated ed.). CRC. p. 576. ISBN 9781420041316.
![]() This article incorporates public domain material from Federal Standard 1037C. General Services Administration. Archived from the original on 2022-01-22.
This article incorporates public domain material from Federal Standard 1037C. General Services Administration. Archived from the original on 2022-01-22.
https://en.wikipedia.org/wiki/Flood_search_routing

















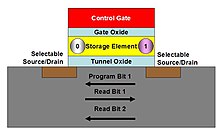

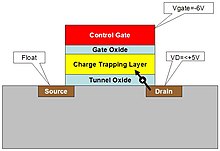
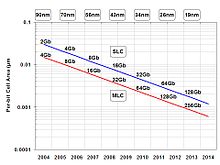
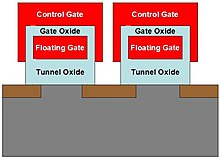






























![{\displaystyle I_{\text{D}}={\frac {\mu _{n}C_{\text{ox}}}{2}}{\frac {W}{L}}\left[V_{\text{GS}}-V_{\text{th}}\right]^{2}\left[1+\lambda (V_{\text{DS}}-V_{\text{DSsat}})\right].}](https://wikimedia.org/api/rest_v1/media/math/render/svg/f6593b8932bc4a92e53bfce27d1c29b1254b0ed3)





















































![\textstyle C=E[(x-f(x))^{2}]](https://wikimedia.org/api/rest_v1/media/math/render/svg/2929ecb1606fdfeaddc55477d9671e11c034e21c)


















No comments:
Post a Comment