Amputation is the removal of a limb by trauma, medical illness, or surgery. As a surgical measure, it is used to control pain or a disease process in the affected limb, such as malignancy or gangrene. In some cases, it is carried out on individuals as a preventive surgery for such problems. A special case is that of congenital amputation, a congenital disorder, where fetal limbs have been cut off by constrictive bands. In some countries, amputation is currently used to punish people who commit crimes.[1][2][3][4] Amputation has also been used as a tactic in war and acts of terrorism; it may also occur as a war injury. In some cultures and religions, minor amputations or mutilations are considered a ritual accomplishment.[5][6][7] When done by a person, the person executing the amputation is an amputator.[8][9] The oldest evidence of this practice comes from a skeleton found buried in Liang Tebo cave, East Kalimantan, Indonesian Borneo dating back to at least 31,000 years ago, where it was done when the amputee was a young child.[10]
https://en.wikipedia.org/wiki/Amputation
An accident is an unintended, normally unwanted event that was not directly caused by humans.[1] The term accident implies that nobody should be blamed, but the event may have been caused by unrecognized or unaddressed risks. Most researchers who study unintentional injury avoid using the term accident and focus on factors that increase risk of severe injury and that reduce injury incidence and severity.[2] For example, when a tree falls down during a wind storm, its fall may not have been caused by humans, but the tree's type, size, health, location, or improper maintenance may have contributed to the result. Most car wrecks are not true accidents; however English speakers started using that word in the mid-20th century as a result of media manipulation by the US automobile industry.[3]
https://en.wikipedia.org/wiki/Accident
https://en.wikipedia.org/w/index.php?search=rebuild+surgery&title=Special%3ASearch&ns0=1
Otofacial syndrome is an extraordinarily rare congenital deformity in which a person is born without a mandible, and, consequently, without a chin.
In nearly all cases, the child does not survive because it is unable to breathe and eat properly. Even with reconstructive surgery, the tongue is extremely underdeveloped, making unaided breathing and swallowing impossible.
https://en.wikipedia.org/wiki/Otofacial_syndrome
https://en.wikipedia.org/w/index.php?title=DNA_surgery&redirect=no
https://en.wikipedia.org/wiki/Cheap_Trick
Aesthetic flat closure after mastectomy is contouring of the chest wall after mastectomy without traditional breast reconstruction.[1] Vernacular synonyms and related vernacular and technical terms include “going flat”,[2] "flat closure",[3] "optimal flat closure",[4] "nonreconstructive mastectomy",[5] “oncoplastic mastectomy”,[6] “non-skin sparing mastectomy”,[7] “mastectomy without reconstruction”,[8] and “aesthetic primary closure post-mastectomy”.[5]
Women who have decided against traditional reconstructive surgery following mastectomy have gained media visibility in recent years.[9] Media reports have covered patients' claims that their choices not to undergo reconstruction have been overridden by their surgeons.[10][11] Recent research has characterized the "going flat" movement and patient experience going flat[12][13][14] and described aesthetic flat closure surgical technique.[15][16][17]
Aesthetic flat closure is the surgical work required to produce a smooth flat chest wall contour after the removal of one or both breasts, including obliteration of the inframammary fold and excision of excess lateral tissue (to avoid "dog ears.")[18][19] It is defined by the National Cancer Institute as the following: “A type of surgery that is done to rebuild the shape of the chest wall after one or both breasts are removed. An aesthetic flat closure may also be done after removal of a breast implant that was used to restore breast shape. During an aesthetic flat closure, extra skin, fat, and other tissue in the breast area are removed. The remaining tissue is then tightened and smoothed out so that the chest wall appears flat.”[20]
https://en.wikipedia.org/wiki/Flat_closure_after_mastectomy
Reconstruction may refer to:
Politics, history, and sociology
- Reconstruction (law), the transfer of a company's (or several companies') business to a new company
- Perestroika (Russian for "reconstruction"), a late 20th century Soviet Union political movement
- Critical reconstruction, an architectural theory related to the reconstruction of Berlin after the end of the Berlin Wall
- Economic reconstruction
- Ministry of Reconstruction, a UK government department
- The Reconstruction era of the United States, the period after the Civil War, 1865–1877
- The Reconstruction Acts, or Military Reconstruction Acts, addressing requirements for Southern States to be readmitted to the Union
- Reconstruction Finance Corporation, a United States government agency from 1932 to 1957
Arts, entertainment, and media
Films
- Reconstruction (1968 film), a Romanian tragicomedy
- Reconstruction (2001 film), about the 1959 Ioanid Gang bank heist in Romania
- Reconstruction (2003 film), a Danish psychological romantic drama
Music
- Reconstruction (band), featuring Jerry Garcia, Nick Kahner and John Kahn
- Reconstruction (Hugh Masekela album), 1970
- Reconstruction (Max Romeo album), 1977
- Reconstructions (Don Diablo album)
- Reconstructions (Kerry Livgren album)
Television
- "Reconstruction" (Jericho episode)
- Red vs. Blue: Reconstruction, a machinima comedy series
Other uses in arts, entertainment, and media
- Reconstruction (magazine), a monthly edited by Allan L. Benson from 1919 to 1921
- ReConStruction, a 2010 science fiction convention
- Memorial reconstruction, a hypothesis regarding the transcription of 17th-century plays
Science and computing
- 3D reconstruction in computer vision
- Ancestral reconstruction, the analysis of organisms' relationships via genome data
- Cone beam reconstruction, a computational microtomography method
- Crime reconstruction
- Event reconstruction, the interpretation of signals from a particle detector
- Forensic facial reconstruction, the process of recreating the face of an individual from its skeletal remains
- Iterative reconstruction, methods to construct images of objects
- Reconstruction algorithm, an algorithm used in iterative reconstruction
- Reconstruction conjecture, in graph theory
- Reconstructive plastic surgery
- Shooting reconstruction
- Signal reconstruction, the determination of an original continuous signal from samples
- Single particle reconstruction, the combination of multiple images of molecules to produce a three-dimensional image
- Surface reconstruction, the process which alters atomic structure in crystal surfaces
- Tomographic reconstruction
- Vector field reconstruction, the creation of a vector field from experimental data
Other uses
- 3D sound reconstruction
- Reconstruction (architecture), the act of rebuilding a destroyed structure
- Linguistic reconstruction
See also
https://en.wikipedia.org/wiki/Reconstruction
| Polydactyly | |
|---|---|
| Other names | Hyperdactyly |
| Specialty | Medical genetics |
| Usual onset | During pregnancy |
| Duration | Lifelong unless surgically removed |
| Treatment | Surgery in some cases |
| Deaths | None |
Polydactyly or polydactylism (from Greek πολύς (polys) 'many', and δάκτυλος (daktylos) 'finger'),[1] also known as hyperdactyly, is an anomaly in humans and animals resulting in supernumerary fingers and/or toes.[2] Polydactyly is the opposite of oligodactyly (fewer fingers or toes).
https://en.wikipedia.org/wiki/Polydactyly
Anorexia is a medical term for a loss of appetite. While the term outside of the scientific literature is often used interchangeably with anorexia nervosa, many possible causes exist for a loss of appetite, some of which may be harmless, while others indicate a serious clinical condition or pose a significant risk.
https://en.wikipedia.org/wiki/Anorexia_(symptom)
https://en.wikipedia.org/wiki/Artificial_organ
Artificial ventilation (also called artificial respiration) is a means of assisting or stimulating respiration, a metabolic process referring to the overall exchange of gases in the body by pulmonary ventilation, external respiration, and internal respiration.[1][2] It may take the form of manually providing air for a person who is not breathing or is not making sufficient respiratory effort,[3] or it may be mechanical ventilation involving the use of a mechanical ventilator to move air in and out of the lungs when an individual is unable to breathe on their own, for example during surgery with general anesthesia or when an individual is in a coma or trauma.
https://en.wikipedia.org/wiki/Artificial_ventilation
Artificial photosynthesis is a chemical process that biomimics the natural process of photosynthesis to convert sunlight, water, and carbon dioxide into carbohydrates and oxygen. The term artificial photosynthesis is commonly used to refer to any scheme for capturing and storing the energy from sunlight in the chemical bonds of a fuel (a solar fuel). Photocatalytic water splitting converts water into hydrogen and oxygen and is a major research topic of artificial photosynthesis. Light-driven carbon dioxide reduction is another process studied that replicates natural carbon fixation.
Research on this topic includes the design and assembly of devices for the direct production of solar fuels, photoelectrochemistry and its application in fuel cells, and the engineering of enzymes and photoautotrophic microorganisms for microbial biofuel and biohydrogen production from sunlight.
https://en.wikipedia.org/wiki/Artificial_photosynthesis
| Part of a series of articles on |
| Synthetic biology |
|---|
| Synthetic biological circuits |
| Genome editing |
| Artificial cells |
| Xenobiology |
| Other topics |
Synthetic biology (SynBio) is a multidisciplinary field of science that focuses on living systems and organisms, and it applies engineering principles to develop new biological parts, devices, and systems or to redesign existing systems found in nature.[1]
It is a branch of science that encompasses a broad range of methodologies from various disciplines, such as biotechnology, biomaterials, material science/engineering, genetic engineering, molecular biology, molecular engineering, systems biology, membrane science, biophysics, chemical and biological engineering, electrical and computer engineering, control engineering and evolutionary biology.
It includes designing and constructing biological modules, biological systems, and biological machines or, re-design of existing biological systems for useful purposes.[2]
Additionally, it is the branch of science that focuses on the new abilities of engineering into existing organisms to redesign them for useful purposes.[3]
In order to produce predictable and robust systems with novel functionalities that do not already exist in nature, it is also necessary to apply the engineering paradigm of systems design to biological systems. According to the European Commission, this possibly involves a molecular assembler based on biomolecular systems such as the ribosome.[4]
https://en.wikipedia.org/wiki/Synthetic_biology
https://en.wikipedia.org/wiki/Timeline_of_biotechnology?wprov=srpw1_5
An artificial cell, synthetic cell or minimal cell is an engineered particle that mimics one or many functions of a biological cell. Often, artificial cells are biological or polymeric membranes which enclose biologically active materials.[1] As such, liposomes, polymersomes, nanoparticles, microcapsules and a number of other particles can qualify as artificial cells.
The terms "artificial cell" and "synthetic cell" are used in a variety of different fields and can have different meanings, as it is also reflected in the different sections of this article. Some stricter definitions are based on the assumption that the term "cell" directly relates to biological cells and that these structures therefore have to be alive (or part of a living organism) and, further, that the term "artificial" implies that these structures are artificially built from the bottom-up, i.e. from basic components. As such, in the area of synthetic biology, an artificial cell can be understood as a completely synthetically made cell that can capture energy, maintain ion gradients, contain macromolecules as well as store information and have the ability to replicate.[2] This kind of artificial cell has not yet been made.
However, in other cases, the term "artificial" does not imply that the entire structure is man-made, but instead, it can refer to the idea that certain functions or structures of biological cells can be modified, simplified, replaced or supplemented with a synthetic entity.
In other fields, the term "artificial cell" can refer to any compartment that somewhat resembles a biological cell in size or structure, but is synthetically made, or even fully made from non-biological components. The term "artificial cell" is also used for structures with direct applications such as compartments for drug delivery. Micro-encapsulation allows for metabolism within the membrane, exchange of small molecules and prevention of passage of large substances across it.[3][4] The main advantages of encapsulation include improved mimicry in the body, increased solubility of the cargo and decreased immune responses. Notably, artificial cells have been clinically successful in hemoperfusion.[5]
https://en.wikipedia.org/wiki/Artificial_cell
Artificial kidney is often a synonym for hemodialysis, but may also refer to the other renal replacement therapies (with exclusion of kidney transplantation) that are in use and/or in development. This article deals mainly with bioengineered kidneys/bioartificial kidneys that are grown from renal cell lines/renal tissue.
The first successful artificial kidney was developed by Willem Kolff in the Netherlands during the early 1940s: Kolff was the first to construct a working dialyzer in 1943.
https://en.wikipedia.org/wiki/Artificial_kidney
An induced coma – also known as a medically induced coma (MIC), barbiturate-induced coma, or drug-induced coma – is a temporary coma (a deep state of unconsciousness) brought on by a controlled dose of an anesthetic drug, often a barbiturate such as pentobarbital or thiopental. Other intravenous anesthetic drugs such as midazolam or propofol may be used.[1][2]
Drug-induced comas are used to protect the brain during major neurosurgery, as a last line of treatment in certain cases of status epilepticus that have not responded to other treatments,[2] and in refractory intracranial hypertension following traumatic brain injury.[1]
Induced coma usually results in significant systemic adverse effects. The patient is likely to completely lose respiratory drive and require mechanical ventilation; gut motility is reduced; hypotension can complicate efforts to maintain cerebral perfusion pressure and often requires the use of vasopressor drugs. Hypokalemia often results. The completely immobile patient is at increased risk of bed sores as well as infection from catheters.[citation needed]
Induced coma is a feature of the Milwaukee protocol, a controversial method that is promoted as a means of treating rabies infection in people.[3][4]
https://en.wikipedia.org/wiki/Induced_coma
Artificial constructs
Scientists have modified strains of viruses in order to study their behavior, as in the case of the H5N1 influenza virus. While funding for such research has aroused controversy at times due to safety concerns, leading to a temporary pause, it has subsequently proceeded.[5][6]
In biotechnology, microbial strains have been constructed to establish metabolic pathways suitable for treating a variety of applications.[7] Historically, a major effort of metabolic research has been devoted to the field of biofuel production.[8] Escherichia coli is most common species for prokaryotic strain engineering. Scientists have succeeded in establishing viable minimal genomes from which new strains can be developed.[9] These minimal strains provide a near guarantee that experiments on genes outside the minimal framework will not be effected by non-essential pathways. Optimized strains of E. coli are typically used for this application. E. coli are also often used as a chassis for the expression of simple proteins. These strains, such as BL21, are genetically modified to minimize protease activity, hence enabling potential for high efficiency industrial scale protein production.[10]
Strains of yeasts are the most common subjects of eukaryotic genetic modification, especially with respect to industrial fermentation.[11]
https://en.wikipedia.org/wiki/Strain_(biology)#Artificial_constructs
Artificial gene synthesis, or simply gene synthesis, refers to a group of methods that are used in synthetic biology to construct and assemble genes from nucleotides de novo. Unlike DNA synthesis in living cells, artificial gene synthesis does not require template DNA, allowing virtually any DNA sequence to be synthesized in the laboratory. It comprises two main steps, the first of which is solid-phase DNA synthesis, sometimes known as DNA printing.[1] This produces oligonucleotide fragments that are generally under 200 base pairs. The second step then involves connecting these oligonucleotide fragments using various DNA assembly methods. Because artificial gene synthesis does not require template DNA, it is theoretically possible to make a completely synthetic DNA molecule with no limits on the nucleotide sequence or size.
Synthesis of the first complete gene, a yeast tRNA, was demonstrated by Har Gobind Khorana and coworkers in 1972.[2] Synthesis of the first peptide- and protein-coding genes was performed in the laboratories of Herbert Boyer and Alexander Markham, respectively.[3][4] More recently, artificial gene synthesis methods have been developed that will allow the assembly of entire chromosomes and genomes. The first synthetic yeast chromosome was synthesised in 2014, and entire functional bacterial chromosomes have also been synthesised.[5] In addition, artificial gene synthesis could in the future make use of novel nucleobase pairs (unnatural base pairs).[6][7][8]
https://en.wikipedia.org/wiki/Artificial_gene_synthesis
Artificial life
The chemoton has laid the foundation of some aspects of artificial life. The computational basis has become a topic of software development and experimentation in the investigation of artificial life.[10] The main reason is that the chemoton simplifies the otherwise complex biochemical and molecular functions of living cells. Since the chemoton is a system consisting of a large but fixed number of interacting molecular species, it can effectively be implemented in a process algebra-based computer language.[11]
https://en.wikipedia.org/wiki/Chemoton#Artificial_life
Hairy root culture, also called transformed root culture, is a type of plant tissue culture that is used to study plant metabolic processes or to produce valuable secondary metabolites or recombinant proteins, often with plant genetic engineering.[1]
A naturally occurring soil bacterium Agrobacterium rhizogenes that contains root-inducing plasmids (also called Ri plasmids) can infect plant roots and cause them to produce a food source for the bacterium, opines, and to grow abnormally.[2] The abnormal roots are particularly easy to culture in artificial media because hormones are not needed in contrast to adventitious roots,[2] and they are neoplastic, with indefinite growth. The neoplastic roots produced by A. rhizogenes infection have a high growth rate (compared to untransformed adventitious roots), as well as genetic and biochemical stability.
Currently the main constraint for commercial utilization of hairy root culture is the development and up-scaling of appropriate (bioreactors) vessels for the delicate and sensitive hairy roots.[2][3][4]
Some of the applied research on utilization of hairy root cultures has been and is conducted at VTT Technical Research Centre of Finland Ltd.[5][6] Other labs working on hairy roots are the phytotechnology lab of Amiens University and the Arkansas Biosciences Institute.
Metabolic studies
Hairy root cultures can be used for phytoremediation, and are particularly valuable for studies of the metabolic processes involved in phytoremediation.[2]
Further applications include detailed studies of fundamental molecular, genetic and biochemical aspects of genetic transformation and of hairy root induction.[7]
Genetically transformed cultures
The Ri plasmids can be engineered to also contain T-DNA, used for genetic transformation (biotransformation) of the plant cells. The resulting genetically transformed root cultures can produce high levels of secondary metabolites, comparable or even higher than those of intact plants.[8]
Use in plant propagation
Hairy root culture can also be used for regeneration of whole plants and for production of artificial seeds.[7]
This section needs expansion. You can help by adding to it. (August 2010) |
See also
- Crown gall, a plant disease with similar uses caused by a related bacterium, Agrobacterium tumefaciens
References
https://en.wikipedia.org/wiki/Hairy_root_culture
https://en.wikipedia.org/wiki/Urine_anion_gap
A powered exoskeleton, also known as power armor, powered armor, powered suit, cybernetic suit, cybernetic armor, exosuit, hardsuit, exoframe or augmented mobility,[1] is a mobile machine that is wearable over all or part of the human body, providing ergonomic structural support and powered by a system of electric motors, pneumatics, levers, hydraulics or a combination of cybernetic technologies, while allowing for sufficient limb movement with increased strength and endurance.[2] The exoskeleton is designed to provide better mechanical load tolerance, and its control system aims to sense and synchronize with the user's intended motion and relay the signal to motors which manage the gears. The exoskeleton also protects the user's shoulder, waist, back and thigh against overload, and stabilizes movements when lifting and holding heavy items.[3]
https://en.wikipedia.org/wiki/Powered_exoskeleton
Artificial cartilage is a synthetic material made of hydrogels[1] or polymers that aims to mimic the functional properties of natural cartilage in the human body. Tissue engineering principles are used in order to create a non-degradable and biocompatible material that can replace cartilage.[2] While creating a useful synthetic cartilage material, certain challenges need to be overcome. First, cartilage is an avascular structure in the body and therefore does not repair itself.[3] This creates issues in regeneration of the tissue. Synthetic cartilage also needs to be stably attached to its underlying surface, bone. Lastly, in the case of creating synthetic cartilage to be used in joint spaces, high mechanical strength under compression needs to be an intrinsic property of the material.[4]
https://en.wikipedia.org/wiki/Artificial_cartilage
https://en.wikipedia.org/wiki/Artificial_ovary
Carbon sequestration (or carbon storage) is the process of storing carbon (in particular atmospheric carbon dioxide) in a carbon pool.[2]: 2248 Carbon sequestration is a naturally occurring process but it can also be enhanced or achieved with technology, for example within carbon capture and storage projects. There are two main types of carbon sequestration: geologic and biologic (also called biosequestration).[3]
Carbon dioxide (CO
2) is naturally captured from the atmosphere through biological, chemical, and physical processes.[4]
These changes can be accelerated through changes in land use and
agricultural practices, such as converting crop land into land for
non-crop fast growing plants.[5] Artificial processes have been devised to produce similar effects,[4] including large-scale, artificial capture and sequestration of industrially produced CO
2 using subsurface saline aquifers or aging oil fields. Other technologies that work with carbon sequestration include bio-energy with carbon capture and storage, biochar, enhanced weathering, direct air carbon capture and sequestration (DACCS).
Forests, kelp beds, and other forms of plant life absorb carbon dioxide from the air as they grow, and bind it into biomass. However, these biological stores are considered volatile carbon sinks as the long-term sequestration cannot be guaranteed. For example, natural events, such as wildfires or disease, economic pressures and changing political priorities can result in the sequestered carbon being released back into the atmosphere.[6] Carbon dioxide that has been removed from the atmosphere can also be stored in the Earth's crust by injecting it into the subsurface, or in the form of insoluble carbonate salts (mineral sequestration). These methods are considered non-volatile because they remove carbon from the atmosphere and sequester it indefinitely and presumably for a considerable duration (thousands to millions of years).
