Texas Peace Officers' Memorial
| Artist | Linda Johnson |
|---|---|
| Year | 1999 |
| Location | Austin, Texas, United States |
| 30.275256°N 97.739046°WCoordinates: 30.275256°N 97.739046°W | |
The Texas Peace Officers' Memorial is an outdoor monument commemorating law enforcement and corrections officers who died in service since August 5, 1823, installed on the Texas State Capitol grounds in Austin, Texas, United States. The memorial was designed by Linda Johnson and erected by the Texas Commission on Law Enforcement and Texas State Preservation Board in 1999. It features a granite obelisk on a base with a Texas Lone Star, as well as inscribed names along granite walls of those who died since Stephen F. Austin commissioned the Texas Peace Officers, or the Texas Ranger Division.[1]
See also
References
- "Texas Peace Officers' Memorial". Texas State Preservation Board. Archived from the original on September 3, 2018. Retrieved September 4, 2018.
External links
 Media related to Texas Peace Officers' Memorial at Wikimedia Commons
Media related to Texas Peace Officers' Memorial at Wikimedia Commons
https://en.wikipedia.org/wiki/Texas_Peace_Officers%27_Memorial
The secretary problem demonstrates a scenario involving optimal stopping theory[1][2] that is studied extensively in the fields of applied probability, statistics, and decision theory. It is also known as the marriage problem, the sultan's dowry problem, the fussy suitor problem, the googol game, and the best choice problem.
The basic form of the problem is the following: imagine an administrator who wants to hire the best secretary out of rankable applicants for a position. The applicants are interviewed one by one in random order. A decision about each particular applicant is to be made immediately after the interview. Once rejected, an applicant cannot be recalled. During the interview, the administrator gains information sufficient to rank the applicant among all applicants interviewed so far, but is unaware of the quality of yet unseen applicants. The question is about the optimal strategy (stopping rule) to maximize the probability of selecting the best applicant. If the decision can be deferred to the end, this can be solved by the simple maximum selection algorithm of tracking the running maximum (and who achieved it), and selecting the overall maximum at the end. The difficulty is that the decision must be made immediately.
The shortest rigorous proof known so far is provided by the odds algorithm. It implies that the optimal win probability is always at least (where e is the base of the natural logarithm), and that the latter holds even in a much greater generality. The optimal stopping rule prescribes always rejecting the first applicants that are interviewed and then stopping at the first applicant who is better than every applicant interviewed so far (or continuing to the last applicant if this never occurs). Sometimes this strategy is called the stopping rule, because the probability of stopping at the best applicant with this strategy is about already for moderate values of . One reason why the secretary problem has received so much attention is that the optimal policy for the problem (the stopping rule) is simple and selects the single best candidate about 37% of the time, irrespective of whether there are 100 or 100 million applicants.
https://en.wikipedia.org/wiki/Secretary_problem
https://en.wikipedia.org/wiki/Optimal_stopping
In finance, the style or family of an option is the class into which the option falls, usually defined by the dates on which the option may be exercised. The vast majority of options are either European or American (style) options. These options—as well as others where the payoff is calculated similarly—are referred to as "vanilla options". Options where the payoff is calculated differently are categorized as "exotic options". Exotic options can pose challenging problems in valuation and hedging.
https://en.wikipedia.org/wiki/Option_style
Money creation, or money issuance, is the process by which the money supply of a country, or of an economic or monetary region,[note 1] is increased. In most modern economies, money creation is controlled by the central banks. Money issued by central banks is termed base money. Central banks can increase the quantity of base money directly, by engaging in open market operations. However, the majority of the money supply is created by the commercial banking system in the form of bank deposits. Bank loans issued by commercial banks that practice fractional reserve banking expands the quantity of broad money to more than the original amount of base money issued by the central bank.
https://en.wikipedia.org/wiki/Money_creation
https://en.wikipedia.org/wiki/Resource
https://en.wikipedia.org/wiki/Men
https://en.wikipedia.org/wiki/Reconstructive_surgery
https://en.wikipedia.org/wiki/Embryo
https://en.wikipedia.org/wiki/Progeny
https://en.wikipedia.org/wiki/Rescue
https://en.wikipedia.org/wiki/clone
https://en.wikipedia.org/wiki/cloak
https://en.wikipedia.org/wiki/amnestic-drug
https://en.wikipedia.org/wiki/implant
https://en.wikipedia.org/wiki/distance-incapacitation-weapon
https://en.wikipedia.org/wiki/non-lethal-weapon
https://en.wikipedia.org/wiki/jammer
https://en.wikipedia.org/wiki/Reserve
https://en.wikipedia.org/wiki/animals
https://en.wikipedia.org/wiki/book
https://en.wikipedia.org/wiki/database
https://en.wikipedia.org/wiki/memory
https://en.wikipedia.org/wiki/veterinarian
https://en.wikipedia.org/wiki/engineer
https://en.wikipedia.org/wiki/mathematician
https://en.wikipedia.org/wiki/land
https://en.wikipedia.org/wiki/plants
https://en.wikipedia.org/wiki/water
https://en.wikipedia.org/wiki/underground
https://en.wikipedia.org/wiki/forest
https://en.wikipedia.org/wiki/train
https://en.wikipedia.org/wiki/bomb
https://en.wikipedia.org/wiki/transport
https://en.wikipedia.org/wiki/defense
https://en.wikipedia.org/wiki/communication
https://en.wikipedia.org/wiki/language
https://en.wikipedia.org/wiki/account
https://en.wikipedia.org/wiki/euthanasia
https://en.wikipedia.org/wiki/computer_printer_fax_telephone
https://en.wikipedia.org/wiki/paper
https://en.wikipedia.org/wiki/tree
https://en.wikipedia.org/wiki/rock
https://en.wikipedia.org/wiki/diamond
https://en.wikipedia.org/wiki/sand
https://en.wikipedia.org/wiki/glass
https://en.wikipedia.org/wiki/mirror
https://en.wikipedia.org/wiki/Reactor
https://en.wikipedia.org/wiki/power_plant
https://en.wikipedia.org/wiki/nuclear_reactor
https://en.wikipedia.org/wiki/observable_universe
https://en.wikipedia.org/wiki/sensation_perception_cognition
https://en.wikipedia.org/wiki/church
https://en.wikipedia.org/wiki/cathedral
https://en.wikipedia.org/wiki/doctrine
https://en.wikipedia.org/wiki/law
https://en.wikipedia.org/wiki/regulation
https://en.wikipedia.org/wiki/law_enforcement
https://en.wikipedia.org/wiki/measure
https://en.wikipedia.org/wiki/space_time
https://en.wikipedia.org/wiki/count
https://en.wikipedia.org/wiki/calibration
https://en.wikipedia.org/wiki/correction
https://en.wikipedia.org/wiki/error
https://en.wikipedia.org/wiki/discrimination
https://en.wikipedia.org/wiki/identification
https://en.wikipedia.org/wiki/detection
https://en.wikipedia.org/wiki/deception
https://en.wikipedia.org/wiki/air_earth_water_fire
https://en.wikipedia.org/wiki/salt
https://en.wikipedia.org/wiki/treasure
https://en.wikipedia.org/wiki/containment
https://en.wikipedia.org/wiki/contamination
https://en.wikipedia.org/wiki/reparition_remediation_restitution_rectification
https://en.wikipedia.org/wiki/amendment
https://en.wikipedia.org/wiki/amnesty_mercy_forgiveness_sanction_debarrment
https://en.wikipedia.org/wiki/exoneration_vindication_amelioriation_mitigation_ etc.