To enhance carbon sequestration processes in oceans the following technologies have been proposed but none have achieved large scale application so far: Seaweed farming, ocean fertilisation, artificial upwelling, basalt storage, mineralization and deep sea sediments, adding bases to neutralize acids. The idea of direct deep-sea carbon dioxide injection has been abandoned.[7]
https://en.wikipedia.org/wiki/Carbon_sequestration
Artificial insemination
Artificial insemination is a mechanism in which spermatozoa are deposited into the reproductive tract of a female.[8] Artificial insemination provides a number of benefits relating to reproduction in the poultry industry. Broiler breeds have been selected specifically for growth, causing them to develop large pectoral muscles, which interfere with and reduce natural mating.[9] The amount of sperm produced and deposited in the hen's reproductive tract may be limited because of this. Additionally, the males' overall sex drive may be significantly reduced due to growth selection.[10] Artificial insemination has allowed many farmers to incorporate selected genes into their stock, increasing their genetic quality.[11]
Abdominal massage is the most common method used for semen collection.[9] During this process, the rooster is restrained and the back region located towards the tail and behind the wings is caressed. This is done gently but quickly. Within a short period of time, the male should get an erection of the phallus. Once this occurs, the cloaca is squeezed and semen is collected from the external papilla of the vas deferens.[12]
During artificial insemination, semen is most frequently deposited intra-vaginally by means of a plastic syringe. In order for semen to be deposited here, the vaginal orifice is everted through the cloaca. This is simply done by applying pressure to the abdomen of the hen. The semen-containing instrument is placed 2–4 cm into the vaginal orifice. As the semen is being deposited, the pressure applied to the hen's abdomen is being released simultaneously.[9] The person performing this procedure typically uses one hand to move and direct the tail feathers, while using the other hand to insert the instrument and semen into the vagina.[12]
https://en.wikipedia.org/wiki/Broiler#Artificial_insemination
https://en.wikipedia.org/wiki/Organ_(biology)
Sterilization may refer to:
- Sterilization (microbiology), killing or inactivation of micro-organisms
- Soil steam sterilization, a farming technique that sterilizes soil with steam in open fields or greenhouses
- Sterilization (medicine) renders a human unable to reproduce
- Neutering is the surgical sterilization of animals
- Irradiation induced sterility is used in the sterile insect technique
- A chemosterilant is a chemical compound that causes sterility
- Sterilization (economics), central bank operations aimed at neutralizing foreign exchange operations' impact on domestic money supply, or offset adverse consequences of large capital flows
See also
Soil steam sterilization (soil steaming) is a farming technique that sterilizes soil with steam in open fields or greenhouses. Pests of plant cultures such as weeds, bacteria, fungi and viruses are killed through induced hot steam which causes vital cellular proteins to unfold. Biologically, the method is considered a partial disinfection. Important heat-resistant, spore-forming bacteria can survive and revitalize the soil after cooling down. Soil fatigue can be cured through the release of nutritive substances blocked within the soil. Steaming leads to a better starting position, quicker growth and strengthened resistance against plant disease and pests. Today, the application of hot steam is considered the best and most effective way to disinfect sick soil, potting soil and compost. It is being used as an alternative to bromomethane, whose production and use was curtailed by the Montreal Protocol. "Steam effectively kills pathogens by heating the soil to levels that cause protein coagulation or enzyme inactivation."[1]
https://en.wikipedia.org/wiki/Soil_steam_sterilization
Apertium is a free/open-source rule-based machine translation platform. It is free software and released under the terms of the GNU General Public License.
https://en.wikipedia.org/wiki/Apertium
Fertilisation or fertilization (see spelling differences), also known as generative fertilisation, syngamy and impregnation,[1] is the fusion of gametes to give rise to a new individual organism or offspring and initiate its development.[2] While processes such as insemination or pollination which happen before the fusion of gametes are also sometimes informally referred to as fertilisation,[3] these are technically separate processes. The cycle of fertilisation and development of new individuals is called sexual reproduction. During double fertilisation in angiosperms the haploid male gamete combines with two haploid polar nuclei to form a triploid primary endosperm nucleus by the process of vegetative fertilisation.
https://en.wikipedia.org/wiki/Fertilisation
Double fertilization is a complex fertilization mechanism of flowering plants (angiosperms). This process involves the joining of a female gametophyte (megagametophyte, also called the embryo sac) with two male gametes (sperm). It begins when a pollen grain adheres to the stigma of the carpel, the female reproductive structure of a flower. The pollen grain then takes in moisture and begins to germinate, forming a pollen tube that extends down toward the ovary through the style. The tip of the pollen tube then enters the ovary and penetrates through the micropyle opening in the ovule. The pollen tube proceeds to release the two sperm in the embryo sac.
The cells of an embryo sac of an unfertilized ovule are 8 in number and arranged in the form of 3+2+3 (from top to bottom) i.e. 3 antipodal cells, 2 polar central cells, 2 synergids & 1 egg cell. One sperm fertilizes the egg cell and the other sperm combines with the two polar nuclei of the large central cell of the megagametophyte. The haploid sperm and haploid egg combine to form a diploid zygote, the process being called syngamy, while the other sperm and the two haploid polar nuclei of the large central cell of the megagametophyte form a triploid nucleus (triple fusion). Some plants may form polyploid nuclei. The large cell of the gametophyte will then develop into the endosperm, a nutrient-rich tissue which provides nourishment to the developing embryo. The ovary, surrounding the ovules, develops into the fruit, which protects the seeds and may function to disperse them.[1]
The two central cell maternal nuclei (polar nuclei) that contribute to the endosperm, arise by mitosis from the same single meiotic product that gave rise to the egg. The maternal contribution to the genetic constitution of the triploid endosperm is double that of the sperm.
In a study conducted in 2008 of the plant Arabidopsis thaliana, the migration of male nuclei inside the female gamete, in fusion with the female nuclei, has been documented for the first time using in vivo imaging. Some of the genes involved in the migration and fusion process have also been determined.[2]
Evidence of double fertilization in Gnetales, which are non-flowering seed plants, has been reported.[3]
https://en.wikipedia.org/wiki/Double_fertilization
Internal fertilization is the union of an egg and sperm cell during sexual reproduction inside the female body. Internal fertilization, unlike its counterpart, external fertilization, brings more control to the female with reproduction.[1] For internal fertilization to happen there needs to be a method for the male to introduce the sperm into the female's reproductive tract.
Most taxa that reproduce by internal fertilization are gonochoric.[2]: 124–125 In mammals, reptiles, and certain other groups of animals, this is done by copulation, an intromittent organ being introduced into the vagina or cloaca.[3][4] In most birds, the cloacal kiss is used, the two animals pressing their cloacas together while transferring sperm.[5] Salamanders, spiders, some insects and some molluscs undertake internal fertilization by transferring a spermatophore, a bundle of sperm, from the male to the female. Following fertilization, the embryos are laid as eggs in oviparous organisms, or continue to develop inside the reproductive tract of the mother to be born later as live young in viviparous organisms.
https://en.wikipedia.org/wiki/Internal_fertilization
| In vitro fertilisation | |
|---|---|
 This image shows intracytoplasmic sperm injection, the most commonly used IVF technique. | |
| Specialty | Reproductive Endocrinology & Infertility |
| ICD-10-PCS | 8E0ZXY1 |
In vitro fertilisation (IVF) is a process of fertilisation where an egg is combined with sperm in vitro ("in glass"). The process involves monitoring and stimulating a woman's ovulatory process, removing an ovum or ova (egg or eggs) from her ovaries and letting sperm fertilise them in a culture medium in a laboratory. After the fertilised egg (zygote) undergoes embryo culture for 2–6 days, it is transferred by catheter into the uterus, with the intention of establishing a successful pregnancy.
IVF is a type of assisted reproductive technology used for infertility treatment, gestational surrogacy, and, in combination with pre-implantation genetic testing, avoiding transmission of genetic conditions. A fertilised egg from a donor may implant into a surrogate's uterus, and the resulting child is genetically unrelated to the surrogate. Some countries have banned or otherwise regulate the availability of IVF treatment, giving rise to fertility tourism. Restrictions on the availability of IVF include costs and age, in order for a woman to carry a healthy pregnancy to term. Children born through IVF are colloquially called test tube babies.
In July 1978, Louise Brown was the first child successfully born after her mother received IVF treatment.[1] Brown was born as a result of natural-cycle IVF, where no stimulation was made. The procedure took place at Dr Kershaw's Cottage Hospital (now Dr Kershaw's Hospice) in Royton, Oldham, England. Robert G. Edwards was awarded the Nobel Prize in Physiology or Medicine in 2010. The physiologist co-developed the treatment together with Patrick Steptoe and embryologist Jean Purdy but the latter two were not eligible for consideration as they had died and the Nobel Prize is not awarded posthumously.[2][3]
With egg donation and IVF, women who are past their reproductive years, have infertile partners, have idiopathic female-fertility issues, or have reached menopause can still become pregnant. After the IVF treatment, some couples get pregnant without any fertility treatments.[4] In 2018, it was estimated that eight million children had been born worldwide using IVF and other assisted reproduction techniques.[5] A 2019 study that explores 10 adjuncts with IVF (screening hysteroscopy, DHEA, testosterone, GH, aspirin, heparin, antioxidants in males and females, seminal plasma and PRP) suggests that until more evidence is done to show that these adjuncts are safe and effective, they should be avoided.[6]
https://en.wikipedia.org/wiki/In_vitro_fertilisation
External fertilization is a mode of reproduction in which a male organism's sperm fertilizes a female organism's egg outside of the female's body.[1] It is contrasted with internal fertilization, in which sperm are introduced via insemination and then combine with an egg inside the body of a female organism.[2] External fertilization typically occurs in water or a moist area to facilitate the movement of sperm to the egg.[3] The release of eggs and sperm into the water is known as spawning.[4] In motile species, spawning females often travel to a suitable location to release their eggs.
However, sessile species are less able to move to spawning locations and must release gametes locally.[4] Among vertebrates, external fertilization is most common in amphibians and fish.[5] Invertebrates utilizing external fertilization are mostly benthic, sessile, or both, including animals such as coral, sea anemones, and tube-dwelling polychaetes.[3] Benthic marine plants also use external fertilization to reproduce.[3] Environmental factors and timing are key challenges to the success of external fertilization. While in the water, the male and female must both release gametes at similar times in order to fertilize the egg.[3] Gametes spawned into the water may also be washed away, eaten, or damaged by external factors.
https://en.wikipedia.org/wiki/External_fertilization
Iron fertilization is the intentional introduction of iron to iron-poor areas of the ocean surface to stimulate phytoplankton production. This is intended to enhance biological productivity and/or accelerate carbon dioxide (CO2) sequestration from the atmosphere. Iron is a trace element necessary for photosynthesis in plants. It is highly insoluble in sea water and in a variety of locations is the limiting nutrient for phytoplankton growth. Large algal blooms can be created by supplying iron to iron-deficient ocean waters. These blooms can nourish other organisms.
Ocean iron fertilization is an example of a geoengineering technique.[1] Iron fertilization[2] attempts to encourage phytoplankton growth, which removes carbon from the atmosphere for at least a period of time.[3][4] This technique is controversial because there is limited understanding of its complete effects on the marine ecosystem,[5] including side effects and possibly large deviations from expected behavior. Such effects potentially include release of nitrogen oxides,[6] and disruption of the ocean's nutrient balance.[1] Controversy remains over the effectiveness of atmospheric CO
2 sequestration and ecological effects.[7]
Since 1990, 13 major large scale experiments have been carried out to
evaluate efficiency and possible consequences of the iron fertilization
in ocean waters. A study in 2017 determined that the method is unproven;
sequestering efficiency is low and sometimes no effect was seen and the
amount of iron deposits that is needed to make a small cut in the
carbon emissions is in the million tons per year.[8]
Approximately 25 per cent of the ocean surface has ample macronutrients, with little plant biomass (as defined by chlorophyll). The production in these high-nutrient low-chlorophyll (HNLC) waters is primarily limited by micronutrients, especially iron.[9] The cost of distributing iron over large ocean areas is large compared with the expected value of carbon credits.[10] Research in the early 2020s suggested that it could only permanently sequester a small amount of carbon.[11]
https://en.wikipedia.org/wiki/Iron_fertilization
Selfing" redirects here. For self-pollination specifically in flowering plants, see Self-pollination.
Autogamy, or self-fertilization, refers to the fusion of two gametes that come from one individual. Autogamy is predominantly observed in the form of self-pollination, a reproductive mechanism employed by many flowering plants. However, species of protists have also been observed using autogamy as a means of reproduction. Flowering plants engage in autogamy regularly, while the protists that engage in autogamy only do so in stressful environments.
https://en.wikipedia.org/wiki/Autogamy
Occurrence
Protists
Paramecium aurelia
Paramecium aurelia is the most commonly studied protozoan for autogamy. Similar to other unicellular organisms, Paramecium aurelia typically reproduce asexually via binary fission or sexually via cross-fertilization. However, studies have shown that when put under nutritional stress, Paramecium aurelia will undergo meiosis and subsequent fusion of gametic-like nuclei.[1] This process, defined as hemixis, a chromosomal rearrangement process, takes place in a number of steps. First, the two micronuclei of P. aurelia enlarge and divide two times to form eight nuclei. Some of these daughter nuclei will continue to divide to create potential future gametic nuclei. Of these potential gametic nuclei, one will divide two more times. Of the four daughter nuclei arising from this step, two of them become anlagen, or cells that will form part of the new organism. The other two daughter nuclei become the gametic micronuclei that will undergo autogamous self-fertilization.[2] These nuclear divisions are observed mainly when the P. aurelia is put under nutritional stress. Research shows that P. aurelia undergo autogamy synchronously with other individuals of the same species.
Clonal aging and rejuvenation
In Paramecium tetraurelia, vitality declines over the course of successive asexual cell divisions by binary fission. Clonal aging is associated with a dramatic increase in DNA damage.[3][4][5] When paramecia that have experienced clonal aging undergo meiosis, either during conjugation or automixis, the old macronucleus disintegrates and a new macronucleus is formed by replication of the micronuclear DNA that had just experienced meiosis followed by syngamy. These paramecia are rejuvenated in the sense of having a restored clonal lifespan. Thus it appears that clonal aging is due in large part to the progressive accumulation of DNA damage, and that rejuvenation is due to repair of DNA damage during meiosis that occurs in the micronucleus during conjugation or automixis and reestablishment of the macronucleus by replication of the newly repaired micronuclear DNA.
Tetrahymena rostrata
Similar to Paramecium aurelia, the parasitic ciliate Tetrahymena rostrata has also been shown to engage in meiosis, autogamy and development of new macronuclei when placed under nutritional stress.[6] Due to the degeneration and remodeling of genetic information that occurs in autogamy, genetic variability arises and possibly increases an offspring's chances of survival in stressful environments.
Allogromia laticollaris
Allogromia laticollaris is perhaps the best-studied foraminiferan amoeboid for autogamy. A. laticollaris can alternate between sexual reproduction via cross-fertilization and asexual reproduction via binary fission. The details of the life cycle of A. laticollaris are unknown, but similar to Paramecium aurelia, A. laticollaris is also shown to sometimes defer to autogamous behavior when placed in nutritional stress. As seen in Paramecium, there is some nuclear dimorphism observed in A. laticollaris. There are often observations of macronuclei and chromosomal fragments coexisting in A. laticollaris. This is indicative of nuclear and chromosomal degeneration, a process similar to the subdivisions observed in P. aurelia. Multiple generations of haploid A. laticollaris individuals can exist before autogamy actually takes place.[7] The autogamous behavior in A. laticollaris has the added consequence of giving rise to daughter cells that are substantially smaller than those rising from binary fission.[8] It is hypothesized that this is a survival mechanism employed when the cell is in stressful environments, and thus not able to allocate all resources to creating offspring. If a cell was under nutritional stress and not able to function regularly, there would be a strong possibility of its offspring's fitness being sub-par.
Self-pollination in flowering plants
About 10–15% of flowering plants are predominantly self-fertilizing.[9] Self-pollination is an example of autogamy that occurs in flowering plants. Self-pollination occurs when the sperm in the pollen from the stamen of a plant goes to the carpels of that same plant and fertilizes the egg cell present. Self-pollination can either be done completely autogamously or geitonogamously. In the former, the egg and sperm cells that unite come from the same flower. In the latter, the sperm and egg cells can come from a different flower on the same plant. While the latter method does blur the lines between autogamous self-fertilization and normal sexual reproduction, it is still considered autogamous self-fertilization.[10]
Self-pollination can lead to inbreeding depression due to expression of deleterious recessive mutations.[11] Meiosis followed by self-pollination results in little genetic variation, raising the question of how meiosis in self-pollinating plants is adaptively maintained over an extended period in preference to a less complicated and less costly asexual ameiotic process for producing progeny. For instance, Arabidopsis thaliana is a predominantly self-pollinating plant that has an outcrossing rate in the wild estimated at less than 0.3%,[12] and self-pollination appears to have evolved roughly a million years ago or more.[13] An adaptive benefit of meiosis that may explain its long-term maintenance in self-pollinating plants is efficient recombinational repair of DNA damage.[14]
Fungi
There are basically two distinct types of sexual reproduction among fungi. The first is outcrossing (in heterothallic fungi). In this case, mating occurs between two different haploid individuals to form a diploid zygote, that can then undergo meiosis. The second type is self-fertilization or selfing (in homothallic fungi). In this case, two haploid nuclei derived from the same individual fuse to form a zygote than can then undergo meiosis. Examples of homothallic fungi that undergo selfing include species with an aspergillus-like asexual stage (anamorphs) occurring in many different genera,[15] several species of the ascomycete genus Cochliobolus,[16] and the ascomycete Pneumocystis jirovecii[17] (for other examples, see Homothallism). A review of evidence on the evolution of sexual reproduction in the fungi led to the concept that the original mode of sexual reproduction in the last eukaryotic common ancestor was homothallic or self-fertile unisexual reproduction.[18]
Advantages of autogamy
There are several advantages for the self-fertilization observed in flowering plants and protists. In flowering plants, it is important for some plants not to be dependent on pollinating agents that other plants rely on for fertilization. This is unusual, however, considering that many plant species have evolved to become incompatible with their own gametes. While these species would not be well served by having autogamous self-fertilization as a reproductive mechanism, other species, which do not have self-incompatibility, would benefit from autogamy. Protists have the advantage of diversifying their modes of reproduction. This is useful for a multitude of reasons. First, if there is an unfavorable change in the environment that puts the ability to deliver offspring at risk, then it is advantageous for an organism to have autogamy at its disposal. In other organisms, it is seen that genetic diversity arising from sexual reproduction is maintained by changes in the environment that favor certain genotypes over others. Aside from extreme circumstances, it is possible that this form of reproduction gives rise to a genotype in the offspring that will increase fitness in the environment. This is due to the nature of the genetic degeneration and remodeling intrinsic to autogamy in unicellular organisms. Thus, autogamous behavior may become advantageous to have if an individual wanted to ensure offspring viability and survival. This advantage also applies to flowering plants. However, it is important to note that this change has not shown to produce a progeny with more fitness in unicellular organisms.[19] It is possible that the nutrition deprived state of the parent cells before autogamy created a barrier for producing offspring that could thrive in those same stressful environments.
Disadvantages of autogamy
In flowering plants, autogamy has the disadvantage of producing low genetic diversity in the species that use it as the predominant mode of reproduction. This leaves those species particularly susceptible to pathogens and viruses that can harm it. In addition, the foraminiferans that use autogamy have shown to produce substantially smaller progeny as a result.[20] This indicates that since it is generally an emergency survival mechanism for unicellular species, the mechanism does not have the nutritional resources that would be provided by the organism if it were undergoing binary fission.
Genetic consequences of self-fertilization
Self-fertilization results in the loss of genetic variation within an individual (offspring), because many of the genetic loci that were heterozygous become homozygous. This can result in the expression of harmful recessive alleles, which can have serious consequences for the individual. The effects are most extreme when self-fertilization occurs in organisms that are usually out-crossing.[21] In plants, selfing can occur as autogamous or geitonogamous pollinations and can have varying fitness affects that show up as autogamy depression. After several generations, inbreeding depression is likely to purge the deleterious alleles from the population because the individuals carrying them have mostly died or failed to reproduce.
If no other effects interfere, the proportion of heterozygous loci is halved in each successive generation, as shown in the following table.
- Parental : x (100%), and in
- 1 generation gives: : : , which means that the frequency of heterozygotes now is 50% of the starting value.
- By the 10 generation, heterozygotes have almost completely disappeared, and the population is polarized, with almost exclusively homozygous individuals ( and )
Illustration model of the decrease in genetic variation in a population of self-fertilized organisms derived from a heterozygous individual, assuming equal fitness
| Generation | AA (%) |
Aa (%) |
aa (%) |
| P | – | 100 | – |
| F1 | 25 | 50 | 25 |
| F2 | 37.5 | 25 | 37.5 |
| F3 | 43.75 | 12.5 | 43.75 |
| F4 | 46.875 | 6.25 | 46.875 |
| F5 | 48.4375 | 3.125 | 48.4375 |
| F6 | 49.21875 | 1.5625 | 49.21875 |
| F7 | 49.609375 | 0.78125 | 49.609375 |
| F8 | 49.8046875 | 0.390625 | 49.8046875 |
| F9 | 49.90234375 | 0.1953125 | 49.90234375 |
| F10 | 49.995117187 ≈ 50.0 | 0.09765626 ≈ 0.0 | 49.995117187 ≈ 50.0 |
Evolution of autogamy
The evolutionary shift from outcrossing to self-fertilization is one of the most frequent evolutionary transitions in plants. Since autogamy in flowering plants and autogamy in unicellular species is fundamentally different, and plants and protists are not related, it is likely that both instances evolved separately. However, due to the little overall genetic variation that arises in progeny, it is not fully understood how autogamy has been maintained in the tree of life.
See also
- Effective selfing model
- Parthenogenesis
- Inbreeding
- Outcrossing
- Inbreeding depression
- Outbreeding depression
- Sequential hermaphroditism; the organism spends part of its life as a female and part as a male; self-fertilization is not possible.
References
- Bernstein H, Byerly HC, Hopf FA, Michod RE (September 1985). "Genetic damage, mutation, and the evolution of sex". Science. 229 (4719): 1277–81. Bibcode:1985Sci...229.1277B. doi:10.1126/science.3898363. PMID 3898363.
https://en.wikipedia.org/wiki/Autogamy
Reconstructive surgery is surgery performed to restore normal appearance and function to body parts malformed by a disease or medical condition.
https://en.wikipedia.org/wiki/Reconstructive_surgery
The Reconstruction era was a period in American history following the American Civil War (1861–1865) and lasting until approximately the Compromise of 1877. During Reconstruction, attempts were made to rebuild the country after the bloody Civil War, bring the former Confederate states back into the United States, and to counteract the political, social, and economic legacies of slavery.
During the era, Congress abolished slavery, ended the remnants of Confederate secession in the South, and passed the 13th, 14th, and 15th Amendments to the Constitution (the Reconstruction Amendments) ostensibly guaranteeing the newly freed slaves (freedmen) the same civil rights as those of whites. Following a year of violent attacks against Blacks in the South, in 1866 Congress federalized the protection of civil rights, and placed formerly secessionist states under the control of the U.S. military, requiring ex-Confederate states to adopt guarantees for the civil rights of freedmen before they could be readmitted to the Union. In nearly all ex-Confederate states, Republican coalitions set out to transform Southern society. The Freedmen's Bureau and the U.S. Army both aimed to implement a post-slavery free labor economy, protect the legal rights of freedmen, negotiate labor contracts, and helped establish networks of schools and churches. Thousands of Northerners ("Carpetbaggers") came to the South to serve in the social and economic programs of Reconstruction. White Southerners who supported Reconstruction policies and efforts were known as "Scalawags".
Fighting against suffrage and full rights for freedmen, and in favor of giving the returning Southern states relatively free rein over former slaves, were the white "Redeemers"; Southern Bourbon Democrats;[2] Vice President Andrew Johnson, a Southerner who assumed the presidency after the assassination of President Abraham Lincoln; and especially the Ku Klux Klan, which intimidated, terrorized, and murdered freedmen and Republicans, including Arkansas Congressman James M. Hinds, throughout the former Confederacy.
Republican President Ulysses S. Grant (1869–1877) succeeded Johnson and supported congressional Reconstruction and the protection of African Americans in the South, but eventually support for Reconstruction declined in the North with "Liberal Republicans" joining Democrats in calling for a withdrawal of the Army from the South. In 1877, as part of a congressional compromise to elect a Republican as president after a disputed election, federal troops were withdrawn from the three Southern states where they remained.
Among the many "shortcomings and failures" of Reconstruction were the failure to protect freed blacks from Ku Klux Klan violence prior to 1871, starvation, disease and death, brutal treatment of Union soldiers, and the offering of reparations to former slaveowners but not to former slaves.[3] However, Reconstruction did succeed in restoring the federal Union, limiting reprisals against the South directly after the war, establishing the constitutional rights to national birthright citizenship, due process, equal protection of the laws, and male suffrage regardless of race, and a framework for eventual legal equality for black people.[4]
https://en.wikipedia.org/wiki/Reconstruction_era
Reconstructive memory is a theory of memory recall, in which the act of remembering is influenced by various other cognitive processes including perception, imagination, motivation, semantic memory and beliefs, amongst others. People view their memories as being a coherent and truthful account of episodic memory and believe that their perspective is free from an error during recall. However, the reconstructive process of memory recall is subject to distortion by other intervening cognitive functions such as individual perceptions, social influences, and world knowledge, all of which can lead to errors during reconstruction.
Reconstructive process
Memory rarely relies on a literal recount of past experiences. By using multiple interdependent cognitive processes, there is never a single location in the brain where a given complete memory trace of experience is stored.[1] Rather, memory is dependent on constructive processes during encoding that may introduce errors or distortions. Essentially, the constructive memory process functions by encoding the patterns of perceived physical characteristics, as well as the interpretive conceptual and semantic functions that act in response to the incoming information.[2]
In this manner, the various features of the experience must be joined together to form a coherent representation of the episode.[3] If this binding process fails, it can result in memory errors. The complexity required for reconstructing some episodes is quite demanding and can result in incorrect or incomplete recall.[4] This complexity leaves individuals susceptible to phenomena such as the misinformation effect across subsequent recollections.[5] By employing reconstructive processes, individuals supplement other aspects of available personal knowledge and schema into the gaps found in episodic memory in order to provide a fuller and more coherent version, albeit one that is often distorted.[6]
Many errors can occur when attempting to retrieve a specific episode. First, the retrieval cues used to initiate the search for a specific episode may be too similar to other experiential memories and the retrieval process may fail if the individual is unable to form a specific description of the unique characteristics of the given memory they would like to retrieve.[7] When there is little available distinctive information for a given episode there will be more overlap across multiple episodes, leading the individual to recall only the general similarities common to these memories. Ultimately proper recall for a desired target memory fails due to the interference of non-target memories that are activated because of their similarity.[3]
Secondly, a large number of errors that occur during memory reconstruction are caused by faults in the criterion-setting and decision making processes used to direct attention towards retrieving a specific target memory. When there are lapses in the recall of aspects of episodic memory, the individual tends to supplement other aspects of knowledge that are unrelated to the actual episode to form a more cohesive and well-rounded reconstruction of the memory, regardless of whether or not the individual is aware of such supplemental processing. This process is known as confabulation. All of the supplemental processes occurring during the course of reconstruction rely on the use of schema, information networks that organize and store abstract knowledge in the brain.
Characteristics
Schema
Schema are generally defined as mental information networks that represent some aspect of collected world knowledge. Frederic Bartlett was one of the first psychologists to propose Schematic theory, suggesting that the individual's understanding of the world is influenced by elaborate neural networks that organize abstract information and concepts.[8] Schema are fairly consistent and become strongly internalized in the individual through socialization, which in turn alters the recall of episodic memory. Schema is understood to be central to reconstruction, used to confabulate, and fill in gaps to provide a plausible narrative. Bartlett also showed that schema can be tied to cultural and social norms.[9]
Jean Piaget's theory of schema
Piaget's theory proposed an alternative understanding of schema based on the two concepts: assimilation and accommodation. Piaget defined assimilation as the process of making sense of the novel and unfamiliar information by using previously learned information. To assimilate, Piaget defined a second cognitive process that served to integrate new information into memory by altering preexisting schematic networks to fit novel concepts, what he referred to as accommodation.[10] For Piaget, these two processes, accommodation, and assimilation, are mutually reliant on one another and are vital requirements for people to form basic conceptual networks around world knowledge and to add onto these structures by utilizing preexisting learning to understand new information, respectively.
According to Piaget, schematic knowledge organizes features information in such a way that more similar features are grouped so that when activated during recall the more strongly related aspects of memory will be more likely to activate together. An extension of this theory, Piaget proposed that the schematic frameworks that are more frequently activated will become more strongly consolidated and thus quicker and more efficient to activate later.[11]
Frederic Bartlett's experiments
Frederic Bartlett originally tested his idea of the reconstructive nature of recall by presenting a group of participants with foreign folk tales (his most famous being "War of the Ghosts"[12]) with which they had no previous experience. After presenting the story, he tested their ability to recall and summarize the stories at various points after the presentation to newer generations of participants. His findings showed that the participants could provide a simple summary but had difficulty recalling the story accurately, with the participants' own account generally being shorter and manipulated in such a way that aspects of the original story that were unfamiliar or conflicting to the participants' own schematic knowledge were removed or altered in a way to fit into more personally relevant versions.[8] For instance, allusions made to magic and Native American mysticism that were in the original version were omitted as they failed to fit into the average Westerner schematic network. Besides, after several recounts of the story had been made by successive generations of participants, certain aspects of the recalled tale were embellished so they were more consistent with the participants' cultural and historical viewpoint compared to the original text (e.g. Emphasis placed on one of the characters desire to return to care for his dependent elderly mother). These findings lead Bartlett to conclude that recall is predominately a reconstructive rather than reproductive process.[9]
James J. Gibson built off of the work that Bartlett originally laid down, suggesting that the degree of change found in a reproduction of an episodic memory depends on how that memory is later perceived.[13] This concept was later tested by Carmichael, Hogan, and Walter (1932) who exposed a group of participants to a series of simple figures and provided different words to describe each images. For example, all participants were exposed to an image of two circles attached by a single line, where some of the participants were told it was a barbell and the rest were told it was a pair of reading glasses. The experiment revealed that when the participants were later tasked with replicating the images, they tended to add features to their own reproduction that more closely resembled the word they were primed with.
Confirmation bias
During retrieval of episodic memories, people use their schematic knowledge to fill in information gaps, though they generally do so in a manner that implements aspects of their own beliefs, moral values, and personal perspective that leads the reproduced memory to be a biased interpretation of the original version. Confirmation bias results in overconfidence in personal perception and usually leads to a strengthening of beliefs, often in the face of contradictory dis-confirming evidence.[14]
Associated neural activity
Recent research using neuro-imaging technology including PET and fMRI scanning has shown that there is an extensive amount of distributed brain activation during the process of episodic encoding and retrieval. Among the various regions, the two most active areas during the constructive processes are the medial temporal lobe (including the hippocampus) and the prefrontal cortex.[15] The Medial Temporal lobe is especially vital for encoding novel events in episodic networks, with the Hippocampus acting as one of the central locations that acts to both combine and later separate the various features of an event.[16][17] Most popular research holds that the Hippocampus becomes less important in long term memory functioning after more extensive consolidation of the distinct features present at the time of episode encoding has occurred. In this way long term episodic functioning moves away from the CA3 region of the Hippocampal formation into the neocortex, effectively freeing up the CA3 area for more initial processing.[17] Studies have also consistently linked the activity of the Prefrontal Cortex, especially that which occurs in the right hemisphere, to the process of retrieval.[18] The Prefrontal cortex appears to be utilized for executive functioning primarily for directing the focus of attention during retrieval processing, as well as for setting the appropriate criterion required to find the desired target memory.[15]
Applications
Eyewitness testimony
Eyewitness testimony is a commonly recurring topic in the discussion of reconstructive memory and its accuracy is the subject of many studies. Eyewitness testimony is any firsthand accounts given by individuals of an event they have witnessed. Eyewitness testimony is used to acquire details about the event and even to identify the perpetrators of the event.[19] Eyewitness testimony is used often in court and is viewed favorably by juries as a reliable source of information.[19] Unfortunately, eyewitness testimony can be easily manipulated by a variety of factors such as:
- Anxiety and stress
- Schema
- The cross-race effect
Anxiety and stress
Anxiety is a state of distress or uneasiness of mind caused by fear[20] and it is a consistently associated with witnessing crimes. In a study done by Yuille and Cutshall (1986), they discovered that witnesses of real-life violent crimes were able to remember the event quite vividly even five months after it originally occurred.[19] In fact, witnesses to violent or traumatic crimes often self-report the memory as being particularly vivid. For this reason, eyewitness memory is often listed as an example of flashbulb memory.
However, in a study by Clifford and Scott (1978), participants were shown either a film of a violent crime or a film of a non-violent crime. The participants who viewed the stressful film had difficulty remembering details about the event compared to the participants that watched the non-violent film.[19] In a study by Brigham et al. (2010), subjects who experienced an electrical shock were less accurate in facial recognition tests, suggesting that some details were not well remembered under stressful situations.[21] In fact, in the case of the phenomena known as weapon focus, eyewitnesses to stressful crimes involving weapons may perform worse during suspect identification.[22]
Further studies on flashbulb memories seem to indicate that witnesses may recall vivid sensory content unrelated to the actual event but which enhance its perceived vividness.[23] Due to this vividness, eyewitnesses may place higher confidence in their reconstructed memories.[24]
Application of schema
The use of schemas has been shown to increase the accuracy of recall of schema-consistent information but this comes at the cost of decreased recall of schema-inconsistent information. A study by Tuckey and Brewer[25] found that after 12 weeks, memories of information inconsistent with a schema-typical robbery decays much faster than those that are schema-consistent. These were memories such as the method of getaway, demands by the robbers, and the robbers' physical appearance. The study also found that information that was schema-inconsistent but stood out as very abnormal for the participants was usually recalled more readily and was retained for the duration of the study. The authors of the study advise that interviewers of eyewitnesses should take note of such reports because there is a possibility that they may be accurate.
Cross-race effect
Reconstructing the face of another race requires the use of schemas that may not be as developed and refined as those of the same race.[26] The cross-race effect is the tendency that people have to distinguish among other of their race than of other races. Although the exact cause of the effect is unknown, two main theories are supported. The perceptual expertise hypothesis postulates that because most people are raised and are more likely to associate with others of the same race, they develop an expertise in identifying the faces of that race. The other main theory is the in-group advantage. It has been shown in the lab that people are better at discriminating the emotions of in-group members than those of out-groups.[27]
Leading questions
Often during eyewitness testimonies, the witness is interrogated about their particular view of an incident and often the interrogator will use leading questions to direct and control the type of response that is elicited by the witness.[28] This phenomenon occurs when the response a person gives can be persuaded by the way a question is worded. For example, a person could be posed a question in two different forms:
- "What was the approximate height of the robber?" which would lead the respondent to estimate the height according to their original perceptions. They could alternatively be asked:
- "How short was the robber?" which would persuade the respondent to recall that the robber was actually shorter than they had originally perceived.
Using this method of controlled interrogation, the direction of a witness cross-examination can often be controlled and manipulated by the individual who is posing questions to fit their own needs and intentions.
Retrieval cues
After the information is encoded and stored in our memory, specific cues are often needed to retrieve these memories. These are known as retrieval cues[citation needed] and they play a major role in reconstructive memory. The use of retrieval cues can both promote the accuracy of reconstructive memory as well as detract from it. The most common aspect of retrieval cues associated with reconstructive memory is the process that involves recollection. This process uses logical structures, partial memories, narratives, or clues to retrieve the desired memory.[29] However, the process of recollection is not always successful due to cue-dependent forgetting and priming.
Cue-dependent forgetting
Cue-dependent forgetting (also known as retrieval failure) occurs when memories are not obtainable because the appropriate cues are absent.[30] This is associated with a relatively common occurrence known as the tip of the tongue (TOT) phenomenon, originally developed by the psychologist William James. Tip of the tongue phenomenon refers to when an individual knows particular information, and they are aware that they know this information, yet can not produce it even though they may know certain aspects about the information.[31] For example, during an exam a student is asked who theorized the concept of Psychosexual Development, the student may be able to recall the details about the actual theory but they are unable to retrieve the memory associated with who originally introduced the theory.
Priming
Priming refers to an increased sensitivity to certain stimuli due to prior experience.[32] Priming is believed to occur outside of conscious awareness, which makes it different from memory that relies on the direct retrieval of information.[33] Priming can influence reconstructive memory because it can interfere with retrieval cues. Psychologist Elizabeth Loftus presented many papers concerning the effects of proactive interference on the recall of eyewitness events. Interference involving priming was established in her classic study with John Palmer in 1974.[34] Loftus and Palmer recruited 150 participants and showed each of them a film of a traffic accident. After, they had the participants fill out a questionnaire concerning the video's details. The participants were split into three groups:
- Group A contained 50 participants that were asked: "About how fast were the cars going when they hit each other?”
- Group B contained 50 participants that were asked: "About how fast were the cars going when they smashed each other?"
- Group C contained 50 participants and were not asked this question because they were meant to represent a control group
A week later, all of the participants were asked whether or not there had been any broken glass in the video. A statistically significant number of participants in the group B answered that they remembered seeing broken glass in the video (p < -.05). However, there was not any broken glass in the video. The difference between this group and the others was that they were primed with the word “smashed” in the questionnaire, one week before answering the question. By changing one word in the questionnaire, their memories were re-encoded with new details.[35]
Reconstructive errors
Confabulation
Confabulation is the involuntary false remembering of events and can be a characteristic of several psychological diseases such as Korsakoff's syndrome, Alzheimer's disease, schizophrenia and traumatic injury of certain brain structures.[36] Those confabulating don't know that what they are remembering is false and have no intent to deceive.[37]
In the regular process of reconstruction, several sources are used to accrue information and add detail to memory. For patients producing confabulations, some key sources of information are missing and so other sources are used to produce a cohesive, internally consistent, and often believable false memory.[38] The source and type of confabulations differ for each type of disease or area of traumatic damage.
Selective memory
Selective memory involves actively forgetting negative experiences or enhancing positive ones.[39] This process actively affects reconstructive memory by distorting recollections of events. This affects reconstructive memories in two ways:
- by preventing memories from being recalled, even when appropriate cues are present
- by enhancing one's own role in previous experiences, also known as motivated self-enhancement
Many autobiographies are excellent examples of motivated self-enhancement because when recalling the events that have taken place in one's life, there is a tendency to make oneself appear to be more involved in positive experiences, though others may remember the event differently.
See also
References
- Waulhauser, G. (2011, July 11). Selective memory does exist. The Telegraph.
https://en.wikipedia.org/wiki/Reconstructive_memory
A belief is a subjective attitude that a proposition is true or a state of affairs is the case. A subjective attitude is a mental state of having some stance, take, or opinion about something.[1] In epistemology, philosophers use the term "belief" to refer to attitudes about the world which can be either true or false.[2] To believe something is to take it to be true; for instance, to believe that snow is white is comparable to accepting the truth of the proposition "snow is white". However, holding a belief does not require active introspection. For example, few carefully consider whether or not the sun will rise tomorrow, simply assuming that it will. Moreover, beliefs need not be occurrent (e.g. a person actively thinking "snow is white"), but can instead be dispositional (e.g. a person who if asked about the color of snow would assert "snow is white").[2]
https://en.wikipedia.org/wiki/Belief
Compulsory sterilization, also known as forced or coerced sterilization, is a government-mandated program to involuntarily sterilize a specific group of people. Sterilization removes a person's capacity to reproduce, and is usually done through surgical procedures. Several countries implemented sterilization programs in the early 20th century.[1] Although such programs have been made illegal in most countries of the world, instances of forced or coerced sterilizations persist.
Rationalizations for compulsory sterilization have included eugenics, population control, gender discrimination, limiting the spread of HIV,[2] "gender-normalizing" surgeries for intersex people, and ethnic genocide. In some countries, transgender individuals are required to undergo sterilization before gaining legal recognition of their gender, a practice that the United Nations Special Rapporteur on torture and other cruel, inhuman or degrading treatment or punishment has described as a violation of the Yogyakarta Principles.[3]
https://en.wikipedia.org/wiki/Compulsory_sterilization
Sterilization law is the area of law, within reproductive rights, that gives a person the right to choose or refuse reproductive sterilization and governs when the government may limit this fundamental right. Sterilization law includes federal and state constitutional law, statutory law, administrative law, and common law. This article primarily focuses on laws concerning compulsory sterilization that have not been repealed or abrogated and are still good laws, in whole or in part, in each jurisdiction.
https://en.wikipedia.org/wiki/Sterilization_law_in_the_United_States
Breed-specific legislation (BSL) is a type of law that prohibits or restricts particular breeds or types of dog.[1] Such laws range from outright bans on the possession of these dogs, to restrictions and conditions on ownership, and often establishes a legal presumption that such dogs are dangerous or vicious to prevent dog attacks. Some jurisdictions have enacted breed-specific legislation in response to a number of fatalities or maulings involving pit bull–type dogs or other dog breeds commonly used in dog fighting, and some government organizations such as the United States Army[2][3] and Marine Corps[4] have taken administrative action as well. Due to opposition to such laws, anti-BSL laws have been passed in 21 of the 50 state-level governments in the United States, prohibiting or restricting the ability of jurisdictions within those states to enact or enforce breed-specific legislation.[5]
https://en.wikipedia.org/wiki/Breed-specific_legislation
Compulsory sterilisation in Sweden were sterilisations which were carried out in Sweden, without a valid consent of the subject, during the years 1906–1975 on eugenic, medical and social grounds. Between 1972 and 2013, sterilisation was also a condition for gender reassignment surgery.
https://en.wikipedia.org/wiki/Compulsory_sterilisation_in_Sweden
The State Institute for Racial Biology (SIRB, Swedish: Statens institut för rasbiologi, SIFR) was a Swedish governmental research institute founded in 1922 with the stated purpose of studying eugenics and human genetics. It was the most prominent institution for the study of "racial science" in Sweden.[1] It was located in Uppsala. In 1958, it was renamed to the State Institute for Human Genetics[2] (Institutionen för medicinisk genetik) and is today incorporated as a department of Uppsala University.
https://en.wikipedia.org/wiki/State_Institute_for_Racial_Biology
Prohibition of forced sterilization and forced abortion
The Istanbul convention, the first legally binding instrument in Europe in the field of violence against women and domestic violence,[30] prohibits forced sterilization and forced abortion:[31]
Article 39 – Forced abortion and forced sterilisation
- Parties shall take the necessary legislative or other measures to ensure that the following intentional conducts are criminalised:
- a performing an abortion on a woman without her prior and informed consent;
- b performing surgery which has the purpose or effect of terminating a woman’s capacity to naturally reproduce without her prior and informed consent or understanding of the procedure
https://en.wikipedia.org/wiki/Reproductive_rights#Prohibition_of_forced_sterilization_and_forced_abortion
https://en.wikipedia.org/wiki/International_human_rights_instruments
https://en.wikipedia.org/wiki/United_States
This page is a list of the episodes of The Outer Limits, a 1995 science fiction/dark fantasy television series. The series was broadcast on Showtime from 1995 to 2000, and on the Sci Fi channel in its final year (2001–2002).
https://en.wikipedia.org/wiki/List_of_The_Outer_Limits_(1995_TV_series)_episodes#ep146
Cleaning, Disinfection, Sterilization
The field of infection prevention describes a hierarchy of removal of microorganisms from surfaces including medical equipment and instruments. Cleaning is the lowest level, accomplishing substantial removal. Disinfection involves the removal of all pathogens other than bacterial spores. Sterilization is defined as the removal or destruction of ALL microorganisms including bacterial spores.[citation needed]
Cleaning
Cleaning is the first and simplest step in preventing the spread of infection via surfaces and fomites. Cleaning reduces microbial burden by chemical deadsorption of organisms (loosening bioburden/organisms from surfaces via cleaning chemicals), simple mechanical removal (rinsing, wiping), as well as disinfection (killing of organisms by cleaning chemicals).[citation needed]
In order to reduce their chances to contract an infection, individuals are recommended to maintain a good hygiene by washing their hands after every contact with questionable areas or bodily fluids and by disposing of garbage at regular intervals to prevent germs from growing.[13]
Disinfection
Disinfection uses liquid chemicals on surfaces and at room temperature to kill disease causing microorganisms. Ultraviolet light has also been used to disinfect the rooms of patients infected with Clostridium difficile after discharge.[14] Disinfection is less effective than sterilization because it does not kill bacterial endospores.[15]
Along with ensuring proper hand washing techniques are followed, another major component to decrease the spread of disease is sanitation of all medical equipment. The ANA and AANA set guidelines for sterilization and disinfection based on the Spaulding Disinfection and Sterilization Classification Scheme (SDSCS). The SDSCS classifies sterilization techniques into three categories: critical, semi-critical, and non-critical.[3] For critical situations, or situations involving contact with sterile tissue or the vascular system, sterilize devices with sterilants that destroy all bacteria, rinse with sterile water, and use chemical germicides.[5][3] In semi-critical situations, or situations with contact of mucous membranes or non-intact skin, high-level disinfectants are required. Cleaning and disinfecting devices with high-level disinfectants, rinsing with sterile water, and drying all equipment surfaces to prevent microorganism growth are methods nurses and doctors must follow. For non-critical situations, or situations involving electronic devices, stethoscopes, blood pressure cuffs, beds, monitors and other general hospital equipment, intermediate level disinfection is required. "Clean all equipment between patients with alcohol, use protective covering for non-critical surfaces that are difficult to clean, and hydrogen peroxide gas. . .for reusable items that are difficult to clean."[3]
Sterilization
Sterilization is a process intended to kill all microorganisms and is the highest level of microbial kill that is possible.[citation needed]
Sterilization, if performed properly, is an effective way of preventing Infections from spreading. It should be used for the cleaning of medical instruments and any type of medical item that comes into contact with the blood stream and sterile tissues.[citation needed]
There are four main ways in which such items are usually sterilized: autoclave (by using high-pressure steam), dry heat (in an oven), by using chemical sterilants such as glutaraldehydes or formaldehyde solutions or by exposure to ionizing radiation. The first two are the most widely used methods of sterilization mainly because of their accessibility and availability. Steam sterilization is one of the most effective types of sterilizations, if done correctly which is often hard to achieve. Instruments that are used in health care facilities are usually sterilized with this method. The general rule in this case is that in order to perform an effective sterilization, the steam must get into contact with all the surfaces that are meant to be disinfected. On the other hand, dry heat sterilization, which is performed with the help of an oven, is also an accessible type of sterilization, although it can only be used to disinfect instruments that are made of metal or glass. The very high temperatures needed to perform sterilization in this way are able to melt the instruments that are not made of glass or metal.[citation needed]
Effectiveness of the sterilizer, for example a steam autoclave is determined in three ways.[15] First, mechanical indicators and gauges on the machine itself indicate proper operation of the machine. Second heat sensitive indicators or tape on the sterilizing bags change color which indicate proper levels of heat or steam. And, third (most importantly) is biological testing in which a microorganism that is highly heat and chemical resistant (often the bacterial endospore) is selected as the standard challenge. If the process kills this microorganism, the sterilizer is considered to be effective.[15]
Steam sterilization is done at a temperature of 121 C (250 F) with a pressure of 209 kPa (~2atm). In these conditions, rubber items must be sterilized for 20 minutes, and wrapped items 134 C with pressure of 310 kPa for 7 minutes. The time is counted once the temperature that is needed has been reached. Steam sterilization requires four conditions in order to be efficient: adequate contact, sufficiently high temperature, correct time and sufficient moisture.[16] Sterilization using steam can also be done at a temperature of 132 C (270 F), at a double pressure.[citation needed]
Dry heat sterilization is performed at 170 C (340 F) for one hour or two hours at a temperature of 160 C (320 F). Dry heat sterilization can also be performed at 121 C, for at least 16 hours.[17]
Chemical sterilization, also referred to as cold sterilization, can be used to sterilize instruments that cannot normally be disinfected through the other two processes described above. The items sterilized with cold sterilization are usually those that can be damaged by regular sterilization. A variety of chemicals can be used including aldehydes, hydrogen peroxide, and peroxyacetic acid. Commonly, glutaraldehydes and formaldehyde are used in this process, but in different ways. When using the first type of disinfectant, the instruments are soaked in a 2–4% solution for at least 10 hours while a solution of 8% formaldehyde will sterilize the items in 24 hours or more. Chemical sterilization is generally more expensive than steam sterilization and therefore it is used for instruments that cannot be disinfected otherwise. After the instruments have been soaked in the chemical solutions, they must be rinsed with sterile water which will remove the residues from the disinfectants. This is the reason why needles and syringes are not sterilized in this way, as the residues left by the chemical solution that has been used to disinfect them cannot be washed off with water and they may interfere with the administered treatment. Although formaldehyde is less expensive than glutaraldehydes, it is also more irritating to the eyes, skin and respiratory tract and is classified as a potential carcinogen,[16] so it is used much less commonly.