https://en.wikipedia.org/wiki/remediation_reconstruction_rebuild_reformation
https://en.wikipedia.org/wiki/prohibition_violation_infarction_accident_incident_expungement_etc.
https://en.wikipedia.org/wiki/restriction_limitation_corruption_etc.
https://en.wikipedia.org/wiki/eradication_operation_implementation_installation_etc.
https://en.wikipedia.org/wiki/exculpation_fallacy_logic_bias_system_error_tamper_obstruction_statute_civil-wrong_escalation_privilege_discretion_declinationary_arraignment_precedence_group-team-impersonation_personification_authority_impersonation-of-authority_patient_subject_hostage_attained-men-women-principle_price-of-doctrine-politics_failed-operation_etc.
https://en.wikipedia.org/wiki/obstruction-of-justice_witness-tamper-etc.
https://en.wikipedia.org/wiki/process-of-impersonation-no-equity-social-systems-and-displacement-interest-cycle-personation-etc.
https://en.wikipedia.org/wiki/limitation
https://en.wikipedia.org/wiki/us-code_statute_of_limitations
https://en.wikipedia.org/wiki/SS_SF_USAF_etc.
https://en.wikipedia.org/wiki/law-enforcement
A cease and desist letter is a document sent to an individual or business to stop alleged illegal activity. The phrase "cease and desist" is a legal doublet, made up of two near-synonyms. The letter may warn that, if the recipient does not discontinue specified conduct, or take certain actions, by deadlines set in the letter, that party, i.e., the letter's recipient, may be sued.[1][2] When issued by a public authority, a cease and desist letter, being "a warning of impending judicial enforcement",[3] is most appropriately called a "cease and desist order".
https://en.wikipedia.org/wiki/Cease_and_desist
A legal doublet is a standardized phrase used frequently in English legal language consisting of two or more words that are irreversible binomials and frequently synonyms, usually connected by "and", such as "null and void". The order of the words cannot be reversed, as it would be particularly unusual to ask someone to desist and cease or to have property owned clear and free; these common legal phrases are universally known as cease and desist and free and clear.
https://en.wikipedia.org/wiki/Legal_doublet
In law, void means of no legal effect. An action, document, or transaction which is void is of no legal effect whatsoever: an absolute nullity—the law treats it as if it had never existed or happened. The term void ab initio, which means "to be treated as invalid from the outset", comes from adding the Latin phrase ab initio (from the beginning) as a qualifier. For example, in many jurisdictions where a person signs a contract under duress, that contract is treated as being void ab initio. The frequent combination "null and void" is a legal doublet.
The term is frequently used in contradistinction to the term "voidable" and "unenforceable".
https://en.wikipedia.org/wiki/Void_(law)
Nullification, in United States constitutional history, is a legal theory that a state has the right to nullify, or invalidate, any federal laws which they deem unconstitutional with respect to the United States Constitution (as opposed to the state's own constitution). There are similar theories that any officer,[1] jury,[2] or individual[3] may do the same. The theory of state nullification has never been legally upheld by federal courts,[4] although jury nullification has.[2]
https://en.wikipedia.org/wiki/Nullification_(U.S._Constitution)
The null coalescing operator (called the Logical Defined-Or operator in Perl) is a binary operator that is part of the syntax for a basic conditional expression in several programming languages, including C#,[1] PowerShell as of version 7.0.0,[2] Perl as of version 5.10,[3] Swift,[4] and PHP 7.0.0.[5] While its behavior differs between implementations, the null coalescing operator generally returns the result of its left-most operand if it exists and is not null, and otherwise returns the right-most operand. This behavior allows a default value to be defined for cases where a more specific value is not available.
In contrast to the ternary conditional if operator used as x ? x : y, but like the binary Elvis operator used as x ?: y,
the null coalescing operator is a binary operator and thus evaluates
its operands at most once, which is significant if the evaluation of x has side-effects.
https://en.wikipedia.org/wiki/Null_coalescing_operator
In linguistic typology, a null-subject language is a language whose grammar permits an independent clause to lack an explicit subject; such a clause is then said to have a null subject.
In the principles and parameters framework, the null subject is controlled by the pro-drop parameter, which is either on or off for a particular language.[citation needed]
Typically, null-subject languages express person, number, and/or gender agreement with the referent on the verb, rendering a subject noun phrase redundant.
For example, in Italian the subject "she" can be either explicit or implicit:
Borja
Borja
non
not
vuole
want
pagare.
[to-]pay
"Borja does not want to pay."
The subject "(s)he" of the second sentence is only implied in Italian. English and French, on the other hand, require an explicit subject in this sentence.
Of the thousands of languages in the world, a considerable number are null-subject languages, from a wide diversity of unrelated language families. They include Albanian, Arabic, Basque, Berber, Bengali, Catalan/Valencian, Chinese, Estonian, Finnish, Galician, Gujarati, Greek, Hebrew, Hindi, Hungarian, Italian, Romanian, Japanese, Korean, Maltese, Nepali, Persian, Portuguese, Punjabi, Sindhi, Slavic languages, Spanish, Tamil and the Turkic languages, as well as most languages related to these, and many others still. In fact, it is rather the absence of pronoun dropping that is an areal feature of Standard Average European, including French, German, and English.[1]
https://en.wikipedia.org/wiki/Null-subject_language
The nullification crisis was a sectional political crisis in the United States in 1832 and 1833, during the presidency of Andrew Jackson, which involved a confrontation between the state of South Carolina and the federal government. It ensued after South Carolina declared the federal Tariffs of 1828 and 1832 unconstitutional and therefore null and void within the sovereign boundaries of the state. However, courts at the state and federal level, including the U.S. Supreme Court, repeatedly have rejected the theory of nullification by states.[1][2]
https://en.wikipedia.org/wiki/Nullification_crisis
Null symbol may refer to:
- Null character, U+0000, U+2400 "symbol for null" (␀), a single-character glyph "NUL"
- Null sign (∅), the empty set
- Null (SQL) (ω), a special marker and keyword
NULLin SQL - Empty string (λ, Λ, or ε), in formal language theory
See also
https://en.wikipedia.org/wiki/Null_symbol
In radio electronics, a null is a direction in an antenna's radiation pattern where the antenna radiates almost no radio waves, so the far field signal strength is a local minimum. Nulls occur because different parts of an antenna radiate radio waves of different phase. In directions at which the antenna radiates equal amplitude radio waves of opposite phase, the radio waves cancel, resulting in little or no radio power being radiated in that direction. In other directions the radio waves from different parts of the antenna are in phase and reinforce, resulting in a maximum signal strength in the radiation pattern, called a lobe.
In transmitting antennas designed to provide broad coverage nulls can be a problem, preventing reception in a given area. Null fill in the vertical plane is used to prevent this.
https://en.wikipedia.org/wiki/Null_(radio)
In mathematics, the word null (from German: null[citation needed] meaning "zero", which is from Latin: nullus meaning "none") is often associated with the concept of zero or the concept of nothing.[1][2] It is used in varying context from "having zero members in a set" (e.g., null set)[3] to "having a value of zero" (e.g., null vector).[4]
In a vector space, the null vector is the neutral element of vector addition; depending on the context, a null vector may also be a vector mapped to some null by a function under consideration (such as a quadratic form coming with the vector space, see null vector, a linear mapping given as matrix product or dot product,[4] a seminorm in a Minkowski space, etc.). In set theory, the empty set, that is, the set with zero elements, denoted "{}" or "∅", may also be called null set.[3][5] In measure theory, a null set is a (possibly nonempty) set with zero measure.
A null space of a mapping is the part of the domain that is mapped into the null element of the image (the inverse image of the null element). For example, in linear algebra, the null space of a linear mapping, also known as kernel, is the set of vectors which map to the null vector under that mapping.
In statistics, a null hypothesis is a proposition that no effect or relationship exists between populations and phenomena. It is the hypothesis which is presumed true—unless statistical evidence indicates otherwise.[6]
https://en.wikipedia.org/wiki/Null_(mathematics)
Null modem is a communication method to directly connect two DTEs (computer, terminal, printer, etc.) using an RS-232 serial cable. The name stems from the historical use of RS-232 cables to connect two teleprinter devices or two modems in order to communicate with one another; null modem communication refers to using a crossed-over RS-232 cable to connect the teleprinters directly to one another without the modems. It is also used to serially connect a computer to a printer, since both are DTE, and is known as a Printer Cable.
The RS-232 standard is asymmetric as to the definitions of the two ends of the communications link, assuming that one end is a DTE and the other is a DCE, e.g. a modem. With a null modem connection the transmit and receive lines are crosslinked. Depending on the purpose, sometimes also one or more handshake lines are crosslinked. Several wiring layouts are in use because the null modem connection is not covered by the RS-232 standard.
https://en.wikipedia.org/wiki/Null_modem
A teleprinter (teletypewriter, teletype or TTY) is an electromechanical device that can be used to send and receive typed messages through various communications channels, in both point-to-point and point-to-multipoint configurations. Initially they were used in telegraphy, which developed in the late 1830s and 1840s as the first use of electrical engineering,[1] though teleprinters were not used for telegraphy until 1887 at the earliest.[2] The machines were adapted to provide a user interface to early mainframe computers and minicomputers, sending typed data to the computer and printing the response. Some models could also be used to create punched tape for data storage (either from typed input or from data received from a remote source) and to read back such tape for local printing or transmission.
https://en.wikipedia.org/wiki/Teleprinter
A fax modem enables a computer to transmit and receive documents as faxes on a telephone line. A fax modem is like a data modem but is designed to transmit and receive documents to and from a fax machine or another fax modem. Some, but not all, fax modems do double duty as data modems. As with other modems, fax modems can be internal or external. Internal fax modems are often called fax boards.
In the early 1990s small business PCs commonly had a PC-based fax/modem card and fax software (typically WinFax Pro). Largely replaced by email, PC-based faxing with a fax/modem declined at the turn of the century. Where faxing from a PC is required there are a number of Internet-based faxing alternatives. Where businesses still had one or more traditional fax machines churning out pages, they were usually outnumbered by PCs processing E-mail.
https://en.wikipedia.org/wiki/Fax_modem
Infiltration may refer to:
Science, medicine, and engineering
- Infiltration (hydrology), downward movement of water into soil
- Infiltration (HVAC), a heating, ventilation, and air conditioning term for air leakage into buildings
- Infiltration (medical), the diffusion or accumulation of substances or cells not normal to it or in amounts in excess of the normal
- Infiltration/Inflow, leakage of groundwater into sanitary sewers
Other uses
- Entryism, the infiltration by a political organisation of another, usually larger, organisation
- In espionage, using double agents to join an enemy organization
- Infiltration tactics, tactics developed by the German army in early 1915 that broke the trench-warfare stalemate on the western front
- Urban exploration, exploring parts of towns, etc. which are normally off-limits
- Infiltration (zine), a popular urban exploration zine/website created by Jeff Chapman (Ninjalicious)
- Seon-Woo Lee (born 1985), professional electronic sports players, specializing in fighting games, who plays under the alias Infiltration
- Infiltration (2017 film), a Canadian film
- Infiltration (2022 film), Russian war drama film
See also
https://en.wikipedia.org/wiki/Infiltration
Infiltration is the diffusion or accumulation (in a tissue or cells) of foreign substances in amounts excess of the normal. The material collected in those tissues or cells is called infiltrate.