Ionizing radiation is typically used only for sterilizing items for which none of the above methods are practical, because of the risks involved in the process[citation needed]
https://en.wikipedia.org/wiki/Infection_prevention_and_control#Cleaning%2C_Disinfection%2C_Sterilization
https://en.wikipedia.org/wiki/Occupational_Safety_and_Health_Administration
https://en.wikipedia.org/wiki/United_States_Department_of_Labor
A secret service is a government agency, intelligence agency, or the activities of a government agency, concerned with the gathering of intelligence data. The tasks and powers of a secret service can vary greatly from one country to another. For instance, a country may establish a secret service which has some policing powers (such as surveillance) but not others. The powers and duties of a government organization may be partly secret and partly not. The organization may be said to operate openly at home and secretly abroad, or vice versa. Secret police and intelligence agencies can usually be considered secret services. [1]
Various states and regimes, at different times and places, established bodies that could be described as a secret service or secret police – for example, the agentes in rebus of the late Roman Empire were sometimes defined as such. In modern times, the French police officer Joseph Fouché is sometimes regarded as the primary pioneer within secret intelligence. Among other things, he is alleged to have prevented several murder attempts on Napoleon during his time as First Consul (1799–1804) through a large and tight net of various informers.
https://en.wikipedia.org/wiki/Secret_service
The agentes in rebus (Ancient Greek: ἀγγελιαφόροι, romanized: angeliaphóroi, lit. 'messengers', or μαγιστριανοί, magistrianoí, 'magister's men'[1]) were the late Roman imperial courier service and general agents of the central government from the 4th to the 7th centuries.
https://en.wikipedia.org/wiki/Agentes_in_rebus
Secret Service of the Air (also known as Murder Plane) is a 1939 American adventure film directed by Noel M. Smith and starring Ronald Reagan. This film was the first in Warner Bros.' Secret Service series. The series consisted of four films, all starring Ronald Reagan as Lieutenant "Brass" Bancroft of the U.S. Secret Service and Eddie Foy, Jr. as his sidekick "Gabby." It was followed up by Code of the Secret Service, Smashing the Money Ring (both 1939), and Murder in the Air (1940), the last film in the series.[1] Reagan was just starting out his film career and commented later that during that period, he was a B movie "Errol Flynn".[2]
https://en.wikipedia.org/wiki/Secret_Service_of_the_Air
Plot
An undercover Secret Service agent stumbles upon a smuggling ring illegally transporting Mexicans into the United States by air. When he pulls a gun on the pilot on one such trip, the pilot sends the aircraft into a sudden climb, causing the agent to tumble back into the cabin; the pilot then pulls a lever which opens the cabin floor, sending the agent and six illegal aliens plummeting to their deaths.https://en.wikipedia.org/wiki/Secret_Service_of_the_Air
Human trafficking is the trade of humans for the purpose of forced labour, sexual slavery, or commercial sexual exploitation.[1] Human trafficking can occur within a country or trans-nationally. It is distinct from people smuggling, which is characterized by the consent of the person being smuggled.
Human trafficking is condemned as a violation of human rights by international conventions, but legal protection varies globally. The practice has millions of victims around the world.
https://en.wikipedia.org/wiki/Human_trafficking
Euthanasia (from Greek: εὐθανασία, lit. 'good death': εὖ, eu, 'well, good' + θάνατος, thanatos, 'death') is the practice of intentionally ending life to eliminate pain and suffering.[1][2]
Different countries have different euthanasia laws. The British House of Lords select committee on medical ethics defines euthanasia as "a deliberate intervention undertaken with the express intention of ending a life, to relieve intractable suffering".[3] In the Netherlands and Belgium, euthanasia is understood as "termination of life by a doctor at the request of a patient".[4] The Dutch law, however, does not use the term 'euthanasia' but includes the concept under the broader definition of "assisted suicide and termination of life on request".[5]
Euthanasia is categorized in different ways, which include voluntary, non-voluntary, or involuntary.[6] Voluntary euthanasia is when a person wills to have their life ended and is legal in a growing number of countries. Non-voluntary euthanasia occurs when a patient's consent is unavailable and is legal in some countries under certain limited conditions, in both active and passive forms. Involuntary euthanasia, which is done without asking for consent or against the patient's will, is illegal in all countries and is usually considered murder.
As of 2006 euthanasia had become the most active area of research in bioethics.[7] In some countries divisive public controversy occurs over the moral, ethical, and legal issues associated with euthanasia. Passive euthanasia (known as "pulling the plug") is legal under some circumstances in many countries. Active euthanasia, however, is legal or de facto legal in only a handful of countries (for example: Belgium, Canada and Switzerland), which limit it to specific circumstances and require the approval of counselors and doctors or other specialists. In some countries—such as Nigeria, Saudi Arabia and Pakistan—support for active euthanasia is almost non-existent.
https://en.wikipedia.org/wiki/Euthanasia
For supervised learning applications in machine learning and statistical learning theory, generalization error[1] (also known as the out-of-sample error[2] or the risk) is a measure of how accurately an algorithm is able to predict outcome values for previously unseen data. Because learning algorithms are evaluated on finite samples, the evaluation of a learning algorithm may be sensitive to sampling error. As a result, measurements of prediction error on the current data may not provide much information about predictive ability on new data. Generalization error can be minimized by avoiding overfitting in the learning algorithm. The performance of a machine learning algorithm is visualized by plots that show values of estimates of the generalization error through the learning process, which are called learning curves.
https://en.wikipedia.org/wiki/Generalization_error
Individual psychology (German: Individualpsychologie) is a psychological method or science founded by the Viennese psychiatrist Alfred Adler.[1][2] The English edition of Adler's work on the subject (1925) is a collection of papers and lectures given mainly between 1912 and 1914. The papers cover the whole range of human psychology in a single survey, and were intended to mirror the indivisible unity of the personality.[further explanation needed]
In developing the concept of individual psychology, Adler broke away from the psychoanalytic school of Sigmund Freud.[3][4] While Adler initially called his work "free psychoanalysis", he later rejected the label of "psychoanalyst".[5] His method, involving a holistic approach to the study of character,[6] has been extremely influential in later 20th century counselling and psychiatric strategies.[7]
The term "individual psychology" does not mean to focus on the individual. Adler said one must take into account the patient's whole environment, including the people the patient associates with. The term "individual" is used to mean the patient is an indivisible whole.
https://en.wikipedia.org/wiki/Individual_psychology
Ethics or moral philosophy is a branch[1] of philosophy that "involves systematizing, defending, and recommending concepts of right and wrong behavior".[2] The field of ethics, along with aesthetics, concerns matters of value; these fields comprise the branch of philosophy called axiology.[3]
https://en.wikipedia.org/wiki/Ethics
The Golden Rule is the principle of treating others as one wants to be treated.
https://en.wikipedia.org/wiki/Golden_Rule
A land ethic is a philosophy or theoretical framework about how, ethically, humans should regard the land. The term was coined by Aldo Leopold (1887–1948) in his A Sand County Almanac (1949), a classic text of the environmental movement. There he argues that there is a critical need for a "new ethic", an "ethic dealing with human's relation to land and to the animals and plants which grow upon it".[1]
Leopold offers an ecologically based land ethic that rejects strictly human-centered views of the environment and focuses on the preservation of healthy, self-renewing ecosystems. A Sand County Almanac was the first systematic presentation of a holistic or ecocentric approach to the environment.[2] Although Leopold is credited with coining the term "land ethic", there are many philosophical theories that speak to how humans should treat the land. Some of the most prominent land ethics include those rooted in economics, utilitarianism, libertarianism, egalitarianism, and ecology.
https://en.wikipedia.org/wiki/Land_ethic
Biomimetics or biomimicry is the emulation of the models, systems, and elements of nature for the purpose of solving complex human problems.[2] The terms "biomimetics" and "biomimicry" are derived from Ancient Greek: βίος (bios), life, and μίμησις (mīmēsis), imitation, from μιμεῖσθαι (mīmeisthai), to imitate, from μῖμος (mimos), actor. A closely related field is bionics.[3]
Living organisms have evolved well-adapted structures and materials over geological time through natural selection. Biomimetics has given rise to new technologies inspired by biological solutions at macro and nanoscales. Humans have looked at nature for answers to problems throughout their existence. Nature has solved engineering problems such as self-healing abilities, environmental exposure tolerance and resistance, hydrophobicity, self-assembly, and harnessing solar energy.
https://en.wikipedia.org/wiki/Biomimetics
The history of eugenics is the study of development and advocacy of ideas related to eugenics around the world. Early eugenic ideas were discussed in Ancient Greece and Rome. The height of the modern eugenics movement came in the late 19th and early 20th centuries.
https://en.wikipedia.org/wiki/History_of_eugenics
On the Origin of Species (or, more completely, On the Origin of Species by Means of Natural Selection, or the Preservation of Favoured Races in the Struggle for Life)[3] is a work of scientific literature by Charles Darwin that is considered to be the foundation of evolutionary biology; it was published on 24 November 1859.[4] Darwin's book introduced the scientific theory that populations evolve over the course of generations through a process of natural selection. The book presented a body of evidence that the diversity of life arose by common descent through a branching pattern of evolution. Darwin included evidence that he had collected on the Beagle expedition in the 1830s and his subsequent findings from research, correspondence, and experimentation.[5]
https://en.wikipedia.org/wiki/On_the_Origin_of_Species
Compulsory education refers to a period of education that is required of all people and is imposed by the government. This education may take place at a registered school or at other places.
Compulsory school attendance or compulsory schooling means that parents are obliged to send their children to a certain school.[1]
The International Covenant on Economic, Social and Cultural Rights requires, within a reasonable number of years, the principle of compulsory education free of charge for all.[2] All countries except Bhutan, Papua New Guinea, Solomon Islands, and Vatican City have compulsory education.
https://en.wikipedia.org/wiki/Compulsory_education
https://en.wikipedia.org/wiki/Category:Biology_textbooks
In the United States, education is provided in public and private schools and by individuals through homeschooling. State governments set overall educational standards, often mandate standardized tests for K–12 public school systems and supervise, usually through a board of regents, state colleges, and universities. The bulk of the $1.3 trillion in funding comes from state and local governments, with federal funding accounting for about $260 billion in 2021[9] compared to around $200 billion in past years.[2]
Private schools are free to determine their own curriculum and staffing policies, with voluntary accreditation available through independent regional accreditation authorities, although some state regulation can apply.
In 2013, about 87% of school-age children (those below higher education) attended state-funded public schools, about 10% attended tuition and foundation-funded private schools,[10] and roughly 3% were home-schooled.[11]
By state law, education is compulsory over an age range starting between five and eight and ending somewhere between ages sixteen and eighteen, depending on the state.[12] This requirement can be satisfied in public or state-certified private schools, or an approved home school program. Compulsory education is divided into three levels: elementary school, middle or junior high school, and high school.
Numerous publicly and privately administered colleges and universities offer a wide variety in post-secondary education. Post-secondary education is divided into college, as the first tertiary degree, and graduate school. Higher education includes public research universities, private liberal arts colleges, historically black colleges and universities, community colleges, for-profit colleges, and many other kinds and combinations of institutions. College enrollment rates in the United States have increased over the long term.[13] At the same time, student loan debt has also risen to $1.5 trillion.
The large majority of the world's top universities, as listed by various ranking organizations, are in the United States, including 19 of the top 25, and the most prestigious – the Harvard University,[14][15][16][17] and the country placed first in the annual U.S. News & World Report Best Countries for Education rankings.[18] The U.S. has by far the most Nobel Prize winners in history, with 403 (having won 406 awards).[19]
The United States spends more per student on education than any other country.[20] In 2014, the Economist Intelligence Unit rated U.S. education as 14th best in the world. The Programme for International Student Assessment coordinated by the Organisation for Economic Co-operation and Development (OECD) currently ranks the overall knowledge and skills of American 15-year-olds as 31st in the world in reading literacy, mathematics, and science with the average American student scoring 487.7, compared with the OECD average of 493.[21][22] In 2014, the country spent 6.2% of its GDP on all levels of education—1.0 percentage points above the OECD average of 5.2%.[23] In 2017, 46.4% of Americans aged 25 to 64 attained some form of post-secondary education.[5] 48% of Americans aged 25 to 34 attained some form of tertiary education, about 4% above the OECD average of 44%.[24][25][26] 35% of Americans aged 25 and over have achieved a bachelor's degree or higher.[27]
History
19th century
Colonial New England encouraged its towns to support free public schools funded by taxation. In the early 19th century, Massachusetts took the lead in education reform and public education with programs designed by Horace Mann that were widely emulated across the North. Teachers were specially trained in normal schools and taught the three Rs (of reading, writing, and arithmetic) and also history and geography. Public education was at the elementary level in most places. After the Civil War (1861–1865), the cities began building high schools. The South was far behind northern standards on every educational measure and gave weak support to its segregated all-black schools. However, northern philanthropy and northern churches provided assistance to private black colleges across the South. Religious denominations across the country set up their private colleges. States also opened state universities, but they were quite small until well into the 20th century.
https://en.wikipedia.org/wiki/Education_in_the_United_States
https://en.wikipedia.org/wiki/Conspiracy
A clandestine cell system is a method for organizing a group of people, such as resistance fighters, sleeper agents, mobsters, or terrorists, to make it harder for the police or military to catch them.
In a cell structure, each of the small groups of people in the cell know the identities of the people only in their own cell. Thus any cell member who is apprehended and interrogated (or who is a mole) will not likely know the identities of the higher-ranking individuals in the organization.
The structure of a clandestine cell system can range from a strict hierarchy to an extremely distributed organization, depending on the group's ideology, its operational area, the communications technologies available, and the nature of the mission.
Criminal organizations, undercover operations, and unconventional warfare units led by special forces may also use this sort of organizational structure.
https://en.wikipedia.org/wiki/Clandestine_cell_system
Etymology
Conspiracy comes from the Latin word conspiratio. While conspiratio can mean "plot" or "conspiracy", it can also translated as "unity" and "agreement", in the context of a group.[11] Conspiratio comes from conspiro which, while still meaning "conspiracy" in the modern sense, also means "I sing in unison", as con- means "with" or "together", and spiro means "I breathe", literally meaning "I breathe together with others".
https://en.wikipedia.org/wiki/Conspiracy
A scheme is a systematic plan for the implementation of a certain idea.
Scheme or schemer may refer to:
Arts and entertainment
- The Scheme (TV series), a BBC Scotland documentary series
- The Scheme (band), an English pop band
- The Scheme, an action role-playing video game for the PC-8801, made by Quest Corporation
- Schemer (comics), Richard Fisk, a Marvel Comics villain turned antihero
- Horace Schemer, a fictional character in the TV series Shining Time Station
- Schemee, a fictional child character and Schemer's nephew in the TV Series Shining Time Station
- Schemers (film), a Scottish film
Other uses
- Classification scheme, eg a thesaurus, a taxonomy, a data model, or an ontology
- Scheme (programming language), a minimalist dialect of Lisp
- Scheme (mathematics), a concept in algebraic geometry
- Scheme (linguistics), a figure of speech that changes a sentence's structure
- Scam, an attempt to swindle or cheat people through deception
- Get-rich-quick scheme, a plan to obtain high rates of return for a small investment
- Matrix scheme, or ladder scheme, a business model involving the exchange of money for a certain product with a side bonus of being added to a waiting list for a product of greater value than the amount given
- Ponzi scheme, a scam paying investors returns from their own or others' money (rather than from profits)
- Pyramid scheme, a non-sustainable business model involving payments primarily for enrolling other people
- Google Schemer, a former service allowing its users to share plans and interests
- Scheme, a type of government program in India
See also
- Color scheme
- Contract
- Housing scheme, a Scottish term for a council housing development
- Investment fund
- Numbering scheme
- Rhyme scheme
- Schema (disambiguation)
- URI scheme, the outermost part of internet Uniform Resource Identifiers
https://en.wikipedia.org/wiki/Scheme
Medicalization is the process by which human conditions and problems come to be defined and treated as medical conditions, and thus become the subject of medical study, diagnosis, prevention, or treatment. Medicalization can be driven by new evidence or hypotheses about conditions; by changing social attitudes or economic considerations; or by the development of new medications or treatments.
https://en.wikipedia.org/wiki/Medicalization
https://en.wikipedia.org/wiki/Parapsychology
https://en.wikipedia.org/wiki/Behavioral_economics
A pyramid scheme is a business model that recruits members via a promise of payments or services for enrolling others into the scheme, rather than supplying investments or sale of products. As recruiting multiplies, recruiting becomes quickly impossible, and most members are unable to profit; as such, pyramid schemes are unsustainable and often illegal.
Pyramid schemes have existed for at least a century in different guises. Some multi-level marketing plans have been classified as pyramid schemes.[1]
https://en.wikipedia.org/wiki/Pyramid_scheme
https://en.wikipedia.org/wiki/Category:Pyramid_and_Ponzi_schemes
https://en.wikipedia.org/wiki/Scams_in_intellectual_property
https://en.wikipedia.org/wiki/List_of_con_artists
A SIM swap scam (also known as port-out scam, SIM splitting, Smishing[1] and simjacking, SIM swapping)[2] is a type of account takeover fraud that generally targets a weakness in two-factor authentication and two-step verification in which the second factor or step is a text message (SMS) or call placed to a mobile telephone.
https://en.wikipedia.org/wiki/SIM_swap_scam
An SSA impersonation scam, or SSA scam, is a class of telecommunications fraud and scam which targets citizens of the United States by impersonating personnel of the Social Security Administration. SSA scams are typically initiated by pre-recorded messages, or robocalls, which are designed to panic the victim so that they follow the scammer's instructions. In 2018, over 35,000 incidences[spelling?] of SSA scam robocalls were reported to the Better Business Bureau, and the total losses of victims added up to over $10 million.[1] It is believed that approximately 47% of Americans were subject to an SSA impersonation scam robocall during a three-month period in mid- to late 2020, and that 21% of seniors were targeted by at least three SSA scam robocalls in the same time period.[2][3]
https://en.wikipedia.org/wiki/SSA_impersonation_scam
Theoretically, it is possible for certain Ponzi schemes to ultimately "succeed" financially, at least so long as a Ponzi scheme was not what the promoters were initially intending to operate. For example, a failing hedge fund reporting fraudulent returns could conceivably "make good" its reported numbers, for example by making a successful high-risk investment. Moreover, if the operators of such a scheme are facing the likelihood of imminent collapse accompanied by criminal charges, they may see little additional "risk" to themselves in attempting to cover their tracks by engaging in further illegal acts to try and make good the shortfall (for example, by engaging in insider trading). Especially with investment vehicles like hedge funds that are regulated and monitored less heavily than other investment vehicles such as mutual funds,[23] in the absence of a whistleblower or accompanying illegal acts, any fraudulent content in reports is often difficult to detect unless and until the investment vehicles ultimately collapse.
https://en.wikipedia.org/wiki/Ponzi_scheme
https://en.wikipedia.org/wiki/Glossary_of_algebraic_geometry#affine
A scheme of work[1][2] defines the structure and content of an academic course. It splits an often-multi-year curriculum into deliverable units of work, each of a far shorter weeks' duration (e.g. two or three weeks). Each unit of work is then analysed out into teachable individual topics of even shorter duration (e.g. two hours or less).
Better schemes of work map out clearly how resources (e.g. books, equipment, time) and class activities (e.g. teacher-talk, group work, practicals, discussions) and assessment strategies (e.g. tests, quizzes, Q&A, homework) will be used to teach each topic and assess students' progress in learning the material associated with each topic, unit and the scheme of work as a whole. As students progress through the scheme of work, there is an expectation that their perception of the interconnections between topics and units will be enhanced.
Schemes of work may include times and dates (deadlines) for delivering the different elements of the curriculum. Philosophically, this is linked to a belief that all students should be exposed to all elements of the curriculum such that those who are able to "keep up" ("the best" / elite) do not miss out on any content and can achieve the highest grades. This might be described as a "traditionalist" view.
There is a conflicting philosophical view that deadlines should be avoided and that each class should progress at its own pace: such that no student is "left behind". Whilst the remaining students "catch up", those students who understand quickly should be placed in a "holding pattern" full of puzzles and questions that challenge them to connect recent learning with longer-established learning (they may also be encouraged to spend a small amount of time enhancing their understanding by supporting teaching staff in unpicking underlying errors/questions of fellow students who have not grasped recent ideas as quickly). This view might be described as a "Mastery" approach. In mathematics teaching in England it is strongly supported by the Government-funded National Centre for Excellence in Teaching Mathematics[3] based on research guided by the globally-exceptional performance of schools in Singapore and Shanghai.
https://en.wikipedia.org/wiki/Scheme_of_work
The CO2 fertilization effect or carbon fertilization effect causes an increased rate of photosynthesis while limiting leaf transpiration in plants. Both processes result from increased levels of atmospheric carbon dioxide (CO2).[1][2] The carbon fertilization effect varies depending on plant species, air and soil temperature, and availability of water and nutrients.[3][4] Net primary productivity (NPP) might positively respond to the carbon fertilization effect.[5] Although, evidence shows that enhanced rates of photosynthesis in plants due to CO2 fertilization do not directly enhance all plant growth, and thus carbon storage.[3] The carbon fertilization effect has been reported to be the cause of 44% of gross primary productivity (GPP) increase since the 2000s.[6] Earth System Models, Land System Models and Dynamic Global Vegetation Models are used to investigate and interpret vegetation trends related to increasing levels of atmospheric CO2.[3][7] However, the ecosystem processes associated with the CO2 fertilization effect remain uncertain and therefore are challenging to model.[8][9]
Terrestrial ecosystems have reduced atmospheric CO2 concentrations and have partially mitigated climate change effects.[10] The response by plants to the carbon fertilization effect is unlikely to significantly reduce atmospheric CO2 concentration over the next century due to the increasing anthropogenic influences on atmospheric CO2.[2][3][11][12] Earth's vegetated lands have shown significant greening since the early 1980s[13] largely due to rising levels of atmospheric CO2.[14][15][16][17]
Theory predicts the tropics to have the largest uptake due to the carbon fertilization effect, but this has not been observed. The amount of CO2 uptake from CO2 fertilization also depends on how forests respond to climate change, and if they are protected from deforestation.[18]
Changes in atmospheric carbon dioxide may reduce the nutritional quality of some crops, with for instance wheat having less protein and less of some minerals.[19]: 439 [20] Food crops could see a reduction of protein, iron and zinc content in common food crops of 3 to 17%.[21]
https://en.wikipedia.org/wiki/CO2_fertilization_effect
Organized crime (or organised crime) is a category of transnational, national, or local groupings of highly centralized enterprises run by criminals to engage in illegal activity, most commonly for profit. While organized crime is generally thought of as a form of illegal business, some criminal organizations, such as terrorist groups, rebel forces, and separatists, are politically motivated. Many criminal organizations rely on fear or terror to achieve their goals or aims as well as to maintain control within the organization and may adopt tactics commonly used by authoritarian regimes to maintain power. Some forms of organized crime simply exist to cater towards demand of illegal goods in a state or to facilitate trade of goods and services that may have been banned by a state (such as illegal drugs or firearms). Sometimes, criminal organizations force people to do business with them, such as when a gang extorts money from shopkeepers for "protection".[1] Street gangs may often be deemed organized crime groups or, under stricter definitions of organized crime, may become disciplined enough to be considered organized. A criminal organization can also be referred to as a gang, mafia, mob,[2][3] (crime) ring,[4] or syndicate;[5] the network, subculture, and community of criminals involved in organized crime may be referred to as the underworld or gangland. Sociologists sometimes specifically distinguish a "mafia" as a type of organized crime group that specializes in the supply of extra-legal protection and quasi-law enforcement. Academic studies of the original "Mafia", the Italian Mafia,[6] which predates the other groups, generated an economic study of organized crime groups and exerted great influence on studies of the Russian mafia,[7] the Chinese Triads,[8] the Hong Kong Triads,[9] and the Japanese Yakuza.[10]
Other organizations—including states, churches, militaries, police forces, and corporations—may sometimes use organized-crime methods to conduct their activities, but their powers derive from their status as formal social institutions. There is a tendency to distinguish "traditional" organized crime from certain other forms of crime that also usually involve organized or group criminal acts, such as white-collar crime, financial crimes, political crimes, war crimes, state crimes, and treason. This distinction is not always apparent and academics continue to debate the matter.[11] For example, in failed states that can no longer perform basic functions such as education, security, or governance (usually due to fractious violence or to extreme poverty), organized crime, governance, and war sometimes complement each other. The term "oligarchy" has been used to describe democratic countries whose political, social, and economic institutions come under the control of a few families and business oligarchs that may be deemed or may devolve into organized crime groups in practice.[12][failed verification] By their very nature, kleptocracies, mafia states, narco-states or narcokleptocracies, and states with high levels of clientelism and political corruption are either heavily involved with organized crime or tend to foster organized crime within their own governments.
In the United States, the Organized Crime Control Act (1970) defines organized crime as "[t]he unlawful activities of [...] a highly organized, disciplined association [...]".[13] Criminal activity as a structured process is referred to as racketeering. In the UK, police estimate that organized crime involves up to 38,000 people operating in 6,000 various groups.[14] Historically, the largest organized crime force in the United States has been La Cosa Nostra (Italian-American Mafia), but other transnational criminal organizations have also risen in prominence in recent decades.[15] A 2012 article in a U.S. Department of Justice journal stated that: "Since the end of the Cold War, organized crime groups from Russia, China, Italy, Nigeria, and Japan have increased their international presence and worldwide networks or have become involved in more transnational criminal activities. Most of the world's major international organized crime groups are present in the United States."[15] The US Drug Enforcement Administration's 2017 National Drug Threat Assessment classified Mexican transnational criminal organizations (TCOs) as the "greatest criminal drug threat to the United States," citing their dominance "over large regions in Mexico used for the cultivation, production, importation, and transportation of illicit drugs" and identifying the Sinaloa, Jalisco New Generation, Juárez, Gulf, Los Zetas, and Beltrán-Leyva cartels as the six Mexican TCO with the greatest influence in drug trafficking to the United States.[16] The United Nations Sustainable Development Goal 16 has a target to combat all forms of organized crime as part of the 2030 Agenda.[17]
In some countries, football hooligans can be considered a criminal organization if it engages in illicit and violent activities.
https://en.wikipedia.org/wiki/Organized_crime
A bookmaker, bookie, or turf accountant is an organization or a person that accepts and pays out bets on sporting and other events at agreed-upon odds.
https://en.wikipedia.org/wiki/Bookmaker
Typical activities
Organized crime groups provide a range of illegal services and goods. Organized crime often victimizes businesses through the use of extortion or theft and fraud activities like hijacking cargo trucks and ships, robbing goods, committing bankruptcy fraud (also known as "bust-out"), insurance fraud or stock fraud (insider trading). Organized crime groups also victimize individuals by car theft (either for dismantling at "chop shops" or for export), art theft, Metal theft, bank robbery, burglary, jewelry and gems theft and heists, shoplifting, computer hacking, credit card fraud, economic espionage, embezzlement, identity theft, and securities fraud ("pump and dump" scam). Some organized crime groups defraud national, state, or local governments by bid rigging public projects, counterfeiting money, smuggling or manufacturing untaxed alcohol (rum-running) or cigarettes (buttlegging), and providing immigrant workers to avoid taxes.
Organized crime groups seek out corrupt public officials in executive, law enforcement, and judicial roles so that their criminal rackets and activities on the black market can avoid, or at least receive early warnings about, investigation and prosecution.
Activities of organized crime include loansharking of money at very high interest rates, blackmailing, assassination, backyard breeding, bombings, bookmaking and illegal gambling, confidence tricks, forging early release prison documents, copyright infringement, counterfeiting of intellectual property, metal theft, fencing, kidnapping, prostitution, smuggling, drug trafficking, arms trafficking, impersonating armored truck drivers, oil smuggling, antiquities smuggling, organ trafficking, contract killing, identity document forgery, money laundering, bribery, seduction, electoral fraud, insurance fraud, point shaving, price fixing, cargo theft via fictions pickup, illegal taxicab operation, illegal dumping of toxic waste, illegal trading of nuclear materials, military equipment smuggling, nuclear weapons smuggling, passport fraud, providing illegal immigration and cheap labor, people smuggling, trading in endangered species, and trafficking in human beings. Organized crime groups also do a range of business and labor racketeering activities, such as skimming casinos, insider trading, setting up monopolies in industries such as garbage collecting, construction and cement pouring, bid rigging, getting "no-show" and "no-work" jobs, political corruption and bullying.
Violence
Assault
The commission of violent crime may form part of a criminal organization's 'tools' used to achieve criminogenic goals (for example, its threatening, authoritative, coercive, terror-inducing, or rebellious role), due to psycho-social factors (cultural conflict, aggression, rebellion against authority, access to illicit substances, counter-cultural dynamic), or may, in and of itself, be crime rationally chosen by individual criminals and the groups they form. Assaults are used for coercive measures, to "rough up" debtors, competition or recruits, in the commission of robberies, in connection to other property offenses, and as an expression of counter-cultural authority;[61] violence is normalized within criminal organizations (in direct opposition to mainstream society) and the locations they control.[62] Whilst the intensity of violence is dependent on the types of crime the organization is involved in (as well as their organizational structure or cultural tradition) aggressive acts range on a spectrum from low-grade physical assaults to major trauma assaults. Bodily harm and grievous bodily harm, within the context of organized crime, must be understood as indicators of intense social and cultural conflict, motivations contrary to the security of the public, and other psycho-social factors.[63]
Murder
Murder has evolved from the honor and vengeance killings of the Yakuza or Sicilian mafia[64][65][66][67] which placed large physical and symbolic importance on the act of murder, its purposes and consequences,[68][69] to a much less discriminate form of expressing power, enforcing criminal authority, achieving retribution or eliminating competition. The role of the hit man has been generally consistent throughout the history of organized crime, whether that be due to the efficiency or expediency of hiring a professional assassin or the need to distance oneself from the commission of murderous acts (making it harder to prove criminal culpability). This may include the assassination of notable figures (public, private or criminal), once again dependent on authority, retribution or competition. Revenge killings, armed robberies, violent disputes over controlled territories and offenses against members of the public must also be considered when looking at the dynamic between different criminal organizations and their (at times) conflicting needs. After killing their victims, the gangsters often try to destroy evidence by getting rid of the victims remains in such a way as to prevent, hinder, or delay the discovery of the body, to prevent identification of the body, or to prevent autopsy. The different ways that organized criminals have been known to dispose of dead bodies include but are not limited to hiding the bodies in trash or landfills, feeding the bodies to animals (such as pigs or rats),[70][71] destruction by industrial process (such as machinery, chemical bath, molten metal or a junked car), injection into the legitimate body disposal system (such as morgues, funeral homes, cemeteries, crematoriums, funeral pyres or cadaver donations) or covert killings at health care facilities, disguising as animal flesh (such as food waste or restaurant food), creating false evidence of the circumstances of death and letting investigators dispose of the body, possibly obscuring identity, abandonment in a remote area where the body can degrade significantly, while exposure to elements (such as rain, wind, heat, etc) as well as animal activity (such as consumption by scavengers) can contaminate the crime scene and/or destroy evidence before being discovered, if ever, such as a wilderness area (such as national parks or nature reserves)[72] or an abandoned area (such as an abandoned building, well or mine). However, there are also many instances of gangsters putting the bodies of their victims on display as a form of psychological warfare against their enemies.
Vigilantism
In an ironic twist, criminal syndicates are often known to commit acts of vigilantism by enforcing laws, investigating certain criminal acts and punishing those who violate such rules. People who are often targeted by organized criminals tend to be individualistic criminals, people who committed crimes that are considered particularly heinous by society, people who committed wrongdoings against members or associates, rivals and/or terrorist groups. One reason why criminal groups might commit vigilantism in their neighborhoods is to prevent heavy levels of community policing, that could be harmful to their illicit businesses; additionally the vigilante acts could help the gangs to ingratiate themselves in their communities.
During the roaring twenties, the anti-catholic and anti-semitic Ku Klux Klan was known to be staunch enforcers of prohibition, as a result Italian, Irish, Polish, and Jewish mobsters would at times have violent confrontations against the KKK, on one occasion FBI informant and notorious mobster Gregory Scarpa kidnapped and tortured a local Klansmen into revealing the bodies of Civil rights workers who had been killed by the KKK.[73] During World War II, America had a growing number of Nazi supporters that formed the German American Bund, which was known to be threatening to local Jewish people, as a result Jewish mobsters (such a Meyer Lansky, Bugsy Siegel and Jack Ruby) were often hired by the American Jewish community to help defend against the Nazi bund, even going as far as attacking and killing Nazi sympathizers during bund meetings.[74] Vigilante groups such as the Black Panther Party, White Panther Party and Young Lords have been accused of committing crimes in order to fund their political activities.[75]
While protection racketeering is often seen as nothing more than extortion, criminal syndicates that participate in protection rackets have at times provided genuine protection against other criminals for their clients, the reason for this is because the criminal organization would want the business of their clients to do better so that the gang can demand even more protection money, additionally if the gang has enough knowledge of the local fencers, they may even be able to track down and retrieve any objects that were stolen from the business owner, to further help their clients the gang may also force out, disrupt, vandalize, steal from or shutdown competing businesses for their clients.[76] In Colombia the insurgent groups were trying to steal land, kidnap family members, and extort money from the drug barons. As a result the drug lords of the Medellín Cartel formed a paramilitary vigilante group known as Muerte a Secuestradores ("Death to Kidnappers") to defend the cartel against the FARC and M-19, even kidnapping and torturing the leader of M-19 before leaving him tied up in front of a police station.[77] During the Medellín Cartel's war against the Colombian government, both the Norte del Valle Cartel and Cali Cartel formed and operated a vigilante group called Los Pepes (which also comprised members of the Colombian government, police and former members of the Medellín Cartel) to bring about the downfall of Pablo Escobar; they did so by bombing the properties of the Medellín Cartel and kidnapping, torturing and/or killing Escobar's associates as well as working alongside the Search Bloc, which would eventually lead to the dismantling of the Medellín Cartel and the death of Pablo Escobar.[78] Because of the high levels of corruption, the Oficina de Envigado would do things to help the police and vice versa, to the point where the police and the cartel would sometimes do operations together against other criminals; additionally the leaders of La Oficina would often act as judges to mediate disputes between the various different drug gangs throughout Colombia, which according to some helped prevented a lot of disputes from turning violent.[79]
On Somalia coastline many people rely on fishing for economic survival, because of this Somali pirates are often known to attack foreign vessels who partake in illegal fishing and overfishing in their waters and vessels that illegally dump waste into their waters. As a result, marine biologists say that the local fishery is recovering.[80] In Mexico a vigilante group called Grupos de autodefensa comunitaria was formed to counter the illegal loggers, the La Familia Michoacana Cartel and a drug cartel/cult known as the Knights Templar Cartel; as they grew, they were being joined by former cartel members and as they got bigger they began to sell drugs in order to buy weapons. The Knights Templar Cartel was eventually defeated and dissolved by the vigilantes' actions but they ended up forming their own cartel called Los Viagras, which has links with the Jalisco New Generation Cartel.[81] The Minuteman Project is a far-right paramilitary organization that seeks to prevent illegal immigration across the US-Mexico border; however, doing so is detrimental to gangs like Mara Salvatrucha, who make money through people smuggling, and as a result MS-13 is known to commit acts of violence against members of the Minutemen, to prevent them from interfering with their illegal immigration activities.[82] Throughout the world there are various anti-gang vigilante groups, who profess to be fighting against gang influence, but share characteristics and acts similarly to gangs, including Sombra Negra, Friends Stand United, People Against Gangsterism and Drugs, and OG Imba.[83][84] Gangs that are involved in drug trafficking often commit violent acts to stop or force out independent dealers—drug dealers with no gang ties—to keep them from taking customers.
In America there is an animal welfare organization called Rescue Ink, in which outlaw biker gang members volunteer to rescue animals in need and combat against people who commit animal cruelty, such as breaking up cockfighting rings, stopping the killing of stray cats, breaking up dog fighting rings, and rescuing pets from abusive owners.[85] In the American prison system, prison gangs are often known to physically harm and even kill inmates who have committed such crimes as child murder, serial killing, pedophilia, hate crimes, domestic violence, and rape, and inmates who have committed crimes against the elderly, animals, the disabled, the poor and the less fortunate.[86][87] In many minority communities and poor neighborhoods, residents often distrust law enforcement, as a result the gang syndicates often take over to "police" their neighborhoods by committing acts against people who had committed crimes such as bullying, muggings, home invasions, hate crimes, stalking, sexual assault, domestic violence and child molestation, as well as mediating disputes between neighbors. The ways that the gangs would punish such individuals could range from forced apologies, being threatened, being forced to return stolen objects, vandalizing property, arson, being forced to move, bombings, being assaulted and/or battered, kidnappings, false imprisonment, torture and/or being murdered.[88] Some criminal syndicates have been known to hold their own "trials" for members of theirs who had been accused of wrongdoing; the punishments that the accused member would face if "found guilty" would vary depending on the offense.
Terrorism
In addition to what is considered traditional organized crime involving direct crimes of fraud swindles, scams, racketeering and other acts motivated for the accumulation of monetary gain, there is also non-traditional organized crime which is engaged in for political or ideological gain or acceptance. Such crime groups are often labelled terrorist groups or narcoterrorists.[89][90]
There is no universally agreed, legally binding, criminal law definition of terrorism.[91][92] Common definitions of terrorism refer only to those violent acts which are intended to create fear (terror), are perpetrated for a religious, political or ideological goal, deliberately target or disregard the safety of non-combatants (e.g., neutral military personnel or civilians), and are committed by non-government agencies.[89] Some definitions also include acts of unlawful violence and war, especially crimes against humanity (see the Nuremberg Trials), Allied authorities deeming the German Nazi Party, its paramilitary and police organizations, and numerous associations subsidiary to the Nazi Party "criminal organizations". The use of similar tactics by criminal organizations for protection rackets or to enforce a code of silence is usually not labeled terrorism though these same actions may be labeled terrorism when done by a politically motivated group.
Notable groups include the Medellín Cartel, Corleonesi Mafia, various Mexican Cartels, and Jamaican Posse.
Other
Financial crime
This article needs additional citations for verification. (June 2011) |
Organized crime groups generate large amounts of money by activities such as drug trafficking, arms smuggling, extortion, theft, and financial crime.[93] These illegally sourced assets are of little use to them unless they can disguise it and convert it into funds that are available for investment into legitimate enterprise. The methods they use for converting its ‘dirty’ money into ‘clean’ assets encourages corruption. Organized crime groups need to hide the money's illegal origin. This allows for the expansion of OC groups, as the ‘laundry’ or ‘wash cycle’ operates to cover the money trail and convert proceeds of crime into usable assets. Money laundering is bad for international and domestic trade, banking reputations and for effective governments and rule of law. This is due to the methods used to hide the proceeds of crime. These methods include, but are not limited to: buying easily transported values, transfer pricing, and using "underground banks,"[94] as well as infiltrating firms in the legal economy.[95]
Launderers will also co-mingle illegal money with revenue made from businesses in order to further mask their illicit funds. Accurate figures for the amounts of criminal proceeds laundered are almost impossible to calculate, rough estimates have been made, but only give a sense of the scale of the problem and not quite how great the problem truly is. The United Nations Office on Drugs and Crime conducted a study, they estimated that in 2009, money laundering equated to about 2.7% of global GDP being laundered; this is equal to about 1.6 trillion US dollars.[96] The Financial Action Task Force on Money Laundering (FATF), an intergovernmental body set up to combat money laundering, has stated that "A sustained effort between 1996 and 2000 by the Financial Action Task Force (FATF) to produce such estimates failed."[97] However, anti-money laundering efforts that seize money laundered assets in 2001 amounted to $386 million.[97] The rapid growth of money laundering is due to:
- the scale of organized crime precluding it from being a cash business - groups have little option but to convert its proceeds into legitimate funds and do so by investment, by developing legitimate businesses and purchasing property;
- globalization of communications and commerce - technology has made rapid transfer of funds across international borders much easier, with groups continuously changing techniques to avoid investigation; and,
- a lack of effective financial regulation in parts of the global economy.
Money laundering is a three-stage process:
- Placement: (also called immersion) groups ‘smurf’ small amounts at a time to avoid suspicion; physical disposal of money by moving crime funds into the legitimate financial system; may involve bank complicity, mixing licit and illicit funds, cash purchases and smuggling currency to safe havens.
- Layering: disguises the trail to foil pursuit. Also called ‘heavy soaping’. It involves creating false paper trails, converting cash into assets by cash purchases.
- Integration: (also called ‘spin dry): Making it into clean taxable income by real-estate transactions, sham loans, foreign bank complicity and false import and export transactions.
Means of money laundering:
- Money transmitters, black money markets purchasing goods, gambling, increasing the complexity of the money trail.
- Underground banking (flying money), involves clandestine ‘bankers’ around the world.
- It often involves otherwise legitimate banks and professionals.
The policy aim in this area is to make the financial markets transparent, and minimize the circulation of criminal money and its cost upon legitimate markets.[98][99]
Counterfeiting
Counterfeiting money is another financial crime. The counterfeiting of money includes illegally producing money that is then used to pay for anything desired. In addition to being a financial crime, counterfeiting also involves manufacturing or distributing goods under assumed names. Counterfeiters benefit because consumers believe they are buying goods from companies that they trust, when in reality they are buying low quality counterfeit goods.[100] In 2007, the OECD reported the scope of counterfeit products to include food, pharmaceuticals, pesticides, electrical components, tobacco and even household cleaning products in addition to the usual films, music, literature, games and other electrical appliances, software and fashion.[101] A number of qualitative changes in the trade of counterfeit products:
- a large increase in fake goods which are dangerous to health and safety;
- most products repossessed by authorities are now household items rather than luxury goods;
- a growing number of technological products; and,
- production is now operated on an industrial scale.[102]
Tax evasion
The economic effects of organized crime have been approached from a number of both theoretical and empirical positions, however the nature of such activity allows for misrepresentation.[103][104][105][106][107][108] The level of taxation taken by a nation-state, rates of unemployment, mean household incomes and level of satisfaction with government and other economic factors all contribute to the likelihood of criminals to participate in tax evasion.[104] As most organized crime is perpetrated in the liminal state between legitimate and illegitimate markets, these economic factors must adjusted to ensure the optimal amount of taxation without promoting the practice of tax evasion.[109] As with any other crime, technological advancements have made the commission of tax evasion easier, faster and more globalized. The ability for organized criminals to operate fraudulent financial accounts, utilize illicit offshore bank accounts, access tax havens or tax shelters,[110] and operating goods smuggling syndicates to evade importation taxes help ensure financial sustainability, security from law enforcement, general anonymity and the continuation of their operations.
Cybercrime
Internet fraud
Identity theft is a form of fraud or cheating of another person's identity in which someone pretends to be someone else by assuming that person's identity, typically in order to access resources or obtain credit and other benefits in that person's name. Victims of identity theft (those whose identity has been assumed by the identity thief) can suffer adverse consequences if held accountable for the perpetrator's actions, as can organizations and individuals who are defrauded by the identity thief, and to that extent are also victims. Internet fraud refers to the actual use of Internet services to present fraudulent solicitations to prospective victims, to conduct fraudulent transactions, or to transmit the proceeds of fraud to financial institutions or to others connected with the scheme. In the context of organized crime, both may serve as means through which other criminal activity may be successfully perpetrated or as the primary goal themselves. Email fraud, advance-fee fraud, romance scams, employment scams, and other phishing scams are the most common and most widely used forms of identity theft,[111] though with the advent of social networking fake websites, accounts and other fraudulent or deceitful activity has become commonplace.