https://en.wikipedia.org/wiki/Infiltration_(medical)
Rebuild may refer to:
Music
Albums
- Rebuild (The Letter Black album), a 2013 album by The Letter Black
- Rebuild, a 2005 album by Verse
Songs
- "Rebuild" (song), by Matt Thiessen from Relient K, Dustin Ruth and Switchfoot
- "Rebuild", a song by Son Lux, composed by Ryan Lott, from We Are Rising
Other
- Rebuild, a 2014 Green Lantern Corps comic book by Robert Venditti, DC Comics
- "Rebuild", a 2014 episode of Mistresses with Alyssa Milano
See also
- Rebuild of Evangelion, a 2007 Japanese animated film series
- Build. Destroy. Rebuild., album by Hanni El Khatib
- Remanufacturing
- Refurbishment (disambiguation)
https://en.wikipedia.org/wiki/Rebuild
Rescue comprises responsive operations that usually involve the saving of life, or the urgent treatment of injuries after an accident or a dangerous situation.
https://en.wikipedia.org/wiki/Rescue
Containerization is a system of intermodal freight transport using intermodal containers (also called shipping containers, or ISO containers).[1] Containerization, also referred as container stuffing or container loading, is the process of unitization of cargoes in exports. Containerization is the predominant form of unitization of export cargoes, as opposed to other systems such as the barge system or palletization.[2] The containers have standardized dimensions. They can be loaded and unloaded, stacked, transported efficiently over long distances, and transferred from one mode of transport to another—container ships, rail transport flatcars, and semi-trailer trucks—without being opened. The handling system is completely mechanized so that all handling is done with cranes[3] and special forklift trucks. All containers are numbered and tracked using computerized systems.
https://en.wikipedia.org/wiki/Containerization
https://en.wikipedia.org/wiki/OS-level_virtualization
https://en.wikipedia.org/wiki/Container_revolution_(pottery)
Progeny may refer to:
- A genetic descendant or offspring
- Progeny Linux Systems, a defunct company which provided Linux platform technology
- Progeny (Stargate Atlantis), an episode of the television series Stargate Atlantis
- Progeny – a song on the Celtic Frost album Monotheist
- Progenies of the Great Apocalypse, a 2003 song by Dimmu Borgir
- The Progeny Of Flies – an album by Andrew Liles and Daniel Menche
- Progeny (film), a 1998 movie about an alien abduction
- Progeny, a short story from author Philip K. Dick
- The Progeny, a title occasionally used to refer to Sophocles' lost play, the Epigoni
- Progeny: Seven Shows from Seventy-Two, a 14-CD live box set from the English rock band Yes with a highlight set named Progeny: Highlights from Seventy-Two.
- "Progeny" (Legends of Tomorrow), an episode of Legends of Tomorrow
https://en.wikipedia.org/wiki/Progeny
https://en.wikipedia.org/wiki/United_States_Code
|
|
|
|
|
|
|
|
|
|
In the United States, human trafficking tends to occur around international travel hubs with large immigrant populations, notably in California, Texas, and Georgia. Those trafficked include young children, teenagers, men, and women; victims can be domestic citizens or foreign nationals.
Under federal law (18 USC § 1589), it is a crime to make people work by use of force, coercion, or fear. U.S. State Department's Office to Monitor and Combat Trafficking in Persons placed the country in "Tier 1" in 2017.[1]
On April 11, 2018, U.S. President Donald Trump signed the Stop Enabling Sex Traffickers Act into law to close websites that enable crime and prosecute their owners and users.[2]
https://en.wikipedia.org/wiki/Human_trafficking_in_the_United_States
https://en.wikipedia.org/wiki/Anti-Trafficking_in_Persons_Act_of_2003
The lost children of Francoism (Spanish: niños perdidos del franquismo, niños robados por el franquismo; Catalan: nens perduts del franquisme, nens furtats pel franquisme; Galician: nenos do franquismo, pícaros roubados polo Franquismo) were the children abducted from Republican parents, who were either in jail or had been assassinated by Nationalist troops, during the Spanish Civil War and Francoist Spain.[1] The kidnapped children were sometimes also victims of child trafficking and illegal adoption.[2] The numbers of stolen children are highly speculative; these figures may include children who became orphaned as a result of the Civil War (1936-1939) and, therefore, do not fall under the same category as children taken away from their parents by the regime after the war for political or social reasons. Children who were stolen or adopted by families during or immediately after the war may have been victims of either side in the conflict. The issue has been highly ideologized in recent years as the political environment in Spain has become highly polarized.
https://en.wikipedia.org/wiki/Lost_children_of_Francoism
https://en.wikipedia.org/wiki/Global_Slavery_Index
https://en.wikipedia.org/wiki/Peon
https://en.wikipedia.org/wiki/Abolitionism
https://en.wikipedia.org/wiki/Thirteenth_Amendment_to_the_United_States_Constitution
https://en.wikipedia.org/wiki/American_Anti-Slavery_Society
https://en.wikipedia.org/wiki/Corwin_Amendment
https://en.wikipedia.org/wiki/Slavery_in_Canada
https://www.law.cornell.edu/uscode/text/18/part-I/chapter-77
https://en.wikipedia.org/wiki/Semen
https://en.wikipedia.org/wiki/Child_abduction
https://en.wikipedia.org/wiki/Slave_breeding_in_the_United_States
https://en.wikipedia.org/wiki/Sperm_theft
https://en.wikipedia.org/wiki/Origin_of_language
https://en.wikipedia.org/wiki/List_of_Batman_family_enemies
Childbirth in ancient Rome was dangerous for both the mother and the child. Mothers usually would rely on religious superstition to avoid death. Certain customs such as lying in bed after childbirth and using plants and herbs as relief were also practiced. Midwives assisted the mothers in birth. Once children were born they would not be given a name until 8 or 9 days after their birth. The number depended on if they were male or female. Once the days had past, the child would be gifted a name and a bulla during a ceremony. Once a child reached the age of 1, they would gain legal privileges which could lead to citizenship. Children 7 and under were considered infants, and were under the care of women. Children were expected to help with housework from age 8 until they reached adulthood at age 12 for girls, or 14 for boys. Children would often have a variety of toys to play with. If a child died they could be buried or cremated. Some would be commemorated in Roman religious tradition.