Copyright infringement
Copyright infringement is the unauthorized or prohibited use of works under copyright, infringing the copyright holder's exclusive rights, such as the right to reproduce or perform the copyrighted work, or to make derivative works. Whilst almost universally considered under civil procedure, the impact and intent of organized criminal operations in this area of crime has been the subject of much debate. Article 61 of the Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPs) requires that signatory countries establish criminal procedures and penalties in cases of willful trademark counterfeiting or copyright piracy on a commercial scale. More recently copyright holders have demanded that states provide criminal sanctions for all types of copyright infringement.[112] Organized criminal groups capitalize on consumer complicity, advancements in security and anonymity technology, emerging markets and new methods of product transmission, and the consistent nature of these provides a stable financial basis for other areas of organized crime.[citation needed]
Cyberwarfare
Cyberwarfare refers to politically motivated hacking to conduct sabotage and espionage. It is a form of information warfare sometimes seen as analogous to conventional warfare[113] although this analogy is controversial for both its accuracy and its political motivation. It has been defined as activities by a nation-state to penetrate another nation's computers or networks with the intention of causing civil damage or disruption.[114] Moreover, it acts as the "fifth domain of warfare,"[115] and William J. Lynn, U.S. Deputy Secretary of Defense, states that "as a doctrinal matter, the Pentagon has formally recognized cyberspace as a new domain in warfare . . . [which] has become just as critical to military operations as land, sea, air, and space."[116] Cyber espionage is the practice of obtaining confidential, sensitive, proprietary or classified information from individuals, competitors, groups, or governments using illegal exploitation methods on internet, networks, software and/or computers. There is also a clear military, political, or economic motivation. Unsecured information may be intercepted and modified, making espionage possible internationally. The recently established Cyber Command is currently debating whether such activities as commercial espionage or theft of intellectual property are criminal activities or actual "breaches of national security."[117] Furthermore, military activities that use computers and satellites for coordination are at risk of equipment disruption. Orders and communications can be intercepted or replaced. Power, water, fuel, communications, and transportation infrastructure all may be vulnerable to sabotage. According to Clarke, the civilian realm is also at risk, noting that the security breaches have already gone beyond stolen credit card numbers, and that potential targets can also include the electric power grid, trains, or the stock market.[117]
Computer viruses
The term "computer virus" may be used as an overarching phrase to include all types of true viruses, malware, including computer worms, Trojan horses, most rootkits, spyware, dishonest adware and other malicious and unwanted software (though all are technically unique),[118] and proves to be quite financially lucrative for criminal organizations,[119] offering greater opportunities for fraud and extortion whilst increasing security, secrecy and anonymity.[120] Worms may be utilized by organized crime groups to exploit security vulnerabilities (duplicating itself automatically across other computers a given network),[121] while a Trojan horse is a program that appears harmless but hides malicious functions (such as retrieval of stored confidential data, corruption of information, or interception of transmissions). Worms and Trojan horses, like viruses, may harm a computer system's data or performance. Applying the Internet model of organized crime, the proliferation of computer viruses and other malicious software promotes a sense of detachment between the perpetrator (whether that be the criminal organization or another individual) and the victim; this may help to explain vast increases in cyber-crime such as these for the purpose of ideological crime or terrorism.[122] In mid July 2010, security experts discovered a malicious software program that had infiltrated factory computers and had spread to plants around the world. It is considered "the first attack on critical industrial infrastructure that sits at the foundation of modern economies," notes the New York Times.[123]
White-collar crime and corruption
This article needs additional citations for verification. (June 2011) |
Corporate crime
Corporate crime refers to crimes committed either by a corporation (i.e., a business entity having a separate legal personality from the natural persons that manage its activities), or by individuals that may be identified with a corporation or other business entity (see vicarious liability and corporate liability). Corporate crimes are motivated by either the individuals desire or the corporations desire to increase profits.[124] The cost of corporate crimes to United States taxpayers is about $500 billion.[124] Note that some forms of corporate corruption may not actually be criminal if they are not specifically illegal under a given system of laws. For example, some jurisdictions allow insider trading. The different businesses that organized crime figures have been known to operate is vast, including but not limited to pharmacies, import-export companies, check-cashing stores, tattoo parlors, zoos, online dating sites, liquor stores, motorcycle shops, banks, hotels, ranches and plantations, electronic stores, beauty salons, real estate companies, daycares, framing stores, taxicab companies, phone companies, shopping malls, jewelry stores, modeling agencies, dry cleaners, pawn shops, pool halls, clothing stores, freight companies, charity foundations, youth centers, recording studios, sporting goods stores, furniture stores, gyms, insurance companies, security companies, law firms, and private military companies.[125]
Labor racketeering
Labor Racketeering, as defined by the United States Department of Labor, is the infiltrating, exploiting, and controlling of employee benefit plan, union, employer entity, or workforce that is carried out through illegal, violent, or fraudulent means for profit or personal benefit.[126] Labor racketeering has developed since the 1930s, affecting national and international construction, mining, energy production and transportation[127] sectors immensely.[128] Activity has focused on the importation of cheap or unfree labor, involvement with union and public officials (political corruption), and counterfeiting.[129]
Political corruption
Political corruption [130] is the use of legislated powers by government officials for illegitimate private gain. Misuse of government power for other purposes, such as repression of political opponents and general police brutality, is not considered political corruption. Neither are illegal acts by private persons or corporations not directly involved with the government. An illegal act by an officeholder constitutes political corruption only if the act is directly related to their official duties. Forms of corruption vary, but include bribery, extortion, cronyism, nepotism, patronage, graft, and embezzlement. While corruption may facilitate criminal enterprise such as drug trafficking, money laundering, and human trafficking, it is not restricted to these activities. The activities that constitute illegal corruption differ depending on the country or jurisdiction. For instance, certain political funding practices that are legal in one place may be illegal in another. In some cases, government officials have broad or poorly defined powers, which make it difficult to distinguish between legal and illegal actions. Worldwide, bribery alone is estimated to involve over 1 trillion US dollars annually.[131][132] A state of unrestrained political corruption is known as a kleptocracy, literally meaning "rule by thieves".
Drug trafficking
There are three major regions that center around drug trafficking, known as the Golden Triangle (Burma, Laos, Thailand), Golden Crescent (Afghanistan) and Central and South America. There are suggestions that due to the continuing decline in opium production in South East Asia, traffickers may begin to look to Afghanistan as a source of heroin."[133]
With respect to organized crime and accelerating synthetic drug production in East and Southeast Asia, especially the Golden Triangle, Sam Gor, also known as The Company, is the most prominent international crime syndicate based in Asia-Pacific. It is made up of members of five different triads. Sam Gor is understood to be headed by Chinese-Canadian Tse Chi Lop. The Cantonese Chinese syndicate is primarily involved in drug trafficking, earning at least $8 billion per year.[134] Sam Gor is alleged to control 40% of the Asia-Pacific methamphetamine market, while also trafficking heroin and ketamine. The organization is active in a variety of countries, including Myanmar, Thailand, New Zealand, Australia, Japan, China and Taiwan. Sam Gor previously produced meth in Southern China and is now believed to manufacture mainly in the Golden Triangle, specifically Shan State, Myanmar, responsible for much of the massive surge of crystal meth in recent years.[135] The group is understood to be headed by Tse Chi Lop, a Chinese-Canadian gangster born in Guangzhou, China.[136] Tse is a former member of the Hong Kong-based crime group, the Big Circle Gang. In 1988, Tse immigrated to Canada. In 1998, Tse was convicted of transporting heroin into the United States and served nine years behind bars. Tse has been compared in prominence to Joaquín "El Chapo" Guzmán and Pablo Escobar.[137]
The U.S. supply of heroin comes mainly from foreign sources which include Southeast Asia's Golden Triangle, Southwest Asia, and Latin America. Heroin comes in two forms. The first is its chemical base form which presents itself as brown and the second is a salt form that is white.[133] The former is mainly produced in Afghanistan and some south-west countries while the latter had a history of being produced in only south-east Asia, but has since moved to also being produced in Afghanistan. There is some suspicion white Heroin is also being produced in Iran and Pakistan, but it is not confirmed. This area of Heroin production is referred to as the Golden Crescent. Heroin is not the only drug being used in these areas. The European market has shown signs of growing use in opioids on top of the long-term heroin use.[138]
Drug traffickers produce drugs in drug laboratories and drug farms. A drug lab can range in size from small workshops to the size of small towns (such as Tranquilandia). A drug farm is a place where drug crops are grown before being made into illegal narcotics. A drug farm can range in size from smallholdings to large plantations. In addition to drug crops, it's also not uncommon for drug farms to also host livestock, both to have a legal source of revenue to help disguise the dirty money and so that the livestock can provide a source of organic fertilizer (such as manure) for the drug crops.[139] Their are multiple instances where traffickers set up some of their drug farms, safe houses and drug labs in remote wilderness areas.[140] Once produced, the fully processed narcotics are then transported to more populated areas to be sold. Often times the traffickers stationed in these remote criminal settlements, sustain themselves with a combination of survival skills and with food, supplies and workers being brought to them by associates. The reason that traffickers have been known to establish such remote compounds is so that the surrounding area can help to provide varying degrees of natural cover. Additionally the traffickers may also hope, that the surrounding terrain and local wildlife might serve to deter and/or impede either investigative authorities or rival gangs, if the location of the clandestine compound were revealed. While usually thought of as an urban issue, drug trafficking is also known to be a problem in both suburban and rural areas as well.[141]
Human trafficking
Sex trafficking
Human trafficking for the purpose of sexual exploitation is a major cause of contemporary sexual slavery and is primarily for prostituting women and children into sex industries.[142] Sexual slavery encompasses most, if not all, forms of forced prostitution.[143] The terms "forced prostitution" or "enforced prostitution" appear in international and humanitarian conventions but have been insufficiently understood and inconsistently applied. "Forced prostitution" generally refers to conditions of control over a person who is coerced by another to engage in sexual activity.[144] Official numbers of individuals in sexual slavery worldwide vary. In 2001 International Organization for Migration estimated 400,000, the Federal Bureau of Investigation estimated 700,000 and UNICEF estimated 1.75 million.[145] The most common destinations for victims of human trafficking are Thailand, Japan, Israel, Belgium, the Netherlands, Germany, Italy, Turkey and the United States, according to a report by UNODC.[146]
Illegal immigration and people smuggling
People smuggling is defined as "the facilitation, transportation, attempted transportation or illegal entry of a person or persons across an international border, in violation of one or more countries laws, either clandestinely or through deception, such as the use of fraudulent documents".[147] The term is understood as and often used interchangeably with migrant smuggling, which is defined by the United Nations Convention Against Transnational Organized Crime as "...the procurement, in order to obtain, directly or indirectly, a financial or other material benefit, of the illegal entry of a person into a state party of which the person is not a national".[148] This practice has increased over the past few decades and today now accounts for a significant portion of illegal immigration in countries around the world. People smuggling generally takes place with the consent of the person or persons being smuggled, and common reasons for individuals seeking to be smuggled include employment and economic opportunity, personal and/or familial betterment, and escape from persecution or conflict.
Contemporary slavery and forced labor
The number of slaves today remains as high as 12 million[149] to 27 million.[150][151][152] This is probably the smallest proportion of slaves to the rest of the world's population in history.[153] Most are debt slaves, largely in South Asia, who are under debt bondage incurred by lenders, sometimes even for generations.[154] It is the fastest growing criminal industry and is predicted to eventually outgrow drug trafficking.[142][155]
Historical origins
Pre-nineteenth century
Today, crime is sometimes thought of as an urban phenomenon, but for most of human history it was the rural interfaces that encountered the majority of crimes (bearing in mind the fact that for most of human history, rural areas were the vast majority of inhabited places). For the most part, within a village, members kept crime at very low rates; however, outsiders such as pirates, highwaymen and bandits attacked trade routes and roads, at times severely disrupting commerce, raising costs, insurance rates and prices to the consumer. According to criminologist Paul Lunde, "Piracy and banditry were to the pre-industrial world what organized crime is to modern society."[156]
If we take a global rather than a strictly domestic view, it becomes evident that even crime of the organized kind has a long if not a necessarily noble heritage. The word 'thug' dates back to early 13th-century India, when Thugs, or gangs of criminals, roamed from town to town, looting and pillaging. Smuggling and drug-trafficking rings are as old as the hills in Asia and Africa, and extant criminal organizations in Italy and Japan trace their histories back several centuries...[157]
As Lunde states, "Barbarian conquerors, whether Vandals, Goths, the Norse, Turks or Mongols are not normally thought of as organized crime groups, yet they share many features associated with thriving criminal organizations. They were for the most part non-ideological, predominantly ethnically based, used violence and intimidation, and adhered to their own codes of law."[156] In Ancient Rome, there was an infamous outlaw called Bulla Felix who organized and led a gang of up to six hundred bandits. Terrorism is linked to organized crime, but has political aims rather than solely financial ones, so there is overlap but separation between terrorism and organized crime.
Fencing in Ming and Qing China
A fence or receiver (銷贓者), was a merchant who bought and sold stolen goods. Fences were part of the extensive network of accomplices in the criminal underground of Ming and Qing China. Their occupation entailed criminal activity, but as fences often acted as liaisons between the more respectable community to the underground criminals, they were seen as living a "precarious existence on the fringes of respectable society".[158]
A fence worked alongside bandits, but in a different line of work. The network of criminal accomplices that was often acquired was essential to ensuring both the safety and the success of fences.
The path into the occupation of a fence stemmed, in a large degree, from necessity. As most fences came from the ranks of poorer people, they often took whatever work they could – both legal and illegal.[158]
Like most bandits operated within their own community, fences also worked within their own town or village. For example, in some satellite areas of the capital, military troops lived within or close to the commoner population and they had the opportunity to hold illegal trades with commoners.[159]
In areas like Baoding and Hejian, local peasants and community members not only purchased military livestock such as horses and cattle, but also helped to hide the "stolen livestock from military allured by the profits". Local peasants and community members became fences and they hid criminal activities from officials in return for products or money from these soldiers.[160]
Types of fences
Most fences were not individuals who only bought and sold stolen goods to make a living. The majority of fences had other occupations within the "polite" society and held a variety of official occupations. These occupations included laborers, coolies, and peddlers.[161] Such individuals often encountered criminals in markets in their line of work, and, recognizing a potential avenue for an extra source of income, formed acquaintances and temporary associations for mutual aid and protection with criminals.[161] In one example, an owner of a tea house overheard the conversation between Deng Yawen, a criminal and others planning a robbery and he offered to help to sell the loot for an exchange of spoils.
At times, the robbers themselves filled the role of fences, selling to people they met on the road. This may actually have been preferable for robbers in certain circumstances, because they would not have to pay the fence a portion of the spoils.
Butchers were also prime receivers for stolen animals because of the simple fact that owners could no longer recognize their livestock once butchers slaughtered them.[161] Animals were very valuable commodities within Ming China and a robber could potentially sustain a living from stealing livestock and selling them to butcher-fences.
Although the vast majority of the time, fences worked with physical stolen property, fences who also worked as itinerant barbers also sold information as a good. Itinerant barbers often amassed important sources of information and news as they traveled, and sold significant pieces of information, often to criminals in search of places to hide or individuals to rob.[161] In this way, itinerant barbers also served the role as a keeper of information that could be sold to both members of the criminal underground, as well as powerful clients in performing the function of a spy.
Fences not only sold items such as jewelry and clothing but was also involved in trafficking hostages that bandits had kidnapped. Women and children were the easiest and among the most common "objects" the fences sold. Most of the female hostages were sold to fences and then sold as prostitutes, wives or concubines. One example of human trafficking can be seen from Chen Akuei's gang who abducted a servant girl and sold her to Lin Baimao, who in turn sold her for thirty parts of silver as wives.[162] In contrast to women, who required beauty to sell for a high price, children were sold regardless of their physical appearance or family background. Children were often sold as servants or entertainers, while young girls were often sold as prostitutes.[163]
Network of connections
Like merchants of honest goods, one of the most significant tools of a fence was their network of connections. As they were the middlemen between robbers and clients, fences needed to form and maintain connections in both the "polite" society, as well as among criminals. However, there were a few exceptions in which members of the so-called "well-respected" society became receivers and harborers. They not only help bandits to sell the stolen goods but also acted as agents of bandits to collect protection money from local merchants and residents. These "part-time" fences with high social status used their connection with bandits to help themselves gain social capital as well as wealth.
It was extremely important to their occupation that fences maintained a positive relationship with their customers, especially their richer gentry clients. When some members of the local elites joined the ranks of fences, they not only protect bandits to protect their business interests, they actively took down any potential threats to their illegal profiting, even government officials. In the Zhejiang Province, the local elites not only got the provincial commissioner, Zhu Wan, dismissed from his office but also eventually "[drove] him to suicide".[164] This was possible because fences often had legal means of making a living, as well as illegal activities and could threaten to turn in bandits to the authorities.[158]
It was also essential for them to maintain a relationship with bandits. However, it was just as true that bandits needed fences to make a living. As a result, fences often held dominance in their relationship with bandits and fences could exploit their position, cheating the bandits by manipulating the prices they paid bandits for the stolen property.[158]
Safe houses
Aside from simply buying and selling stolen goods, fences often played additional roles in the criminal underground of early China. Because of the high floating population in public places such as inns and tea houses, they often became ideal places for bandies and gangs to gather to exchange information and plan for their next crime. Harborers, people who provided safe houses for criminals, often played the role of receiving stolen goods from their harbored criminals to sell to other customers.[158] Safe houses included inns, tea houses, brothels, opium dens, as well as gambling parlors and employees or owners of such institutions often functioned as harborers, as well as fences.[165] These safe houses locate in places where there are high floating population and people from all kinds of social backgrounds.
Brothels themselves helped these bandits to hide and sell stolen goods because of the special Ming Law that exempted brothels from being held responsible "for the criminal actions of their clients." Even though the government required owners of these places to report any suspicious activities, lack of enforcement from the government itself and some of the owners being fences for the bandits made an ideal safe house for bandits and gangs.
Pawnshops were also often affiliated with fencing stolen goods. The owners or employees of such shops often paid cash for stolen goods at a price a great deal below market value to bandits, who were often desperate for money, and resold the goods to earn a profit.[166]
Punishments for fences
Two different Ming Laws, the Da Ming Lü 大明律 and the Da Gao 大诰, drafted by the Hongwu Emperor Zhu Yuanzhang, sentenced fences with different penalties based on the categories and prices of the products that were stolen.
In coastal regions, illegal trading with foreigners, as well as smuggling, became a huge concern for the government during the middle to late Ming era. In order to prohibit this crime, the government passed a law in which illegal smugglers who traded with foreigners without the consent of the government would be punished with exile to the border for military service.[167]
In areas where military troops were stationed, stealing and selling military property would result in a more severe punishment. In the Jiaqing time, a case was recorded of stealing and selling military horses. The emperor himself gave direction that the thieves who stole the horses and the people who helped to sell the horses would be put on cangue and sent to labor in a border military camp.[168]
In the salt mines, the penalty for workers who stole salt and people who sold the stolen salt was the most severe. Anyone who was arrested and found guilty of stealing and selling government salt was put to death.
Nineteenth century
During the Victorian era, criminals and gangs started to form organizations which would collectively become London's criminal underworld.[169] Criminal societies in the underworld started to develop their own ranks and groups which were sometimes called families and were often made up of lower-classes and operated on pick-pocketry, prostitution, forgery and counterfeiting, commercial burglary and even money laundering schemes.[169][170] Unique also were the use of slang and argots used by Victorian criminal societies to distinguish each other, like those propagated by street gangs like the Peaky Blinders.[171][172] One of the most infamous crime bosses in the Victorian underworld was Adam Worth, who was nicknamed "the Napoleon of the criminal world" or "the Napoleon of Crime" and became the inspiration behind the popular character of Professor Moriarty.[169][173]
Organized crime in the United States first came to prominence in the Old West and historians such as Brian J. Robb and Erin H. Turner traced the first organized crime syndicates to the Coschise Cowboy Gang and the Wild Bunch.[174][175] The Cochise Cowboys, though loosely organized, were unique for their criminal operations in the Mexican border, in which they would steal and sell cattle as well smuggled contraband goods in between the countries.[176] In the Old west there were other examples of gangs that operated in ways similar to an organized crime syndicate such as the Innocents gang, the Jim Miller gang, the Soapy Smith gang, the Belle Starr gang and the Bob Dozier gang.
Twentieth century
Donald Cressey's Cosa Nostra model studied Mafia families exclusively and this limits his broader findings. Structures are formal and rational with allocated tasks, limits on entrance, and influence on the rules established for organizational maintenance and sustainability.[177][178] In this context there is a difference between organized and professional crime; there is well-defined hierarchy of roles for leaders and members, underlying rules and specific goals that determine their behavior and these are formed as a social system, one that was rationally designed to maximize profits and to provide forbidden goods. Albini saw organized criminal behavior as consisting of networks of patrons and clients, rather than rational hierarchies or secret societies.[18][19][20]
The networks are characterized by a loose system of power relations. Each participant is interested in furthering his own welfare. Criminal entrepreneurs are the patrons and they exchange information with their clients in order to obtain their support. Clients include members of gangs, local and national politicians, government officials and people engaged in legitimate business. People in the network may not directly be part of the core criminal organization. Furthering the approach of both Cressey and Albini, Ianni and Ianni studied Italian-American crime syndicates in New York and other cities.[179][180]
Kinship is seen as the basis of organized crime rather than the structures Cressey had identified; this includes fictive godparental and affinitive ties as well as those based on blood relations and it is the impersonal actions, not the status or affiliations of their members, that define the group. Rules of conduct and behavioral aspects of power and networks and roles include the following:
- family operates as a social unit, with social and business functions merged;
- leadership positions down to middle management are kinship based;
- the higher the position, the closer the kinship relationship;
- group assigns leadership positions to a central group of family members, including fictive god-parental relationship reinforcement;
- the leadership group are assigned to legal or illegal enterprises, but not both; and,
- transfer of money, from legal and illegal business, and back to illegal business is by individuals, not companies.
Strong family ties are derived from the traditions of southern Italy, where family rather than the church or state is the basis of social order and morality.