https://en.wikipedia.org/wiki/Childhood_in_ancient_Rome
Baby Jesus theft is the theft of figurines of the infant Jesus from outdoor public and private nativity displays during the Christmas season. It is an "enduring (and illegal) practice" according to New York Times journalist Katie Rogers, "believed to be part of a yearly tradition, often carried out by bored teenagers looking for an easy prank."[1] Sometimes these are stolen for resale, other times the associated pranks are more involved and include dropping it off somewhere else.[2]
The prevalence of such thefts has caused some owners of outdoor manger scenes to protect their property with GPS devices or surveillance cameras, or to removing baby Jesus from the displays outside of specific requests or public showings.[3] Occasionally the figurines are returned.[4]
https://en.wikipedia.org/wiki/Baby_Jesus_theft
The Comedy of Errors is one of William Shakespeare's early plays. It is his shortest and one of his most farcical comedies, with a major part of the humour coming from slapstick and mistaken identity, in addition to puns and word play. It has been adapted for opera, stage, screen and musical theatre numerous times worldwide. In the centuries following its premiere, the play's title has entered the popular English lexicon as an idiom for "an event or series of events made ridiculous by the number of errors that were made throughout".[1]
https://en.wikipedia.org/wiki/The_Comedy_of_Errors
Alien abduction (also called abduction phenomenon, alien abduction syndrome, or UFO abduction) refers to the phenomenon of people reporting the experience of being kidnapped and subjected to physical and psychological experimentation by an alien figure.[1] People claiming to have been abducted are usually called "abductees"[2] or "experiencers". Most scientists and mental health professionals explain these experiences by factors such as suggestibility (e.g. false memory syndrome), sleep paralysis, deception, and psychopathology.[3] Skeptic Robert Sheaffer sees similarity between some of the aliens described by abductees and those depicted in science fiction films, in particular Invaders From Mars (1953).[4]
https://en.wikipedia.org/wiki/Alien_abduction
Prohibition of forced sterilization and forced abortion
The Istanbul convention, the first legally binding instrument in Europe in the field of violence against women and domestic violence,[30] prohibits forced sterilization and forced abortion:[31]
Article 39 – Forced abortion and forced sterilisation
- Parties shall take the necessary legislative or other measures to ensure that the following intentional conducts are criminalised:
- a performing an abortion on a woman without her prior and informed consent;
- b performing surgery which has the purpose or effect of terminating a woman’s capacity to naturally reproduce without her prior and informed consent or understanding of the procedure
https://en.wikipedia.org/wiki/Reproductive_rights#Prohibition_of_forced_sterilization_and_forced_abortion
Euthanasia (from Greek: εὐθανασία, lit. 'good death': εὖ, eu, 'well, good' + θάνατος, thanatos, 'death') is the practice of intentionally ending life to eliminate pain and suffering.[1][2]
Different countries have different euthanasia laws. The British House of Lords select committee on medical ethics defines euthanasia as "a deliberate intervention undertaken with the express intention of ending a life, to relieve intractable suffering".[3] In the Netherlands and Belgium, euthanasia is understood as "termination of life by a doctor at the request of a patient".[4] The Dutch law, however, does not use the term 'euthanasia' but includes the concept under the broader definition of "assisted suicide and termination of life on request".[5]
https://en.wikipedia.org/wiki/Euthanasia
https://en.wikipedia.org/wiki/Death
Smuggling is the illegal transportation of objects, substances, information or people, such as out of a house or buildings, into a prison, or across an international border, in violation of applicable laws or other regulations. More broadly, social scientists define smuggling as the purposeful movement across a border in contravention to the relevant legal frameworks.[2]
There are various motivations to smuggle. These include the participation in illegal trade, such as in the drug trade, illegal weapons trade, prostitution, human trafficking, kidnapping, exotic wildlife trade, art theft, blood diamonds, heists, chop shops, illegal immigration or illegal emigration, tax evasion, import/export restrictions, providing contraband to prison inmates, or the theft of the items being smuggled.
Smuggling is a common theme in literature, from Bizet's opera Carmen to the James Bond spy books (and later films) Diamonds Are Forever and Goldfinger.
https://en.wikipedia.org/wiki/Smuggling
Human trafficking is the trade of humans for the purpose of forced labour, sexual slavery, or commercial sexual exploitation.[1] Human trafficking can occur within a country or trans-nationally. It is distinct from people smuggling, which is characterized by the consent of the person being smuggled.
Human trafficking is condemned as a violation of human rights by international conventions, but legal protection varies globally. The practice has millions of victims around the world.
https://en.wikipedia.org/wiki/Human_trafficking
Slave raiding is a military raid for the purpose of capturing people and bringing them from the raid area to serve as slaves. Once seen as a normal part of warfare, it is nowadays widely considered a crime.[citation needed] Slave raiding has occurred since antiquity. Some of the earliest surviving written records of slave raiding come from Sumer (in present-day Iraq). Kidnapping and prisoners of war was the most common source of African slaves, although indentured servitude or punishment also resulted in slavery.[1][2]
The many alternative methods of obtaining human beings to work in indentured or other involuntary conditions, as well as technological and cultural changes, have made slave raiding rarer.[citation needed]
https://en.wikipedia.org/wiki/Slave_raiding
Slave breeding was the practice in slave states of the United States of slave owners to systematically force the reproduction of slaves to increase their profits.[1] It included coerced sexual relations between male slaves and women or girls, forced pregnancies of female slaves, and favoring women or young girls who could produce a relatively large number of children.[1] The objective was to increase the number of slaves without incurring the cost of purchase, and to fill labor shortages caused by the abolition of the Atlantic slave trade.[2]
https://en.wikipedia.org/wiki/Slave_breeding_in_the_United_States
Blackbirding is the coercion of people through deception or kidnapping to work as slaves or poorly paid labourers in countries distant from their native land. The practice took place on a large scale with the taking of people indigenous to the numerous islands in the Pacific Ocean during the 19th and 20th centuries. These blackbirded people were called Kanakas or South Sea Islanders. They were taken from places such as Papua New Guinea, the Solomon Islands, Vanuatu, Niue, Easter Island, the Gilbert Islands, Tuvalu, Fiji, and the islands of the Bismarck Archipelago amongst others.
https://en.wikipedia.org/wiki/Blackbirding
The Turkish Abductions (Icelandic: Tyrkjaránið) were a series of slave raids by pirates from Northwest Africa that took place in Iceland in the summer of 1627.[1]
The pirates came from the cities of Algiers and Salé.[2] They raided Grindavík, the East Fjords, and Vestmannaeyjar.[1] About 50 people were killed[1] and close to 400 captured and sold into slavery.[1] A ransom was eventually paid, 9 to 18 years later,[3] for the return of 50 individuals.[1]
The label "Turkish" does not refer to Turkey; at the time it was a general term for all Muslims in the Mediterranean region since the majority were a part of the Ottoman Empire.[2] During the 17th century, the majority of those called "Turks" in Algeria, were European Christians that had converted to Islam.[4]
https://en.wikipedia.org/wiki/Turkish_Abductions
The Barbary slave trade involved slave markets in the Barbary States. European slaves were acquired by Barbary pirates in slave raids on ships and by raids on coastal towns from Italy to the Netherlands, Ireland and the southwest of Britain, as far north as Iceland and into the Eastern Mediterranean.
The Ottoman Eastern Mediterranean was the scene of intense piracy.[1] As late as the 18th century, piracy continued to be a "consistent threat to maritime traffic in the Aegean".[2]
https://en.wikipedia.org/wiki/Barbary_slave_trade
Theft is the act of taking another person's property or services without that person's permission or consent with the intent to deprive the rightful owner of it.[1][2][3] The word theft is also used as a synonym or informal shorthand term for some crimes against property, such as larceny, robbery,[1] embezzlement, extortion, blackmail, or receiving stolen property.[2] In some jurisdictions, theft is considered to be synonymous with larceny,[4][5] while in others, theft is defined more narrowly.[6] Someone who carries out an act of theft may be described as a "thief" (PL: thieves).[7]
Theft is the name of a statutory offence in California, Canada, England and Wales, Hong Kong,[8] Northern Ireland, the Republic of Ireland,[9] and the Australian states of South Australia[10] and Victoria.[11]
https://en.wikipedia.org/wiki/Theft
Possession of stolen goods is a crime in which an individual has bought, been given, or acquired stolen goods.
In many jurisdictions, if an individual has accepted possession of goods (or property) and knew they were stolen, then the individual may be charged with a crime, depending on the value of the stolen goods, and the goods are returned to the original owner. If the individual did not know the goods were stolen, then the goods are returned to the owner and the individual is not prosecuted. However, it can be difficult to prove or disprove a suspect's knowledge that the goods were stolen.
https://en.wikipedia.org/wiki/Possession_of_stolen_goods
The Salmon Act 1986 is a United Kingdom Act of Parliament which outlines legislation that covers legal and illegal matter within the salmon farming and fishing industries. Among the provisions in the Act, it makes it illegal to "handle salmon in suspicious circumstances",[1] which is defined in law as when one believes, or could reasonably believe, that salmon has been illegally fished or that salmon—that has come from an illegal source—has been received, retained, removed, or disposed of.
https://en.wikipedia.org/wiki/Salmon_Act_1986#Handling_Salmon_in_Suspicious_Circumstances
Extraordinary rendition is a euphemism for state-sponsored forcible abduction in another jurisdiction and transfer to a third state. The phrase usually refers to a United States-led program used during the War on Terror,[1] which had the purpose of circumventing the source country's laws on interrogation, detention, extradition and/or torture. Extraordinary rendition is a type of extraterritorial abduction, but not all extraterritorial abductions include transfer to a third country.
https://en.wikipedia.org/wiki/Extraordinary_rendition
Impressment, colloquially "the press" or the "press gang", is the taking of men into a military or naval force by compulsion, with or without notice. European navies of several nations used forced recruitment by various means. The large size of the British Royal Navy in the Age of Sail meant impressment was most commonly associated with Great Britain and Ireland. It was used by the Royal Navy in wartime, beginning in 1664 and during the 18th and early 19th centuries as a means of crewing warships, although legal sanction for the practice can be traced back to the time of Edward I of England. The Royal Navy impressed many merchant sailors, as well as some sailors from other, mostly European, nations. People liable to impressment were "eligible men of seafaring habits between the ages of 18 and 55 years". Non-seamen were sometimes impressed as well, though rarely. In addition to the Royal Navy's use of impressment, the British Army also experimented with impressment from 1778 to 1780.
https://en.wikipedia.org/wiki/Impressment
A conscription crisis is a public dispute about a policy of conscription, or mandatory service in the military,[1] known in US English as a "draft". A dispute can become a crisis when submission to military service becomes highly controversial and popular revolt ensues. From the point of view of military officials, the crisis is one of supply; where they may claim to lack enough troops to accomplish a military objective, and have, to some degree, lost control of their political ability to enforce existing conscription law.
When conscripted soldiers are sent to foreign wars that do not directly affect the security of the nation, or under pretexts and contexts that are otherwise controversial, conscription has historically been highly politically contentious within democracies.
https://en.wikipedia.org/wiki/Conscription_crisis
A tiger kidnapping or tiger robbery involves two separate crimes. The first crime usually involves an abduction of a person or something someone highly values. Instead of demanding money, the captors demand that a second crime be committed on their behalf. The second crime could be anything from robbery, murder, to planting a bomb.[1] A person or item held hostage is kept by the captors until their demands are met. The goal of the captors is to have their risky/dirty work performed by another person. The victims of a crime like this are less likely to report to authorities since they just committed a crime themselves.[2][3]
https://en.wikipedia.org/wiki/Tiger_kidnapping
Horse theft is the crime of stealing horses. A person engaged in stealing horses is known as a horse thief. Historically, punishments were often severe for horse theft, with several cultures pronouncing the sentence of death upon actual or presumed thieves. Several societies were formed in the United States to prevent horse theft and apprehend horse thieves. However, horse theft continues to occur throughout the world, as horses are stolen for their meat, for ransom, or in disputes between their owners and other persons. Horse theft today is comparable to automobile theft, a crime punishable by felony jail time.
https://en.wikipedia.org/wiki/Horse_theft
https://en.wikipedia.org/wiki/Category:Animal_theft
https://en.wikipedia.org/wiki/Category:Property_crimes
A home invasion, also called a hot prowl burglary, is a sub-type of burglary (or in some jurisdictions, a separately defined crime) in which an offender unlawfully enters into a building residence while the occupants are inside.[1] The overarching intent of a hot prowl burglary can be theft, robbery, assault, sexual assault, murder, kidnapping, or another crime, either by stealth or direct force.[2][3][4] Hot prowl burglaries are considered especially dangerous by law enforcement because of the potential for a violent confrontation between the occupant and the offender.[5]
https://en.wikipedia.org/wiki/Home_invasion
In criminal law, a conspiracy is an agreement between two or more persons to commit a crime at some time in the future.[1] Criminal law in some countries or for some conspiracies may require that at least one overt act be undertaken in furtherance of that agreement, to constitute an offense. There is no limit to the number participating in the conspiracy and, in most countries, the plan itself is the crime, so there is no requirement that any steps have been taken to put the plan into effect (compare attempts which require proximity to the full offense). For the purposes of concurrence, the actus reus is a continuing one and parties may join the plot later and incur joint liability and conspiracy can be charged where the co-conspirators have been acquitted or cannot be traced. Finally, repentance by one or more parties does not affect liability (unless, in some cases, it occurs before the parties have committed overt acts) but may reduce their sentence.