The "disorganized crime" and choice theses
One of the most important trends to emerge in criminological thinking about OC in recent years is the suggestion that it is not, in a formal sense, "organized" at all. Evidence includes lack of centralized control, absence of formal lines of communication, fragmented organizational structure. It is distinctively disorganized. For example, Seattle's crime network in the 1970s and 80s consisted of groups of businessmen, politicians and of law enforcement officers. They all had links to a national network via Meyer Lansky, who was powerful, but there was no evidence that Lansky or anyone else exercised centralized control over them.[181]
While some crime involved well-known criminal hierarchies in the city, criminal activity was not subject to central management by these hierarchies nor by other controlling groups, nor were activities limited to a finite number of objectives. The networks of criminals involved with the crimes did not exhibit organizational cohesion. Too much emphasis had been placed on the Mafia as controlling OC. The Mafia were certainly powerful but they "were part of a heterogeneous underworld, a network characterized by complex webs of relationships." OC groups were violent and aimed at making money but because of the lack of structure and fragmentation of objectives, they were "disorganized".[182][183]
Further studies showed neither bureaucracy nor kinship groups are the primary structure of organized crime; rather, the primary structures were found to lie in partnerships or a series of joint business ventures.[184][185] Despite these conclusions, all researchers observed a degree of managerial activities among the groups they studied. All observed networks and a degree of persistence, and there may be utility in focusing on the identification of organizing roles of people and events rather than the group's structure.[186][187] There may be three main approaches to understand the organizations in terms of their roles as social systems:[188]
- organizations as rational systems: Highly formalized structures in terms of bureaucracy's and hierarchy, with formal systems of rules regarding authority and highly specific goals;
- organizations as natural systems: Participants may regard the organization as an end in itself, not merely a means to some other end. Promoting group values to maintain solidarity is high on the agenda. They do not rely on profit maximization. Their perversity and violence in respect of relationships is often remarkable, but they are characterized by their focus on the connections between their members, their associates and their victims; and,
- organizations open systems: High levels of interdependence between themselves and the environment in which they operate. There is no one way in which they are organized or how they operate. They are adaptable and change to meet the demands of their changing environments and circumstances.
Organized crime groups may be a combination of all three.
International governance approach
International consensus on defining organized crime has become important since the 1970s due to its increased prevalence and impact. e.g., UN in 1976 and EU 1998. OC is "...the large scale and complex criminal activity carried on by groups of persons, however loosely or tightly organized for the enrichment of those participating at the expense of the community and its members. It is frequently accomplished through ruthless disregard of any law, including offenses against the person and frequently in connection with political corruption." (UN) "A criminal organization shall mean a lasting, structured association of two or more persons, acting in concert with a view to committing crimes or other offenses which are punishable by deprivation of liberty or a detention order of a maximum of at least four years or a more serious penalty, whether such crimes or offenses are an end in themselves or a means of obtaining material benefits and, if necessary, of improperly influencing the operation of public authorities." (UE) Not all groups exhibit the same characteristics of structure. However, violence and corruption and the pursuit of multiple enterprises and continuity serve to form the essence of OC activity.[189][190]
There are eleven characteristics from the European Commission and Europol pertinent to a working definition of organized crime. Six of those must be satisfied and the four in italics are mandatory. Summarized, they are:
- more than two people;
- their own appointed tasks;
- activity over a prolonged or indefinite period of time;
- the use discipline or control;
- perpetration of serious criminal offenses;
- operations on an international or transnational level;
- the use violence or other intimidation;
- the use of commercial or businesslike structures;
- engagement in money laundering;
- exertion of influence on politics, media, public administration, judicial authorities or the economy; and,
- motivated by the pursuit of profit and/or power,
with the Convention against Transnational Organized Crime (the Palermo Convention) having a similar definition:
- organized criminal: structured group, three or more people, one or more serious crimes, in order to obtain financial or other material benefit;
- serious crime: offense punishable by at least four years in prison; and,
- structured group: Not randomly formed but doesn't need formal structure,
Others stress the importance of power, profit and perpetuity, defining organized criminal behavior as:
- nonideological: i.e., profit driven;
- hierarchical: few elites and many operatives;
- limited or exclusive membership: maintain secrecy and loyalty of members;
- perpetuating itself: Recruitment process and policy;
- willing to use illegal violence and bribery;
- specialized division of labor: to achieve organization goal;
- monopolistic: Market control to maximize profits; and,
- has explicit rules and regulations: Codes of honor.[191]
Definitions need to bring together its legal and social elements. OC has widespread social, political and economic effects. It uses violence and corruption to achieve its ends: "OC when group primarily focused on illegal profits systematically commit crimes that adversely affect society and are capable of successfully shielding their activities, in particular by being willing to use physical violence or eliminate individuals by way of corruption."[192][193]
It is a mistake to use the term "OC" as though it denotes a clear and well-defined phenomenon. The evidence regarding OC "shows a less well-organized, very diversified landscape of organizing criminals…the economic activities of these organizing criminals can be better described from the viewpoint of 'crime enterprises' than from a conceptually unclear frameworks such as 'OC'." Many of the definitions emphasize the ‘group nature’ of OC, the ‘organization’ of its members, its use of violence or corruption to achieve its goals and its extra-jurisdictional character...OC may appear in many forms at different times and in different places. Due to the variety of definitions, there is “evident danger” in asking “what is OC?” and expecting a simple answer.[194]
The locus of power and organized crime
Some espouse that all organized crime operates at an international level, though there is currently no international court capable of trying offenses resulting from such activities (the International Criminal Court's remit extends only to dealing with people accused of offenses against humanity, e.g., genocide). If a network operates primarily from one jurisdiction and carries out its illicit operations there and in some other jurisdictions it is ‘international,' though it may be appropriate to use the term ‘transnational’ only to label the activities of a major crime group that is centered in no one jurisdiction but operating in many. The understanding of organized crime has therefore progressed to combined internationalization and an understanding of social conflict into one of power, control, efficiency risk and utility, all within the context of organizational theory. The accumulation of social, economic and political power[195] have sustained themselves as a core concerns of all criminal organizations:
- social: criminal groups seek to develop social control in relation to particular communities;
- economic: seek to exert influence by means of corruption and by coercion of legitimate and illegitimate praxis; and,
- political: criminal groups use corruption and violence to attain power and status.[196][194]
Contemporary organized crime may be very different from traditional Mafia style, particularly in terms of the distribution and centralization of power, authority structures and the concept of 'control' over one's territory and organization. There is a tendency away from centralization of power and reliance upon family ties towards a fragmentation of structures and informality of relationships in crime groups. Organized crime most typically flourishes when a central government and civil society is disorganized, weak, absent or untrustworthy.
This may occur in a society facing periods of political, economic or social turmoil or transition, such as a change of government or a period of rapid economic development, particularly if the society lacks strong and established institutions and the rule of law. The dissolution of the Soviet Union and the Revolutions of 1989 in Eastern Europe that saw the downfall of the Communist Bloc created a breeding ground for criminal organizations.
The newest growth sectors for organized crime are identity theft and online extortion. These activities are troubling because they discourage consumers from using the Internet for e-commerce. E-commerce was supposed to level the playing ground between small and large businesses, but the growth of online organized crime is leading to the opposite effect; large businesses are able to afford more bandwidth (to resist denial-of-service attacks) and superior security. Furthermore, organized crime using the Internet is much harder to trace down for the police (even though they increasingly deploy cybercops) since most police forces and law enforcement agencies operate within a local or national jurisdiction while the Internet makes it easier for criminal organizations to operate across such boundaries without detection.
In the past criminal organizations have naturally limited themselves by their need to expand, putting them in competition with each other. This competition, often leading to violence, uses valuable resources such as manpower (either killed or sent to prison), equipment and finances. In the United States, James "Whitey" Bulger, the Irish Mob boss of the Winter Hill Gang in Boston turned informant for the Federal Bureau of Investigation (FBI). He used this position to eliminate competition and consolidate power within the city of Boston which led to the imprisonment of several senior organized crime figures including Gennaro Angiulo, underboss of the Patriarca crime family. Infighting sometimes occurs within an organization, such as the Castellamarese war of 1930–31 and the Boston Irish Mob Wars of the 1960s and 1970s.
Today criminal organizations are increasingly working together, realizing that it is better to work in cooperation rather than in competition with each other (once again, consolidating power). This has led to the rise of global criminal organizations such as Mara Salvatrucha, 18th Street gang and Barrio Azteca. The American Mafia, in addition to having links with organized crime groups in Italy such as the Camorra, the 'Ndrangheta, Sacra Corona Unita and Sicilian Mafia, has at various times done business with the Irish Mob, Jewish-American organized crime, the Japanese Yakuza, Indian mafia, the Russian mafia, Thief in law and Post-Soviet Organized crime groups, the Chinese Triads, Chinese Tongs and Asian street gangs, Motorcycle Gangs and numerous White, Black and Hispanic prison and street gangs. The United Nations Office on Drugs and Crime estimated that organized crime groups held $322 billion in assets in 2005.[197]
This rise in cooperation between criminal organizations has meant that law enforcement agencies are increasingly having to work together. The FBI operates an organized crime section from its headquarters in Washington, D.C. and is known to work with other national (e.g., Polizia di Stato, Russian Federal Security Service (FSB) and the Royal Canadian Mounted Police), federal (e.g., Bureau of Alcohol, Tobacco, Firearms and Explosives, Drug Enforcement Administration, United States Marshals Service, Immigration and Customs Enforcement, United States Secret Service, US Diplomatic Security Service, United States Postal Inspection Service, U.S. Customs and Border Protection, United States Border Patrol, and the United States Coast Guard), state (e.g., Massachusetts State Police Special Investigation Unit, New Jersey State Police organized crime unit, Pennsylvania State Police organized crime unit and the New York State Police Bureau of Criminal Investigation) and city (e.g., New York City Police Department Organized Crime Unit, Philadelphia Police Department Organized crime unit, Chicago Police Organized Crime Unit and the Los Angeles Police Department Special Operations Division) law enforcement agencies.
Academic analysis
Criminal psychology
Criminal psychology is defined as the study of the intentions, behaviors, and actions of a criminal or someone who allows themselves to participate in criminal behavior. The goal is understand what is going on in the criminal's head and explain why they are doing what they are doing. This varies depending on whether the person is facing the punishment for what they did, are roaming free, or if they are punishing themselves. Criminal psychologists get called to court to explain the inside the mind of the criminal.[citation needed]
Rational choice
This theory treats all individuals as rational operators, committing criminal acts after consideration of all associated risks (detection and punishment) compared with the rewards of crimes (personal, financial etc.).[198] Little emphasis is placed on the offenders’ emotional state. The role of criminal organizations in lowering the perceptions of risk and increasing the likelihood of personal benefit is prioritized by this approach, with the organizations structure, purpose, and activity being indicative of the rational choices made by criminals and their organizers.[199]
Deterrence
This theory sees criminal behavior as reflective of an individual, internal calculation[200] by the criminal that the benefits associated with offending (whether financial or otherwise) outweigh the perceived risks.[201][202] The perceived strength, importance or infallibility of the criminal organization is directly proportional to the types of crime committed, their intensity and arguably the level of community response. The benefits of participating in organized crime (higher financial rewards, greater socioeconomic control and influence, protection of the family or significant others, perceived freedoms from 'oppressive' laws or norms) contribute greatly to the psychology behind highly organized group offending.
Social learning
Criminals learn through associations with one another. The success of organized crime groups is therefore dependent upon the strength of their communication and the enforcement of their value systems, the recruitment and training processes employed to sustain, build or fill gaps in criminal operations.[203] An understanding of this theory sees close associations between criminals, imitation of superiors, and understanding of value systems, processes and authority as the main drivers behind organized crime. Interpersonal relationships define the motivations the individual develops, with the effect of family or peer criminal activity being a strong predictor of inter-generational offending.[204] This theory also developed to include the strengths and weaknesses of reinforcement, which in the context of continuing criminal enterprises may be used to help understand propensities for certain crimes or victims, level of integration into the mainstream culture and likelihood of recidivism / success in rehabilitation.[203][205][206]
Enterprise
Under this theory, organized crime exists because legitimate markets leave many customers and potential customers unsatisfied.[47] High demand for a particular good or service (e.g., drugs, prostitution, arms, slaves), low levels of risk detection and high profits lead to a conducive environment for entrepreneurial criminal groups to enter the market and profit by supplying those goods and services.[207] For success, there must be:
- an identified market; and,
- a certain rate of consumption (demand) to maintain profit and outweigh perceived risks.[48][49]
Under these conditions competition is discouraged, ensuring criminal monopolies sustain profits. Legal substitution of goods or services may (by increasing competition) force the dynamic of organized criminal operations to adjust, as will deterrence measures (reducing demand), and the restriction of resources (controlling the ability to supply or produce to supply).[208]
Differential association
Sutherland goes further to say that deviancy is contingent on conflicting groups within society, and that such groups struggle over the means to define what is criminal or deviant within society. Criminal organizations therefore gravitate around illegal avenues of production, profit-making, protectionism or social control and attempt (by increasing their operations or membership) to make these acceptable.[203][209][210] This also explains the propensity of criminal organizations to develop protection rackets, to coerce through the use of violence, aggression and threatening behavior (at times termed 'terrorism').[211][212][213][214] Preoccupation with methods of accumulating profit highlight the lack of legitimate means to achieve economic or social advantage, as does the organization of white-collar crime or political corruption (though it is debatable whether these are based on wealth, power or both). The ability to effect social norms and practices through political and economic influence (and the enforcement or normalization of criminogenic needs) may be defined by differential association theory.
Critical criminology and sociology
Social disorganization
Social disorganization theory is intended to be applied to neighborhood level street crime,[215] thus the context of gang activity, loosely formed criminal associations or networks, socioeconomic demographic impacts, legitimate access to public resources, employment or education, and mobility give it relevance to organized crime. Where the upper- and lower-classes live in close proximity this can result in feelings of anger, hostility, social injustice and frustration.[216] Criminals experience poverty; and witness affluence they are deprived of and which is virtually impossible for them to attain through conventional means.[217] The concept of neighborhood is central to this theory, as it defines the social learning, locus of control, cultural influences and access to social opportunity experienced by criminals and the groups they form.[218] Fear of or lack of trust in mainstream authority may also be a key contributor to social disorganization; organized crime groups replicate such figures and thus ensure control over the counter-culture.[219] This theory has tended to view violent or antisocial behavior by gangs as reflective of their social disorganization rather than as a product or tool of their organization.[220]
Anomie
Sociologist Robert K. Merton believed deviance depended on society's definition of success,[221] and the desires of individuals to achieve success through socially defined avenues. Criminality becomes attractive when expectations of being able to fulfill goals (therefore achieving success) by legitimate means cannot be fulfilled.[222] Criminal organizations capitalize on states with a lack of norm by imposing criminogenic needs and illicit avenues to achieve them. This has been used as the basis for numerous meta-theories of organized crime through its integration of social learning, cultural deviance, and criminogenic motivations.[223] If crime is seen as a function of anomie,[224] organized behavior produces stability, increases protection or security, and may be directly proportional to market forces as expressed by entrepreneurship- or risk-based approaches. It is the inadequate supply of legitimate opportunities that constrains the ability for the individual to pursue valued societal goals and reduces the likelihood that using legitimate opportunities will enable them to satisfy such goals (due to their position in society).[225]
Cultural deviance
Criminals violate the law because they belong to a unique subculture - the counter-culture - their values and norms conflicting with those of the working-, middle- or upper-classes upon which criminal laws are based. This subculture shares an alternative lifestyle, language and culture, and is generally typified by being tough, taking care of their own affairs and rejecting government authority. Role models include drug dealers, thieves and pimps, as they have achieved success and wealth not otherwise available through socially-provided opportunities. It is through modeling organized crime as a counter-cultural avenue to success that such organizations are sustained.[203][226][227]
Alien conspiracy/queer ladder of mobility
The alien conspiracy theory and queer ladder of mobility theories state that ethnicity and 'outsider' status (immigrants, or those not within the dominant ethnocentric groups) and their influences are thought to dictate the prevalence of organized crime in society.[228] The alien theory posits that the contemporary structures of organized crime gained prominence during the 1860s in Sicily and that elements of the Sicilian population are responsible for the foundation of most European and North American organized crime,[229] made up of Italian-dominated crime families. Bell's theory of the 'queer ladder of mobility' hypothesized that 'ethnic succession' (the attainment of power and control by one more marginalized ethnic group over other less marginalized groups) occurs by promoting the perpetration of criminal activities within a disenfranchised or oppressed demographic. Whilst early organized crime was dominated by the Irish Mob (early 1800s), they were relatively substituted by the Sicilian Mafia and Italian-American Mafia, the Aryan Brotherhood (1960s onward), Colombian Medellín Cartel and Cali cartel (mid-1970s - 1990s), and more recently the Mexican Tijuana Cartel (late 1980s onward), Mexican Los Zetas (late 1990s to onward), the Russian Mafia (1988 onward), terrorism-related organized crime Al-Qaeda (1988 onward), the Taliban (1994 onward), and Islamic State of Iraq and the Levant (ISIL) (2010s to onward) . Many argue this misinterprets and overstates the role of ethnicity in organized crime.[230] A contradiction of this theory is that syndicates had developed long before large-scale Sicilian immigration in the 1860s, with these immigrants merely joining a widespread phenomenon of crime and corruption.[231][232][233]
Legislative frameworks and policing measures
- International
- Convention against Transnational Organized Crime (the 'Palermo Convention') - the international treaty against organized crime; includes the Protocol to Prevent, Suppress and Punish Trafficking in Persons, especially Women and Children and the Protocol against the Smuggling of Migrants by Land, Sea and Air
- Canada
- Criminal Code, RSC 1985, c C-46, ss 467.1 to 467.2 Archived 2015-10-05 at the Wayback Machine.
- China
- India
- Republic of Ireland
- Italy
- United Kingdom
- United States
- Federal Anti-Racketeering Act (the 'Hobbs Act') 1946
- Federal Wire Act 1961
- Bank Secrecy Act 1970
- Organized Crime Control Act 1970
- Title 21 of the United States Code 1970
- Continuing Criminal Enterprise (contemporary)
- Racketeer Influenced and Corrupt Organizations Act (the 'RICO Act') 1970
- Money Laundering Control Act 1986
- United States Patriot Act 2001
- Fraud Enforcement and Recovery Act of 2009
By nation
- List of criminal enterprises, gangs, and syndicates
- Timeline of organized crime
- Organized crime in Afghanistan
- Organized crime in Albania
- Organized crime in Australia
- Organized crime in Bulgaria
- Category:Organized crime in Canada
- Organized crime in China
- Organized crime in France
- Organized crime in Greece
- Organized crime in India
- Organized crime in Ireland
- Organized crime in Italy
- Organized crime in Japan
- Organized crime in Kenya
- Organized crime in Kyrgyzstan
- Organized crime in Lebanon
- Organized crime in the Netherlands
- Organized crime in Nigeria
- Organized crime in Pakistan
- Organized crime in Russia
- Organized crime in Romania
- Organized crime in Serbia
- Organized crime in South Korea
- Organized crime in Sweden
- Organized crime in Turkey
- Organized crime in Ukraine
- Organized crime in the United Kingdom
- Category:Organized crime in the United States
- Organized crime in Vietnam
References
a criminal gang, especially one involved in drug trafficking, extortion, etc.
The Mafia or a similar criminal organization[dead link]
a group of persons cooperating for unethical, illicit, or illegal purposes, as to control stock-market prices, manipulate politicians, or elude the law
a group, combination, or association of gangsters controlling organized crime or one type of crime, especially in one region of the country
thrasher 1927.
Sanchez-Jankowski (1991) gang.
DELINQUENCY, CRIME, AND SOCIAL PROCESS'.
ianni ianni gang.
abadinsky organised crime.
- Dwight (1976). "Mafia: The Prototypical Alien Conspiracy". The Annals of the American Academy of Political and Social Science. 423 (1): 75–88. doi:10.1177/000271627642300108. S2CID 145638748.
External links
- Mob Life: Gangster Kings of Crime—slideshow by Life magazine
- UNODC—United Nations Office on Drugs and Crime—sub-section dealing with organized crime worldwide
- "Organized Crime" (Archived 2010-04-25 at the Wayback Machine)—Oxford Bibliographies Online: Criminology
https://en.wikipedia.org/wiki/Organized_crime
Category:Illegal occupations
Subcategories
This category has the following 19 subcategories, out of 19 total.
-
B
- Burglars (4 C, 13 P)
C
- Contract killers (5 C, 39 P)
D
- Drug traffickers (8 C, 25 P)
G
- Gangsters (11 C, 3 P)
H
- Highwaymen (7 C, 8 P)
M
- Moonshine producers (4 P)
P
- Prostitutes (6 C, 3 P)
R
- Robbers (8 C, 18 P)
S
- Spies (11 C, 5 P)
T
- Thieves (11 C, 22 P)
V
- Vigilantes (6 C, 56 P)
Pages in category "Illegal occupations"
The following 37 pages are in this category, out of 37 total. This list may not reflect recent changes.
R
W
https://en.wikipedia.org/wiki/Category:Illegal_occupations
Train robbery is a type of robbery, in which the goal is to steal money or other valuables being carried by trains.
https://en.wikipedia.org/wiki/Train_robbery
llegal mining is mining activity that is undertaken without state permission, in particular in absence of land rights, mining licenses, and exploration or mineral transportation permits.[1]
Illegal mining can be a subsistence activity, as is the case with artisanal mining, or it can belong to large-scale organized crime,[2] spearheaded by illegal mining syndicates.[3][4] On an international level, approximately 80 percent of small-scale mining operations can be categorized as illegal.[5] Despite strategic developments towards "responsible mining," even big companies can be involved in illegal mineral digging and extraction, if only on the financing side.[6]
https://en.wikipedia.org/wiki/Illegal_mining
Sand theft or unauthorised or illegal sand mining leads to a widely unknown global example of natural and non-renewable resource depletion problem comparable in extent to global water scarcity.[1][2][3] Beach theft is illegal removal of large quantities of sand from a beach leading to full or partial disappearance of the beach. In India illegal sand mining is the country's largest organized criminal activity.[4]
https://en.wikipedia.org/wiki/Sand_theft
Sand Wars is a documentary by director Denis Delestrac and produced by Rappi Productions, La Compagnie des Taxi-Brousse, InfomAction, Arte France, with the support of The Santa Aguila Foundation.
The film premiered at the Cinéma Publicis on the Champs-Elysées in 2013 and was first broadcast in May in France and Germany (Arte), where it became the highest rated documentary for 2013.[1] A Gold Panda Award winner, Sand Wars is distributed worldwide by PBS International.
Among many other outreach victories, the film inspired the United Nations Environment Programme (UNEP) to publish a Global Environmental Alert in March 2014 titled "Sand, rarer than one thinks".[2]
https://en.wikipedia.org/wiki/Sand_Wars
Horse theft is the crime of stealing horses. A person engaged in stealing horses is known as a horse thief. Historically, punishments were often severe for horse theft, with several cultures pronouncing the sentence of death upon actual or presumed thieves. Several societies were formed in the United States to prevent horse theft and apprehend horse thieves. However, horse theft continues to occur throughout the world, as horses are stolen for their meat, for ransom, or in disputes between their owners and other persons. Horse theft today is comparable to automobile theft, a crime punishable by felony jail time.
https://en.wikipedia.org/wiki/Horse_theft
Innocent Sorcerers (Polish: Niewinni czarodzieje) is a 1960 Polish psychological romantic drama film[1] directed by Andrzej Wajda, and starring Tadeusz Łomnicki and Krystyna Stypułkowska. Its plot follows a young doctor and jazz drummer meeting a mysterious girl, who all but forces herself into his apartment where they talk of morals and love.