An unindicted co-conspirator, or unindicted conspirator, is a person or entity that is alleged in an indictment to have engaged in conspiracy, but who is not charged in the same indictment. Prosecutors choose to name persons as unindicted co-conspirators for a variety of reasons including grants of immunity, pragmatic considerations, and evidentiary concerns.
https://en.wikipedia.org/wiki/Criminal_conspiracy
Piracy is an act of robbery or criminal violence by ship or boat-borne attackers upon another ship or a coastal area, typically with the goal of stealing cargo and other valuable goods. Those who conduct acts of piracy are called pirates, vessels used for piracy are pirate ships. The earliest documented instances of piracy were in the 14th century BC, when the Sea Peoples, a group of ocean raiders, attacked the ships of the Aegean and Mediterranean civilisations. Narrow channels which funnel shipping into predictable routes have long created opportunities for piracy,[1] as well as for privateering and commerce raiding. Historic examples include the waters of Gibraltar, the Strait of Malacca, Madagascar, the Gulf of Aden, and the English Channel, whose geographic structures facilitated pirate attacks.[2][3] The term piracy generally refers to maritime piracy, although the term has been generalized to refer to acts committed on land,[4] in the air, on computer networks, and (in science fiction) outer space. Piracy usually excludes crimes committed by the perpetrator on their own vessel (e.g. theft), as well as privateering, which implies authorization by a state government.
https://en.wikipedia.org/wiki/Piracy
Grave robbery, tomb robbing, or tomb raiding is the act of uncovering a grave, tomb or crypt to steal commodities. It is usually perpetrated to take and profit from valuable artefacts or personal property.[n 1] A related act is body snatching, a term denoting the contested or unlawful taking of a body (seldom from a grave), which can be extended to the unlawful taking of organs alone.
Grave robbing has caused great difficulty to the studies of archaeology, art history, and history.[1][2] Countless precious grave sites and tombs have been robbed before scholars were able to examine them. In any way, the archaeological context and the historical and anthropological information are destroyed:
Looting obliterates the memory of the ancient world and turns its highest artistic creations into decorations, adornments on a shelf, divorced from historical context and ultimately from all meaning.[3]
Grave robbers who are not caught usually sell relatively modern items anonymously and artifacts on the black market. Those intercepted, in a public justice domain, are inclined to deny their guilt. Though some artifacts may make their way to museums or scholars, the majority end up in private collections.[4]
https://en.wikipedia.org/wiki/Grave_robbery
Extrinsic fraud is fraud that induces one not to present a case in court or deprives one of the opportunity to be heard or is not involved in the actual issues.[1] More broadly, it is defined as:
fraudulent acts which keep a person from obtaining information about his/her rights to enforce a contract or getting evidence to defend against a lawsuit. This could include destroying evidence or misleading an ignorant person about the right to sue. Extrinsic fraud is distinguished from intrinsic fraud, which is the fraud that is the subject of a lawsuit.[2]
Extrinsic fraud often involves fraud on the court, but may arise in other contexts. Extrinsic fraud does not mean merely lying or perjury, nor misrepresentations, nor intrinsic fraud, nor "to matters that could have been raised during the divorce proceeding."[3] It must involve "collateral ... circumstances" such as:
- "bribery of a judge or juror,"
- "fabrication of evidence by an attorney,"
- "preventing another party's witness from appearing,"
- "intentionally failing to join a necessary party," or
- "misleading another party into thinking a continuance had been granted...."[3]
The U.S. Supreme Court distinguished extrinsic fraud from intrinsic fraud in the 1878 case United States v. Throckmorton. Where, "by reason of something done by the successful party to a suit, there was in fact no adversary trial or decision of the issue in the case", an unsuccessful litigant is entitled to equitable relief from the judgement thus obtained, or a new trial if the fraud prevented that from happening.[4]
Examples
Family law
Extrinsic fraud may be claimed in family law and domestic relations cases. For example, paternity cases are sometimes the subject of extrinsic fraud; the classic case is when a man is encouraged to sign an acknowledgment that he is the father of a newborn baby, thus giving up his right to contest the matter in a filiation action.[5][6]
In Love v. Love, the Nevada Supreme Court ruled that extrinsic fraud had led the putative father to sign an admission against his interest, thus allowing the court to grant equitable relief to undo the fraud.[7] It also may occur when a man fails to appear in court when a paternity suit is filed against him, thus resulting in a default judgment due to the fraud by his "paramour".[8]
In such cases, there is a high burden of proof (typically moral certainty or beyond a reasonable doubt) of the petitioner to prove the intrinsic fraud, because of the state's interest "in the best interests of the child" to ensure that every child has a father. That is called paternity by estoppel, in which the putative father is actually prevented from proving he is not the father due to the high standard of evidence necessary as a matter of law.[citation needed]
Other examples
Extrinsic fraud may occur in real estate transactions or financing, such as when a lender forces a homeowner to lose their real property in a foreclosure through acts of fraud.[9]
A lawyer who intentionally keeps information from their client about an upcoming hearing or trial could be held responsible for extrinsic fraud, as well as being subject to disciplinary action and a legal malpractice lawsuit.[10]
It is at least theoretically possible for a court to enjoin a criminal proceeding, but unlikely.[11] A writ of habeas corpus or writ of error coram nobis may be possible as well.
See also
References
- "Equity Jurisdiction: Enjoining Execution of Criminal Judgment: Extrinsic and Intrinsic Fraud", California Law Review, Vol. 11, No. 4 (May, 1923), pp. 279-282, found atJSTOR website. Retrieved September 15, 2008.
External links
https://en.wikipedia.org/wiki/Extrinsic_fraud
A statute of frauds is a form of statute requiring that certain kinds of contracts be memorialized in writing, signed by the party against whom they are to be enforced, with sufficient content to evidence the contract.[1][2]
https://en.wikipedia.org/wiki/Statute_of_frauds
https://en.wikipedia.org/wiki/United_States_Code
https://en.wikipedia.org/wiki/Language
https://en.wikipedia.org/wiki/history
https://en.wikipedia.org/wiki/account
https://en.wikipedia.org/wiki/code
https://en.wikipedia.org/wiki/definition_homonym_operations
https://en.wikipedia.org/wiki/schemes_interpretation_education-compulsory-usa
Neonatal infant abduction and prenatal fetal abduction are the earliest ages of child abduction, when child is expansively defined as a viable baby before birth (usually a few months before the typical time for birth) through the age of majority (the age at which a young person is legally recognized as an adult). In addition, embryo theft and even oocyte misappropriation in reproductive medical settings have been legalistically construed as child abduction.[20][21][22]
https://en.wikipedia.org/wiki/Child_abduction
https://en.wikipedia.org/w/index.php?search=amnestic+drug&title=Special%3ASearch&ns0=1
Drug-induced amnesia is amnesia caused by drugs. Amnesia may be therapeutic for medical treatment or for medical procedures, or it may be a side-effect of a drug, such as alcohol, or certain medications for psychiatric disorders, such as benzodiazepines.[1] It is seen also with slow acting parenteral general anaesthetics.
https://en.wikipedia.org/wiki/Drug-induced_amnesia
https://en.wikipedia.org/wiki/Euthanasia
https://en.wikipedia.org/wiki/Nuclear_winter
https://en.wikipedia.org/wiki/Schutzstaffel
A brain transplant or whole-body transplant is a procedure in which the brain of one organism is transplanted into the body of another organism. It is a procedure distinct from head transplantation, which involves transferring the entire head to a new body, as opposed to the brain only. Theoretically, a person with complete organ failure could be given a new and functional body while keeping their own personality, memories, and consciousness through such a procedure. Neurosurgeon Robert J. White has grafted the head of a monkey onto the headless body of another monkey. EEG readings showed the brain was later functioning normally. Initially, it was thought to prove that the brain was an immunologically privileged organ, as the host's immune system did not attack it at first,[1] but immunorejection caused the monkey to die after nine days.[2] Brain transplants and similar concepts have also been explored in various forms of science fiction.
https://en.wikipedia.org/wiki/Brain_transplant
Implant can refer to:
Medicine
- Implant (medicine), or specifically:
Alternative
- Alien implants
- Extraocular implant
- Implant (body modification)
- Implant (thought insertion)
- Microchip implant (animal) (human)
- The Implant, a television episode of Seinfeld
See also
https://en.wikipedia.org/wiki/Implant
An artificial organ is a human made organ device or tissue that is implanted or integrated into a human — interfacing with living tissue — to replace a natural organ, to duplicate or augment a specific function or functions so the patient may return to a normal life as soon as possible.[1] The replaced function does not have to be related to life support, but it often is. For example, replacement bones and joints, such as those found in hip replacements, could also be considered artificial organs.[2][3]
Implied by definition, is that the device must not be continuously tethered to a stationary power supply or other stationary resources such as filters or chemical processing units. (Periodic rapid recharging of batteries, refilling of chemicals, and/or cleaning/replacing of filters would exclude a device from being called an artificial organ.)[4] Thus, a dialysis machine, while a very successful and critically important life support device that almost completely replaces the duties of a kidney, is not an artificial organ.
https://en.wikipedia.org/wiki/Artificial_organ
https://en.wikipedia.org/wiki/Embryo
https://en.wikipedia.org/wiki/Artificial_white_blood_cells
https://en.wikipedia.org/wiki/Gene_therapy
https://en.wikipedia.org/wiki/human-genetic-engineering
https://en.wikipedia.org/wiki/Genetic_algorithm
https://en.wikipedia.org/wiki/Reconstructive_surgery
https://en.wikipedia.org/wiki/Reconstructive_memory
https://en.wikipedia.org/wiki/nightmare
https://en.wikipedia.org/wiki/dream
https://en.wikipedia.org/wiki/flashbulb_memory
https://en.wikipedia.org/wiki/waking-dream
https://en.wikipedia.org/wiki/lucid-dream
https://en.wikipedia.org/wiki/vision
https://en.wikipedia.org/wiki/imagery
https://en.wikipedia.org/wiki/Transceiver
https://en.wikipedia.org/wiki/Receiver
Organ theft is the forcible removal of a person's organs to be used as transplants and sold in black market. The pop culture image of organ theft involving a drugged traveller waking up in a bathtub full of ice is an urban legend; in reality, cases of organ theft involve traffickers coercing poor people, war crimes, and thefts in a hospital setting.[1] It is also a commonly used trope in science fiction.[2]
https://en.wikipedia.org/wiki/Organ_theft
https://en.wikipedia.org/wiki/Clone
https://en.wikipedia.org/wiki/Sample
https://en.wikipedia.org/wiki/Material
https://en.wikipedia.org/wiki/Part
https://en.wikipedia.org/wiki/Component
https://en.wikipedia.org/w/index.php?search=blank+gene&title=Special%3ASearch&ns0=1
https://en.wikipedia.org/w/index.php?search=genetic+reconstruction&title=Special%3ASearch&ns0=1
The urbilaterian (from German ur- 'original') is the hypothetical last common ancestor of the bilaterian clade, i.e., all animals having a bilateral symmetry.
https://en.wikipedia.org/wiki/Urbilaterian
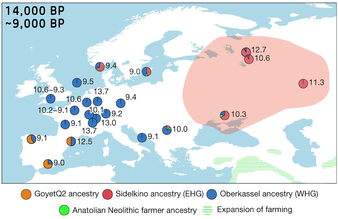
Artifacts and forensic reconstruction of an Eastern Hunter-Gatherer from the site of Yuzhny Oleny island (dated c. 8,100 BP), by M.M. Gerasimov. National Museum of Karelia.[1] Hunter-gatherers in Europe between 14 ka and 9 ka, with the main area of Eastern Hunter-Gatherers (EHG, ). Individual numbers correspond to calibrated sample dates.[2] |
In archaeogenetics, the term Eastern Hunter-Gatherer (EHG), sometimes East European Hunter-Gatherer, or Eastern European Hunter-Gatherer is the name given to a distinct ancestral component that represents descent from Mesolithic hunter-gatherers of Eastern Europe.[3]
https://en.wikipedia.org/wiki/Eastern_Hunter-Gatherer
https://en.wikipedia.org/wiki/equivalent
https://en.wikipedia.org/wiki/Rational_reconstruction
https://en.wikipedia.org/wiki/Invasion_genetics
https://en.wikipedia.org/wiki/Pdr1p
https://en.wikipedia.org/wiki/Supercluster_(genetic)
https://en.wikipedia.org/wiki/Neanderthal_genetics
https://en.wikipedia.org/wiki/Craniofacial_cleft#Genetic_Experimentation
https://en.wikipedia.org/wiki/Archaeogenetics
https://en.wikipedia.org/w/index.php?search=foundation+con&title=Special%3ASearch&ns0=1
https://en.wikipedia.org/no-record-no-outcome-measure









No comments:
Post a Comment