The film was appreciated with Diploma of Merit at the Edinburgh International Film Festival in 1961.[2] In Poland however, after its premiere Innocent Sorcerers met with criticism from both the then communist authorities and the Catholic Church. Nevertheless, since its release the film has garnered acclaim from film critics and audience, similarly to its worldwide reception to date. American filmmaker Martin Scorsese recognized the film as one of the masterpieces of Polish cinema and in 2013 he selected it for screening in the United States, Canada and United Kingdom as part of the Martin Scorsese Presents: Masterpieces of Polish Cinema festival of Polish films.[3]
https://en.wikipedia.org/wiki/Innocent_Sorcerers
Innocence is a lack of guilt, with respect to any kind of crime, or wrongdoing. In a legal context, innocence is to the lack of legal guilt of an individual, with respect to a crime. In other contexts, it is a lack of experience.
https://en.wikipedia.org/wiki/Innocence
Ignorance can mean a lack of knowledge and understanding. Deliberate ignorance is a culturally-induced phenomenon, the study of which is called agnotology.
The word "ignorant" is an adjective that describes a person in the state of being unaware, or even cognitive dissonance and other cognitive relation, and can describe individuals who are unaware of important information or facts. Ignorance can appear in three different types: factual ignorance (absence of knowledge of some fact), object ignorance (unacquaintance with some object), and technical ignorance (absence of knowledge of how to do something).[1]
https://en.wikipedia.org/wiki/Ignorance
Quota may refer to:
Economics
- Import quota, a trade restriction on the quantity of goods imported into a country
- Market Sharing Quota, an economic system used in Canadian agriculture
- Milk quota, a quota on milk production in Europe
- Individual fishing quota, a quota on allowable catch
Politics
- Gender quota (disambiguation)
- Racial quota, numerical requirements for hiring, promoting, admitting or graduating members of a particular racial group
- Ticket quota, directives by police departments for their officers to deliver a predetermined number of summons
- Quotas in electoral systems
Music and entertainment
- The Quota (Jimmy Heath album) or the title song, 1961
- The Quota (Red Garland album), an 1973 song.
- Quota (EP), by Eleventyseven, an 2011 song.
- Quota (film) - a 2020 Indian film.
Other
- Disk quota, a limit that restricts disk file system usage in computing
- Quota International, a service organization
See also
- Quotaism, the concept of organising society by a quota system
- All pages with titles containing quota
https://en.wikipedia.org/wiki/Quota
A disk quota is a limit set by a system administrator that restricts certain aspects of file system usage on modern operating systems. The function of using disk quotas is to allocate limited disk space in a reasonable way.
https://en.wikipedia.org/wiki/Disk_quota
Old Pension Scheme (OPS) in India was abolished as a part of pension reforms by Union Government. Repealed from 1 January 2004, it had a defined-benefit (DB) pension of half the Last Pay Drawn (LPD) at the time of retirement along with components like Dearness Allowances (DA) etc. OPS was a unfunded pension scheme financed on a pay-as-you-go (PAYG) basis in which current revenues of the government funded the pension benefit for its retired employees. Old Pension Scheme was replaced by a restructured defined-contribution (DC) pension scheme called the National Pension System.[1]
The Union Government's pension liabilities in Budget Estimate 2022-2023 on account of Old Pension Scheme for existing retirees is Rupees 2.07 lakh crore.[2] The cost of pension for all State Government's combined Budget Estimate 2022-2023 is 4,63,436.9 Crores.[3]
https://en.wikipedia.org/wiki/Old_Pension_Scheme
The National Pension System (NPS) is a defined-contribution pension system in India regulated by Pension Fund Regulatory and Development Authority (PFRDA) which is under the jurisdiction of Ministry of Finance of the Government of India. National Pension System Trust (NPS Trust) established by PFRDA is the registered owner of all assets under this scheme.[1] National Pension System, like PPF and EPF is an EEE (Exempt-Exempt-Exempt) instrument in India where the entire corpus escapes tax at maturity and entire pension withdrawal amount is tax-free.[2]
https://en.wikipedia.org/wiki/National_Pension_System
Magnet is a URI scheme that defines the format of magnet links, a de facto standard for identifying files (URN) by their content, via cryptographic hash value rather than by their location.
Although magnet links can be used in a number of contexts, they are particularly useful in peer-to-peer file sharing networks because they allow resources to be referred to without the need for a continuously available host, and can be generated by anyone who already has the file, without the need for a central authority to issue them. This makes them popular for use as "guaranteed" search terms within the file sharing community where anyone can distribute a magnet link to ensure that the resource retrieved by that link is the one intended, regardless of how it is retrieved.
https://en.wikipedia.org/wiki/Magnet_URI_scheme
A Uniform Resource Identifier (URI) is a unique sequence of characters that identifies a logical or physical resource used by web technologies. URIs may be used to identify anything, including real-world objects, such as people and places, concepts, or information resources such as web pages and books. Some URIs provide a means of locating and retrieving information resources on a network (either on the Internet or on another private network, such as a computer filesystem or an Intranet); these are Uniform Resource Locators (URLs). A URL provides the location of the resource. A URI identifies the resource by name at the specified location or URL. Other URIs provide only a unique name, without a means of locating or retrieving the resource or information about it, these are Uniform Resource Names (URNs). The web technologies that use URIs are not limited to web browsers. URIs are used to identify anything described using the Resource Description Framework (RDF), for example, concepts that are part of an ontology defined using the Web Ontology Language (OWL), and people who are described using the Friend of a Friend vocabulary would each have an individual URI.
https://en.wikipedia.org/wiki/Uniform_Resource_Identifier
Russian organized crime or Russian mafia (Russian: росси́йская ма́фия, tr. rossíyskaya máfiya, IPA: [rɐˈsʲijskəjə ˈmafʲɪjə],[2] Russian: ру́сская ма́фия, tr. rússkaya máfiya, IPA: [ˈruskəjə ˈmafʲɪjə]), otherwise known as Bratva (Russian: братва́, tr. bratvá, IPA: [brɐtˈva], lit. 'brotherhood'), is a collective of various organized crime elements originating in the former Soviet Union. The initialism OPG is Organized Criminal (prestupnaya in Russian) Group, used to refer to any of the Russian mafia groups, sometimes modified with a specific name, e.g. Orekhovskaya OPG. Sometimes the initialism is translated and OCG is used.
Organized crime in Russia began in the Russian Empire, but it was not until the Soviet era that vory v zakone ("thieves-in-law") emerged as leaders of prison groups in forced labor camps, and their honor code became more defined. With the end of World War II, the death of Joseph Stalin, and the fall of the Soviet Union, more gangs emerged in a flourishing black market, exploiting the unstable governments of the former republics. Louis Freeh, former director of the FBI, said that the Russian mafia posed the greatest threat to US national security in the mid-1990s.[3]
In 2012, there were as many as 6,000 groups,[4] with more than 200 of them having a global reach. Criminals of these various groups are either former prison members, corrupt officials and business leaders, people with ethnic ties, or people from the same region with shared criminal experiences and leaders.[clarification needed][5] In December 2009, Timur Lakhonin, the head of the Russian National Central Bureau of Interpol, stated "Certainly, there is crime involving our former compatriots abroad, but there is no data suggesting that an organized structure of criminal groups comprising former Russians exists abroad",[6] while in August 2010, Alain Bauer, a French criminologist, said that it "is one of the best structured criminal organizations in Europe, with a quasi-military operation."[7] Since the 1980s, the Russian mafia has been among the most powerful, dangerous and feared criminal organizations in the world, and as of 2022, the organization remains to be among the world's largest, deadliest and most powerful crime syndicates. The FBI has called them a "criminal superpower".
The Russian mafia is similar to the Italian Mafia in many ways, the groups organizations and structures follow a similar model. The two groups also share a similar portfolio of criminal activity. The highly publicized Italian Mafia is believed to have inspired early criminal groups in Russia to form Mafia-like organizations, eventually spawning their own version. The Russian mafia, however, differed from the Italians due to their environment. The level of political corruption and arms sales in a post-Soviet Russia allowed for massive expansion and incorporation of many government officials into the crime syndicates. The Russians also dabbled in uranium trading, stolen from the Soviet nuclear program, and human trafficking.[8]
https://en.wikipedia.org/wiki/Russian_mafia
A state is a centralized political organization that imposes and enforces rules over a population within a territory. There is no undisputed definition of a state.[1][2] One widely used definition comes from the German sociologist Max Weber: a "state" is a polity that maintains a monopoly on the legitimate use of violence, although other definitions are not uncommon.[3][4] Absence of a state does not preclude the existence of a society, such as stateless societies like the Haudenosaunee Confederacy that "do not have either purely or even primarily political institutions or roles".[5] The level of governance of a state, government being considered to form the fundamental apparatus of contemporary states,[6][7] is used to determine whether it has failed.[8]
https://en.wikipedia.org/wiki/State_(polity)
Taxonomy is the practice and science of categorization or classification.
https://en.wikipedia.org/wiki/Taxonomy
Self-organized criticality (SOC) is a property of dynamical systems that have a critical point as an attractor. Their macroscopic behavior thus displays the spatial or temporal scale-invariance characteristic of the critical point of a phase transition, but without the need to tune control parameters to a precise value, because the system, effectively, tunes itself as it evolves towards criticality.
The concept was put forward by Per Bak, Chao Tang and Kurt Wiesenfeld ("BTW") in a paper[1] published in 1987 in Physical Review Letters, and is considered to be one of the mechanisms by which complexity[2] arises in nature. Its concepts have been applied across fields as diverse as geophysics,[3][4] physical cosmology, evolutionary biology and ecology, bio-inspired computing and optimization (mathematics), economics, quantum gravity, sociology, solar physics, plasma physics, neurobiology[5][6][7][8] and others.
SOC is typically observed in slowly driven non-equilibrium systems with many degrees of freedom and strongly nonlinear dynamics. Many individual examples have been identified since BTW's original paper, but to date there is no known set of general characteristics that guarantee a system will display SOC.
https://en.wikipedia.org/wiki/Self-organized_criticality
The National Rural Employment Generation Scheme (NREGS) is an employment scheme in India for providing 100 days guaranteed wage employment for all employment seekers above 18 years of age and willing to do work. The scheme came into force on 1995 in 199 districts in India and extended to another 130 districts later.
https://en.wikipedia.org/wiki/National_Rural_Employment_Generation_Scheme
The Russian Laundromat was a scheme to move $20–80 billion out of Russia from 2010 to 2014 through a network of global banks, many of them in Moldova and Latvia.[1][2] The Guardian reported that around 500 people were suspected of being involved, many of whom were wealthy Russians.[3] The money laundering scheme was uncovered by Global Laundromat, an investigation.[4] The New Yorker says that that operation was known as "The Russian Laundromat," "The Global Laundromat," or "The Moldovan Scheme."[5] The Herald wrote that the scheme is "thought to be the world's biggest and most elaborate money-laundering scheme."[6]
https://en.wikipedia.org/wiki/Russian_Laundromat
The American Mafia,[7][8][9] commonly referred to in North America as the Italian American Mafia, the Mafia, or the Mob,[7][8][9] is a highly organized Italian American criminal society and organized crime group. The organization is often referred to by its members as Cosa Nostra (Italian pronunciation: [ˈkɔːza ˈnɔstra, ˈkɔːsa -], "our thing" or "this thing of ours") and by the American government as La Cosa Nostra (LCN). The organization's name is derived from the original Mafia or Cosa Nostra, the Sicilian Mafia, with "American Mafia" originally referring simply to Mafia groups from Sicily operating in the United States, as the organization initially emerged as an offshoot of the Sicilian Mafia formed by Italian immigrants in the United States. However, the organization gradually evolved into a separate entity partially independent of the original Mafia in Sicily, and it eventually encompassed or absorbed other Italian immigrant and Italian American gangsters and Italian American crime groups (such as the American Camorra) active in the United States and Canada that were not of Sicilian origin. In North America, it is often colloquially referred to as the Italian Mafia or Italian Mob, though these terms may also apply to the separate yet related Sicilian Mafia or other organized crime groups in Italy or ethnic Italian crime groups in other countries.
The Mafia in the United States emerged in impoverished Italian immigrant neighborhoods or ghettos in New York's East Harlem (or Italian Harlem), the Lower East Side, and Brooklyn; also emerging in other areas of the Northeastern United States and several other major metropolitan areas (such as New Orleans[10] and Chicago) during the late 19th century and early 20th century, following waves of Italian immigration especially from Sicily and other regions of Southern Italy. It has its roots in the Sicilian Mafia but is a separate organization in the United States. Campanian, Calabrian and other Italian criminal groups in the U.S., as well as independent Italian American criminals, eventually merged with Sicilian Mafiosi to create the modern pan-Italian Mafia in North America. Today, the American Mafia cooperates in various criminal activities with Italian organized crime groups, such as the Sicilian Mafia, the Camorra of Campania and the 'Ndrangheta of Calabria. The most important unit of the American Mafia is that of a "family," as the various criminal organizations that make up the Mafia are known. Despite the name of "family" to describe the various units, they are not familial groupings.[11]
The Mafia is currently most active in the Northeastern United States, with the heaviest activity in New York, Philadelphia, Baltimore, New Jersey, Pittsburgh, Buffalo, and New England, in areas such as Boston, Providence, and Hartford. It also remains heavily active in Chicago and has a significant and powerful presence in other Midwestern metropolitan areas such as Kansas City, Detroit, Milwaukee, Cleveland, and St. Louis. Outside of these areas, the Mafia is also very active in Florida, Las Vegas, and Los Angeles. Mafia families have previously existed to a greater extent and continue to exist to a lesser extent in Northeastern Pennsylvania, Dallas, Denver, New Orleans, Rochester, San Francisco, San Jose, Seattle, and Tampa. While some of the regional crime families in these areas may no longer exist to the same extent as before, descendants have continued to engage in criminal operations, while consolidation has occurred in other areas, with rackets being controlled by more powerful crime families from nearby cities.[12] At the Mafia's peak, there were at least 26 cities around the United States with Cosa Nostra families, with many more offshoots and associates in other cities. There are five main New York City Mafia families, known as the Five Families: the Gambino, Lucchese, Genovese, Bonanno, and Colombo families. The Italian American Mafia has long dominated organized crime in the United States. Each crime family has its own territory and operates independently, while nationwide coordination is overseen by the Commission, which consists of the bosses of each of the strongest families. Though the majority of the Mafia's activities are contained to the Northeastern United States and Chicago, they continue to dominate organized crime in the United States, despite the increasing numbers of other crime groups.[13][14]
https://en.wikipedia.org/wiki/American_Mafia
Funding is the act of providing resources to finance a need, program, or project. While this is usually in the form of money, it can also take the form of effort or time from an organization or company. Generally, this word is used when a firm uses its internal reserves to satisfy its necessity for cash, while the term financing is used when the firm acquires capital from external sources.[citation needed]
Sources of funding include credit, venture capital, donations, grants, savings, subsidies, and taxes. Fundings such as donations, subsidies, and grants that have no direct requirement for return of investment are described as "soft funding" or "crowdfunding". Funding that facilitates the exchange of equity ownership in a company for capital investment via an online funding portal per the Jumpstart Our Business Startups Act (alternately, the "JOBS Act of 2012") (U.S.) is known as equity crowdfunding.
Funds can be allocated for either short-term or long-term purposes.
https://en.wikipedia.org/wiki/Funding
Lift irrigation is a method of irrigation in which water is not transported by natural flow, (as in gravity-fed canal) but is lifted with pumps or surge pools etc.[1]
https://en.wikipedia.org/wiki/Lift_irrigation
A library classification is a system of organization of knowledge by which library resources are arranged and ordered systematically. Library classifications are a notational system that represents the order of topics in the classification and allows items to be stored in that order. Library classification systems group related materials together, typically arranged as a hierarchical tree structure. A different kind of classification system, called a faceted classification[1] system, is also widely used, which allows the assignment of multiple classifications to an object, enabling the classifications to be ordered in many ways.
https://en.wikipedia.org/wiki/Library_classification
A pension (/ˈpɛnʃən/, from Latin pensiō, "payment") is a fund into which a sum of money is added during an employee's employment years and from which payments are drawn to support the person's retirement from work in the form of periodic payments. A pension may be a "defined benefit plan", where a fixed sum is paid regularly to a person, or a "defined contribution plan", under which a fixed sum is invested that then becomes available at retirement age.[1] Pensions should not be confused with severance pay; the former is usually paid in regular amounts for life after retirement, while the latter is typically paid as a fixed amount after involuntary termination of employment before retirement.
The terms "retirement plan" and "superannuation" tend to refer to a pension granted upon retirement of the individual.[2] Retirement plans may be set up by employers, insurance companies, the government, or other institutions such as employer associations or trade unions. Called retirement plans in the United States, they are commonly known as pension schemes in the United Kingdom and Ireland and superannuation plans (or super[3]) in Australia and New Zealand. Retirement pensions are typically in the form of a guaranteed life annuity, thus insuring against the risk of longevity.
A pension created by an employer for the benefit of an employee is commonly referred to as an occupational or employer pension. Labor unions, the government, or other organizations may also fund pensions. Occupational pensions are a form of deferred compensation, usually advantageous to employee and employer for tax reasons. Many pensions also contain an additional insurance aspect, since they often will pay benefits to survivors or disabled beneficiaries. Other vehicles (certain lottery payouts, for example, or an annuity) may provide a similar stream of payments.
The common use of the term pension is to describe the payments a person receives upon retirement, usually under pre-determined legal or contractual terms. A recipient of a retirement pension is known as a pensioner or retiree.
https://en.wikipedia.org/wiki/Pension
https://en.wikipedia.org/wiki/Category:1953_births
One Rank One Pension (OROP), or "same pension, for same rank, for same length of service, irrespective of the date of retirement", is a longstanding demand of the Indian armed forces and veterans.[1]: p 1 The demand for pay-pension equity, which underlies the OROP concept, was provoked by the exparte decision by the Indira Gandhi-led Indian National Congress (INC) government, in 1973, two years after the historic victory in the 1971 Bangladesh war.[2] : paras 10.4 and 11.2 [3]
https://en.wikipedia.org/wiki/One_Rank,_One_Pension
https://en.wikipedia.org/wiki/Structure
https://en.wikipedia.org/wiki/Adjustment
https://en.wikipedia.org/wiki/Addition
https://en.wikipedia.org/wiki/Hash_table
https://en.wikipedia.org/wiki/Session_Initiation_Protocol
https://en.wikipedia.org/wiki/Pseudolaw
https://en.wikipedia.org/wiki/White-collar_crime#Organized_transnational_crime
https://en.wikipedia.org/wiki/Mathematics#Areas_of_mathematics
https://en.wikipedia.org/wiki/1898_in_organized_crime
https://en.wikipedia.org/wiki/1926_in_organized_crime
https://en.wikipedia.org/wiki/List_of_counties_in_Texas
https://en.wikipedia.org/wiki/Light-dependent_reactions
https://en.wikipedia.org/wiki/Point_shaving
This is a list of grading systems used by countries of the world, primarily within the fields of secondary education and university education, organized by continent with links to specifics in numerous entries.
https://en.wikipedia.org/wiki/Grading_systems_by_country
In ontology, the theory of categories concerns itself with the categories of being: the highest genera or kinds of entities according to Amie Thomasson.[1] To investigate the categories of being, or simply categories, is to determine the most fundamental and the broadest classes of entities.[2] A distinction between such categories, in making the categories or applying them, is called an ontological distinction. Various systems of categories have been proposed, they often include categories for substances, properties, relations, states of affairs or events.[3][4] A representative question within the theory of categories might articulate itself, for example, in a query like, "Are universals prior to particulars?"
https://en.wikipedia.org/wiki/Theory_of_categories
https://en.wikipedia.org/wiki/FBI_Index
Architectural scheme
The Sistine Chapel is about 35 m (118 ft) long and 14 m (46 ft) wide,[13] with the ceiling rising to about 20 m (66 ft) above the main floor.[82][83] The vault is of quite a complex design and it is unlikely that it was originally intended to have such elaborate decoration.
The chapel walls have three horizontal tiers with six windows in the upper tier down each side. There were also two windows at each end, but these have been closed up above the altar when Michelangelo's Last Judgment was painted, obliterating two lunettes. Between the windows are large pendentives which support the vault. Between the pendentives are triangularly shaped arches or spandrels cut into the vault above each window. Above the height of the pendentives, the ceiling slopes gently without much deviation from the horizontal.[7]
The first element in the scheme of painted architecture is a definition of the real architectural elements by accentuating the lines where spandrels and pendentives intersect with the curving vault. Michelangelo painted these as decorative courses that look like sculpted stone mouldings.[j] These have two repeating motifs, a formula common in Classical architecture.[k] Here, one motif is the acorn, the symbol of the family of both Pope Sixtus IV, who built the chapel, and Pope Julius II, who commissioned Michelangelo's work.[84][l] The other motif is the scallop shell, one of the symbols of the Madonna, to whose Assumption the chapel was dedicated in 1483.[85][m] The crown of the wall then rises above the spandrels, to a strongly projecting painted cornice that runs right around the ceiling, separating the pictorial areas of the biblical scenes from the figures of prophets, sibyls, and ancestors, who literally and figuratively support the narratives. Ten broad painted cross-ribs of travertine cross the ceiling and divide it into alternately wide and narrow pictorial spaces, a grid that gives all the figures their defined place.[86]
A great number of small figures are integrated with the painted architecture, their purpose apparently purely decorative. These include pilasters with capitals supported by pairs of infant telamones, rams' skulls are placed at the apex of each spandrel like bucrania; bronze nude figures in varying poses, hiding in the shadows, propped between the spandrels and the ribs like animated bookends; and more putti, both clothed and unclothed, strike a variety of poses as they support the nameplates of the Prophets and Sibyls.[87] Above the cornice and to either side of the smaller scenes are an array of medallions, or round shields. They are framed by a total of 20 more figures, the so-called ignudi, which are not part of the architecture but sit on plinths, their feet planted convincingly on the fictive cornice. Pictorially, the ignudi appear to occupy a space between the narrative spaces and the space of the chapel itself.
https://en.wikipedia.org/wiki/Sistine_Chapel_ceiling#Architectural_scheme

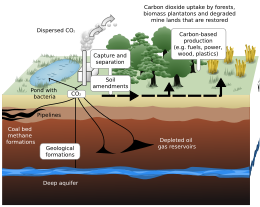




















No comments:
Post a Comment